Exam Code: EX0-105
Exam Name: Information Security Foundation based on ISO/IEC 27002
Certification Provider: Exin
Corresponding Certification: Information Security Foundation (based on ISO/IEC 27002)
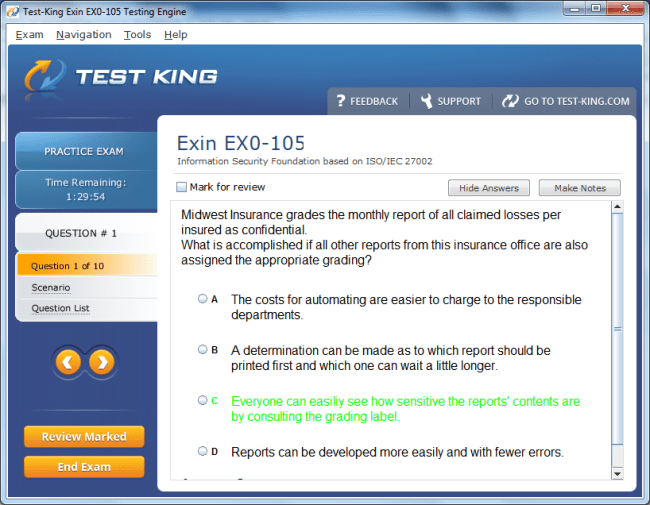
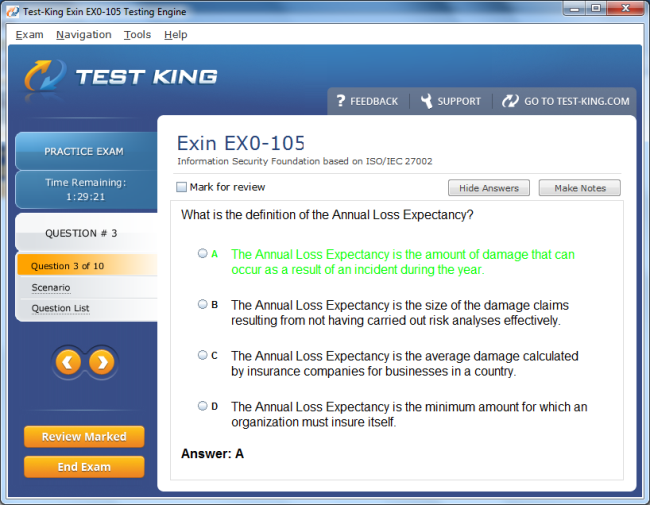
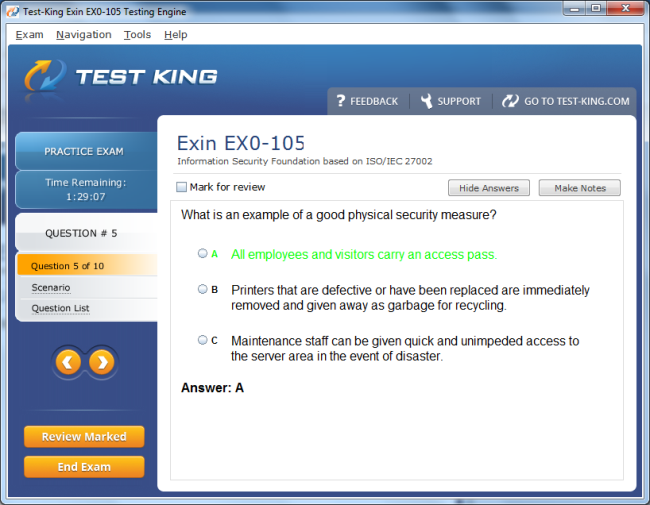
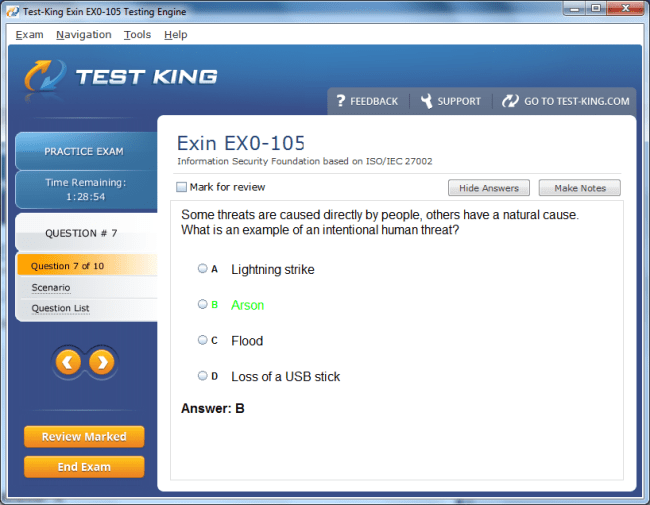
EX0-105 Exam Product Screenshots
Product Reviews
Passed My EX0-105 Exam
"Test king keep up the good work.Test king provide me such miraculous material thaa i complete my exam in one shot.A lots of thanks to you and your team. I have passed my EX0-105 exam.I am planning fro further exams as well and also will use test king forever.Test king is key to success.
