Exam Code: 050-80-CASECURID01
Exam Name: RSA SecurID Certified Administrator 8.0
Certification Provider: RSA
Corresponding Certification: RSA
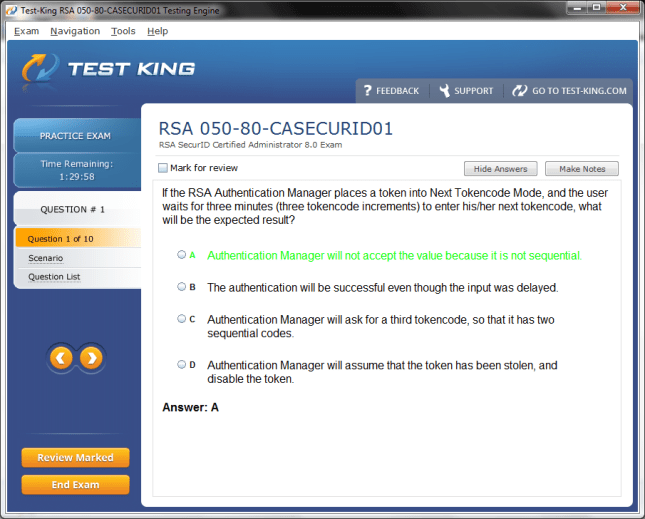
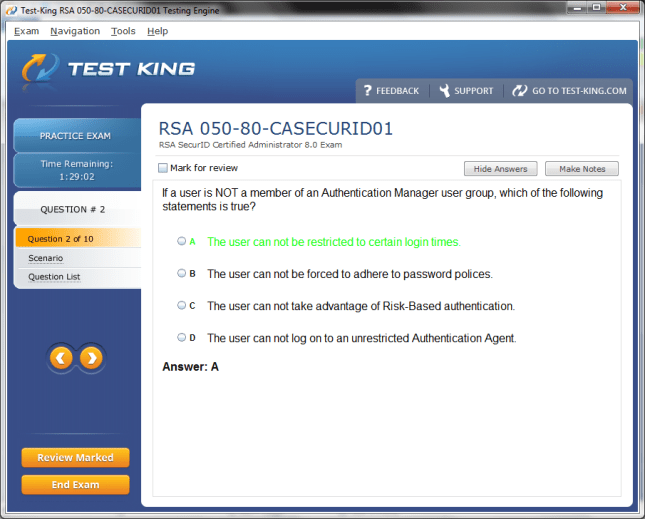
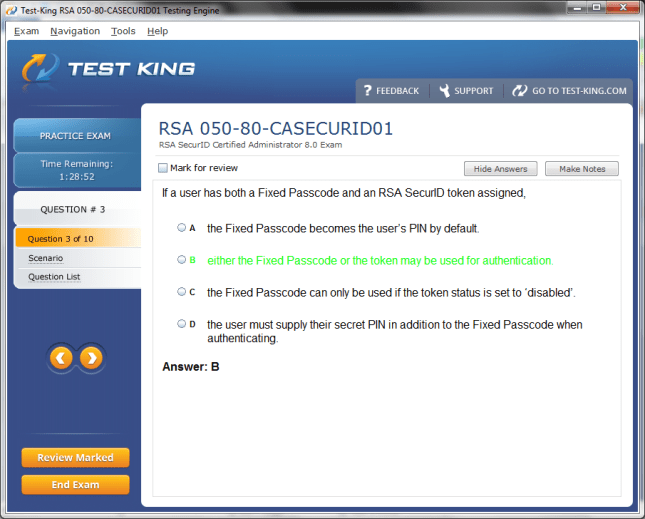
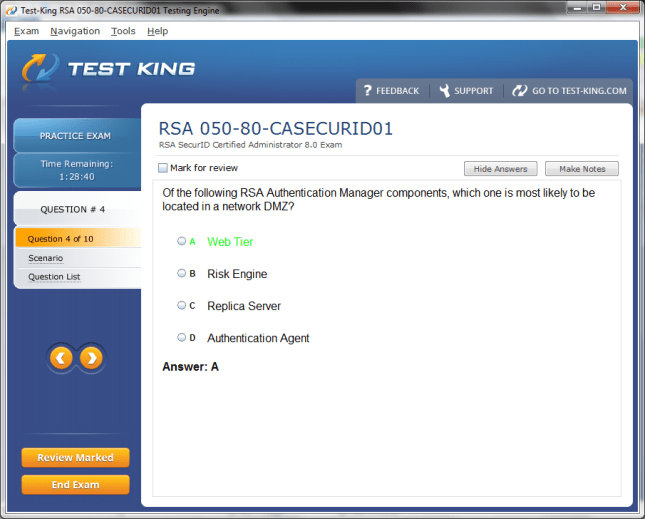
050-80-CASECURID01 Exam Product Screenshots
Frequently Asked Questions
How can I get the products after purchase?
All products are available for download immediately from your Member's Area. Once you have made the payment, you will be transferred to Member's Area where you can login and download the products you have purchased to your computer.
How long can I use my product? Will it be valid forever?
Test-King products have a validity of 90 days from the date of purchase. This means that any updates to the products, including but not limited to new questions, or updates and changes by our editing team, will be automatically downloaded on to computer to make sure that you get latest exam prep materials during those 90 days.
Can I renew my product if when it's expired?
Yes, when the 90 days of your product validity are over, you have the option of renewing your expired products with a 30% discount. This can be done in your Member's Area.
Please note that you will not be able to use the product after it has expired if you don't renew it.
How often are the questions updated?
We always try to provide the latest pool of questions, Updates in the questions depend on the changes in actual pool of questions by different vendors. As soon as we know about the change in the exam question pool we try our best to update the products as fast as possible.
