Exam Code: ISFS
Exam Name: Information Security Foundation (based on ISO/IEC 27002) (EX0-105)
Certification Provider: Exin
Corresponding Certification: Information Security Foundation (based on ISO/IEC 27002)
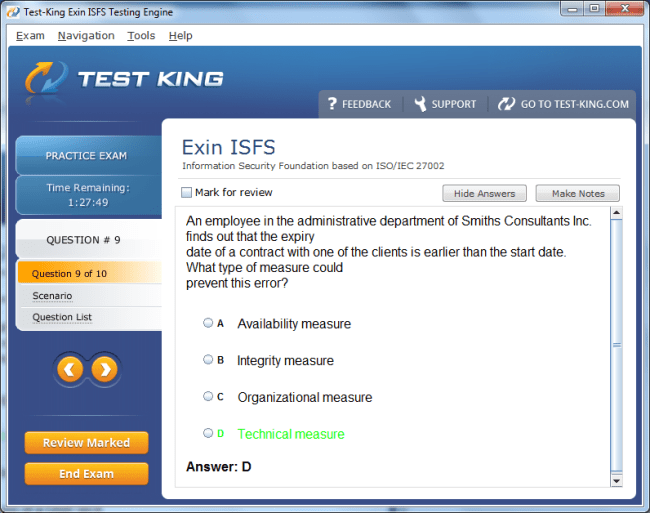
ISFS Exam Product Screenshots
Frequently Asked Questions
How can I get the products after purchase?
All products are available for download immediately from your Member's Area. Once you have made the payment, you will be transferred to Member's Area where you can login and download the products you have purchased to your computer.
How long can I use my product? Will it be valid forever?
Test-King products have a validity of 90 days from the date of purchase. This means that any updates to the products, including but not limited to new questions, or updates and changes by our editing team, will be automatically downloaded on to computer to make sure that you get latest exam prep materials during those 90 days.
Can I renew my product if when it's expired?
Yes, when the 90 days of your product validity are over, you have the option of renewing your expired products with a 30% discount. This can be done in your Member's Area.
Please note that you will not be able to use the product after it has expired if you don't renew it.
How often are the questions updated?
We always try to provide the latest pool of questions, Updates in the questions depend on the changes in actual pool of questions by different vendors. As soon as we know about the change in the exam question pool we try our best to update the products as fast as possible.
How many computers I can download Test-King software on?
You can download the Test-King products on the maximum number of 2 (two) computers or devices. If you need to use the software on more than two machines, you can purchase this option separately. Please email support@test-king.com if you need to use more than 5 (five) computers.
What is a PDF Version?
PDF Version is a pdf document of Questions & Answers product. The document file has standart .pdf format, which can be easily read by any pdf reader application like Adobe Acrobat Reader, Foxit Reader, OpenOffice, Google Docs and many others.
Can I purchase PDF Version without the Testing Engine?
PDF Version cannot be purchased separately. It is only available as an add-on to main Question & Answer Testing Engine product.
What operating systems are supported by your Testing Engine software?
Our testing engine is supported by Windows. Andriod and IOS software is currently under development.
Top Exin Exams
ISFS: Introduction to Information Security and ISO/IEC 27002
In the contemporary digital ecosystem, safeguarding information has become an imperative of strategic importance for organizations across all sectors. Information security is not merely a technical requirement but a multidimensional discipline encompassing governance, policy formulation, operational controls, and cultural integration. The principles of confidentiality, integrity, and availability serve as the cornerstone of any robust security architecture, ensuring that information remains accurate, reliable, and accessible to authorized entities while preventing unauthorized access or modification. Within this context, the ISO/IEC 27002 standard emerges as a globally recognized framework, offering a comprehensive collection of best practices for managing information security effectively. Its guidance extends beyond technology, emphasizing organizational structures, responsibilities, and procedural rigor necessary for sustainable protection of assets.
Understanding the Foundations of Information Security
The evolution of ISO/IEC 27002 is deeply intertwined with the history of information security governance. Initially conceived as a codification of best practices derived from disparate standards, ISO/IEC 27002 provides a structured approach to managing risks in an increasingly complex digital environment. Organizations that align their policies with this standard cultivate a culture of security awareness, ensuring that operational processes, technological infrastructure, and human behaviors collectively contribute to risk mitigation. This holistic paradigm underscores the necessity of integrating information security into organizational strategy rather than treating it as an isolated technical endeavor.
The Scope and Significance of ISO/IEC 27002
ISO/IEC 27002 delineates controls that span multiple dimensions of organizational activity, encompassing asset management, access control, cryptographic practices, physical security, human resource policies, and incident response procedures. Each control is designed to be adaptable, allowing organizations of varying size and sectoral focus to implement measures commensurate with their risk exposure and regulatory obligations. For individuals preparing for the EX0-105 examination, understanding the rationale and application of these controls is essential, as the certification evaluates not only conceptual knowledge but also the ability to contextualize security principles in practical scenarios.
The framework emphasizes risk-based decision-making, guiding organizations to identify critical assets, assess potential threats, and implement proportionate safeguards. It encourages a cyclical approach to security management, where controls are regularly reviewed, monitored, and refined in response to emerging vulnerabilities and evolving threat landscapes. By adhering to these principles, organizations can foster resilience against incidents ranging from unauthorized data access to systemic operational disruptions, thereby reinforcing stakeholder trust and ensuring regulatory compliance.
Core Principles and Strategic Implementation
At the heart of ISO/IEC 27002 lies the understanding that information is an invaluable asset whose compromise can have significant operational, financial, and reputational consequences. Effective security management begins with a comprehensive asset inventory, assigning classification levels that reflect sensitivity and criticality. This enables organizations to allocate resources efficiently, applying enhanced safeguards to high-value assets while maintaining proportional oversight over less critical information. The standard also emphasizes the necessity of access control policies, ensuring that only authorized personnel have appropriate access to sensitive information based on the principle of least privilege.