James"
Good Material
"The Testking study package is highly affordable than all the study material I used. Testking does not compromise on quality.They provide free updates,audio exams,labs and simulations to help the student at maximum.it's a great experience overall.Thanks alot test king you simply rock
Edward"
Testking Made My Career!
"Thank YOU Testking for all your support in the EX0-105 exam. I remember how many questions I was able to attempt successfully only because I remembered I had studied them during the preparation from Testking’s study guide. You guys rock! – Stephen Nick"
I cleared with Testking
"I cleared my Exin EX0-105 exam today with stunning scores. Testing's Exin provided me comprehensive material which definitely help me to get the required place.Testking is best of all .All you people out there can use its study material to get success for sure."
Guys you are great!!!
"I must say that the work you guys are doing its great, I mean each and every concept you clear in such a way that no ambiguity left behind, I recently passed my EX0-105 exams with ravishing marks and I believe it's all due to Testking"
Frequently Asked Questions
How can I get the products after purchase?
All products are available for download immediately from your Member's Area. Once you have made the payment, you will be transferred to Member's Area where you can login and download the products you have purchased to your computer.
How long can I use my product? Will it be valid forever?
Test-King products have a validity of 90 days from the date of purchase. This means that any updates to the products, including but not limited to new questions, or updates and changes by our editing team, will be automatically downloaded on to computer to make sure that you get latest exam prep materials during those 90 days.
Can I renew my product if when it's expired?
Yes, when the 90 days of your product validity are over, you have the option of renewing your expired products with a 30% discount. This can be done in your Member's Area.
Please note that you will not be able to use the product after it has expired if you don't renew it.
How often are the questions updated?
We always try to provide the latest pool of questions, Updates in the questions depend on the changes in actual pool of questions by different vendors. As soon as we know about the change in the exam question pool we try our best to update the products as fast as possible.
How many computers I can download Test-King software on?
You can download the Test-King products on the maximum number of 2 (two) computers or devices. If you need to use the software on more than two machines, you can purchase this option separately. Please email support@test-king.com if you need to use more than 5 (five) computers.
What is a PDF Version?
PDF Version is a pdf document of Questions & Answers product. The document file has standart .pdf format, which can be easily read by any pdf reader application like Adobe Acrobat Reader, Foxit Reader, OpenOffice, Google Docs and many others.
Can I purchase PDF Version without the Testing Engine?
PDF Version cannot be purchased separately. It is only available as an add-on to main Question & Answer Testing Engine product.
What operating systems are supported by your Testing Engine software?
Our testing engine is supported by Windows. Andriod and IOS software is currently under development.
Top Exin Exams
Overview of EX0-105: What You Need to Know About the Information Security Foundation Exam
The EX0-105 examination, administered by EXIN, serves as a foundational assessment for individuals seeking to establish their proficiency in information security management aligned with ISO/IEC 27002 standards. The exam evaluates not only the comprehension of theoretical principles but also the ability to implement practical security measures within organizational structures. Information security, as delineated in ISO/IEC 27002, encompasses the systematic protection of information assets, mitigating risks from unauthorized access, disclosure, alteration, and destruction. The exam thus emphasizes both conceptual understanding and practical application, aiming to cultivate professionals who can contribute to the secure management of information resources.
Understanding the EX0-105 Examination and Its Significance
Candidates preparing for the EX0-105 must develop a thorough familiarity with the objectives and guidelines prescribed in ISO/IEC 27002. This international standard outlines best practices for establishing, implementing, maintaining, and continually improving an information security management system. While the framework offers structured guidance, it also encourages adaptability, acknowledging the dynamic nature of technological threats and organizational environments. The exam evaluates understanding of these principles and the ability to apply them in real-world scenarios, ensuring that certified individuals possess both analytical acumen and operational insight.
Core Domains Covered in EX0-105
The curriculum of the EX0-105 exam is organized around essential domains that define the scope of information security management. One of the primary areas concerns the assessment of information security risks and the development of strategies to mitigate vulnerabilities. Candidates are expected to understand the processes involved in identifying critical assets, evaluating threats and vulnerabilities, and determining the potential impact of security breaches. This necessitates a holistic understanding of organizational operations, technological infrastructures, and the interdependencies between systems and data.
