Exam Code: MK0-201
Exam Name: Certified Penetration Testing Specialist (CPTS)
Certification Provider: Mile2
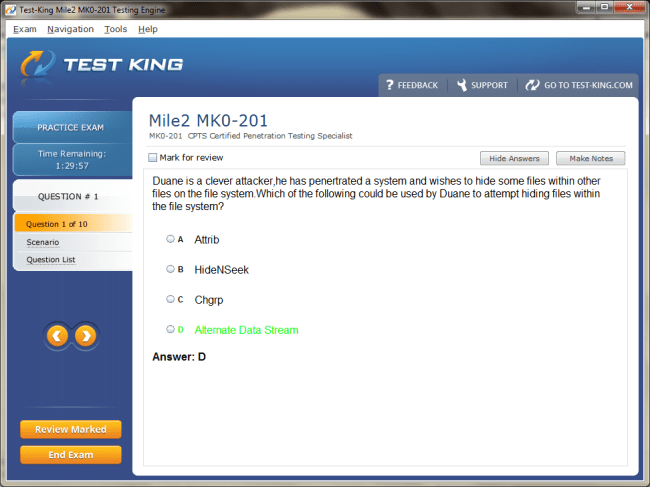
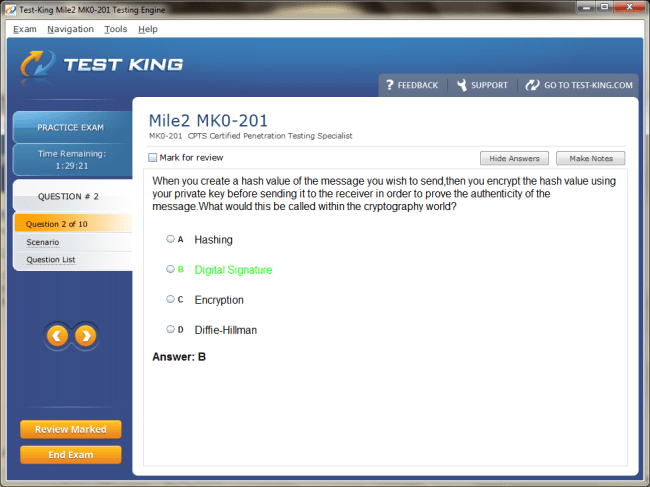
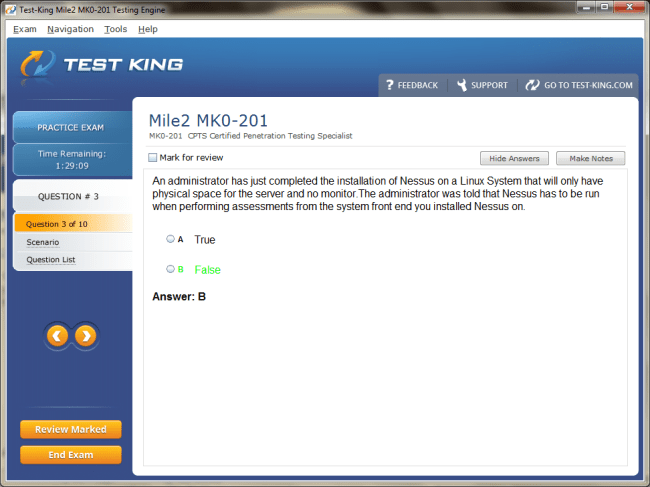
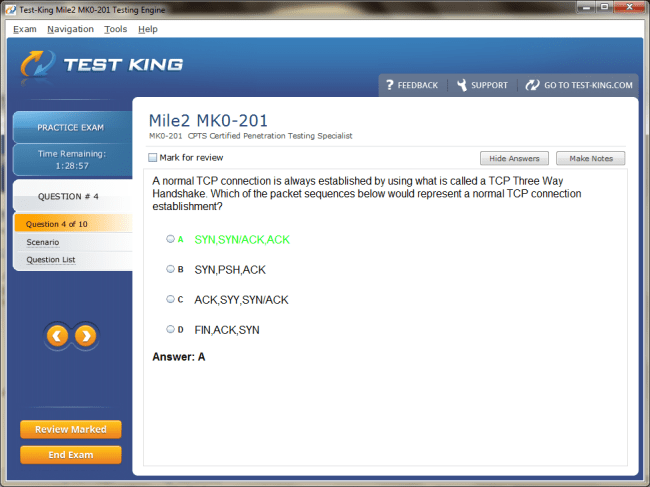
MK0-201 Exam Product Screenshots
Frequently Asked Questions
How can I get the products after purchase?
All products are available for download immediately from your Member's Area. Once you have made the payment, you will be transferred to Member's Area where you can login and download the products you have purchased to your computer.
How long can I use my product? Will it be valid forever?
Test-King products have a validity of 90 days from the date of purchase. This means that any updates to the products, including but not limited to new questions, or updates and changes by our editing team, will be automatically downloaded on to computer to make sure that you get latest exam prep materials during those 90 days.
Can I renew my product if when it's expired?
Yes, when the 90 days of your product validity are over, you have the option of renewing your expired products with a 30% discount. This can be done in your Member's Area.
Please note that you will not be able to use the product after it has expired if you don't renew it.
How often are the questions updated?
We always try to provide the latest pool of questions, Updates in the questions depend on the changes in actual pool of questions by different vendors. As soon as we know about the change in the exam question pool we try our best to update the products as fast as possible.
How many computers I can download Test-King software on?
You can download the Test-King products on the maximum number of 2 (two) computers or devices. If you need to use the software on more than two machines, you can purchase this option separately. Please email support@test-king.com if you need to use more than 5 (five) computers.
What is a PDF Version?
PDF Version is a pdf document of Questions & Answers product. The document file has standart .pdf format, which can be easily read by any pdf reader application like Adobe Acrobat Reader, Foxit Reader, OpenOffice, Google Docs and many others.
Can I purchase PDF Version without the Testing Engine?
PDF Version cannot be purchased separately. It is only available as an add-on to main Question & Answer Testing Engine product.
What operating systems are supported by your Testing Engine software?
Our testing engine is supported by Windows. Andriod and IOS software is currently under development.
Common Mistakes to Avoid When Preparing for the Mile2 CPTS (MK0-201) Exam
The Mile2 Certified Penetration Testing Specialist examination, also identified by the code MK0-201, is not an ordinary assessment of technical competence. It is an intricate exploration of the candidate’s capacity to simulate the mindset of a professional adversary, while maintaining a strong adherence to ethical and procedural discipline. The exam evaluates not only technical mastery but also cognitive structure, critical reasoning, and decision-making patterns under simulated cybersecurity conditions. Many aspirants falter in their preparation because they misjudge the essence of the CPTS framework, viewing it as merely a test of hacking tools or command-line syntax rather than a holistic validation of penetration testing methodology.
The True Nature of the Mile2 Certified Penetration Testing Specialist (CPTS) Exam
The CPTS curriculum is constructed around a philosophy of adversarial simulation, in which the penetration tester must emulate a sophisticated threat actor with meticulous strategy, persistence, and ethical restraint. Candidates often underestimate this conceptual foundation. They assume that rote memorization of commands or superficial practice in virtual labs will suffice. However, the examination expects a comprehensive understanding of reconnaissance, exploitation, post-exploitation, and documentation phases in a way that reflects real-world offensive security engagements. This means that the aspirant must internalize the logical flow of a penetration test — from initial scoping and legal compliance to final report articulation.
A frequent misstep involves disregarding the multi-layered cognitive demand of the MK0-201 exam. The CPTS test measures analytical interpretation rather than mechanical execution. The examinee is expected to exhibit fluency across a wide range of tools and platforms, including vulnerability scanners, exploitation frameworks, password auditing utilities, and network sniffers, while demonstrating discretion and strategic insight. The failure to connect theory with situational judgment creates a cognitive gap that often leads to poor performance. Those who succeed typically possess a balanced grasp of the underlying protocols, operating systems, scripting fundamentals, and the psychology of threat modeling.
The exam’s architecture intentionally mirrors the fluidity of live network engagements. The Mile2 CPTS assessment integrates theoretical questions with scenario-driven simulations. This requires the learner to translate abstract security principles into real-time operational reasoning. A candidate unprepared for this synthesis may find the test deceptively difficult. Therefore, a proper mindset toward CPTS preparation must go beyond superficial study habits and aim for conceptual assimilation, deep comprehension of methodologies, and reflective thinking aligned with the Mile2 ethical standard.