Human factors play a pivotal role in the efficacy of any security framework. Policies alone cannot safeguard information unless they are complemented by training programs that cultivate awareness and behavioral vigilance among employees. ISO/IEC 27002 advocates for continuous educational initiatives, incident reporting mechanisms, and role-based responsibilities that collectively mitigate the risk of insider threats. Such measures integrate cognitive resilience into the organizational fabric, creating a workforce capable of recognizing and responding to security anomalies with both alacrity and prudence.
Risk Management and Governance
Risk management constitutes a critical dimension of ISO/IEC 27002. The standard promotes a systematic methodology for identifying potential vulnerabilities, estimating their likelihood and impact, and determining appropriate treatment strategies. This process encompasses threat modeling, risk analysis, and residual risk evaluation, allowing organizations to implement controls that are both effective and cost-efficient. Governance structures, including clear delineation of accountability and reporting channels, reinforce the efficacy of these measures by ensuring oversight, transparency, and compliance with internal and external mandates.
A salient feature of ISO/IEC 27002 is its adaptability, enabling organizations to tailor controls according to their contextual exigencies. This requires a nuanced understanding of the organizational risk appetite, regulatory requirements, and technological dependencies. Integrating risk management with strategic objectives ensures that security measures are not perceived as impediments but as enablers of operational continuity and competitive advantage.
The Role of EX0-105 Certification
The EX0-105 certification offered by EXIN validates an individual’s comprehension of ISO/IEC 27002 principles and their practical application within organizational contexts. It serves as a benchmark for foundational knowledge, demonstrating proficiency in interpreting security policies, evaluating risks, and understanding the operational implications of controls. Candidates preparing for this exam benefit from familiarizing themselves with the breadth of the standard, encompassing governance, asset protection, cryptography, operational security, and human factors. Mastery of these areas not only facilitates certification success but also equips professionals with the analytical and procedural acumen necessary to support enterprise-wide security initiatives.
In preparing for the EX0-105 examination, it is essential to approach the subject matter with an integrative perspective. Rather than memorizing controls in isolation, candidates should focus on understanding the interdependencies between policies, processes, and technology. This holistic comprehension enables practical application, equipping professionals to identify vulnerabilities, implement appropriate safeguards, and contribute meaningfully to the organization’s overall security posture.
Emerging Trends in Information Security
The dynamic nature of the threat landscape necessitates continuous vigilance and adaptability. Emerging technologies, such as cloud computing, artificial intelligence, and the Internet of Things, introduce novel vulnerabilities that challenge traditional security paradigms. ISO/IEC 27002 provides the scaffolding for addressing these challenges, advocating for risk-based strategies that are iterative, evidence-driven, and aligned with organizational priorities. Professionals equipped with knowledge from this standard are better positioned to anticipate threats, evaluate emerging risks, and implement controls that sustain operational integrity.
Organizations that embrace ISO/IEC 27002 foster a culture of proactive security, integrating preventive, detective, and corrective controls into every facet of their operations. This includes meticulous documentation, regular audits, and a commitment to continual improvement, ensuring that security practices evolve alongside technological and regulatory developments. Such foresight enhances resilience, minimizes potential losses, and underpins the long-term viability of information-dependent enterprises.
Integrating Knowledge into Organizational Practices
Effective adoption of ISO/IEC 27002 requires more than theoretical understanding; it demands practical integration into everyday organizational processes. This entails aligning security policies with business objectives, incorporating risk assessments into decision-making, and fostering an environment where compliance and accountability are intrinsic to operations. Tools such as asset registers, incident logs, and procedural manuals support operationalization, while awareness programs and training initiatives reinforce behavioral compliance. By embedding these practices into the organizational DNA, enterprises achieve a sustainable, adaptable security posture that responds efficiently to both internal and external challenges.
The standard also underscores the significance of continuous evaluation. Controls should be reviewed periodically to ensure their relevance and effectiveness, informed by incident data, audit outcomes, and evolving threat intelligence. Organizations that cultivate this iterative mindset develop agility, enabling timely responses to vulnerabilities, regulatory changes, and technological innovations.
Establishing a Robust Policy Framework
Information security policies form the bedrock of an organization’s defense mechanisms against an ever-evolving threat landscape. They encapsulate the strategic intent of leadership, translating organizational objectives into actionable directives that safeguard information assets. Developing these policies requires a meticulous understanding of operational processes, technological dependencies, and regulatory obligations. They serve not only as a guideline for day-to-day operations but also as a reference point during incidents, audits, or compliance reviews. A comprehensive policy framework integrates governance principles, delineates accountability, and ensures that security considerations are consistently embedded into decision-making processes.
ISO/IEC 27002 provides a detailed blueprint for crafting such policies, emphasizing clarity, consistency, and adaptability. Policies should articulate expectations for acceptable use, access management, incident handling, and risk mitigation, among other critical areas. They must resonate with organizational culture, ensuring that employees understand the rationale behind controls and recognize their individual responsibilities. This alignment between policy and practice fosters behavioral adherence, reducing the likelihood of security breaches arising from negligence or misunderstanding.
Governance and Organizational Oversight
Effective governance under ISO/IEC 27002 encompasses more than top-down supervision; it is a collaborative structure where leadership, management, and operational staff share accountability for security outcomes. Governance mechanisms include defining roles, establishing reporting hierarchies, and implementing monitoring procedures that ensure policies are enforced consistently. Strategic oversight allows organizations to align security objectives with broader business goals, ensuring that risk management and operational resilience are not peripheral considerations but integral components of organizational strategy.