Another pivotal domain is the establishment of security policies and procedures. ISO/IEC 27002 emphasizes the formulation of coherent policies that delineate responsibilities, define acceptable use, and prescribe the implementation of protective controls. For the EX0-105 candidate, this requires not only familiarity with policy frameworks but also the capacity to interpret these frameworks in light of organizational objectives and regulatory requirements. Policies must be comprehensive yet flexible, allowing for operational continuity while maintaining stringent safeguards against security incidents.
Physical and environmental security represents an additional domain within the examination syllabus. Candidates must comprehend the measures necessary to safeguard physical assets, such as servers, storage devices, and office environments, from unauthorized access, environmental hazards, and potential sabotage. Understanding the interplay between physical controls, environmental monitoring, and technological safeguards underscores the holistic approach of ISO/IEC 27002, where security is considered across multiple dimensions, from digital to tangible.
Human resource security constitutes another critical aspect of the EX0-105 content. The standard emphasizes that personnel play a central role in the protection of information. Recruitment processes, training programs, and ongoing awareness initiatives are instrumental in fostering a security-conscious organizational culture. Candidates are expected to appreciate the importance of background verification, role-specific security responsibilities, and continuous education, highlighting the human factor as both a potential vulnerability and a strategic asset in information security.
Access control mechanisms form a central theme in the examination. EX0-105 candidates must understand the principles of authentication, authorization, and accountability, ensuring that access to information and systems is appropriately restricted. This involves knowledge of user provisioning, password management, and the implementation of multi-factor authentication. Additionally, candidates are required to recognize the significance of monitoring and logging access activities, enabling timely detection and response to unauthorized attempts or anomalies in system usage.
Cryptography and secure communications are also encompassed within the domain structure. The exam evaluates knowledge of encryption techniques, digital signatures, and secure transmission protocols, emphasizing the protection of data both at rest and in transit. Candidates must be able to distinguish between symmetric and asymmetric encryption methods, understand key management principles, and appreciate the implications of cryptographic failures or weaknesses within organizational contexts.
Operational security and system acquisition, development, and maintenance constitute further key areas. This domain addresses the integration of security controls into operational processes, ensuring that security is not an afterthought but a fundamental component of system design and deployment. Candidates are expected to grasp the lifecycle of information systems, including the identification of security requirements during acquisition, the embedding of security in development processes, and the maintenance of safeguards during operational use. This holistic approach ensures continuity of protection and alignment with organizational risk management strategies.
Incident management and business continuity planning represent another area of focus for EX0-105 aspirants. The standard emphasizes proactive measures to detect, respond to, and recover from security incidents. Candidates must understand the procedures for incident reporting, investigation, and corrective action. Furthermore, they are expected to appreciate the interrelationship between incident management and business continuity planning, ensuring that critical operations can resume swiftly after disruptive events, thereby minimizing operational and reputational damage.
Compliance with legal, regulatory, and contractual obligations is interwoven throughout the exam objectives. EX0-105 evaluates a candidate’s awareness of statutory requirements related to information security, privacy, and data protection. This includes the capacity to identify relevant legislation, interpret obligations, and implement controls that satisfy compliance mandates. An understanding of audit mechanisms, reporting structures, and ethical considerations is equally emphasized, reinforcing the importance of accountability and governance in information security management.
Preparing for the EX0-105 Exam
Effective preparation for the EX0-105 examination demands a structured and immersive approach. Candidates are encouraged to engage with the ISO/IEC 27002 standard directly, studying its clauses, control objectives, and recommended practices. Complementary resources, such as official EXIN study guides, practice tests, and training courses, provide practical reinforcement, enabling learners to translate theoretical knowledge into applied understanding. The integration of real-world scenarios and case studies enhances cognitive retention, allowing candidates to appreciate the operational implications of abstract concepts.
Time management and strategic revision play pivotal roles in preparation. Candidates should prioritize areas of relative weakness while reinforcing foundational principles, ensuring comprehensive coverage across all domains. Utilizing spaced repetition, active recall, and scenario-based learning can enhance retention, particularly for nuanced topics such as cryptographic mechanisms, access control policies, and risk assessment methodologies. Participation in discussion forums or study groups may further enrich understanding, providing exposure to diverse perspectives and problem-solving approaches.