Misinterpreting the Core Framework of Penetration Testing Methodology
One of the most pervasive misjudgments made by learners preparing for the CPTS MK0-201 is the misunderstanding of the penetration testing methodology itself. Many participants treat the methodology as a fixed sequence of steps, while in reality, it is a dynamic and recursive process that requires adaptive reasoning. The Mile2 framework draws upon internationally recognized standards of ethical penetration testing such as reconnaissance, enumeration, exploitation, privilege escalation, post-exploitation, and reporting. However, its real challenge lies not in knowing these steps but in knowing how to transition between them with contextual awareness.
A large portion of candidates fail because they ignore the importance of pre-engagement interaction and scoping. Before any technical testing begins, the professional penetration tester must negotiate the boundaries of engagement, define the rules of authorization, and understand the client’s infrastructure landscape. Neglecting this foundational stage often translates to poor conceptual understanding during the exam. Mile2 expects candidates to think like responsible professionals who comprehend the legal implications of unauthorized testing.
Furthermore, misinterpreting the reconnaissance and enumeration phases often leads to flawed analysis. These early stages are not mere data collection exercises; they are intelligence-driven explorations designed to build a narrative of the target environment. Many learners practice commands without understanding their analytical purpose. For instance, knowing how to run a network mapper or vulnerability scanner is insufficient if the candidate cannot deduce potential attack surfaces, pivoting points, or privilege escalation vectors from the output.
Another subtle error occurs in how candidates treat the exploitation phase. Some become overly fascinated with finding a single exploit or tool that “works,” neglecting the deeper logic behind exploit selection and payload customization. The CPTS exam demands discernment: understanding why a specific vulnerability exists, how it can be chained with others, and what implications it holds for confidentiality, integrity, and availability. Over-reliance on automated tools without manual verification undermines the critical thinking that Mile2 emphasizes.
In addition, the post-exploitation and reporting stages are often underestimated. The CPTS assessment values clarity of documentation, accurate representation of evidence, and structured mitigation recommendations. Many examinees focus entirely on attack execution, forgetting that the ultimate goal of a penetration testing specialist is to communicate findings ethically and constructively. Without mastering this communicative dimension, even technically adept candidates may fail to meet the expected professional standard.
Neglecting Comprehensive Technical Practice and Tool Familiarity
A common weakness among candidates is insufficient engagement with practical tool ecosystems. The MK0-201 exam is not restricted to theoretical constructs; it expects tangible familiarity with industry-grade utilities and frameworks. A superficial acquaintance with graphical interfaces or limited exposure to a few common tools creates a fragile technical foundation. The real examination tests whether the aspirant can maneuver across diverse systems and interpret tool outputs accurately.
Many learners attempt to memorize command syntax without immersing themselves in real laboratory exercises. This is a significant error because the CPTS program was designed to evaluate experiential learning. The candidate must demonstrate the ability to configure, deploy, and troubleshoot various penetration testing utilities within controlled environments. Lacking this experiential dimension, the learner’s preparation remains purely abstract, which is inadequate for Mile2’s expectations.
The diversity of platforms used in professional penetration testing—ranging from Linux distributions like Kali or Parrot to Windows environments and networked devices—requires deep cross-system literacy. Candidates who restrict themselves to one environment struggle to adapt during scenario-based questions that reference unfamiliar system behaviors. Successful aspirants tend to cultivate versatility: they can interpret registry modifications, analyze packet captures, script custom payloads, and understand the impact of system patches.
Another frequent mistake involves disregarding updates in security tools. Cybersecurity technology evolves rapidly, and the Mile2 CPTS curriculum remains aligned with modern toolkits. If candidates practice with outdated versions, they may encounter discrepancies in functionality or interface during the exam’s practical simulations. To maintain relevance, learners should regularly engage with current repositories, patch notes, and changelogs to ensure technical precision.
The element of tool interpretation also poses challenges. Knowing how to initiate a scan is meaningless if the candidate cannot decode the significance of the output. CPTS assessors seek interpretive clarity—understanding whether a vulnerability rating indicates real exploitability or whether it represents a false positive within a given context. This analytical layer differentiates genuine specialists from surface-level enthusiasts.
Equally important is documentation during practice sessions. Maintaining a penetration testing diary that records configurations, command sequences, and observed behaviors can significantly reinforce memory retention and procedural awareness. Many aspirants neglect this reflective habit, resulting in fragmented understanding. A systematic approach to recording practical experiences strengthens both conceptual knowledge and examination readiness.
Overlooking Analytical Thinking and Scenario-Based Application
The Mile2 CPTS MK0-201 exam challenges not only technical proficiency but also interpretive intelligence. Candidates who rely solely on memorized definitions or pre-configured tool usage often fail to handle scenario-based challenges. The exam emphasizes reasoning through simulated attack paths, determining appropriate methodologies for varying environments, and selecting ethical courses of action in ambiguous contexts.
A prevalent mistake is neglecting the cultivation of analytical flexibility. Penetration testing is inherently investigative. It demands an ability to hypothesize, test, and revise assumptions dynamically. During CPTS assessments, learners are often presented with situations where multiple solutions appear plausible. The successful respondent distinguishes themselves by evaluating contextual variables—system architecture, user privileges, defense mechanisms, and legal scope—before executing a response. Those who skip analytical preparation usually default to mechanical habits that reveal cognitive rigidity.
Furthermore, a lack of exposure to case-based learning diminishes one’s problem-solving acuity. Real-world penetration testing involves interpreting ambiguous data, identifying indirect indicators of compromise, and formulating logical narratives of attack progression. Candidates should immerse themselves in digital forensics scenarios, vulnerability reports, and network simulations that compel inferential reasoning. By internalizing these patterns, they cultivate a mental discipline that aligns with Mile2’s expectations for cognitive rigor.
Language comprehension also influences analytical performance. The MK0-201 exam is articulated in technically precise yet nuanced English. Misreading a question or misinterpreting qualifiers such as “most appropriate,” “first step,” or “best remediation” can distort the response entirely. Therefore, developing attentive reading habits and parsing exam phrasing carefully is essential.
An additional oversight involves the underestimation of report analysis skills. CPTS candidates must be capable of dissecting sample penetration test reports, understanding the flow of evidence presentation, and correlating vulnerabilities with business impact. Analytical maturity manifests in the ability to contextualize technical findings within organizational risk frameworks. Ignoring this correlation leads to a superficial approach that fails to resonate with Mile2’s professional ethos.
Ignoring the Ethical and Legal Dimensions of the CPTS Framework
One of the cornerstones of the Mile2 Certified Penetration Testing Specialist certification is ethical integrity. Yet, a surprising number of examinees undervalue the legal and ethical dimensions embedded in the MK0-201 blueprint. The examination rigorously evaluates a candidate’s comprehension of legal compliance, responsible disclosure, and adherence to professional conduct standards. Many learners focus exclusively on offensive techniques, forgetting that the CPTS designation signifies not just technical capability but also moral accountability.
The most frequent ethical misstep is a casual attitude toward authorization boundaries. A true penetration testing specialist must possess an ingrained respect for scope definition, contractual limits, and client consent. Engaging in unsanctioned testing, even hypothetically, contradicts the Mile2 doctrine and demonstrates a flawed professional mindset. The CPTS exam implicitly assesses this awareness by presenting situational questions that test the candidate’s ability to distinguish between legitimate engagement and unethical intrusion.
Equally important is understanding the regulatory environment that governs cybersecurity activities. Concepts such as privacy law, intellectual property protection, and digital forensics procedures form part of the professional lexicon. Candidates unfamiliar with frameworks like GDPR or local data protection statutes may misjudge their responsibilities when handling sensitive information. In the Mile2 ethos, technical excellence devoid of legal discernment is incomplete.
Another dimension frequently overlooked is the principle of responsible disclosure. The CPTS program trains professionals to communicate vulnerabilities to authorized stakeholders in a structured and non-exploitative manner. Many aspirants fail to internalize this principle, assuming that discovery alone suffices. However, Mile2 emphasizes the ethical chain of custody for information, including evidence handling, communication protocols, and remediation guidance. Neglecting these standards reflects a partial understanding of the professional role.
In addition, ethical decision-making extends to social engineering simulations and human-centric testing. Candidates must understand psychological manipulation tactics not as ends in themselves but as controlled mechanisms to evaluate awareness within predefined ethical boundaries. Misuse or misrepresentation of such tactics in practice environments can suggest a deficiency in professional judgment. Thus, preparation for the CPTS MK0-201 requires reflection on one’s ethical disposition as much as on technical competence.