How many computers I can download Test-King software on?
You can download the Test-King products on the maximum number of 2 (two) computers or devices. If you need to use the software on more than two machines, you can purchase this option separately. Please email support@test-king.com if you need to use more than 5 (five) computers.
What is a PDF Version?
PDF Version is a pdf document of Questions & Answers product. The document file has standart .pdf format, which can be easily read by any pdf reader application like Adobe Acrobat Reader, Foxit Reader, OpenOffice, Google Docs and many others.
Can I purchase PDF Version without the Testing Engine?
PDF Version cannot be purchased separately. It is only available as an add-on to main Question & Answer Testing Engine product.
What operating systems are supported by your Testing Engine software?
Our testing engine is supported by Windows. Andriod and IOS software is currently under development.
Comprehensive Guide to the RSA SecurID Certified Administrator 8.0 Exam (050-80-CASECURID01)
The RSA SecurID Certified Administrator 8.0 exam, identified by the code 050-80-CASECURID01, serves as a cornerstone for professionals seeking to validate their proficiency in managing and administering the RSA SecurID platform. This certification emphasizes mastery over the implementation, operation, and troubleshooting of SecurID tokens, authentication servers, and associated policies within enterprise environments. Candidates preparing for this examination must cultivate a deep understanding of multifactor authentication concepts, token lifecycle management, user provisioning, and security protocols that safeguard sensitive digital infrastructures. Unlike basic credentials, this examination evaluates practical knowledge, requiring aspirants to demonstrate both conceptual clarity and operational competence.
Understanding the RSA SecurID Certified Administrator 8.0 Exam
The RSA SecurID ecosystem is multifaceted, comprising software and hardware tokens, authentication managers, and integration modules with existing enterprise applications. Understanding the nuances of these components is essential, as the examination often presents scenarios where administrators must configure, monitor, and troubleshoot authentication workflows under varying organizational requirements. The exam emphasizes not merely rote memorization of features but the application of best practices to ensure secure and reliable access control. In this context, candidates should familiarize themselves with the architecture of authentication servers, replication mechanisms between primary and secondary servers, and the configuration of disaster recovery protocols.
Core Competencies Assessed in the Examination
Candidates aspiring to attain the RSA SecurID Certified Administrator 8.0 designation are evaluated across several critical competencies. One prominent area is token management, encompassing hardware, software, and mobile SecurID tokens. Candidates must understand enrollment procedures, token activation, PIN synchronization, and methods to address token failures or discrepancies. Equally important is the knowledge of authentication policies, which define how users access systems and the layers of verification required. Administrators must know how to configure policy rules, apply user groups, and tailor access controls to organizational security mandates.
Another key competency revolves around system monitoring and auditing. The examination tests the ability to utilize server logs, reports, and alerts to detect anomalies or irregular authentication patterns. Understanding the integration of RSA SecurID with other identity management systems, such as LDAP directories or cloud-based authentication modules, is crucial. Candidates are often evaluated on their aptitude to configure these integrations securely, troubleshoot connectivity issues, and maintain compliance with organizational or regulatory standards.
Troubleshooting and problem resolution form a substantial part of the examination. Administrators are expected to identify root causes of authentication failures, token discrepancies, or server replication issues. Proficiency in navigating administrative consoles, interpreting error messages, and applying corrective actions swiftly is highly valued. Additionally, knowledge of upgrade procedures and patch management for RSA SecurID components ensures that systems remain secure against evolving threats. Candidates must demonstrate an ability to plan and execute maintenance without disrupting enterprise access services.
Examination Structure and Question Types
The 050-80-CASECURID01 examination is designed to assess both theoretical knowledge and practical expertise. While the exact number of questions may vary, the exam generally comprises multiple-choice and scenario-based questions that challenge candidates to apply their skills in real-world contexts. Scenario-based questions are particularly significant, as they simulate operational environments where administrators must make critical decisions regarding authentication configurations, user management, and system troubleshooting. The examination requires careful reading of each scenario, logical reasoning, and application of best practices to determine the most effective solutions.
Time management is an essential aspect of the examination. Candidates must pace themselves to allocate sufficient time to interpret complex scenarios, analyze potential outcomes, and select the most accurate responses. Familiarity with common error patterns, token lifecycle issues, and authentication server replication challenges can significantly enhance efficiency. Preparing for scenario-based questions by studying practical examples, performing hands-on lab exercises, and reviewing system documentation can help candidates build confidence and agility in responding to real-world operational dilemmas.
Preparation Strategies and Study Approaches
A successful approach to the RSA SecurID Certified Administrator 8.0 exam combines structured study, practical exercises, and conceptual understanding. The first step is to review the official exam objectives and ensure comprehensive coverage of topics, including token management, authentication policies, system monitoring, auditing, integration, and troubleshooting. Creating a study schedule that balances theoretical review with hands-on practice can optimize retention and skill acquisition.
Engaging with practical labs and simulations is particularly beneficial. Setting up a virtualized environment with SecurID authentication servers, integrating them with LDAP directories or enterprise applications, and simulating token enrollment and failure scenarios can deepen understanding. This experiential approach allows candidates to encounter potential challenges in a controlled setting, improving their ability to troubleshoot and resolve issues under examination conditions. Complementing hands-on exercises with detailed study guides, technical manuals, and peer discussions can further solidify comprehension.
Another effective strategy involves practicing scenario-based questions, which mirror the type of problems presented in the exam. Candidates should analyze each question carefully, identify key elements, and consider potential implications before selecting an answer. Reviewing previous case studies or real-world operational incidents can also provide insight into common challenges administrators face, thereby enhancing problem-solving acumen. Additionally, staying informed about updates to RSA SecurID features and industry best practices ensures that knowledge remains current and applicable.