A key element of governance is accountability, which extends from executive leadership to individual contributors. Clear delineation of responsibility ensures that decision-making is transparent and that deviations from established controls are promptly addressed. Governance frameworks also facilitate communication channels for security incidents, risk assessments, and compliance reporting, creating a feedback loop that supports continual improvement. Within this ecosystem, risk-aware leadership cultivates a culture of vigilance and ethical stewardship, encouraging employees to take proactive measures to protect information assets.
Risk-Based Policy Development
Risk assessment is fundamental to shaping effective information security policies. ISO/IEC 27002 advocates for a methodical approach where potential threats, vulnerabilities, and impacts are evaluated to inform control selection and policy directives. This process entails identifying critical assets, estimating the likelihood and potential severity of compromise, and defining measures to mitigate identified risks. By adopting a risk-based perspective, organizations prioritize resources efficiently, focusing on controls that deliver maximal protection for high-value assets while maintaining proportional oversight for less critical information.
Policy development informed by risk assessment ensures that controls are neither arbitrary nor static. It enables organizations to anticipate emerging threats, adapt to regulatory changes, and respond to technological innovations. By integrating these insights into governance structures, organizations cultivate a resilient security posture capable of withstanding both expected and unforeseen challenges. Terminology such as exposure mapping, vulnerability calibration, and mitigative stratagems reflects the precision and depth inherent in ISO/IEC 27002-aligned policy creation.
Operationalizing Security Policies
Creating comprehensive policies is only the initial step; operationalization ensures that they are actively implemented and monitored. Procedures must be established to translate high-level directives into tangible practices, encompassing system configuration, access management, incident handling, and employee training. ISO/IEC 27002 emphasizes the interplay between policy, procedure, and control, reinforcing the notion that policy effectiveness is contingent upon its integration into operational workflows.
Operationalization also involves documentation and record-keeping, providing a trail for audits, compliance verification, and continuous improvement. Logs of system access, incident reports, and periodic review outcomes support accountability and transparency, allowing organizations to identify deviations from prescribed controls and implement corrective actions. This structured approach mitigates risks while promoting a culture of diligence, awareness, and proactive engagement across the organization.
Human Factors in Governance
Human behavior is an often-underestimated component of information security governance. Employees, contractors, and third-party partners collectively influence the effectiveness of policies, and their actions can either strengthen or compromise security objectives. ISO/IEC 27002 underscores the necessity of embedding human-centric considerations into governance frameworks, emphasizing training, awareness, and clearly defined responsibilities. Awareness programs cultivate a cognitive resilience, equipping personnel to recognize threats, understand procedural requirements, and respond appropriately to incidents.
Role-based responsibilities further reinforce governance by aligning access and accountability with individual duties. Privileges are allocated according to the principle of least privilege, ensuring that employees have access only to information necessary for their functions. Regular training and simulated exercises enhance preparedness, bridging the gap between policy articulation and real-world behavior. By fostering an environment of shared responsibility, organizations reduce the likelihood of inadvertent breaches and encourage proactive security practices.
Monitoring, Audit, and Compliance
Continuous monitoring is an essential aspect of governance, enabling organizations to assess adherence to policies, detect deviations, and evaluate the effectiveness of controls. ISO/IEC 27002 advocates for regular internal audits, risk reviews, and performance evaluations to ensure that security practices remain aligned with organizational objectives and evolving threat landscapes. Monitoring mechanisms range from system logs and anomaly detection to scheduled reviews of policy implementation, collectively providing a comprehensive view of operational compliance.
Compliance extends beyond internal policies to encompass regulatory and contractual obligations. Organizations must integrate governance frameworks with external mandates, ensuring that controls satisfy legal requirements and industry standards. Documentation of compliance activities, audit trails, and incident responses not only demonstrates accountability to regulators and stakeholders but also informs iterative improvements. This continuous feedback loop reinforces a proactive security culture, ensuring that policies evolve alongside organizational growth and technological advancements.
Strategic Integration of Governance and Policy
The strategic value of governance and policy lies in their ability to transform security from a reactive function into a proactive enabler of organizational objectives. ISO/IEC 27002 encourages alignment between information security initiatives and business strategy, ensuring that risk mitigation, asset protection, and operational continuity are considered in all decision-making processes. By integrating governance mechanisms with strategic planning, organizations can anticipate potential vulnerabilities, allocate resources effectively, and sustain resilience in the face of both internal and external challenges.
Effective integration also entails fostering a culture of continuous vigilance. Employees at all levels should internalize security principles, understand the implications of policy adherence, and participate in risk mitigation efforts. Feedback mechanisms, performance assessments, and periodic reviews reinforce accountability and ensure that security governance evolves with changing operational, technological, and regulatory landscapes. This holistic approach positions organizations to not only protect their information assets but also leverage security as a differentiator in competitive and regulatory environments.
The Fundamentals of Risk Assessment
Risk assessment is a cornerstone of information security management, providing a structured methodology to identify, analyze, and prioritize potential threats that could compromise an organization’s information assets. ISO/IEC 27002 emphasizes a systematic approach, where organizations evaluate the likelihood of incidents, the potential impact on operations, and the interplay of vulnerabilities across people, processes, and technology. Understanding these dynamics requires a nuanced perspective that balances analytical rigor with practical applicability. Threats can originate from internal sources, such as inadvertent errors or malicious insider actions, or external vectors including cyberattacks, social engineering, and environmental disruptions. The assessment process captures these dimensions, transforming abstract risks into tangible insights that guide security decision-making.