Underestimating Time Management and Cognitive Preparedness
Time mismanagement represents another critical weakness in CPTS exam preparation. The MK0-201 exam encompasses multifaceted question types that demand both analytical reflection and technical recall within limited time frames. Candidates often expend excessive minutes on a single complex scenario, leaving insufficient time for subsequent items. Proper preparation includes practicing under timed conditions to build cognitive endurance and pacing discipline.
Cognitive fatigue also undermines performance. The CPTS exam environment tests sustained concentration across diverse domains, from network security to exploit analysis. Candidates who fail to train their cognitive stamina through long practice sessions or mock tests experience mental depletion midway through the assessment. Developing endurance involves simulating exam conditions repeatedly until focused reasoning becomes habitual.
A further mistake involves neglecting rest, nutrition, and psychological conditioning. In high-stakes certifications such as Mile2 CPTS, mental clarity and emotional stability directly influence analytical accuracy. Anxiety often arises from unstructured preparation, irregular study intervals, and excessive dependency on last-minute revision. Structuring study cycles with deliberate intervals, incorporating brief physical activity, and maintaining hydration contribute to neurological efficiency.
Equally vital is understanding the rhythm of the exam itself. The CPTS MK0-201 assessment follows a balanced distribution of conceptual and practical items. Strategic pacing demands that candidates swiftly categorize each question by complexity and allocate time proportionally. Those who lack this metacognitive awareness often panic when encountering technical obstacles, thereby compromising performance across the remaining items.
Time management is also intellectual management. Effective scheduling of study modules ensures coverage of all topics, from reconnaissance methodologies to exploitation frameworks and report writing protocols. Many aspirants spend disproportionate time on offensive tools while ignoring documentation or risk assessment domains. Balanced scheduling enhances holistic readiness and mirrors the multidisciplinary expectations of Mile2.
Finally, psychological resilience forms an inseparable part of cognitive preparedness. The CPTS exam’s intricate phrasing and multifaceted scenarios are designed to challenge composure. Learners who train themselves to pause, re-evaluate, and adapt their reasoning under pressure perform consistently better. Developing this calm adaptability requires repeated exposure to simulation-based exercises and reflective debriefing after each attempt. The disciplined learner who integrates technical mastery with emotional steadiness ultimately exemplifies the spirit of the Certified Penetration Testing Specialist.
Misjudging the Depth of Knowledge Required for True CPTS Mastery
Among the recurring misconceptions faced by aspirants of the Mile2 Certified Penetration Testing Specialist examination is the failure to recognize the depth of intellectual commitment the MK0-201 exam demands. The CPTS credential is a professional validation of both technical dexterity and interpretive discernment, reflecting an individual’s capacity to comprehend complex network architectures, exploit vulnerabilities ethically, and report findings with impeccable clarity. Many candidates underestimate the intellectual expanse of the exam and confine their preparation to the superficial level of operational familiarity with tools. This shallow approach often manifests as fragmented comprehension, where knowledge exists in isolation but lacks contextual coherence. To master the CPTS blueprint, an aspirant must perceive cybersecurity not as a static discipline of commands and configurations, but as a dynamic epistemology of evolving threats, countermeasures, and methodologies that continuously reshape the ethical hacker’s craft.
A fundamental mistake observed among learners is the reliance on passive reading habits rather than immersive analytical study. Cybersecurity, particularly in the context of the CPTS certification, requires internalization through engagement, experimentation, and iterative reasoning. Reading study guides or watching tutorials without practical reinforcement yields temporary familiarity rather than lasting proficiency. The true essence of penetration testing lies in its experiential dimension, where each tool becomes an extension of analytical thought. The MK0-201 exam is deliberately structured to expose this deficiency; it demands the synthesis of learned theory into operational logic. Candidates who fail to develop this integrative skill often misinterpret the essence of the questions, mistaking descriptive familiarity for applicable understanding.
Another recurring error lies in disregarding the conceptual continuity that binds the diverse domains of penetration testing together. The CPTS examination encompasses network reconnaissance, vulnerability analysis, exploitation, privilege escalation, and report formulation. Yet, these are not independent silos. Each stage informs and enriches the next through a recursive feedback mechanism. For instance, reconnaissance insights influence vulnerability prioritization, while exploitation outcomes determine reporting focus. A learner who views these domains as isolated topics rather than an interconnected methodology misses the intellectual rhythm that governs professional penetration testing practice. True CPTS preparation requires perceiving this continuity as the logical spine of the discipline.
Candidates also frequently misconstrue the Mile2 CPTS framework as purely offensive in nature, neglecting the defensive and analytical subtleties embedded within. The examination does not merely test how efficiently one can compromise a target system; it evaluates the analytical consciousness with which vulnerabilities are identified, interpreted, and ethically managed. This dualistic perspective—attacker and defender simultaneously—is a hallmark of the CPTS ethos. The ethical hacker must embody precision, restraint, and moral accountability. Failing to cultivate this dual perspective reduces preparation to a mechanical exercise devoid of professional maturity.
An equally detrimental mistake involves neglecting the theoretical underpinnings of network communication. Many learners emphasize tool usage but lack an understanding of how network protocols, packet structures, and system processes interact. The MK0-201 examination frequently embeds its complexity within conceptual traps that test comprehension of protocol behavior under specific conditions. Without a strong grasp of how Transmission Control Protocol, Internet Protocol, or Domain Name System mechanics function at granular levels, candidates cannot accurately interpret anomalies or potential exploits presented during exam scenarios. Mile2 expects an intellectual fluency in these protocols that transcends memorization; it seeks interpretive mastery.
The neglect of scripting fundamentals further weakens many candidates. While CPTS does not require expert-level programming skills, it expects familiarity with scripting logic for automation, payload customization, and report generation. Aspirants who avoid scripting exercises limit their capacity to adapt tools to unconventional environments. In practical engagements, static toolsets rarely suffice; creativity through scripting becomes indispensable. Hence, the aspirant who approaches the CPTS examination without such adaptability reveals a significant lacuna in professional preparedness.
Equally problematic is the underestimation of documentation skills. Penetration testing is as much a communication discipline as it is a technical one. The Mile2 CPTS framework integrates the ethics of clear and responsible reporting as a professional obligation. Many technically adept candidates falter because their documentation lacks analytical depth or coherence. Reports that omit context, risk severity interpretation, or remediation advice demonstrate incomplete mastery. The CPTS examination intentionally evaluates this dimension to ensure that the certified specialist is capable not only of identifying vulnerabilities but also of articulating their implications to stakeholders in comprehensible, business-relevant language.
Cultural and linguistic nuances also influence exam readiness. The MK0-201 questions are composed with precision, often employing terminologies that carry layered meanings. Misinterpretation of such phrasing can lead to inaccurate responses even when the candidate possesses correct technical knowledge. Thus, cultivating linguistic attentiveness and analytical reading habits is crucial. The successful CPTS aspirant must train not merely as a technologist but as an interpreter of technical semantics.
A related oversight involves neglecting the psychological aspect of the testing experience. The MK0-201 exam, like real-world penetration testing operations, demands mental stamina, resilience, and emotional balance under cognitive pressure. Many candidates experience anxiety that disrupts logical reasoning, particularly during scenario-based items that require multi-step deduction. Effective preparation therefore encompasses psychological conditioning alongside technical rehearsal. Mental composure, patience, and reflective confidence distinguish the professional mindset that Mile2 endeavors to certify.
In addition to the intellectual and emotional dimensions, there exists a pedagogical error in how many candidates structure their learning journey. Unsystematic study patterns, absence of revision schedules, and overdependence on third-party notes often lead to uneven conceptual development. The CPTS curriculum is designed with progressive layering, where early modules establish the theoretical foundations necessary for advanced topics. Ignoring this progression produces gaps that later manifest as conceptual confusion. Therefore, disciplined study architecture—structured timelines, targeted revisions, and incremental testing—forms an essential component of effective CPTS preparation.
Moreover, the aspirant must cultivate critical awareness of emerging technologies and security paradigms that influence penetration testing methodologies. The MK0-201 exam, while structured around established frameworks, evolves in response to modern cybersecurity landscapes. Concepts such as cloud infrastructure penetration, IoT vulnerabilities, and container security have increasingly become relevant in Mile2 assessments. Candidates who rely solely on outdated resources risk encountering unfamiliar contexts during the examination. Maintaining academic curiosity through continuous learning and engagement with current cybersecurity discourse ensures alignment with Mile2’s evolving standards.
