Understanding TCP/IP
Exam: Microsoft 70-642 - Windows Server 2008 Network Infrastructure, Configuring
TCP/IP is a combination of two sets of protocols, namely TCP and IP. These protocols are based on a four layer TCP/IP model as illustrated in the figure below
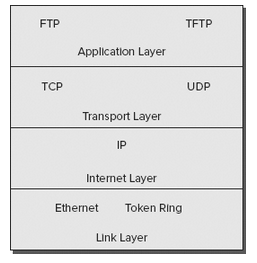
Figure 1: TCP/IP Model Layers
The article discusses the TCP/IP Model in detail.
Four Layers of TCP/IP
The four layers of the TCP/IP are -
- Application Layer: It is the layer where protocol stack resides and it includes applications like FTP (File Transfer Protocol), TFTP (Trivial File Transfer Protocol), SMTP (Simple Mail Transfer Protocol) and HTTP (Hypertext Transfer Protocol)
- Transport Layer: In this layer reside the two Transport layer protocols namely the TCP and the UDP. TCP being a connection oriented protocol and hence delivery is assured. UDP being a connectionless protocol undertakes all efforts to deliver the message.
- Internet Layer: The IP resides in this layer. It is a connectionless protocol relying on the upper layer for a guaranteed delivery. ARP -Address Resolution Protocol residing in this layer turns the IP address to a MAC (Media Access Control) address. All upper and lower layers travel through the IP protocol.
- Link Layer: Ethernet and Token Ring are data link protocols that reside in the Link layer also known as the Network Access Layer.
Communication between TCP/IP Layers
In case an application like an FTP application is called, the application travels down through the layers and retrieval of TCP takes place. TCP then sets up a connection with IP protocol and enters the network through the Link Layer. This being a connection oriented protocol, delivery of the message is guaranteed.
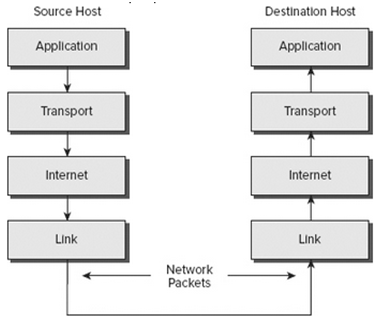
Figure2: TCP/IP Process
Port Numbers
TCP and UDP are dependent on port numbers that have been assigned by IANA - Internet Assigned Numbers Authority for forwarding packets to the proper application process. Port numbers are 16 bit integers that form a portion of the message header.
The application software process with which the packet is to be associated is identified by them. The most commonly used port numbers are listed in the table below. The full list is available at www.iana.org. It is important for an administrator to know the important port numbers that block or allow specific protocols.
| Port Number | Description |
| 20 | FTP data |
| 21 | FTP control |
| 23 | Telnet |
| 25 | Simple Mail Transfer Protocol (SMTP) |
| 53 | Domain Name System (DNS) |
| 80 | Hypertext Transfer Protocol (HTTP), Web |
| 88 | Kerberos |
| 110 | Post Office Protocol v. 3 (POP3) |
| 443 | Secure HTTP (HTTPS) |
Figure 3: Common Port Numbers
The above table shows few common and popular port numbers so that they can be memorized for ease.