Organizations begin by cataloging assets, considering both tangible and intangible elements, including information repositories, network infrastructure, software systems, and human resources. Each asset is evaluated for its sensitivity, criticality, and potential consequences of compromise. This granular approach ensures that high-value assets receive prioritized attention while lower-risk items are managed proportionately. Risk assessment under ISO/IEC 27002 is iterative, acknowledging that threat landscapes evolve and that security measures must adapt accordingly. By embedding this cyclical evaluation into organizational routines, companies cultivate resilience and strategic foresight.
Identifying Threats and Vulnerabilities
The identification of threats and vulnerabilities represents the initial stage of risk management. Threats are events or circumstances that could exploit a weakness and cause harm, while vulnerabilities are inherent weaknesses that increase susceptibility to threats. ISO/IEC 27002 encourages a comprehensive review of organizational operations, technological systems, and human behaviors to uncover potential vulnerabilities. Common vulnerabilities include weak authentication mechanisms, misconfigured systems, inadequate access controls, and insufficient awareness among personnel. Emerging technologies, such as cloud computing and Internet of Things devices, introduce novel exposure points that require specialized attention. Rare and sophisticated terminology such as exploit surface, latent susceptibilities, and attack vector topology can enhance understanding of these concepts.
Understanding the interrelationship between threats and vulnerabilities is essential. A threat that is inconsequential against a robustly secured asset may pose a critical risk to a poorly protected system. Therefore, accurate identification is not merely about cataloging potential hazards but also evaluating the contexts in which they could manifest. This approach ensures that risk treatment strategies are proportionate, targeted, and capable of mitigating the most significant exposures.
Analyzing Likelihood and Impact
Once threats and vulnerabilities are identified, the next step involves assessing the likelihood of occurrence and the potential impact on organizational objectives. Likelihood considers the probability that a specific threat could exploit a vulnerability, influenced by factors such as historical data, threat intelligence, and operational environment. Impact evaluates the consequences of such an event, encompassing operational disruption, financial loss, reputational damage, legal liability, and regulatory penalties. ISO/IEC 27002 encourages a holistic evaluation, integrating both quantitative measures, such as projected financial loss, and qualitative factors, including stakeholder confidence and operational continuity. Concepts like probabilistic modeling, consequence hierarchy, and operational fragility offer a refined lens to understand these dimensions.
This analytical phase provides the foundation for prioritizing risks. High-likelihood, high-impact scenarios demand immediate attention, while low-likelihood or minor-impact risks may be managed through monitoring and routine controls. By systematically mapping risks along these dimensions, organizations can allocate resources efficiently, ensuring that mitigation efforts yield maximal protective value.
Risk Treatment Strategies
Risk treatment encompasses the selection and implementation of controls to mitigate identified risks. ISO/IEC 27002 outlines several strategies, including risk avoidance, reduction, transfer, and acceptance. Risk avoidance involves modifying processes or eliminating activities that introduce excessive exposure. Risk reduction focuses on implementing safeguards to minimize the likelihood or impact of threats, such as access controls, encryption, network segmentation, and regular vulnerability patching. Risk transfer reallocates potential exposure to third parties, often through insurance or outsourcing arrangements. Risk acceptance recognizes residual risks that remain after treatment, deemed tolerable within the organization’s risk appetite. Vocabulary such as mitigative interventions, residual exposure, and protective architecture can articulate these concepts with depth and sophistication.
The efficacy of risk treatment hinges on aligning controls with organizational priorities and operational realities. Overly burdensome controls may impede productivity and induce resistance, whereas insufficient measures fail to provide meaningful protection. ISO/IEC 27002 emphasizes proportionality, advocating for controls that balance security objectives with operational efficiency. Regular monitoring and evaluation ensure that treatment strategies remain effective, enabling iterative adjustments in response to evolving threats.
Risk Communication and Documentation
Effective risk management requires comprehensive documentation and communication. Risk registers, assessment reports, and treatment plans capture the rationale behind decisions, supporting accountability, compliance, and continuous improvement. ISO/IEC 27002 highlights the importance of clear communication, ensuring that stakeholders at all levels understand risks, controls, and their respective responsibilities. Transparent communication channels facilitate incident reporting, collaborative problem-solving, and informed decision-making. Advanced terminology such as exposé logs, audit trail fidelity, and strategic risk articulation can enhance precision and convey the sophistication of organizational practices.
Documentation serves not only as a reference but also as a tool for organizational learning. Historical data on incidents, near misses, and control performance inform future assessments, enabling iterative refinement of risk strategies. This creates a feedback loop where knowledge accrues over time, enhancing both proactive and reactive capabilities.
Integration of Risk Management into Organizational Culture
ISO/IEC 27002 emphasizes that risk assessment and treatment must be integrated into the broader organizational culture rather than treated as isolated technical exercises. Employees at all levels must internalize risk awareness, understanding how individual actions influence overall security posture. Training programs, simulations, and awareness campaigns reinforce behavioral vigilance, ensuring that personnel recognize threats, adhere to controls, and respond effectively to anomalies. Terms such as cognitive vigilance, operational mindfulness, and threat attunement illustrate the nuanced human dimensions of risk management.
Leadership plays a pivotal role in fostering this culture, setting the tone for accountability, transparency, and ethical stewardship. By demonstrating commitment to risk-aware practices and rewarding proactive behavior, management cultivates an environment where security is a shared responsibility rather than a bureaucratic obligation. Embedding risk management into routine workflows, strategic planning, and performance evaluation further reinforces this integration, creating a resilient organization capable of anticipating, mitigating, and recovering from adverse events.