Familiarity with the exam format and question types is equally important. EX0-105 utilizes a combination of multiple-choice and scenario-based questions, assessing both knowledge recall and analytical aptitude. Candidates must develop proficiency in interpreting situational prompts, applying security principles contextually, and selecting the most appropriate responses. This requires a balance between speed and accuracy, as well as the ability to integrate theoretical understanding with practical reasoning.
Understanding common pitfalls and misconceptions can also enhance preparedness. Candidates may overemphasize technical controls while underestimating human factors, or they may misinterpret compliance obligations as purely procedural rather than strategic imperatives. Awareness of these tendencies enables learners to approach the exam holistically, ensuring that responses reflect both breadth and depth of understanding, and that knowledge is applied with discernment.
Practical exercises, including risk assessment simulations, policy drafting, and incident response drills, contribute significantly to readiness. Engaging with these exercises fosters a nuanced appreciation of how ISO/IEC 27002 controls manifest within organizational processes. Candidates gain insight into decision-making under uncertainty, the prioritization of security measures, and the alignment of operational actions with strategic objectives. This experiential approach bridges the gap between theoretical knowledge and real-world applicability, which is central to the philosophy underpinning EX0-105.
Continuous self-assessment is recommended throughout preparation. Regular evaluation of performance on practice tests and scenario-based exercises enables identification of knowledge gaps, misconceptions, and areas requiring reinforcement. Feedback loops, reflective learning, and iterative improvement ensure that preparation evolves in response to demonstrated proficiency, enhancing both confidence and competence.
Exam Day Strategy and Considerations
On the day of the EX0-105 examination, candidates must combine knowledge, strategy, and composure. Familiarity with administrative procedures, identification requirements, and time allocation ensures a smooth examination experience. Maintaining focus, managing anxiety, and pacing responses across the spectrum of questions contribute significantly to performance. Candidates should approach scenario-based questions with analytical clarity, applying principles judiciously rather than relying solely on memorized responses.
Understanding the weighting of exam domains can guide prioritization during the assessment. While all topics are important, allocating mental resources strategically allows for efficient management of time and cognitive load. Candidates benefit from reading questions thoroughly, identifying key contextual cues, and considering the implications of each potential answer within the framework of information security objectives. This disciplined approach reinforces the application-oriented ethos of ISO/IEC 27002, which emphasizes practical efficacy over rote knowledge.
Ethical considerations are paramount during the examination. Candidates are expected to demonstrate integrity, intellectual honesty, and adherence to examination rules. Beyond the assessment itself, this ethical orientation mirrors the professional conduct expected of information security practitioners, reinforcing the interconnection between certification and real-world professional responsibility.
Practical Applications of EX0-105 Certification
Attaining EX0-105 certification signals a candidate’s foundational competence in information security management. Certified individuals are better equipped to contribute to organizational initiatives such as risk assessment, policy development, and incident management. Employers recognize the value of such certification in enhancing security posture, ensuring compliance, and fostering a culture of vigilance. The knowledge gained through EX0-105 preparation equips practitioners to navigate the evolving landscape of cyber threats, regulatory mandates, and technological innovation.
Moreover, the certification lays the groundwork for advanced learning and specialization. Individuals may pursue higher-level certifications in information security, risk management, or auditing, leveraging the foundational understanding established through EX0-105. The blend of theoretical insight, practical reasoning, and professional awareness cultivated during preparation provides a versatile platform for continued career development in information security domains.
Conceptual Foundations of Information Security Management
Information security is no longer a peripheral concern but a central pillar of modern organizational governance. The EX0-105 examination, administered by EXIN, assesses foundational competence in this critical domain, emphasizing principles embedded in ISO/IEC 27002. At its core, information security management is the meticulous orchestration of policies, procedures, and technical safeguards to protect informational assets against a spectrum of threats. These threats are multifaceted, encompassing intentional breaches, inadvertent errors, and environmental hazards, and require a comprehensive understanding to manage effectively.
Candidates for the EX0-105 must appreciate the stratified nature of security controls. Preventive measures, such as access restrictions and encryption, coexist with detective mechanisms like monitoring and logging, and corrective strategies including incident response protocols. The synergy among these control categories is central to ISO/IEC 27002, which advocates a holistic perspective, ensuring that organizational operations are resilient against disruptions while preserving confidentiality, integrity, and availability of data. This conceptual framework forms the intellectual backbone for all subsequent operational applications tested in the examination.
Risk Assessment and Management
Risk management is an indispensable component of information security, demanding analytical rigor and strategic foresight. EX0-105 candidates are expected to grasp the methodologies for identifying assets of critical value, assessing vulnerabilities, and evaluating potential threats. This process involves estimating the likelihood and potential impact of security incidents, thus informing the prioritization of protective measures. Effective risk assessment requires both quantitative metrics and qualitative judgment, balancing statistical analysis with an understanding of organizational context and human behavior.