Key Concepts and Terminology
Mastery of essential concepts and terminology is crucial for success in the examination. Candidates should be familiar with multifactor authentication, which combines something the user knows, something the user has, and, in some cases, something the user is. RSA SecurID tokens exemplify this principle, generating time-based codes synchronized with authentication servers. Understanding token synchronization, resynchronization procedures, and PIN management is vital for maintaining secure access controls.
Authentication server architecture, including primary and replica servers, forms another cornerstone of the exam. Candidates must understand replication policies, failover mechanisms, and backup procedures to ensure business continuity. Knowledge of access policies, authentication rules, and exception handling is necessary for configuring secure and efficient authentication workflows. Equally important is familiarity with system monitoring tools, reporting mechanisms, and audit trails, which allow administrators to detect irregularities, comply with regulatory requirements, and maintain accountability.
Integration with enterprise directories, cloud services, and third-party applications constitutes a significant component of administrative responsibilities. Administrators must understand protocols such as LDAP, RADIUS, and SAML, as well as methods for securing communication between systems. Troubleshooting integration issues, maintaining certificate trust relationships, and configuring single sign-on (SSO) capabilities are areas that often appear in scenario-based questions. By internalizing these concepts and linking them to practical applications, candidates can confidently navigate complex operational challenges.
Common Challenges and How to Address Them
Administrators preparing for the RSA SecurID Certified Administrator 8.0 exam often encounter recurring challenges that require attention and strategic preparation. Token-related issues, such as lost, stolen, or malfunctioning tokens, necessitate knowledge of resynchronization, replacement procedures, and emergency access protocols. Similarly, server replication discrepancies can disrupt authentication processes, making familiarity with replication logs, error codes, and corrective measures essential.
Another frequent challenge involves integration complexities, particularly when connecting RSA SecurID with diverse enterprise applications or cloud platforms. Misconfigured directories, network restrictions, and certificate mismatches can impede authentication workflows. Developing a systematic troubleshooting methodology—identifying the problem, isolating affected components, and applying targeted solutions—can mitigate these issues. Scenario-based practice, combined with exposure to real-world operational incidents, enhances the ability to respond effectively to unexpected problems.
Maintaining compliance with organizational and regulatory standards adds an additional layer of complexity. Administrators must ensure that authentication policies align with security mandates, audit trails are complete and accurate, and system configurations adhere to best practices. Understanding how to implement security controls, monitor system activity, and document processes is crucial. Candidates who cultivate these skills not only excel in the examination but also demonstrate operational proficiency that translates to real-world enterprise environments.
Advanced Token Management and Enrollment Procedures
A central focus of the RSA SecurID Certified Administrator 8.0 exam is the comprehensive understanding and management of tokens, which form the linchpin of multifactor authentication. Tokens are instrumental in ensuring secure access to enterprise systems, and administrators must possess mastery over their lifecycle management. The examination evaluates knowledge of hardware tokens, software tokens, and mobile credentials, encompassing issuance, activation, and ongoing maintenance. Candidates are expected to understand how to synchronize tokens with authentication servers, manage PINs, and resolve discrepancies caused by time desynchronization or network interruptions.
The enrollment process for RSA SecurID tokens requires precise execution to avoid authentication failures. Administrators must comprehend procedures for enrolling new users, generating activation codes, and provisioning tokens according to organizational access policies. Equally vital is the knowledge of deactivating or revoking tokens for users who have left the organization or experienced security incidents. Scenario-based questions often assess the ability to troubleshoot enrollment errors, manage bulk activations, and maintain accurate user-token mappings in dynamic enterprise environments. Proficiency in these operations ensures continuity and security in authentication workflows.
Authentication Policies and Access Control Mechanisms
The design and enforcement of authentication policies are critical competencies evaluated in the examination. RSA SecurID administrators must understand how to configure policy rules that dictate user access, frequency of authentication, and the application of multifactor verification under different circumstances. Policies may vary based on user groups, locations, time windows, and risk levels, requiring careful configuration to balance security and operational efficiency. Candidates should be adept at tailoring access controls to meet compliance standards while minimizing disruptions to user productivity.
Understanding exceptions and policy overrides is also essential, as real-world environments often require temporary adjustments to standard rules. Administrators are expected to implement conditional access controls, allowing for nuanced decision-making that accommodates both security imperatives and practical business needs. The examination tests knowledge of policy hierarchy, inheritance, and conflict resolution, emphasizing the importance of logical structuring and meticulous configuration. Mastery of these concepts enables administrators to create resilient, flexible, and auditable authentication environments.
Monitoring, Auditing, and Reporting
RSA SecurID administrators are responsible for maintaining situational awareness over authentication activities, and the examination evaluates the ability to leverage monitoring and auditing tools effectively. Candidates must understand how to interpret server logs, generate reports, and analyze alerts to identify anomalies or potential security breaches. Monitoring mechanisms provide insights into token usage, failed authentication attempts, and synchronization errors, enabling proactive intervention before issues escalate. Scenario-based questions frequently simulate abnormal patterns that administrators must recognize and address promptly.
Auditing capabilities serve as a vital component of compliance and accountability. Administrators must know how to produce detailed reports on user activity, token issuance, and policy adherence. Such reports support regulatory requirements and internal governance, ensuring transparency and traceability of authentication operations. The ability to extract meaningful insights from audit data, correlate events across servers, and recommend remedial actions is a skill highly valued in both the examination and professional practice. Candidates are encouraged to practice generating comprehensive audit summaries and interpreting intricate log details to enhance analytical proficiency.