Continuous Monitoring and Review
Risk assessment and treatment are dynamic, requiring ongoing monitoring and iterative review. Threat landscapes evolve rapidly, regulatory requirements shift, and organizational priorities change. ISO/IEC 27002 advocates for continuous surveillance of assets, vulnerabilities, and control effectiveness, leveraging metrics, audits, and incident analysis to maintain alignment with objectives. Predictive analytics, anomaly detection, and trend evaluation enable organizations to anticipate emerging threats and adjust strategies preemptively. Sophisticated terminology such as risk telemetry, predictive threat modeling, and vulnerability calibration can convey the precision and rigor of these practices.
Periodic reviews ensure that residual risks remain within acceptable thresholds and that new exposures are promptly addressed. This cyclical approach transforms risk management from a reactive activity into a proactive capability, embedding resilience into both operational processes and strategic decision-making. Organizations that embrace continuous review cultivate agility, maintaining a posture capable of withstanding both anticipated and unforeseen challenges.
Strategic Value of Risk Management in ISO/IEC 27002
The strategic significance of risk assessment and treatment lies in its capacity to transform information security from a defensive mechanism into a driver of organizational confidence and operational continuity. ISO/IEC 27002 enables organizations to make informed decisions, allocate resources prudently, and prioritize initiatives that safeguard critical assets. By embedding rigorous risk evaluation into governance, policy formulation, and operational practices, organizations develop a resilient infrastructure capable of sustaining performance under duress.
Integration of risk management with enterprise strategy also enhances regulatory compliance and stakeholder trust. Demonstrable risk mitigation, documentation fidelity, and transparent communication reinforce credibility with regulators, partners, and clients. This alignment ensures that security practices not only protect information assets but also contribute to long-term strategic objectives, making risk management an indispensable facet of organizational sustainability.
The Significance of Asset Management
Asset management constitutes a critical pillar of information security, underpinning the protection of organizational resources from unauthorized access, modification, or destruction. ISO/IEC 27002 underscores the necessity of identifying, classifying, and maintaining control over assets, recognizing that these resources, whether tangible or intangible, form the backbone of operational continuity. Assets encompass not only hardware, software, and information repositories but also intangible elements such as intellectual property, procedural knowledge, and organizational reputation. Each asset must be inventoried, assigned ownership, and classified according to sensitivity and criticality, allowing organizations to apply appropriate safeguards proportional to potential risks. The process of asset management cultivates accountability, enabling stakeholders to understand the value of each asset and the potential consequences of compromise.
ISO/IEC 27002 emphasizes lifecycle management as a fundamental aspect of asset stewardship. From acquisition through usage, maintenance, and eventual disposal, assets must be managed with vigilance to prevent unintentional exposure or loss. Classification schemes assist in prioritizing security efforts, ensuring that high-value assets receive the most stringent protections while less critical assets are managed efficiently. Terminology such as custodial responsibility, asset sanctity, and operational patrimony provides a refined understanding of the strategic importance of managing information assets comprehensively.
Ownership and Responsibility
A clear delineation of ownership and responsibility is vital for effective asset management. Each asset should have an assigned custodian responsible for ensuring its security, proper use, and compliance with organizational policies. ISO/IEC 27002 advocates for documented accountability, where custodians are aware of their duties, authorized access levels, and reporting obligations. Ownership extends beyond physical possession; it encompasses stewardship over data integrity, availability, and confidentiality. By establishing explicit responsibilities, organizations can mitigate risks associated with neglect, misuse, or unauthorized handling.
Effective stewardship also involves evaluating interdependencies among assets. For instance, the compromise of a network device may have cascading effects on data repositories and operational systems. By understanding these interconnections, asset custodians can implement controls that address both direct and indirect risks, enhancing the resilience of the broader organizational ecosystem. Rare vocabulary such as fiduciary custodianship, asset provenance, and operational lineage can convey the sophistication and precision inherent in responsible asset management.
Classification and Access Controls
Classification of assets is a central tenet of ISO/IEC 27002, enabling organizations to assign sensitivity levels and access privileges in alignment with security requirements. Assets may be classified as confidential, internal, or public, among other categories, based on their potential impact if compromised. This stratification informs decisions regarding access control, encryption, monitoring, and retention policies. Access management must adhere to the principle of least privilege, granting personnel only the necessary permissions to perform their functions while minimizing exposure.
In addition to role-based access, organizations should implement temporal and contextual controls, such as time-bound permissions, location-based access, and monitoring of anomalous activities. These measures enhance security without unduly hindering operational efficiency. Concepts like custodial boundaries, privilege granularity, and access telemetry illustrate the sophisticated mechanisms organizations can employ to protect sensitive assets effectively.
Human Resource Security
Human resources represent both a critical asset and a potential vector for security incidents. ISO/IEC 27002 emphasizes the integration of personnel management into information security practices, ensuring that staff, contractors, and third-party collaborators adhere to organizational policies and ethical standards. This begins with pre-employment screening, which verifies qualifications, assesses integrity, and evaluates potential risks. Background checks, reference verification, and contract stipulations form the foundation of secure onboarding practices, mitigating the likelihood of insider threats.
Ongoing personnel management includes awareness programs, role-specific training, and clear communication of responsibilities. Employees should understand security policies, operational procedures, and reporting mechanisms for incidents or anomalies. ISO/IEC 27002 advocates for cultivating cognitive vigilance and operational mindfulness, ensuring that human behavior aligns with security objectives. By fostering a culture of accountability and continuous education, organizations reduce inadvertent errors, deliberate violations, and negligent practices that could compromise assets.
Termination and Transition Procedures
Effective human resource security extends to managing departures, transitions, and changes in roles. ISO/IEC 27002 emphasizes the need for structured termination procedures, ensuring that access rights, credentials, and organizational property are returned or deactivated promptly. Offboarding processes should include exit interviews, data retrieval, and verification of compliance with non-disclosure agreements or confidentiality obligations. Transitional periods, such as role reassignments or project handovers, require careful oversight to prevent lapses in asset protection and operational continuity.