ISO/IEC 27002 emphasizes that risk management is iterative and dynamic. As technological landscapes evolve, so too must the strategies to mitigate emerging threats. EX0-105 evaluates the candidate’s ability to integrate risk assessments into broader operational planning, ensuring that controls are both proportionate and adaptable. Practical scenarios in the exam often simulate real-world dilemmas, requiring the candidate to weigh the consequences of resource allocation, system vulnerabilities, and policy enforcement, underscoring the necessity for both methodical reasoning and situational acuity.
Policies and Organizational Governance
Establishing robust information security policies is pivotal for embedding a culture of vigilance and compliance. Candidates for EX0-105 must understand how policy frameworks articulate organizational expectations, delineate responsibilities, and guide behavior across all levels of operation. These policies, aligned with ISO/IEC 27002, serve as both preventive and prescriptive instruments, codifying standards for system access, data handling, and procedural adherence.
Organizational governance in information security extends beyond policy formulation to encompass accountability mechanisms, oversight committees, and communication channels. EX0-105 examines the candidate’s ability to interpret governance structures, ensuring that security initiatives are integrated into strategic planning and operational workflows. The creation of clear reporting hierarchies, documentation of responsibilities, and maintenance of compliance audits fosters transparency, reduces ambiguity, and strengthens the overall security posture.
Physical and Environmental Safeguards
While digital defenses often dominate discourse, physical and environmental controls remain fundamental to a comprehensive security strategy. The EX0-105 curriculum underscores measures to safeguard tangible assets, including servers, storage media, and network infrastructure, against unauthorized access and environmental hazards. Candidates are expected to understand access restrictions, surveillance mechanisms, and climate-control measures that mitigate risks such as fire, water damage, and electrical disturbances.
ISO/IEC 27002 emphasizes the symbiosis between physical and technological safeguards. Physical breaches can undermine even the most sophisticated digital protections, while environmental risks, such as temperature fluctuations or humidity, may compromise hardware integrity. The exam evaluates the candidate’s comprehension of these interdependencies, ensuring that individuals can implement layered controls that fortify both the tangible and intangible dimensions of information security.
Human-Centric Security Controls
Humans are simultaneously the greatest asset and the most significant vulnerability in information security ecosystems. EX0-105 candidates are required to understand the spectrum of measures that promote personnel vigilance and mitigate insider risks. Recruitment procedures, background verification, role-based access control, and continuous training are essential to cultivating a security-conscious workforce. Awareness programs, simulated phishing exercises, and structured induction sessions reinforce the principles codified in ISO/IEC 27002, translating abstract policy into everyday operational conduct.
The human factor also entails understanding behavioral tendencies that may compromise security, such as inadvertent errors, social engineering susceptibility, or resistance to procedural compliance. Candidates must demonstrate the ability to integrate preventive measures, continuous education, and monitoring strategies to align personnel behavior with organizational objectives. This focus on human-centric controls reflects the standard’s emphasis on comprehensive risk management that extends beyond technical instrumentation.
Access Control and Authentication
Access control mechanisms are the linchpin of information security. The EX0-105 examination examines candidate knowledge of authentication, authorization, and accountability protocols. Effective access control ensures that only duly authorized individuals can interact with sensitive data, while all interactions are traceable for audit purposes. The implementation of multi-factor authentication, granular user permissions, and role-specific access delineation exemplifies ISO/IEC 27002 guidance, balancing security imperatives with operational efficiency.
Candidates are also expected to understand the lifecycle of access management, from provisioning and modification to revocation, including the monitoring of anomalous behaviors and unauthorized attempts. The exam often presents situational questions, requiring analysis of complex access scenarios, decision-making under uncertainty, and alignment with organizational risk tolerance. Mastery of these principles underscores a candidate’s readiness to safeguard critical informational assets against misuse or compromise.
Cryptographic Techniques and Secure Communication
Encryption and secure communication protocols represent a sophisticated layer of protection that underpins modern information security. EX0-105 assesses understanding of both symmetric and asymmetric cryptography, key management strategies, and digital signatures, emphasizing data protection in transit and at rest. The practical application of these cryptographic principles requires comprehension of algorithmic strength, vulnerability assessment, and compliance with regulatory mandates.
Secure communications extend beyond encryption to include network segmentation, secure tunneling, and monitoring for potential intrusions. Candidates must appreciate how cryptographic techniques interact with broader operational controls, ensuring that confidentiality, integrity, and availability are maintained without hindering legitimate workflows. ISO/IEC 27002 underscores that cryptography is a tool for enabling trust and resilience within organizational communications, rather than an isolated technical solution.