Another subtle yet significant mistake involves ignoring the collaborative dimension of cybersecurity practice. The CPTS credential symbolizes not only individual technical capability but also readiness to function within coordinated teams. Real-world penetration testing projects require communication, coordination, and ethical responsibility among multiple specialists. Candidates who prepare in isolation without engaging in peer learning or simulated teamwork environments often struggle to appreciate this professional dynamic. In contrast, learners who participate in forums, capture-the-flag competitions, or cooperative lab environments develop broader perspectives that enrich both technical and ethical judgment.
Misalignment between study material and exam blueprint constitutes another impediment. Some aspirants rely on generalized ethical hacking resources rather than focusing specifically on Mile2’s unique examination philosophy. The CPTS exam emphasizes methodical reasoning, professional conduct, and structured reporting more than mere exploit execution. Preparation materials that overlook these nuances may misdirect learning effort. Hence, aspirants should prioritize official Mile2 resources, recognized study frameworks, and authoritative cybersecurity literature that reflect the organization’s pedagogical intent.
The issue of cognitive overload must also be addressed. In the pursuit of thoroughness, many learners attempt to absorb excessive information without conceptual filtration. This leads to confusion and fatigue during examination scenarios where clarity of reasoning is paramount. Effective CPTS preparation involves selective assimilation—identifying core principles, understanding their applications, and discarding redundant detail. The aim is intellectual precision, not informational accumulation. Mile2’s examination design rewards strategic comprehension over encyclopedic memorization.
A further area of neglect involves understanding digital forensics correlation within penetration testing. While primarily offensive in nature, the CPTS program acknowledges the interconnectedness between exploitation and post-incident investigation. Professionals must understand how traces of penetration activities can be analyzed, attributed, or mitigated. Ignoring this connection can result in an incomplete grasp of operational integrity. By incorporating basic forensic principles—log analysis, evidence preservation, and attribution reasoning—into preparation, the candidate acquires a multidimensional competence that aligns with Mile2’s holistic vision of cybersecurity expertise.
The technical culture surrounding cybersecurity often encourages fascination with tool mastery, but the CPTS framework expects a more profound form of literacy—one that balances creativity with caution. Candidates frequently conflate innovation with recklessness, experimenting with live systems or unauthorized networks during practice. Such behavior contradicts the ethical precepts enshrined within the Mile2 doctrine. Proper preparation for the MK0-201 examination involves disciplined simulation within legal laboratory environments. The learner must internalize professional restraint, understanding that ethical hacking is defined not by boundary transgression but by the wisdom to respect them.
One of the most overlooked components of effective CPTS preparation is self-assessment. Many candidates study continuously but fail to periodically evaluate their progress against the exam objectives. This absence of diagnostic reflection leads to complacency or false confidence. Structured self-testing—through mock examinations, scenario reconstructions, or analytical journaling—provides insight into cognitive weaknesses. By identifying recurring patterns of error, the learner can recalibrate study focus. This metacognitive discipline is particularly important for MK0-201 because the examination’s complexity lies as much in interpretation as in content.
A final yet crucial area of misunderstanding involves the aspirant’s perception of professional identity. Achieving the Mile2 Certified Penetration Testing Specialist designation is not merely a credentialing milestone but a transformation of mindset. The CPTS professional operates within a global ecosystem of ethical hackers, auditors, and risk analysts dedicated to safeguarding digital integrity. Preparing for the exam without internalizing this sense of vocation results in a fragmented and utilitarian approach. The CPTS framework seeks individuals who perceive penetration testing as a disciplined craft guided by continuous learning, intellectual humility, and ethical precision.
The MK0-201 exam thus becomes not only a test of technical knowledge but a philosophical initiation into a community of cybersecurity custodians. It measures comprehension through ethical lenses, requiring candidates to balance technical aggressiveness with moral restraint. Each question, scenario, and simulated task within the examination carries embedded ethical expectations. To prepare effectively, the learner must cultivate mindfulness—an awareness of intent behind every action, command, and conclusion. This awareness transforms ordinary preparation into professional formation.
Ultimately, the gravest mistake one can make when preparing for the CPTS MK0-201 exam is to treat it as an obstacle rather than an opportunity for intellectual refinement. The process of preparation itself is a microcosm of professional evolution. It teaches discipline, precision, adaptability, and reflective practice—the same qualities that define excellence in real-world cybersecurity engagements. When approached with reverence for knowledge, respect for ethics, and dedication to accuracy, the aspirant’s journey through CPTS preparation becomes an enduring exercise in professional mastery, far exceeding the confines of examination success.
Failing to Integrate Real-World Penetration Testing Experience with Theoretical Learning
The preparation for the Mile2 Certified Penetration Testing Specialist examination demands an unusual blend of abstract reasoning and empirical experience. Many candidates approaching the MK0-201 examination commit the error of confining their study to textual or video-based resources, assuming that theoretical knowledge will suffice to navigate the intricate structure of the test. Yet, the CPTS credential is distinguished by its insistence on experiential comprehension—an expectation that the examinee not merely recall definitions but apply concepts dynamically to unpredictable cybersecurity contexts. The learner who approaches this qualification without tangible exposure to real or simulated penetration testing engagements deprives themselves of the practical intuition necessary for mastery.
To truly internalize the CPTS framework, one must treat theoretical study as a conceptual map and practical simulation as the territory it describes. When learners rely exclusively on manuals or tutorials, they inadvertently reduce complex operational principles into static abstractions. The MK0-201 exam is specifically constructed to expose this limitation, presenting scenarios that require translation of theoretical constructs into live analytical reasoning. For instance, it is insufficient to know the technical definition of reconnaissance or enumeration; one must demonstrate an ability to conduct these processes within varying infrastructural conditions while preserving ethical and legal boundaries. The successful candidate comprehends that penetration testing is a narrative act—each discovery influences the next decision, each vulnerability forms part of an evolving investigative storyline.
Many aspirants overlook the intellectual rhythm that defines genuine penetration testing practice. This rhythm consists of observation, hypothesis, experimentation, and reflection. The CPTS curriculum implicitly trains candidates to cultivate this cyclical cognition. However, when learners adopt mechanical repetition of commands without reflective analysis, they forfeit the developmental progression that transforms a technician into a specialist. Real-world testing requires sensitivity to environmental variance: network latency, misconfigured security devices, inconsistent firewall rules, and user behavior all interact to produce unique operational textures. Preparation that excludes this experiential diversity leaves the candidate conceptually rigid and unprepared for the adaptive demands of the MK0-201 assessment.
Equally detrimental is the habit of performing laboratory exercises without contextual reflection. Learners may spend hours experimenting within virtualized systems, yet rarely pause to examine the rationale underlying each technique. True Mile2-level competence emerges when every procedural action—scanning, exploitation, privilege escalation, or reporting—is consciously linked to a strategic purpose. The CPTS exam evaluates precisely this awareness: whether the candidate understands why a particular tool or command is executed, how it aligns with the rules of engagement, and what ethical implications accompany the decision. Without this cognitive traceability, technical practice becomes sterile repetition devoid of analytical depth.
Another persistent misconception is the belief that the MK0-201 exam rewards aggressiveness in exploiting vulnerabilities. The essence of the Certified Penetration Testing Specialist identity lies not in how forcefully one can compromise a system but in how prudently one manages each stage of the engagement. Real-world experience teaches that excessive exploitation can destabilize production environments or violate scope agreements. Candidates who have never operated under professional ethical constraints may treat the examination as a contest of technical bravado rather than disciplined simulation. Mile2’s evaluative design intentionally penalizes such misconceptions by embedding ethical decision points within technical scenarios. The candidate must demonstrate restraint, prioritizing procedural authorization and accurate documentation over unnecessary intrusion.
A further weakness among learners arises from limited exposure to interdisciplinary collaboration. In authentic penetration testing engagements, professionals rarely work in isolation; they interact with network administrators, risk assessors, and compliance officers. This collaborative matrix cultivates communicative clarity and situational awareness. Aspirants who prepare for the CPTS exam in solitary confinement often fail to develop this interpersonal literacy. They may understand exploitation sequences but lack the vocabulary to translate findings into managerial language or risk metrics. Since the MK0-201 examination evaluates report writing and interpretation, this communicative deficiency manifests as inadequate analytical expression. Those who have experienced team-based cybersecurity exercises, such as red-blue simulations or capture-the-flag environments, typically display superior conceptual elasticity during examination.