Rare vocabulary such as deprovisioning protocols, custodial handover, and operational transference highlights the precision and sophistication required in managing human-centric risks. These procedures protect against residual access, unauthorized data dissemination, and potential breaches arising from organizational changes.
Integration of Assets and Human Resources
ISO/IEC 27002 emphasizes that asset management and human resource security are interconnected domains. Personnel act as custodians of organizational assets, and the efficacy of security controls depends on their knowledge, awareness, and adherence to policies. Integration involves aligning access permissions, training programs, and monitoring mechanisms with the asset classification framework, ensuring that individuals understand both the value of resources and their responsibilities in safeguarding them.
This alignment extends to operational workflows, where tasks are structured to reinforce security while maintaining productivity. By embedding asset awareness into daily activities, organizations cultivate behavioral vigilance, ensuring that personnel act as proactive participants in protecting sensitive information. Concepts such as operational attunement, custodial mindfulness, and human-centric fortification illustrate the nuanced interplay between human behavior and asset protection.
Monitoring, Audit, and Continuous Oversight
Monitoring and auditing are essential components of asset and human resource security. ISO/IEC 27002 encourages organizations to maintain logs of asset usage, access events, and personnel activities, providing visibility into compliance, anomalies, and potential threats. Regular audits assess adherence to policies, evaluate control effectiveness, and identify areas for improvement. This ongoing oversight enables proactive intervention before minor incidents escalate into significant breaches.
Metrics and performance indicators, such as frequency of unauthorized access attempts, asset utilization efficiency, and training participation rates, provide quantitative insights into security posture. Anomaly detection, behavioral analysis, and periodic reviews enhance situational awareness, allowing organizations to respond to emerging risks with agility. Terminology like telemetry analysis, compliance fidelity, and operational vigilance can convey the sophistication of these monitoring practices.
Strategic Implications for Organizational Resilience
The strategic significance of asset management and human resource security extends beyond immediate protection. By effectively managing assets and personnel, organizations enhance operational continuity, regulatory compliance, and stakeholder trust. ISO/IEC 27002 provides a framework to integrate these domains into broader risk management and governance strategies, ensuring that security practices support organizational objectives rather than operate in isolation.
Embedding security considerations into workforce culture and asset stewardship cultivates a resilient enterprise capable of anticipating threats, mitigating vulnerabilities, and maintaining critical functions under adverse conditions. The interplay between human awareness, procedural adherence, and technological safeguards creates a layered defense, where each component reinforces the others. Concepts such as cognitive fortification, operational patrimony, and integrative resilience underscore the holistic nature of security management advocated by ISO/IEC 27002.
Securing Physical Infrastructure
Physical security remains a foundational element of information protection, forming the first line of defense against unauthorized access, environmental hazards, and deliberate sabotage. ISO/IEC 27002 emphasizes that safeguarding physical assets—such as data centers, server rooms, workstations, and critical infrastructure—is integral to maintaining operational continuity. Measures include controlled entry points, surveillance systems, secure storage, and environmental controls such as fire suppression, temperature regulation, and humidity monitoring. By implementing these protections, organizations mitigate risks posed by theft, vandalism, natural disasters, or accidental damage. The vocabulary of operational sanctity, perimetric vigilance, and fortification protocols underscores the precision and strategic importance of physical security measures.
Asset protection is closely linked to human behavior, requiring that personnel adhere to access protocols, visitor management systems, and reporting procedures for anomalies. ISO/IEC 27002 recommends layered security, where multiple controls complement one another to reduce the likelihood of breach. This includes a combination of administrative, technical, and physical measures, ensuring redundancy and resilience. The integration of physical monitoring with access logs and audit trails provides accountability and enables prompt identification of security incidents.
Operational Controls and Process Security
Operational security encompasses the procedures, practices, and controls that ensure reliable and secure day-to-day operations. ISO/IEC 27002 highlights that risks are not only technological but also procedural, emerging from workflow inefficiencies, human error, or inadequate oversight. Key practices include configuration management, change control, separation of duties, and regular backup and recovery procedures. By establishing structured operational controls, organizations minimize exposure to accidental disruptions, malicious activities, and system failures. Terms such as procedural fidelity, operational sanctity, and continuity stewardship convey the precision and diligence required in managing operational security.
Change management is critical, ensuring that modifications to systems, software, or processes are documented, tested, and approved before implementation. Configuration management tracks and maintains the integrity of IT assets, preventing unauthorized alterations that could compromise confidentiality, integrity, or availability. Separation of duties prevents concentration of control, reducing the risk of fraud or accidental mismanagement. Regular review of operational controls, combined with monitoring and audit mechanisms, enhances situational awareness and ensures alignment with organizational objectives.
Communication Security
The protection of information in transit is an essential component of ISO/IEC 27002. Communication channels, whether internal or external, are susceptible to interception, alteration, or disruption. The standard emphasizes encryption, secure protocols, and authentication mechanisms to ensure that messages are transmitted safely. Additionally, it advocates monitoring network traffic, implementing intrusion detection systems, and controlling remote access to prevent unauthorized interception or misuse. Vocabulary such as telemetric fortification, encrypted telemetry, and transmission integrity highlights the technical sophistication inherent in communication security practices.
Secure communication extends beyond digital channels to include verbal and written exchanges. Confidential information should be shared according to access permissions, with consideration of environmental risks and audience trustworthiness. Procedures for transmitting sensitive data, such as secure file transfer protocols and virtual private networks, complement policy-driven guidelines. Regular training on secure communication practices reinforces personnel awareness, ensuring that the human element does not undermine technical safeguards.