System Acquisition, Development, and Maintenance
Integrating security considerations into system lifecycle processes is a hallmark of information security maturity. The EX0-105 curriculum addresses the embedding of controls during system acquisition, software development, and ongoing maintenance. This includes evaluating vendor security posture, specifying security requirements in procurement contracts, and implementing secure coding practices that mitigate vulnerabilities. Maintenance protocols, such as patch management, configuration auditing, and vulnerability scanning, further reinforce operational security, ensuring resilience against emerging threats.
The standard advocates a proactive approach, whereby security is designed into systems rather than retrofitted post-deployment. Candidates are evaluated on their ability to identify potential threats throughout the system lifecycle, prioritize security requirements, and ensure alignment with organizational objectives. This integrated perspective reflects the pragmatic ethos of ISO/IEC 27002, linking technical rigor with strategic foresight.
Incident Management and Business Continuity
Resilience is central to the philosophy of ISO/IEC 27002, encompassing the capacity to detect, respond to, and recover from incidents. EX0-105 emphasizes the design of incident management frameworks, including protocols for detection, reporting, investigation, and corrective action. Candidates are expected to appreciate the interrelationship between incident response and business continuity planning, ensuring that critical operations can continue with minimal disruption following a security event.
Effective incident management requires coordination across technical, organizational, and human dimensions. Candidates must understand escalation procedures, stakeholder communication, and post-incident evaluation, integrating lessons learned into continuous improvement processes. This dynamic approach underscores the adaptive nature of information security, preparing practitioners to navigate unpredictable scenarios with composure and efficacy.
Compliance and Regulatory Awareness
Understanding legal, regulatory, and contractual obligations is integral to information security governance. EX0-105 evaluates candidate familiarity with data protection laws, industry-specific regulations, and contractual mandates. Awareness extends beyond mere compliance, encompassing the strategic alignment of security initiatives with ethical standards, audit readiness, and accountability frameworks.
ISO/IEC 27002 advocates a risk-informed compliance strategy, whereby controls are implemented not simply to meet regulatory requirements but to enhance organizational resilience and stakeholder trust. Candidates are expected to recognize the implications of non-compliance, including reputational, financial, and operational consequences, and to integrate regulatory considerations into policy formulation, risk management, and operational procedures.
Preparation Strategies and Knowledge Reinforcement
Achieving proficiency for the EX0-105 examination necessitates deliberate study and reflective practice. Candidates are encouraged to engage deeply with the ISO/IEC 27002 standard, translating its principles into applied scenarios. Practice tests, case studies, and scenario-based exercises reinforce analytical reasoning and operational judgment, bridging the gap between theoretical knowledge and practical application.
Time management, iterative review, and targeted focus on weaker areas are essential for maximizing preparation efficacy. Participating in discussion forums, workshops, and collaborative study sessions provides exposure to diverse interpretations, practical challenges, and innovative solutions. Continuous self-assessment ensures that knowledge acquisition is active rather than passive, enhancing retention and readiness for the comprehensive evaluation that EX0-105 represents.
Exam Day Tactics and Cognitive Approach
During the examination, candidates must combine knowledge mastery with strategic acumen. Understanding the context of each question, evaluating scenarios critically, and applying ISO/IEC 27002 principles judiciously are key to effective performance. The ability to manage time, remain composed, and respond analytically under pressure reflects not only preparedness but also professional maturity.
Ethical considerations remain integral, as candidates are expected to demonstrate integrity and adherence to testing protocols. This professional orientation mirrors real-world expectations for information security practitioners, reinforcing the link between certification and responsible conduct in safeguarding organizational assets.
Professional Benefits of EX0-105 Certification
EX0-105 certification signifies foundational competence in information security management, offering tangible benefits for career progression. Certified individuals are well-positioned to contribute to risk assessment, policy development, incident management, and compliance initiatives within diverse organizational contexts. Employers recognize the value of such certification in reinforcing operational security, regulatory adherence, and strategic resilience.
The knowledge and skills developed through EX0-105 preparation also establish a springboard for advanced specialization in domains such as risk management, cybersecurity, auditing, and governance. The combination of theoretical understanding, practical reasoning, and ethical orientation equips practitioners to navigate complex challenges, adapt to evolving threats, and contribute meaningfully to organizational security objectives.