It is also common for candidates to misunderstand the relationship between offensive and defensive strategies. The CPTS blueprint insists that an ethical hacker comprehend defense mechanisms not merely to bypass them but to appreciate their functional intent. Without exposure to defensive technologies—firewalls, intrusion detection systems, endpoint protection—a learner’s understanding of offensive methods remains superficial. Practical experience in configuring or monitoring such systems cultivates empathy for the defender’s challenges, sharpening the ethical hacker’s analytical acuity. The MK0-201 exam reflects this symbiotic philosophy by integrating questions that require understanding of both attack vectors and mitigation techniques. Learners who have not internalized this dual perspective find themselves disoriented by the exam’s cross-disciplinary expectations.
Another obstacle arises from the absence of realistic scenario rehearsal. Penetration testing, by nature, unfolds unpredictably; every engagement presents novel topologies, access limitations, and human variables. Preparation that fails to simulate this uncertainty leaves the candidate unready for the cognitive improvisation demanded by the CPTS test. To bridge this gap, aspirants should participate in controlled simulations that mirror the complexity of corporate networks. Such exercises allow them to confront unexpected obstacles—misleading indicators, partial data, and environmental instability—and adapt accordingly. Through this adaptive practice, the learner cultivates the calm problem-solving temperament that distinguishes the seasoned professional from the novice technician.
An often ignored aspect of real-world preparation involves time discipline during engagements. The MK0-201 exam compresses multiple domains of expertise into a finite temporal structure. Candidates accustomed to open-ended laboratory experimentation struggle when constrained by examination timeframes. Practical fieldwork inherently teaches time prioritization: deciding which vulnerabilities warrant deeper exploration, which must be documented immediately, and which can be deferred. By simulating these constraints during study, aspirants develop an intuitive pacing strategy that translates directly into exam efficiency. The capacity to allocate cognitive resources judiciously is one of the defining characteristics of a Certified Penetration Testing Specialist.
Inadequate documentation practice continues to be a recurrent failing among learners. During genuine penetration testing assignments, meticulous note-keeping ensures reproducibility, legal defensibility, and ethical transparency. Many candidates, however, perceive documentation as an afterthought. This habit manifests in examination environments where they struggle to recall procedural sequences or justify analytical conclusions. The CPTS exam subtly tests this competency by requiring synthesis of information from multiple steps. Learners who have cultivated rigorous documentation habits—recording configurations, timestamps, and command outputs—approach the test with organized cognition. Their capacity to reconstruct analytical reasoning translates into coherent answers grounded in evidence rather than conjecture.
Beyond procedural experience, exposure to organizational culture enriches comprehension of cybersecurity operations. Real-world engagements reveal how business priorities, compliance requirements, and human behavior intersect with technical vulnerabilities. The Mile2 philosophy of ethical hacking acknowledges that penetration testing exists within socio-technical ecosystems, not isolated laboratories. Candidates who have interacted with real clients or participated in mock organizational audits understand the subtleties of risk communication, confidentiality obligations, and professional decorum. This maturity resonates throughout the MK0-201 evaluation, which seeks to identify individuals capable of representing cybersecurity as a disciplined consultancy rather than a technical spectacle.
A subtle yet consequential deficiency in many candidates’ preparation is the neglect of post-exploitation ethics. Once access is achieved, the penetration tester’s responsibility expands beyond technical exploration toward stewardship of sensitive data. Mishandling acquired information, even within simulated environments, signals a lack of ethical reflexivity. The CPTS exam measures awareness of these responsibilities by presenting situations in which discretion must outweigh curiosity. Practical exposure to environments containing confidential or proprietary data sensitizes the learner to these boundaries. Those who have internalized such professional restraint perform with calm precision rather than impulsive experimentation.
Equally important is the integration of continuous feedback mechanisms into one’s preparatory routine. Real-world testing environments operate under perpetual evolution; vulnerabilities change, tools advance, and threat actors innovate. Candidates who isolate their study from this dynamic feedback loop risk stagnation. The Mile2 philosophy encourages perpetual recalibration—evaluating previous assessments, analyzing errors, and refining methods. Learners who emulate this iterative model during preparation achieve deeper retention and conceptual flexibility. Static study patterns, by contrast, engender intellectual complacency. The CPTS examination rewards adaptability, not rote consistency.
Technological diversity represents another area frequently underestimated by examinees. Modern penetration testing extends across heterogeneous infrastructures: on-premises systems, virtualized environments, mobile platforms, and cloud architectures. Candidates whose experience remains confined to a single environment, such as a Linux-based lab, struggle when confronted with Windows-specific or cloud-oriented contexts in the exam. Real-world exposure to diverse environments cultivates systemic literacy—the ability to interpret security principles across varying configurations. Mile2’s MK0-201 blueprint implicitly tests this universality by integrating scenarios drawn from multiple technological domains. The candidate who has practiced across such variety develops a nuanced understanding of cross-platform vulnerabilities, authentication schemes, and privilege management.
Moreover, practical experience introduces the aspirant to the unpredictable human dimension of cybersecurity. Users, administrators, and policy makers each contribute variables that no automated tool can fully predict. Phishing susceptibility, weak password habits, and negligent configurations remain persistent vulnerabilities. Candidates who have participated in social engineering exercises or user awareness programs recognize these human factors as integral components of penetration testing. The MK0-201 examination acknowledges this interdisciplinary complexity, incorporating conceptual items that assess comprehension of psychological manipulation, ethical boundaries, and counter-awareness strategies. Without firsthand insight into these human behaviors, theoretical knowledge remains incomplete.
An often unspoken barrier to CPTS success is the disconnect between ethical intention and operational awareness. Real-world penetration testing experience refines ethical sensitivity by exposing professionals to tangible consequences of their actions. A single misstep—altering production data, interrupting service availability, or breaching confidentiality—can carry profound ramifications. Candidates who have not experienced such accountability may underestimate the gravity of ethical decision-making within the MK0-201 context. Mile2 evaluates not merely whether a candidate can identify vulnerabilities, but whether they can do so with discretion, legality, and moral responsibility. Experience transforms ethical compliance from a memorized doctrine into an instinctive habit.
Furthermore, field experience nurtures creative problem-solving. In real environments, tools often fail, permissions change, and access paths collapse unexpectedly. Adaptation becomes a survival skill. The CPTS exam intentionally incorporates ambiguities to simulate this unpredictability. Candidates who have faced similar challenges in practice approach these moments with composure and resourcefulness, whereas those limited to theoretical drills become immobilized. Exposure to practical contingencies—network interruptions, conflicting firewall rules, privilege revocations—builds resilience and cognitive elasticity that pure study cannot substitute.
It is also imperative to recognize that the MK0-201 assessment evaluates judgment, not mere knowledge. Real-world testing develops judgment through consequence awareness. Each decision in a live environment carries potential outcomes—some technical, others ethical or reputational. The aspirant who has engaged in supervised penetration tests develops an instinct for proportionality: determining how far to proceed, when to halt, and how to document responsibly. The absence of this instinct often leads to overconfidence or recklessness during exam scenarios. Mile2 seeks to certify professionals who act with deliberation, demonstrating both courage and caution.
In addition, genuine field practice fosters an appreciation for error analysis. Penetration testing rarely proceeds flawlessly; misconfigurations, false positives, and analytical oversights occur frequently. Reflecting upon these errors cultivates humility and methodological refinement. Learners who treat mistakes as learning catalysts progress steadily toward professional maturity. The CPTS exam mirrors this expectation by rewarding candidates who demonstrate reasoning transparency even when final outcomes are imperfect. In contrast, those who conceal uncertainty or fabricate certainty reveal a lack of authentic experiential grounding.
Another factor frequently underestimated is the importance of environmental awareness. In real engagements, contextual factors such as network topology, business continuity requirements, and regulatory compliance shape every decision. The Mile2 framework demands comprehension of these interdependencies. An aspirant who practices solely within static virtual environments may never confront the constraints imposed by production realities. Understanding how technical actions intersect with organizational priorities allows the candidate to approach MK0-201 questions with holistic reasoning, integrating technological, managerial, and ethical dimensions seamlessly.
Finally, the learner must embrace continuous evolution as the defining ethos of cybersecurity professionalism. Real-world exposure reveals the transience of mastery: today’s exploit becomes tomorrow’s obsolete artifact. The CPTS certification embodies this dynamic equilibrium, certifying not finality but readiness for perpetual learning. Candidates who anchor their preparation in static content fail to embody the spirit of adaptability that Mile2 prizes. True preparation involves cultivating curiosity, engaging with threat intelligence communities, experimenting with emerging technologies, and maintaining humility before the endless complexity of digital systems.