Incident Detection and Response
ISO/IEC 27002 emphasizes the importance of timely detection and effective response to security incidents, encompassing both physical breaches and operational anomalies. Monitoring systems, alert mechanisms, and event logging provide visibility into potential threats, allowing organizations to respond proactively. Incident response procedures should define roles, responsibilities, communication channels, and escalation pathways to ensure swift containment and mitigation. Terminology such as anomaly detection, operational telemetry, and corrective intervention underscores the structured approach to maintaining security integrity.
Physical and operational incidents, such as unauthorized access, environmental hazards, or system malfunctions, require coordinated responses. Employees should be trained to recognize deviations from normal operations and initiate reporting protocols. Response plans should include containment measures, investigation procedures, and post-incident evaluation, enabling organizations to learn from events and strengthen controls.
Continuity Planning and Resilience
Ensuring the resilience of physical, operational, and communication systems is a strategic objective emphasized by ISO/IEC 27002. Business continuity planning and disaster recovery strategies enable organizations to maintain critical functions during adverse events, minimizing disruption and loss. Continuity measures include redundant systems, off-site backups, failover mechanisms, and alternative communication channels. By anticipating potential disruptions, organizations cultivate agility, reducing the impact of incidents on operations, clients, and stakeholders. Vocabulary such as continuity fortification, systemic resilience, and operational perpetuity conveys the proactive and strategic approach to safeguarding organizational functionality.
Integration of continuity planning with security policies ensures that protective measures are coherent and mutually reinforcing. Regular drills, testing, and scenario analysis provide practical experience in responding to crises, enhancing preparedness and reinforcing organizational confidence. Monitoring emerging threats and evaluating recovery procedures ensures that continuity measures remain relevant and effective.
Human Factors in Physical and Operational Security
Personnel behavior remains a pivotal determinant of physical, operational, and communication security. ISO/IEC 27002 emphasizes awareness, training, and clearly defined responsibilities to mitigate risks associated with human error or malicious actions. Employees, contractors, and visitors must understand access protocols, operational procedures, and communication guidelines to prevent inadvertent breaches. Cognitive vigilance, behavioral attunement, and operational mindfulness are concepts that highlight the sophisticated integration of human factors into organizational security practices.
Leadership plays a crucial role in fostering a culture of security awareness. Reinforcing accountability, providing continuous education, and modeling adherence to procedures ensure that personnel engage proactively in protecting assets and maintaining operational integrity. By embedding human-centric considerations into security frameworks, organizations reduce vulnerabilities arising from negligence, misjudgment, or malfeasance.
Integration of Controls for Holistic Security
ISO/IEC 27002 advocates for a layered and integrated approach to physical, operational, and communication security. No single control is sufficient to address the complexity of modern threats; instead, organizations should implement complementary measures across domains. Physical access restrictions, procedural safeguards, and secure communication protocols collectively reinforce each other, creating a resilient security ecosystem. This holistic perspective enables organizations to anticipate risks, respond effectively to incidents, and sustain operational continuity in dynamic environments.
Periodic assessment, monitoring, and refinement of controls ensure that security measures remain effective, adaptable, and aligned with organizational priorities. Audits, reviews, and feedback mechanisms provide evidence of control efficacy, inform policy adjustments, and guide resource allocation. By cultivating an integrated security posture, organizations transform protective measures into strategic enablers, supporting both operational and business objectives.
The Role of Compliance in Information Security
Compliance represents a fundamental dimension of information security management, serving as the bridge between organizational practices and regulatory, legal, or contractual obligations. ISO/IEC 27002 emphasizes that compliance is not merely a procedural requirement but a strategic imperative that aligns operational behavior with external expectations. Organizations are often subject to multiple mandates, including data protection legislation, industry-specific standards, and internal policies, all of which converge to define the parameters of acceptable practice. Ensuring compliance entails establishing systematic procedures, monitoring adherence, and implementing controls that prevent deviations from prescribed norms. Vocabulary such as regulatory consonance, fiduciary alignment, and statutory observance highlights the strategic and disciplined approach necessary to maintain compliance.
Compliance measures extend beyond technical implementations to encompass procedural, operational, and human dimensions. Policies must clearly articulate responsibilities, while personnel are trained to recognize obligations and act in accordance with legal and organizational requirements. By embedding compliance into everyday operations, organizations transform regulatory adherence from a reactive activity into an intrinsic part of organizational culture.
Audit as a Tool for Assurance
Audit functions provide independent verification of compliance and effectiveness, forming a critical component of the ISO/IEC 27002 framework. Audits assess whether policies, controls, and operational practices conform to established standards, offering both assurance and insight for continuous improvement. Internal audits, conducted by personnel independent of day-to-day operations, enable early detection of gaps or inefficiencies. External audits, often mandated by regulatory authorities or certification bodies, provide objective evaluation and credibility to stakeholders. Concepts such as audit trail integrity, evaluative rigor, and procedural transparency reflect the precision and accountability inherent in audit practices.
Auditing encompasses more than documentation review; it requires observation, verification, and testing of controls. This holistic approach ensures that operational practices align with policy directives and that potential vulnerabilities are identified proactively. Findings from audits inform remediation plans, enhance awareness of security posture, and guide decision-making at both strategic and operational levels. ISO/IEC 27002 advocates that audit outcomes feed directly into risk management and governance mechanisms, reinforcing a culture of accountability and evidence-based improvement.