Integration with Enterprise Systems
Integration of RSA SecurID with enterprise directories, cloud platforms, and third-party applications is another pivotal topic. Administrators must understand protocols such as LDAP, RADIUS, and SAML, and how to configure trust relationships to facilitate seamless authentication. The examination assesses the ability to establish secure connections, manage certificates, and configure single sign-on solutions. Integration scenarios often challenge candidates to troubleshoot communication issues, resolve mismatched credentials, and ensure that access policies propagate correctly across systems.
Knowledge of directory synchronization, user provisioning, and federation techniques is crucial for managing complex environments. Candidates must grasp the nuances of mapping user attributes, managing group memberships, and aligning authentication rules across multiple platforms. Scenario-based questions frequently depict integration failures or partial connectivity issues, requiring administrators to apply diagnostic methodologies and remedial procedures. Familiarity with common pitfalls, error codes, and logging mechanisms enhances the ability to maintain continuous and secure authentication services.
Troubleshooting and Problem Resolution
Effective troubleshooting skills are indispensable for RSA SecurID administrators and form a major component of the examination. Candidates are expected to identify root causes of authentication failures, whether related to token desynchronization, server replication inconsistencies, or misconfigured access policies. A systematic approach to problem resolution—diagnosing, isolating, and rectifying issues—is vital for minimizing downtime and maintaining operational reliability. Scenario-based questions evaluate the candidate’s capacity to apply logical reasoning and procedural knowledge to resolve complex issues efficiently.
Common troubleshooting tasks include addressing token synchronization errors, recovering lost or compromised tokens, and rectifying failed authentication attempts. Administrators must also be adept at diagnosing server replication issues, network communication failures, and integration anomalies. Mastery of troubleshooting not only contributes to examination success but also reflects real-world operational competence. Practicing hypothetical scenarios, reviewing system documentation, and performing hands-on exercises are strategies that strengthen analytical skills and reinforce procedural familiarity.
Security Best Practices and Operational Efficiency
The examination emphasizes the importance of adhering to security best practices while maintaining operational efficiency. RSA SecurID administrators must implement robust security measures, including enforcing strong PIN policies, managing token revocation promptly, and monitoring unusual authentication patterns. Understanding the principles of least privilege, segregation of duties, and secure configuration management is essential. Scenario-based questions often present situations requiring the candidate to balance security imperatives with practical constraints, highlighting the necessity of informed judgment.
Operational efficiency is reinforced through proactive maintenance, timely updates, and systematic documentation. Administrators should be familiar with patch management procedures, upgrade methodologies, and disaster recovery planning to ensure continuity and resilience of authentication services. Scenario-based questions may test the ability to schedule maintenance without disrupting user access or to apply updates while preserving system integrity. By internalizing security principles and operational protocols, candidates demonstrate a holistic understanding of RSA SecurID administration, which extends beyond examination requirements into practical enterprise management.
Real-World Applications and Strategic Implementation
Understanding the strategic implications of RSA SecurID deployment in enterprise environments is another dimension evaluated in the examination. Administrators must recognize how multifactor authentication enhances overall security posture, mitigates risk, and supports compliance frameworks. Scenario-based questions often require candidates to design authentication strategies that align with organizational objectives, integrate seamlessly with existing systems, and accommodate evolving security challenges. Knowledge of high-availability configurations, load balancing, and disaster recovery enhances the candidate’s ability to architect resilient and scalable authentication solutions.
Strategic implementation also encompasses capacity planning, performance monitoring, and continuous improvement of authentication services. Administrators are expected to assess system usage trends, predict future requirements, and implement policies that maintain efficiency and security. The examination evaluates not only technical competence but also the capacity to make informed decisions that optimize organizational outcomes. Candidates who internalize these principles can approach both the examination and real-world administration with confidence, adaptability, and strategic foresight.
Mastering Authentication Server Configuration
A pivotal component of the RSA SecurID Certified Administrator 8.0 examination involves comprehensive knowledge of authentication server configuration. Candidates are expected to demonstrate proficiency in installing, configuring, and maintaining RSA Authentication Managers to ensure seamless authentication operations. This includes understanding network settings, time synchronization, and the replication of primary and secondary servers to maintain high availability. Knowledge of clustering, load balancing, and failover mechanisms is essential, as the exam often presents scenarios where administrators must ensure uninterrupted authentication services despite system anomalies.
Administrators must also be adept at configuring user groups, policies, and token assignments to align with organizational access requirements. The examination evaluates the ability to manage hierarchical structures, enforce policy inheritance, and implement exceptions when needed. Scenario-based questions often require troubleshooting misconfigurations, rectifying policy conflicts, or restoring authentication workflows after replication failures. A detailed understanding of server logs, event alerts, and diagnostic tools is crucial for rapid problem identification and resolution.
Token Lifecycle and Advanced Management
Token lifecycle management is another critical domain assessed in the examination. Candidates must understand all phases of a token’s operational life, including issuance, activation, assignment, synchronization, revocation, and replacement. Mastery of hardware tokens, software tokens, and mobile credentials is necessary, alongside familiarity with PIN initialization, reset procedures, and emergency access mechanisms. Scenario-based questions frequently depict token desynchronization, loss, or expiration, challenging candidates to apply best practices for restoring secure access.
Administrators must also consider bulk token operations, such as enrolling multiple users simultaneously or performing large-scale replacements due to organizational restructuring or security incidents. Knowledge of reporting mechanisms that track token status, usage patterns, and anomalies enables administrators to maintain oversight and anticipate potential disruptions. Candidates who can demonstrate both theoretical understanding and practical execution of token management tasks exhibit the proficiency expected in the examination and in operational environments.