In essence, neglecting real-world penetration testing experience transforms CPTS preparation into a purely theoretical exercise devoid of vitality. The MK0-201 examination, by contrast, rewards living knowledge—knowledge forged in experimentation, reflection, and ethical awareness. Those who immerse themselves in authentic practice develop a multifaceted intelligence that transcends rote memorization. Their understanding becomes kinetic, responsive, and self-correcting. Through deliberate engagement with both the technical and human realities of cybersecurity, the aspirant ascends beyond mechanical proficiency toward the intellectual composure that defines a Certified Penetration Testing Specialist in the truest Mile2 tradition.
Overreliance on Memorization and the Absence of Strategic Understanding
A prominent difficulty among those preparing for the Mile2 Certified Penetration Testing Specialist examination lies in the excessive dependence on memorization at the expense of strategic comprehension. The MK0-201 exam, being a complex and intellectually demanding certification, transcends the boundaries of rote recall. It measures not how many commands, tools, or definitions a learner can repeat from memory, but how effectively these can be synthesized into cohesive analytical frameworks. Many aspirants fall into the illusion that success lies in stockpiling vast amounts of technical data. They create elaborate flashcards, rehearse tool syntax, and commit penetration testing steps to memory without developing the intuitive reasoning that binds these elements into meaningful action. Such a superficial approach fails to meet the cognitive expectations of the CPTS framework, which values applied intelligence over mechanical retention.
The architecture of the CPTS MK0-201 examination embodies an intricate design that compels the candidate to think like an adversary yet act within the ethical parameters of a professional cybersecurity consultant. This duality cannot be mastered through repetition alone. True understanding emerges when the learner appreciates the logic that unites reconnaissance, exploitation, escalation, and reporting as interdependent components of a unified methodology. Each activity within penetration testing is not an isolated task but a deliberate movement within a structured engagement cycle. The professional tester must comprehend when to pivot, when to persist, and when to retreat. Memorization cannot cultivate this discernment; only strategic understanding grounded in practice and reflection can achieve it.
One of the recurrent mistakes in CPTS preparation involves the tendency to equate knowledge accumulation with mastery. Candidates often immerse themselves in expansive study materials, gathering numerous resources that reiterate the same content in varied forms. This creates an illusion of progress, yet their grasp remains fragile. The Mile2 examination exposes this fragility through scenario-driven questions that require synthesis, prioritization, and judgment. When faced with a question that intertwines multiple concepts, the memorization-dependent learner struggles to navigate the cognitive intersections between them. In contrast, the candidate trained in strategic reasoning perceives patterns, connects theoretical insights with operational implications, and responds with coherence rather than guesswork.
Another cognitive misstep lies in the misinterpretation of tool proficiency as evidence of conceptual mastery. Many learners spend inordinate time mastering command-line syntax or exploring the interfaces of scanning and exploitation tools, believing that this mechanical familiarity ensures success. However, the MK0-201 examination often evaluates whether the candidate comprehends the rationale behind tool selection and understands the environmental factors influencing tool effectiveness. Knowing how to execute a vulnerability scan is insufficient without grasping why specific ports, protocols, or configurations produce certain results. The CPTS framework rewards reasoning that demonstrates interpretive depth. The aspirant who studies merely the surface-level mechanics of utilities, rather than the underlying network logic that governs their operation, remains ill-prepared for the intellectual rigor of the assessment.
Another error frequently observed is the lack of conceptual layering in study routines. Penetration testing, by its very nature, is hierarchical in structure. Foundational knowledge—such as system architecture, network protocols, and operating system mechanisms—forms the substrate upon which advanced exploitation and analytical techniques are built. Learners who memorize advanced procedures without thoroughly understanding these foundations inevitably encounter conceptual dissonance during the exam. They may recall a command sequence but fail to predict its consequences when applied within a specific context. Strategic understanding requires constructing mental scaffolding that connects principles with practices, creating a durable framework capable of supporting adaptive reasoning.
The Mile2 Certified Penetration Testing Specialist examination was designed to test strategic cognition through situational fluidity. Questions may not always conform to predictable patterns. Some items combine ethical considerations with technical scenarios, while others demand the integration of multiple domains such as network forensics, access control, and privilege escalation. Candidates who have relied purely on memorization are frequently disoriented by this multidimensional complexity. In contrast, those who cultivated adaptive thinking interpret these intersections naturally, perceiving them as authentic reflections of real-world cybersecurity engagements.
Misinterpreting the function of learning materials is another widespread issue. Learners often treat official study guides as repositories of answers rather than frameworks for exploration. The purpose of the CPTS materials is to instill conceptual literacy—the ability to translate principles into effective methodologies. When candidates read passively, focusing solely on reproducing textual content, they deprive themselves of analytical enrichment. Active engagement with materials, through note synthesis, diagrammatic reasoning, and reflective questioning, transforms study from memorization into understanding. The MK0-201 exam indirectly rewards this intellectual engagement, as its questions often require inference rather than direct recall.
Overreliance on memorization also hampers adaptability when encountering novel technologies. The landscape of cybersecurity evolves continuously, introducing new protocols, encryption methods, and attack surfaces. A candidate trained merely to memorize static patterns of information struggles to adjust when confronted with questions referencing modern contexts such as cloud infrastructure penetration or containerized environments. The CPTS examination reflects this technological evolution. Only those who have internalized core principles—such as threat modeling, vulnerability chaining, and systematic risk analysis—can extrapolate their knowledge into unfamiliar domains. Thus, the Mile2 philosophy inherently discourages memorization and advocates strategic fluidity.
Another dimension of this issue is the psychological dependency on predictability. Memorization creates comfort through repetition, but strategic understanding thrives on ambiguity. The MK0-201 exam deliberately incorporates ambiguity to evaluate judgment under uncertainty. Candidates who expect clear-cut scenarios often falter when presented with partially defined problems requiring assumption management. The aspirant who has cultivated strategic insight, however, interprets uncertainty as an analytical signal rather than an obstacle. This mental resilience, rooted in comprehension rather than recall, defines the intellectual maturity expected of a Certified Penetration Testing Specialist.
Additionally, excessive memorization undermines ethical reasoning. Ethics in cybersecurity cannot be reduced to a checklist of dos and don’ts; it involves situational judgment shaped by awareness of consequence and intent. When candidates memorize ethical rules without internalizing their philosophical rationale, they struggle to apply them contextually during the exam. The CPTS framework evaluates ethical reasoning through scenarios that blur the boundaries between legality, professionalism, and technical opportunity. A learner who merely repeats ethical slogans cannot demonstrate moral discernment. Strategic understanding requires recognizing the ethical dimension as an intrinsic part of every technical decision.
Cognitive fatigue also becomes a byproduct of memorization-heavy preparation. Attempting to store extensive datasets of information without understanding creates mental overload and reduces retention efficiency. Learners may perform well in short-term recall exercises yet fail to reproduce insights after a few days. Strategic comprehension, conversely, fosters longevity of memory because it embeds information within conceptual meaning. The MK0-201 exam’s structure, which integrates sequential reasoning across multiple domains, naturally aligns with those whose preparation methods emphasize comprehension over accumulation.
The neglect of metacognition further compounds this problem. Metacognition refers to the awareness and regulation of one’s cognitive processes—knowing how one learns, how one forgets, and how one retrieves information. Candidates who memorize without reflection on their learning patterns cannot identify their weaknesses or recalibrate their methods. Effective CPTS preparation involves constant self-assessment, iterative revision, and adaptive strategy. Memorization precludes this because it treats learning as linear input rather than dynamic refinement. The MK0-201 examination rewards those who exhibit conscious control over their reasoning, demonstrating awareness of decision-making processes under constrained conditions.
Furthermore, reliance on memorization weakens creative problem-solving capacity. Penetration testing frequently demands improvisation: when one vector fails, another must be conceived. The CPTS exam mirrors this reality by embedding questions that require inventive synthesis of concepts. Candidates accustomed to memorized pathways struggle when familiar commands or vulnerabilities prove irrelevant. Strategic learners, by contrast, perceive every obstacle as a stimulus for conceptual innovation. They can reconstruct methodologies based on underlying logic rather than fixed procedure, exhibiting the adaptability that distinguishes the true professional from the formulaic practitioner.