Intricacies of Information Security Governance
Information security governance embodies the strategic orchestration of policies, processes, and practices that ensure the protection and resilient management of informational assets. Within the context of EX0-105, candidates are assessed on their comprehension of ISO/IEC 27002, which emphasizes the integration of governance into organizational strategy rather than treating security as a peripheral function. Governance entails delineating clear accountability structures, establishing coherent reporting channels, and embedding security objectives into overarching corporate objectives, fostering a culture of vigilance and operational prudence.
EXIN’s examination framework evaluates the capacity to interpret these principles in practical terms. Candidates must understand the roles and responsibilities at various organizational levels, including senior management oversight, operational control, and compliance monitoring. Governance is not merely about control but also about fostering a proactive environment where security decisions are informed by risk assessment, ethical considerations, and regulatory obligations, ensuring a holistic and anticipatory approach to organizational protection.
Strategic Risk Assessment and Prioritization
Central to EX0-105 is the nuanced understanding of risk assessment methodologies. Candidates are expected to identify, quantify, and prioritize risks in alignment with organizational objectives and regulatory requirements. ISO/IEC 27002 provides a structured approach to risk management, emphasizing the iterative evaluation of threats, vulnerabilities, and potential impacts on informational assets. Candidates must comprehend both qualitative and quantitative methods, incorporating scenario analysis, probability estimation, and impact evaluation into actionable security strategies.
Effective risk prioritization requires discerning judgment. Candidates must balance the allocation of resources against the severity of potential threats, recognizing that overinvestment in low-impact areas or underestimation of high-risk exposures can jeopardize organizational resilience. The EX0-105 assessment often includes scenario-based questions that challenge candidates to integrate risk evaluation with operational decision-making, reinforcing the practical applicability of theoretical frameworks.
Policies, Standards, and Procedural Frameworks
Developing and enforcing comprehensive policies is an essential competency tested in EX0-105. Policies codify expectations, provide operational guidance, and ensure consistency across organizational processes. ISO/IEC 27002 emphasizes alignment between policies and control objectives, ensuring that protective measures are coherent, enforceable, and adaptable. Candidates are expected to demonstrate the ability to craft policy frameworks that encompass data handling, system usage, access control, incident reporting, and compliance obligations.
In addition to overarching policies, the standard highlights the importance of detailed procedural frameworks. Procedures operationalize policy, providing step-by-step guidance for employees to follow in executing security measures. EXIN evaluates the candidate’s understanding of how procedures support policy objectives, facilitate training, and enable accountability. By linking strategic intent to operational execution, candidates illustrate their readiness to bridge the conceptual and practical dimensions of information security.
Asset Management and Classification
A foundational element of EX0-105 is the identification and management of organizational assets. ISO/IEC 27002 underscores the importance of cataloging information assets, assessing their value, and implementing appropriate protective measures. Candidates must understand the principles of asset classification, assigning sensitivity levels and access requirements that reflect organizational priorities and risk exposure. Effective asset management ensures that protective measures are proportionate to the criticality of information, optimizing security investment while mitigating potential losses.
This domain also entails ongoing monitoring and maintenance of asset registers, ensuring that changes in asset value, location, or operational significance are promptly reflected in security controls. Candidates are evaluated on their capacity to implement dynamic asset management practices, integrating these with risk assessments, access control strategies, and incident response planning. By adopting a comprehensive perspective, candidates demonstrate their ability to safeguard organizational resources with both precision and foresight.
Human Resource Security and Organizational Culture
Personnel represent both the linchpin and potential vulnerability within information security ecosystems. EX0-105 assesses the candidate’s understanding of the mechanisms to cultivate a security-conscious workforce. Recruitment practices, background checks, induction programs, and role-specific security training are integral to establishing a resilient human resource framework. Continuous education, awareness campaigns, and reinforcement of policy compliance further embed security principles into organizational culture.
ISO/IEC 27002 emphasizes that security culture extends beyond formal training to encompass behavioral reinforcement, ethical orientation, and accountability. Candidates must appreciate the subtle interplay between individual actions, group norms, and organizational expectations, recognizing that human factors often dictate the success or failure of security initiatives. EXIN evaluates the ability to implement human-centric security strategies that are both proactive and adaptive, ensuring alignment with organizational objectives.
Access Control Mechanisms and Identity Management
Access control forms a core domain of the EX0-105 curriculum. Candidates must demonstrate an understanding of authentication, authorization, and accountability mechanisms designed to restrict information access to authorized personnel. ISO/IEC 27002 emphasizes role-based access control, segregation of duties, and the principle of least privilege, ensuring that users have appropriate access aligned with their responsibilities.