Security Policies and Multifactor Authentication Strategies
The examination places significant emphasis on the design and implementation of security policies that govern multifactor authentication. Candidates are expected to understand how to configure authentication rules, apply conditional access controls, and enforce policy hierarchies to achieve an optimal balance between security and usability. Real-world scenarios often require administrators to implement risk-based authentication, allowing for dynamic policy adjustments based on user behavior, location, or device characteristics.
Understanding exceptions and emergency overrides is equally vital. Administrators may need to grant temporary access to users while ensuring that overall security posture remains uncompromised. The examination tests the ability to evaluate complex scenarios, identify potential vulnerabilities, and apply policies that maintain compliance with regulatory requirements and organizational standards. By internalizing these principles, candidates can confidently navigate both theoretical questions and practical challenges presented in operational environments.
Monitoring, Auditing, and Incident Management
Monitoring and auditing form the backbone of effective RSA SecurID administration. Candidates must demonstrate the ability to interpret logs, generate reports, and analyze authentication trends to detect irregularities, unauthorized attempts, or system failures. Scenario-based questions often involve examining server logs to identify patterns that indicate potential security breaches or operational inefficiencies. Administrators must be proficient in correlating data from multiple sources, understanding error codes, and implementing corrective actions to restore normal operations.
Incident management is a critical skill assessed in the examination. Administrators are expected to respond swiftly to authentication disruptions, token anomalies, and server replication issues. Developing systematic procedures for incident response, documenting actions, and communicating effectively with stakeholders ensures both operational continuity and regulatory compliance. Candidates who cultivate a methodical approach to monitoring, auditing, and incident management are well-equipped to handle real-world challenges while demonstrating mastery during the examination.
Integration with Enterprise Directories and Third-Party Applications
Integration of RSA SecurID with enterprise directories, cloud-based platforms, and third-party applications is another key area evaluated in the examination. Administrators must understand the intricacies of protocols such as LDAP, RADIUS, and SAML, and how to configure trust relationships to enable seamless authentication. Scenario-based questions often challenge candidates to troubleshoot connectivity issues, resolve attribute mapping errors, or address certificate mismatches that impede user access.
Knowledge of directory synchronization, group membership management, and attribute mapping is essential for maintaining consistency and security across multiple systems. Candidates must demonstrate the ability to configure single sign-on, manage federation relationships, and enforce consistent authentication policies across diverse environments. Practical understanding of integration scenarios not only aids in examination success but also reflects the operational proficiency required for administering complex enterprise authentication infrastructures.
Troubleshooting Complex Scenarios
The examination rigorously evaluates the candidate’s ability to troubleshoot multifaceted authentication issues. Administrators must be capable of diagnosing problems related to token synchronization, server replication, network connectivity, and policy conflicts. Scenario-based questions frequently simulate conditions where multiple factors contribute to authentication failures, requiring candidates to apply logical reasoning, systematic analysis, and procedural knowledge to restore service effectively.
Effective troubleshooting begins with identifying symptoms, isolating affected components, and determining root causes. Administrators must also be skilled in implementing corrective measures while minimizing disruption to users. Familiarity with error codes, log interpretation, and diagnostic utilities enhances problem-solving efficiency. Candidates who practice real-world troubleshooting exercises, including simulated token failures, replication inconsistencies, and integration anomalies, develop the confidence and acumen necessary to excel in the examination and in professional practice.
Strategic Operational Management
Beyond technical expertise, the examination emphasizes strategic operational management. Administrators are expected to optimize authentication systems for efficiency, scalability, and resilience. This involves planning for server capacity, scheduling maintenance, and implementing upgrade strategies without compromising access availability. Scenario-based questions often assess the ability to anticipate system load, manage resource allocation, and ensure high availability in complex environments.
Security, operational efficiency, and user experience must be balanced thoughtfully. Administrators are encouraged to document procedures meticulously, monitor system performance, and continuously refine policies to address emerging risks. Candidates who internalize these operational strategies exhibit a holistic understanding of RSA SecurID administration, demonstrating both technical mastery and strategic insight that extends beyond the confines of the examination.
Advanced Troubleshooting, System Maintenance, and Operational Mastery
The RSA SecurID Certified Administrator 8.0 exam challenges candidates to demonstrate an advanced level of proficiency in maintaining, troubleshooting, and optimizing enterprise authentication systems. Administrators are expected to understand complex operational scenarios, ensuring that authentication services remain uninterrupted while adhering to organizational security mandates. This includes diagnosing token synchronization errors, resolving replication conflicts, managing authentication policies, and integrating third-party applications securely. Candidates must combine technical acuity with practical foresight, applying structured methodologies to restore or enhance system functionality efficiently.
System maintenance encompasses both proactive and reactive strategies. Proactive measures involve monitoring server health, applying patches and updates in a timely manner, and performing routine audits to detect latent vulnerabilities. Reactive measures require swift identification and resolution of anomalies such as failed authentications, token mismatches, or network connectivity disruptions. Scenario-based questions often simulate real-world challenges where administrators must diagnose subtle inconsistencies, implement corrective actions, and verify that services return to operational stability without jeopardizing security.
Token Synchronization and Resilience Management
Token synchronization represents a fundamental competency assessed in the examination. RSA SecurID tokens generate time-based codes that must align precisely with authentication servers. Administrators must understand how to perform resynchronization when discrepancies occur, manage lost or compromised tokens, and enforce robust PIN policies. Scenario-based questions frequently depict complex situations involving multiple users, bulk token enrollments, or simultaneous failures across servers, requiring methodical troubleshooting and remedial strategies.