Monitoring and Measurement
Effective security management necessitates continuous monitoring and measurement to maintain alignment with organizational objectives and evolving threats. ISO/IEC 27002 emphasizes metrics and key performance indicators as tools for quantifying control effectiveness, tracking incidents, and evaluating compliance. Monitoring mechanisms may include system logs, anomaly detection, access tracking, and procedural adherence checks. By systematically collecting and analyzing data, organizations gain visibility into operational patterns, vulnerabilities, and emerging risks. Terminology such as operational telemetry, control efficacy indices, and performance fidelity conveys the analytical depth of these practices.
Measurement and monitoring provide a feedback loop that informs strategic decision-making. Deviations from established thresholds trigger alerts, investigations, and corrective actions, ensuring that security objectives are not compromised. Quantitative and qualitative insights derived from monitoring reinforce accountability, enable resource prioritization, and support evidence-based policy refinement.
Continuous Improvement Frameworks
ISO/IEC 27002 emphasizes the principle of continuous improvement, advocating iterative evaluation and enhancement of security policies, procedures, and controls. Continuous improvement ensures that security management adapts to evolving threats, technological advancements, and organizational growth. Frameworks such as Plan-Do-Check-Act provide structured methodologies to assess performance, implement enhancements, and review outcomes. This cyclical approach fosters resilience and agility, transforming reactive responses into proactive capability. Vocabulary such as evolutive refinement, procedural recalibration, and operational perpetuation highlights the dynamic and sophisticated nature of continuous improvement initiatives.
Continuous improvement encompasses policy review, control optimization, personnel training, and incident analysis. Lessons learned from breaches, near misses, and audit findings inform modifications to both technical and procedural measures. By embedding a culture of perpetual enhancement, organizations ensure that information security remains robust, relevant, and aligned with strategic priorities.
Integration with Risk Management
Compliance, audit, and continuous improvement are intrinsically linked to risk management. ISO/IEC 27002 advocates that monitoring results, audit findings, and policy assessments feed into risk evaluation processes, enabling timely adjustment of controls and mitigation strategies. Integrating these functions ensures that residual risks remain within acceptable levels and that emerging threats are addressed proactively. Concepts such as adaptive risk calibration, strategic exposure management, and iterative mitigation reflect the interconnectedness of these domains.
By aligning compliance and improvement initiatives with risk appetite, organizations optimize the allocation of resources, focus on high-impact vulnerabilities, and strengthen overall security posture. This holistic integration reinforces operational resilience, enhances stakeholder confidence, and ensures that security measures are both effective and proportionate.
Human Factors in Audit and Compliance
Personnel play a pivotal role in ensuring compliance, executing audits, and sustaining continuous improvement. ISO/IEC 27002 emphasizes awareness, training, and accountability as critical enablers of effective practices. Employees must understand the rationale behind controls, the implications of non-compliance, and the mechanisms for reporting anomalies. Cognitive vigilance, procedural mindfulness, and ethical stewardship are concepts that highlight the human dimensions of audit and compliance processes.
Leadership reinforces a culture of accountability by modeling adherence, recognizing proactive behaviors, and ensuring that organizational priorities reflect security objectives. By embedding security awareness into daily operations, organizations cultivate a workforce capable of detecting risks, adhering to policies, and contributing to iterative improvement.
Strategic Benefits of Compliance and Improvement
The strategic value of compliance, audit, and continuous improvement extends beyond regulatory adherence. ISO/IEC 27002 positions these practices as enablers of operational continuity, stakeholder trust, and competitive advantage. Demonstrable compliance reassures clients, partners, and regulators of the organization’s commitment to protecting information assets. Audits provide evidence of control efficacy, inform resource allocation, and support strategic planning. Continuous improvement ensures that security measures evolve alongside threats and organizational growth, maintaining resilience and adaptability.
Integration of these practices creates a feedback-rich environment where knowledge accumulates over time, enabling organizations to anticipate challenges, refine controls, and sustain operational excellence. The interplay of procedural rigor, analytical insight, and human engagement produces a robust security ecosystem that supports both day-to-day operations and long-term strategic objectives.
Embedding Compliance into Organizational Culture
ISO/IEC 27002 underscores that compliance and continuous improvement must be intrinsic to organizational culture rather than treated as external obligations. Embedding these principles involves communication, training, leadership endorsement, and reinforcement of accountability. Policies should be understood, internalized, and applied consistently across all levels of the organization. Behavioral reinforcement, recognition of compliance excellence, and alignment of security objectives with performance metrics cultivate an environment where security is perceived as a shared responsibility. Terms such as cognitive consonance, procedural internalization, and organizational attunement articulate the human and cultural dimensions of effective compliance.
Integrating these cultural practices with operational controls, audit mechanisms, and risk management strategies ensures that the organization remains resilient, adaptable, and capable of sustaining information security in a dynamic environment. Personnel engagement, leadership commitment, and iterative improvement collectively strengthen the organization’s security posture, fostering confidence among stakeholders and mitigating potential exposures.
Conclusion
Compliance, audit, and continuous improvement form a triad that underpins the efficacy of information security management as prescribed by ISO/IEC 27002. These practices ensure that organizational policies, procedures, and controls align with legal, regulatory, and strategic objectives while providing mechanisms for verification, accountability, and enhancement. Auditing offers assurance and insight, monitoring provides real-time awareness, and continuous improvement fosters resilience and adaptability. Human factors play an essential role in these endeavors, as personnel awareness, training, and ethical stewardship reinforce technical and procedural safeguards.
By integrating these functions with governance, risk management, and operational practices, organizations cultivate a holistic security ecosystem capable of anticipating threats, mitigating vulnerabilities, and sustaining critical operations. The strategic benefits of this integration include operational continuity, stakeholder trust, regulatory confidence, and enhanced organizational agility. Compliance and continuous improvement are not static obligations but dynamic enablers, transforming information security into a proactive, strategically aligned discipline that underpins long-term organizational success.