A related issue is the superficial engagement with case studies and past scenarios. Many candidates read sample penetration testing reports or previous examination analyses merely to memorize details rather than to extract interpretive insights. Each case study in CPTS learning materials represents a microcosm of strategic thinking. The goal is to observe how decisions evolve, how constraints shape behavior, and how ethical awareness influences outcomes. Treating such examples as memorization targets negates their instructional purpose. The Mile2 approach to professional formation seeks reflective assimilation—understanding why an expert acted as they did, not just what they did.
The absence of interdisciplinary curiosity also stems from overreliance on memory. Candidates who memorize narrowly defined cybersecurity content seldom explore related disciplines such as psychology, risk management, or law. Yet, the CPTS exam implicitly evaluates the candidate’s capacity to interpret cybersecurity not as an isolated craft but as a dimension of larger organizational ecosystems. Strategic understanding emerges when the learner integrates insights from these adjacent domains, forming a panoramic vision of digital defense and offense. Without this integrative mindset, the aspirant’s reasoning remains confined to technical minutiae, insufficient for the MK0-201’s holistic evaluation.
Another subtle but critical repercussion of memorization is the suppression of ethical autonomy. When individuals rely on prescribed answers, they become dependent on authority rather than judgment. The Mile2 philosophy emphasizes self-governing professionalism—where the Certified Penetration Testing Specialist acts with moral clarity independent of external direction. Memorization trains obedience; understanding cultivates discernment. The CPTS exam measures this independence through situational items where no singular “correct” answer exists. The ethical hacker must justify choices through reasoning rather than citation. Those who lack this internal compass often resort to guesswork, betraying their dependence on rote conditioning.
Additionally, memorization without practice erodes confidence during real engagement simulations. The CPTS MK0-201 exam may introduce scenarios requiring immediate reasoning without visible cues. Learners who have internalized principles respond fluidly, while those who rely on memorized answers experience hesitation and doubt. Confidence rooted in comprehension is stable; that rooted in recall is brittle. Mile2 designed its examination not to intimidate but to validate readiness for professional unpredictability. Only through strategic learning can a candidate exhibit composure under analytical stress.
It is also important to consider the pedagogical context of Mile2 training. The organization’s educational framework emphasizes outcome-based learning, where demonstration of applied understanding outweighs the ability to reproduce definitions. Candidates misaligned with this philosophy misinterpret instructional objectives, focusing on content coverage rather than capability development. Effective learners align their preparation with this ethos by continuously applying learned material in simulated penetration tests, ethical hacking challenges, and documentation exercises. Each application reinforces comprehension, transforming abstract knowledge into embodied competence.
Finally, the psychological comfort derived from memorization must be confronted. Many learners subconsciously prefer memorization because it offers a tangible sense of progress—each fact learned feels like an achievement. However, this comfort is deceptive. Strategic comprehension demands discomfort, uncertainty, and reflection, conditions that mirror the intellectual rigor of the MK0-201 exam itself. Growth in cybersecurity expertise arises from confronting confusion, analyzing mistakes, and reconstructing understanding through persistent inquiry. Mile2’s examination philosophy mirrors this transformative journey. The Certified Penetration Testing Specialist is not expected to know everything by memory but to know how to think through anything.
Thus, the reliance on memorization stands as one of the most formidable obstacles in the path toward CPTS success. It undermines flexibility, suppresses creativity, distorts ethics, and weakens retention. The MK0-201 exam is a crucible for judgment, synthesis, and applied reasoning. The aspirant who abandons mechanical repetition in favor of strategic cognition approaches the test not as a recitation but as a demonstration of professional intellect. The path to certification lies not in remembering what others have said but in understanding why it matters and how it operates in the unpredictable, ever-evolving domain of cybersecurity.
Mismanagement of Practical Application and the Failure to Internalize Experiential Learning
Among the many intellectual obstacles encountered by candidates pursuing the Mile2 Certified Penetration Testing Specialist credential, the most profound lies in their inability to balance theoretical comprehension with authentic practical application. The MK0-201 exam, unlike many conventional certification tests, does not reward passive familiarity. It demands active engagement with real-world penetration testing methodologies, tools, and analytical frameworks. Yet, numerous learners confine their preparation to abstract study, under the illusion that conceptual awareness is a sufficient surrogate for hands-on proficiency. This fundamental misalignment between understanding and execution has become one of the most pervasive missteps in CPTS preparation.
Practical immersion forms the cornerstone of cybersecurity competence. Every theoretical construct within the Mile2 framework is designed to culminate in demonstrable skill. Concepts such as reconnaissance, enumeration, exploitation, and post-exploitation require tactile familiarity that cannot be simulated solely through reading. Unfortunately, many aspirants perceive practice as a secondary endeavor, undertaken only after mastering theory. This hierarchical misunderstanding prevents them from achieving the intuitive synergy that characterizes professional penetration testing. The CPTS examination, in its intricate design, is structured to expose precisely this gap—its situational questions and case-based items reward those who have internalized experience, not those who have memorized procedure.
A recurrent error among candidates involves the disproportionate emphasis on tool learning over methodological comprehension. It is tempting to believe that mastery of utilities like Nmap, Metasploit, or Burp Suite equates to readiness. However, the MK0-201 assessment probes not the candidate’s ability to execute tools mechanically, but their capacity to interpret, adapt, and innovate within unfamiliar contexts. Each tool represents merely a means to enact a strategic principle—identification, exploitation, validation, and reporting. Without understanding these underlying principles, tool proficiency becomes hollow performance. The CPTS professional must cultivate analytical literacy: the capacity to infer causality, to trace vulnerabilities back to systemic logic, and to articulate these findings in a coherent evaluative manner.
Many aspirants also underestimate the importance of structured laboratory environments in their preparation. Effective CPTS readiness depends on the consistent recreation of controlled testing conditions that mirror authentic security ecosystems. Constructing a virtual network, deploying intentionally vulnerable systems, and simulating adversarial behaviors nurture the cognitive agility necessary to succeed in the examination. Some learners rely exclusively on theoretical labs or watch others perform demonstrations, never engaging directly with the complexities of live configuration. This passive observation fosters an illusion of competence, yet during the exam, when hypothetical environments are presented, the lack of tactile confidence becomes evident. The Mile2 examination philosophy emphasizes practice as the crucible of understanding—only through repeated experimentation can the aspirant develop both precision and adaptability.
Another critical oversight is the neglect of documentation during practice. Candidates often engage in unstructured experimentation, failing to record their processes, outcomes, and reflections. The CPTS framework regards documentation not as an administrative burden but as an intellectual discipline. Through documentation, learners refine analytical reasoning, identify recurrent errors, and construct personalized methodologies. It transforms disorganized trial into deliberate practice. Moreover, Mile2’s ethical emphasis mandates traceability and accountability—qualities inherently demonstrated through comprehensive documentation. Thus, failure to integrate systematic record-keeping into training not only weakens exam performance but undermines the professional identity that CPTS certification seeks to cultivate.
The mismanagement of time within practical exercises also represents a recurrent deficiency. Many learners approach practice sessions with the same rigidity as theoretical study, allotting fixed durations for each concept. However, practical mastery unfolds nonlinearly. Some vulnerabilities demand hours of observation, repeated attempts, and cross-referencing before comprehension emerges. Those who rush the process to maintain schedules compromise the depth of learning. The MK0-201 exam subtly evaluates patience, persistence, and the ability to operate under uncertain temporal constraints. Candidates who train with artificial urgency often falter when the examination presents scenarios requiring extended analysis or delayed insight. Thus, effective preparation involves developing an internal tempo that harmonizes deliberation with decisiveness.
Neglecting to correlate practice with theoretical frameworks constitutes another detrimental behavior. Practical work divorced from conceptual grounding degenerates into mechanical repetition. Conversely, theory without experimentation remains sterile. The CPTS philosophy insists on their fusion. Each command executed, vulnerability exploited, or report composed should be accompanied by reflection on its conceptual foundation—why it works, how it interacts with network logic, and what ethical implications it carries. Learners who maintain this bidirectional awareness cultivate not only proficiency but intellectual coherence. The MK0-201 exam’s design mirrors this relationship, weaving technical execution with analytical interpretation.