Resilience management extends beyond individual token issues to encompass replication between primary and secondary authentication servers. Administrators must be adept at configuring replication schedules, resolving conflicts, and ensuring continuity in high-availability configurations. Understanding server logs, alerting mechanisms, and diagnostic tools enables rapid identification of replication anomalies and supports corrective interventions. Candidates are expected to internalize these procedures to demonstrate both operational competence and analytical proficiency.
Policy Enforcement and Multifactor Authentication Optimization
The examination evaluates the candidate’s ability to design, implement, and optimize multifactor authentication policies. Administrators must configure authentication rules, apply conditional access controls, and manage exceptions to ensure both security and usability. Policies may vary according to user roles, geographic locations, device types, and risk levels, requiring thoughtful calibration to prevent security lapses while minimizing user disruption.
Scenario-based questions often challenge candidates to reconcile conflicting policy requirements, address emergency access scenarios, or adapt policies in response to evolving threats. Knowledge of policy hierarchies, inheritance, and precedence ensures that administrators can resolve complex conflicts and maintain coherent authentication environments. By mastering these principles, candidates exhibit the ability to balance stringent security measures with operational pragmatism, a skill essential for both examination success and real-world administration.
Monitoring, Reporting, and Audit Analysis
Effective monitoring and reporting are indispensable for maintaining situational awareness over authentication systems. Administrators must utilize server logs, analytical tools, and alerting mechanisms to detect irregularities, unauthorized attempts, or service disruptions. The examination assesses the ability to interpret complex log entries, correlate events across multiple servers, and implement timely corrective actions. Scenario-based questions often present anomalies in authentication patterns, requiring the candidate to apply systematic analysis and diagnostic reasoning.
Auditing serves as a complementary function, providing transparency and compliance verification. Administrators must generate detailed reports on user activity, token assignments, authentication attempts, and policy adherence. These reports support regulatory requirements and internal governance while providing insights into system performance and potential security risks. Candidates should practice interpreting audit data, identifying trends, and documenting findings to reinforce analytical capabilities and operational acumen.
Integration with Enterprise Environments and Third-Party Systems
Integration with enterprise directories, cloud platforms, and third-party applications is a recurring theme in the examination. Administrators must be conversant with protocols such as LDAP, RADIUS, and SAML, and understand how to configure trust relationships, attribute mappings, and federation mechanisms. Scenario-based questions frequently simulate integration challenges, such as misconfigured attributes, certificate issues, or connectivity failures, requiring candidates to apply diagnostic procedures and remedial strategies.
Knowledge of single sign-on implementation, user provisioning, and policy propagation across integrated systems is essential. Administrators must ensure that authentication policies remain consistent, tokens function correctly, and secure communication channels are maintained. Proficiency in these areas demonstrates an ability to manage complex authentication ecosystems, a skill that directly correlates with both examination performance and operational effectiveness.
Problem-Solving and Operational Decision-Making
The examination emphasizes practical problem-solving capabilities, testing the candidate’s aptitude for resolving multifaceted authentication issues under operational constraints. Administrators must approach challenges methodically, identifying root causes, evaluating potential solutions, and implementing corrective measures efficiently. Scenario-based questions often present simultaneous failures, conflicting policies, or integration discrepancies, requiring the application of both technical knowledge and critical thinking.
Decision-making extends beyond immediate troubleshooting to strategic operational considerations. Administrators must assess the impact of policy changes, server maintenance, and token deployments on system reliability and user experience. Candidates who can integrate analytical reasoning with informed operational judgment demonstrate the breadth of understanding required to succeed in the examination and excel in enterprise administration.
Strategic Maintenance and System Optimization
Strategic maintenance encompasses planning, resource allocation, and performance optimization. Administrators must schedule upgrades, monitor system load, and optimize authentication workflows to sustain high availability and efficiency. Scenario-based questions may evaluate the ability to balance maintenance windows with business requirements, implement redundant configurations, or plan for disaster recovery contingencies. Knowledge of capacity planning, replication integrity, and server performance metrics is crucial for anticipating challenges and maintaining uninterrupted service.
System optimization also involves continuous review and refinement of authentication policies, token management procedures, and integration configurations. Administrators are encouraged to monitor trends, identify inefficiencies, and implement improvements that enhance security and operational agility. Mastery of strategic maintenance and optimization demonstrates a comprehensive understanding of RSA SecurID administration, encompassing both technical execution and forward-looking system management.
Operational Excellence in RSA SecurID Administration
Achieving mastery in RSA SecurID administration requires a meticulous understanding of both the technical and procedural aspects of the platform. The examination evaluates candidates on their ability to maintain high-performing authentication environments, troubleshoot complex scenarios, and enforce security policies that align with enterprise requirements. Administrators must demonstrate a profound understanding of token lifecycle management, authentication server configurations, replication mechanisms, and multifactor authentication strategies. Mastery of these domains ensures not only examination success but also operational proficiency in real-world enterprise settings.
Administrators must navigate the intricacies of token management, encompassing the provisioning of hardware, software, and mobile credentials. Each token type presents unique operational challenges, from enrollment and activation to PIN synchronization and revocation. Candidates are expected to internalize best practices for bulk token deployment, emergency access procedures, and user lifecycle management. Scenario-based questions often challenge candidates to resolve discrepancies across multiple servers or user groups, requiring both analytical reasoning and precise execution.
Authentication Policy Design and Enforcement
Authentication policies constitute a cornerstone of RSA SecurID administration. The examination tests the candidate’s ability to create, configure, and enforce multifactor authentication policies that balance security requirements with operational efficiency. Administrators must be adept at establishing rules for user groups, defining access windows, and implementing conditional access controls that respond dynamically to user behavior, risk profiles, or device attributes. Scenario-based questions frequently explore policy conflicts, requiring candidates to reconcile exceptions and prioritize security without disrupting legitimate access.
Policy enforcement also demands familiarity with emergency overrides, temporary access mechanisms, and exception handling procedures. Administrators must ensure that any temporary deviation from standard policies is auditable and does not compromise the broader security posture. Candidates who internalize these principles are better equipped to manage complex authentication environments, respond effectively to unexpected challenges, and demonstrate mastery during examination scenarios.
Advanced Monitoring, Reporting, and Audit Practices
Monitoring and reporting are integral to maintaining a secure and reliable authentication infrastructure. Administrators must be proficient in interpreting server logs, generating detailed reports, and analyzing authentication patterns to detect anomalies, failures, or potential security threats. The examination often presents scenarios requiring the candidate to diagnose irregularities, correlate events across multiple servers, and implement corrective actions promptly. Effective monitoring allows administrators to anticipate issues, mitigate risks, and maintain service continuity in dynamic enterprise environments.
Audit practices extend beyond reporting to encompass compliance verification and accountability. Administrators must document user activity, token assignments, and policy adherence accurately, ensuring traceability and regulatory compliance. Scenario-based questions may present complex audit challenges, requiring candidates to extract meaningful insights, identify deviations, and recommend corrective measures. Mastery of monitoring and audit practices demonstrates a holistic understanding of operational oversight and reinforces strategic management capabilities in RSA SecurID environments.
Integration with Enterprise Systems and Cloud Platforms
RSA SecurID administration frequently involves integration with enterprise directories, cloud services, and third-party applications. Administrators must understand protocols such as LDAP, RADIUS, and SAML, and how to configure secure trust relationships, attribute mappings, and federation connections. The examination evaluates the candidate’s ability to troubleshoot integration failures, resolve connectivity issues, and ensure that authentication policies propagate consistently across diverse platforms.
Integration tasks also include implementing single sign-on solutions, synchronizing user attributes, and maintaining policy consistency in federated environments. Scenario-based questions may present situations where integration anomalies affect multiple users or applications simultaneously, challenging candidates to diagnose root causes and apply remediation strategies efficiently. Proficiency in integration demonstrates the ability to manage complex, heterogeneous authentication landscapes while maintaining security, reliability, and user experience.
Troubleshooting Complex Authentication Scenarios
Advanced troubleshooting forms a significant portion of the examination, requiring candidates to address multifaceted issues across tokens, authentication servers, and integrated systems. Administrators must apply systematic diagnostic methodologies to identify symptoms, isolate affected components, and implement corrective actions. Scenario-based questions often simulate simultaneous failures, conflicting policies, or integration inconsistencies, requiring both technical knowledge and logical reasoning.
Common troubleshooting challenges include token desynchronization, failed authentications, server replication discrepancies, and policy misconfigurations. Administrators must be familiar with diagnostic tools, log analysis techniques, and error codes to resolve issues efficiently. Practicing complex, real-world scenarios equips candidates with the confidence and acumen necessary to excel in examination situations and to maintain operational continuity in enterprise environments.
Strategic Maintenance and System Optimization
System optimization is critical for maintaining high availability, operational efficiency, and resilience. Administrators must plan maintenance windows, perform server upgrades, monitor system load, and optimize authentication workflows to sustain uninterrupted service. Scenario-based questions often test the ability to anticipate challenges, manage redundant configurations, and execute maintenance without disrupting user access. Knowledge of performance metrics, capacity planning, and replication integrity is essential for proactive operational management.
Strategic maintenance also involves continuous refinement of policies, token management procedures, and integration configurations. Administrators must monitor trends, identify inefficiencies, and implement enhancements that improve both security and usability. Candidates who internalize these strategies demonstrate comprehensive expertise in RSA SecurID administration, encompassing both practical execution and forward-looking operational planning.
Incident Management and Operational Resilience
Effective incident management is central to both examination success and enterprise proficiency. Administrators must respond to authentication disruptions, token failures, and system anomalies swiftly and methodically. Scenario-based questions often simulate incidents requiring immediate corrective action, documentation of responses, and verification of restored functionality. Knowledge of incident escalation, contingency planning, and operational documentation ensures administrators can handle crises without compromising security or service continuity.
Operational resilience extends beyond immediate incident response, emphasizing redundancy, disaster recovery, and business continuity planning. Administrators must ensure authentication services remain functional under adverse conditions, including server failures, network disruptions, or widespread token issues. Mastery of these concepts reflects a holistic understanding of RSA SecurID administration, integrating technical competence, strategic planning, and operational foresight.
Advanced Administration, Strategic Operations, and Certification Mastery
The RSA SecurID Certified Administrator 8.0 examination represents a culmination of knowledge, practical skill, and strategic operational understanding for professionals tasked with managing enterprise authentication systems. Candidates are assessed on their ability to administer authentication servers, configure multifactor authentication policies, manage token lifecycles, troubleshoot complex scenarios, and integrate RSA SecurID with diverse enterprise platforms. Success in this examination demonstrates not only theoretical comprehension but also the operational competence necessary to maintain secure, reliable, and efficient authentication infrastructures.
Administrators are expected to navigate token management with finesse, handling hardware, software, and mobile credentials across varied organizational contexts. This encompasses enrollment, activation, synchronization, revocation, and emergency access procedures. Scenario-based questions often simulate multiple users experiencing simultaneous token issues or system anomalies, testing the candidate’s ability to diagnose root causes, apply corrective measures, and restore normal operations efficiently. Mastery of these operations reflects real-world proficiency and is a critical factor in examination performance.