Many aspirants also overlook the significance of failure within the learning continuum. Practical exercises often lead to frustration, particularly when exploits malfunction or expected results do not materialize. Candidates driven by perfectionism may abandon exercises prematurely, perceiving failure as regression. Yet, within Mile2’s pedagogical ethos, error constitutes an essential learning vector. Each misconfiguration, unsuccessful scan, or flawed payload represents a portal to deeper comprehension. Reflecting upon failure sharpens diagnostic reasoning and nurtures the humility essential to cybersecurity ethics. Those who interpret setbacks as discovery rather than defeat develop resilience—a quality indispensable not only for the CPTS exam but for real-world penetration engagements.
Another persistent misunderstanding lies in the disregard for operational context. Penetration testing does not occur in isolation but within environments constrained by policy, compliance, and organizational architecture. Candidates who practice exclusively in synthetic or idealized conditions fail to appreciate the pragmatic limitations that influence professional testing. The MK0-201 exam integrates contextual variables—system diversity, access permissions, and ethical boundaries—that challenge the candidate to adapt methodology to circumstance. Successful aspirants recognize that technical prowess must coexist with situational awareness. They train not only for execution but for judgment under constraint, developing a professional sensitivity that distinguishes ethical hackers from mere exploit technicians.
Equally concerning is the absence of collaboration during practical preparation. Many learners pursue solitary study, assuming cybersecurity mastery to be an individual endeavor. In reality, penetration testing is inherently collaborative, involving cross-functional communication with analysts, administrators, and legal advisors. Mile2’s educational philosophy reflects this reality by embedding professional communication into the CPTS learning objectives. Engaging with peers during practice sessions fosters dialogue, exposes blind spots, and stimulates critical thinking. Moreover, articulating findings to others reinforces understanding through expression. Candidates who isolate themselves from collaborative feedback risk developing tunnel vision, an intellectual rigidity that undermines performance during scenario-based examination items requiring multidimensional reasoning.
A subtle yet consequential misjudgment involves underestimating the psychological rigor of applied practice. Real-time penetration testing often induces cognitive fatigue and emotional tension. The MK0-201 examination, with its intricate situational constructs, evokes similar pressures. Candidates unaccustomed to sustained problem-solving under uncertainty may experience stress that disrupts logical reasoning. Therefore, practical training must include exposure to sustained analytical effort. Practicing within time-bound simulations, engaging in capture-the-flag challenges, and replicating multi-layered attack chains develop not only technical proficiency but also emotional endurance. This endurance enables composure under exam conditions, a factor frequently overlooked yet critical to success.
A further misstep relates to the incomplete understanding of tool output interpretation. Many learners assume that generating reports from automated scanners or frameworks completes the analysis. However, Mile2’s CPTS program emphasizes human interpretation—the capacity to differentiate between genuine vulnerabilities, false positives, and environmental anomalies. Automation supports testing, but it cannot replace analytical discernment. Candidates who depend solely on automated outcomes without understanding the logic behind detection lose credibility and score poorly in evaluative scenarios requiring interpretive reasoning. The exam seeks evidence of human cognition operating above the machine layer, affirming the ethical hacker’s role as an intelligent analyst rather than a passive operator.
Another deficiency stems from the failure to contextualize findings within risk frameworks. During practice, candidates often focus on identifying vulnerabilities without assessing their severity, exploitability, or business impact. The CPTS methodology demands that every technical observation be mapped to its organizational consequence. Mile2’s approach integrates risk-based analysis as a determinant of professionalism. The MK0-201 exam mirrors this by embedding evaluative questions that test not only detection but prioritization. Learners who practice without developing this evaluative mindset remain technically competent yet strategically incomplete. Understanding that cybersecurity operates within business ecosystems transforms penetration testing from a mechanical act into an instrument of governance and resilience.
Neglecting the ethical dimension during practice further weakens CPTS preparation. Practical exercises must be conducted within lawful and controlled environments, respecting data privacy and intellectual property. Candidates who practice indiscriminately, scanning unauthorized systems or exploiting public servers, compromise not only legal boundaries but the ethical integrity Mile2 certification represents. The MK0-201 exam embeds this ethical awareness into its design, evaluating not only technical decisions but the moral reasoning that underpins them. Training ethically cultivates reflexive responsibility—the instinct to act with caution and respect even when unsupervised. Without this cultivated restraint, technical skill becomes professionally hazardous.
Additionally, the absence of iterative review within practical learning hinders retention. Candidates often progress from one exercise to the next without revisiting earlier ones, assuming that repetition is redundant. However, mastery emerges through recursive engagement. Revisiting previous tasks with newly acquired insight reveals deeper layers of understanding. The CPTS framework, grounded in cumulative learning, rewards this recursive habit. The MK0-201 examination frequently revisits foundational principles in advanced contexts, testing whether the learner can reinterpret familiar concepts through new perspectives. Hence, continual review converts static knowledge into dynamic expertise.
A considerable portion of aspirants also fail to integrate reporting practice into their hands-on preparation. Penetration testing culminates not in exploitation but in articulation—the ability to convey findings to both technical and non-technical stakeholders. The MK0-201 exam measures this capacity by presenting scenarios that demand structured explanation of complex vulnerabilities. Candidates who neglect report writing during training face difficulty translating analytical insight into coherent expression. Practicing concise, structured, and ethically sound reporting transforms raw technical skill into professional communication. This articulation becomes the definitive marker separating a Certified Penetration Testing Specialist from an unrefined technician.
The underappreciation of simulation diversity represents another critical shortcoming. Many learners confine their practice to a narrow range of scenarios—primarily web application testing or basic network exploitation. However, the CPTS exam extends into areas such as wireless assessment, privilege escalation, and operating system security. Without exposure to this diversity, the candidate’s competence remains incomplete. Practicing across varied platforms, including Windows, Linux, and cloud infrastructures, ensures a multidimensional skill set. Moreover, it nurtures adaptability, a trait Mile2 regards as essential to cybersecurity excellence.
An additional cognitive limitation appears in the form of task compartmentalization. Some aspirants isolate different domains of study—networking, scripting, cryptography, or operating systems—treating them as discrete topics. Yet, the CPTS framework is integrative by design. Real penetration testing involves simultaneous interplay among these domains. A vulnerability in a web application may depend on misconfigured network permissions, while privilege escalation could hinge on cryptographic weaknesses. Practicing in isolation prevents the learner from perceiving these correlations. Effective preparation, therefore, demands the synthesis of interdisciplinary awareness where each technical act resonates with systemic implication.
The intellectual culture of cybersecurity sometimes glorifies rapid results, celebrating exploit discovery rather than understanding. This culture misguides learners preparing for the CPTS exam, leading them to prioritize speed over substance. The MK0-201 assessment, however, values discernment and accuracy. Mile2’s evaluative philosophy recognizes that a deliberate, methodical approach reflects professional maturity. Thus, learners should cultivate reflective practice—slowing down to question assumptions, verify findings, and contemplate implications. Such deliberate pacing refines both precision and credibility, traits indispensable for CPTS certification.
Finally, the absence of mentorship during preparation amplifies the aforementioned deficiencies. Cybersecurity, being an experiential craft, thrives on guided learning. Interaction with experienced practitioners accelerates conceptual refinement, introduces nuanced techniques, and provides corrective feedback beyond the reach of textbooks. Candidates who pursue solitary preparation often misinterpret concepts or develop inefficient habits. Mile2’s learning model implicitly endorses mentorship, recognizing it as a conduit for ethical formation and professional alignment. Engaging with mentors transforms preparation from mechanical study into intellectual apprenticeship.
Conclusion
The failure to internalize practical application stands as one of the most profound impediments to success in the Mile2 Certified Penetration Testing Specialist examination. The MK0-201 assessment does not simply evaluate recollection; it measures reasoning in motion—the translation of abstract theory into strategic execution. Candidates who confine their preparation to theoretical review deprive themselves of the experiential intuition that distinguishes the professional ethical hacker. Effective CPTS preparation demands the harmonious integration of conceptual understanding, tactile experimentation, and ethical mindfulness. Through disciplined practice, reflective documentation, and iterative refinement, learners transform knowledge into wisdom and execution into artistry.
Mastery of the CPTS framework arises not from memorizing the sequence of steps but from perceiving the interdependence of principles that govern digital security. The aspirant who learns through doing, who questions through experimenting, and who reflects through documenting transcends the boundaries of exam preparation. They become the embodiment of Mile2’s philosophy—a professional who not only identifies vulnerabilities but understands their origins, implications, and ethical dimensions. In this convergence of intellect, practice, and morality lies the true preparation for the MK0-201 examination and, beyond it, the enduring identity of a Certified Penetration Testing Specialist.