Multifactor Authentication Policies and Dynamic Access Controls
Central to RSA SecurID administration is the design and enforcement of multifactor authentication policies that align with security mandates and organizational objectives. Administrators must configure rules for user groups, enforce conditional access controls, and manage exceptions in a manner that maintains operational fluidity while preserving security integrity. Scenario-based questions often challenge candidates to reconcile conflicting policy requirements, manage emergency access, or adapt authentication rules to dynamic enterprise conditions.
Understanding policy hierarchies, precedence, and inheritance is essential to resolving complex conflicts and ensuring coherent access control frameworks. Candidates are expected to demonstrate the ability to enforce policies consistently across multiple systems, integrate conditional logic based on risk profiles, and maintain robust documentation for compliance and auditing purposes. By internalizing these concepts, administrators exhibit both technical mastery and strategic foresight.
System Monitoring, Auditing, and Operational Insights
Effective monitoring and auditing constitute a cornerstone of RSA SecurID administration. Administrators must utilize diagnostic tools, server logs, and alerting mechanisms to detect anomalies, security threats, or operational inefficiencies. The examination often presents scenarios requiring careful log analysis, event correlation, and timely intervention to prevent disruptions. Candidates must develop a systematic approach to identifying irregular authentication patterns, token desynchronizations, or replication conflicts and applying remediation procedures efficiently.
Auditing extends the scope of oversight, providing accountability and compliance verification. Administrators are expected to generate detailed reports on authentication events, token issuance, policy enforcement, and user activity. These reports support regulatory frameworks and internal governance while revealing potential operational improvements. Scenario-based questions often simulate complex audit challenges that require analytical reasoning and the ability to extract actionable insights from voluminous data. Mastery of monitoring and auditing ensures administrators can maintain situational awareness and operational excellence.
Integration with Enterprise and Cloud Environments
Integration with enterprise directories, cloud-based services, and third-party applications is a recurring domain of focus in the examination. Administrators must configure secure trust relationships, attribute mappings, federation protocols, and single sign-on mechanisms. Scenario-based questions often present complex integration challenges such as misaligned attributes, certificate mismatches, or connectivity failures, requiring candidates to apply problem-solving methodologies and corrective measures effectively.
Administrators must also ensure policy consistency, token functionality, and secure communication across integrated systems. Proficiency in these areas reflects the ability to manage heterogeneous authentication environments, balancing operational efficiency with rigorous security standards. Candidates who practice real-world integration scenarios develop the confidence and analytical skills necessary to address diverse enterprise challenges and succeed in examination simulations.
Advanced Troubleshooting and Problem Resolution
The RSA SecurID Certified Administrator 8.0 exam emphasizes advanced troubleshooting capabilities. Administrators must identify, isolate, and remediate multifaceted authentication issues involving token synchronization, server replication, network connectivity, and policy conflicts. Scenario-based questions often depict simultaneous failures, testing the candidate’s ability to apply systematic diagnostic processes and implement effective solutions.
Effective troubleshooting requires familiarity with server logs, diagnostic utilities, error codes, and corrective methodologies. Administrators must approach each problem methodically, balancing immediate remediation with strategic operational considerations. Practicing complex scenarios such as bulk token failures, integration anomalies, or policy misconfigurations equips candidates with the practical skills required to resolve issues efficiently and confidently, both during the examination and in professional environments.
Strategic Maintenance and Optimization
Strategic maintenance and system optimization are essential competencies for ensuring high availability, operational resilience, and efficiency. Administrators must plan and execute maintenance windows, perform server upgrades, monitor system performance, and optimize authentication workflows. Scenario-based questions may assess the ability to schedule interventions without disrupting user access, implement redundancy, or anticipate capacity requirements to maintain uninterrupted service.
System optimization also involves continual review of policies, token management procedures, and integration configurations. Administrators must identify inefficiencies, refine processes, and enhance operational agility. Mastery of strategic maintenance demonstrates comprehensive understanding, integrating technical proficiency with forward-looking planning, risk mitigation, and sustainable operational management.
Incident Response and Operational Resilience
Incident response forms a critical element of RSA SecurID administration. Administrators must respond to authentication disruptions, token failures, and system anomalies swiftly and systematically. Scenario-based questions frequently simulate incidents requiring immediate corrective action, documentation, and validation of restored functionality. Candidates must understand escalation procedures, contingency planning, and operational documentation to ensure secure, reliable, and traceable resolution.
Operational resilience extends beyond reactive measures to encompass disaster recovery, redundancy, and business continuity strategies. Administrators must ensure authentication systems remain functional under adverse conditions, including server outages, network failures, or widespread token disruptions. Mastery of resilience principles reflects a holistic understanding of RSA SecurID administration, integrating technical expertise, strategic planning, and operational foresight.
Conclusion
The RSA SecurID Certified Administrator 8.0 examination (050-80-CASECURID01) is a rigorous assessment of both theoretical knowledge and practical competence in managing enterprise authentication systems. Candidates must master token lifecycle management, multifactor authentication policy design, authentication server configuration, integration with enterprise and cloud systems, advanced troubleshooting, monitoring, auditing, and operational optimization. Scenario-based questions challenge candidates to apply logical reasoning, technical skill, and strategic foresight to solve complex, real-world problems. By cultivating these competencies, professionals not only achieve certification but also acquire the operational proficiency and strategic insight necessary to maintain secure, efficient, and resilient authentication infrastructures in dynamic enterprise environments. Mastery of RSA SecurID administration thus represents a synthesis of technical excellence, operational acumen, and strategic foresight, enabling candidates to excel in both examination scenarios and professional practice.