In practical terms, this entails managing user accounts, implementing multi-factor authentication, monitoring access activity, and maintaining comprehensive audit trails. EXIN examines candidate proficiency in designing, executing, and sustaining access control frameworks, as well as evaluating their effectiveness over time. The integration of identity management solutions with broader security architecture illustrates the convergence of technical and administrative controls, reinforcing organizational resilience.
Cryptography, Data Protection, and Secure Communications
Data protection and secure communications are indispensable in the contemporary information security landscape. EX0-105 examines candidate knowledge of cryptographic principles, including symmetric and asymmetric encryption, digital signatures, and key management. ISO/IEC 27002 provides guidance for implementing cryptographic controls, ensuring the confidentiality, integrity, and availability of sensitive information across diverse operational contexts.
Secure communication extends to network protection, encryption of data in transit, and the implementation of secure protocols for organizational interactions. Candidates must also comprehend potential vulnerabilities in cryptographic systems, evaluating the adequacy of algorithms, key lengths, and usage policies. EXIN evaluates practical understanding, ensuring that candidates can apply cryptographic measures effectively, balancing technical feasibility with operational necessity.
Operational Security and System Lifecycle Management
The security of information systems is contingent upon comprehensive management throughout the system lifecycle. EX0-105 encompasses the integration of security considerations into system acquisition, development, deployment, and maintenance. Candidates are expected to understand security requirements during procurement, implement secure coding practices, and ensure ongoing protection through patch management, configuration control, and vulnerability assessment.
ISO/IEC 27002 emphasizes that operational security is not static but evolves alongside emerging threats, system modifications, and organizational changes. EXIN evaluates the ability to anticipate potential vulnerabilities, implement preventive measures, and integrate continuous improvement practices into system management. Candidates must demonstrate both conceptual understanding and practical readiness to manage complex systems securely and efficiently.
Incident Response, Business Continuity, and Resilience
Resilience underpins the ethos of information security. EX0-105 emphasizes incident management, including detection, reporting, investigation, and corrective action. Candidates must understand the interconnection between incident response and business continuity planning, ensuring that critical functions can continue with minimal disruption following a security breach or operational failure.
ISO/IEC 27002 advocates structured incident response protocols, incorporating escalation procedures, stakeholder communication, and post-event evaluation. Candidates are assessed on their ability to design and implement frameworks that integrate technical, procedural, and human considerations, enabling timely recovery and minimizing organizational impact. This proactive and structured approach cultivates an adaptive security posture capable of responding effectively to unforeseen challenges.
Compliance, Legal, and Regulatory Awareness
Information security exists within a complex regulatory landscape. EX0-105 evaluates candidate awareness of statutory, contractual, and regulatory requirements relevant to data protection and organizational security. ISO/IEC 27002 underscores the necessity of integrating compliance considerations into policies, procedures, and operational practices.
Candidates must understand the implications of non-compliance, ranging from legal penalties to reputational damage, and develop mechanisms to ensure adherence to obligations. This includes the design of audit processes, documentation practices, and accountability structures. EXIN examines the candidate’s capacity to synthesize regulatory understanding with practical controls, ensuring that organizational security is both legally sound and operationally effective.
Preparing for Examination Excellence
Achieving proficiency for EX0-105 requires disciplined study and practical engagement. Candidates are encouraged to immerse themselves in ISO/IEC 27002, translating standards into operational scenarios. Practice exercises, case analyses, and simulated risk assessments reinforce cognitive understanding and applied problem-solving.
Structured study approaches, including targeted revision, iterative review, and reflective practice, are essential for consolidating knowledge across all domains. Participation in professional forums, discussion groups, and collaborative exercises exposes candidates to diverse operational challenges and solutions, fostering adaptive reasoning and practical insight. Continuous self-assessment ensures that preparation is iterative, responsive, and aligned with the analytical demands of EXIN’s examination framework.
Examination Tactics and Cognitive Approach
EX0-105 requires not only knowledge mastery but also strategic thinking and composure under pressure. Candidates must approach scenario-based questions analytically, applying principles judiciously while evaluating contextual nuances. Effective time management, prioritization, and structured reasoning are vital for navigating the complexity of the examination while maintaining accuracy and clarity.
Ethical integrity is integral to performance, reflecting the professional expectations of information security practitioners. Candidates must demonstrate intellectual honesty, adherence to procedural guidelines, and accountability, reinforcing the alignment between certification and real-world responsibility in safeguarding organizational assets.
Professional Advantages of Certification
EX0-105 certification signals a robust foundation in information security principles, offering tangible benefits for career development. Certified individuals are well-positioned to contribute to risk assessment, policy formulation, incident management, and regulatory compliance within diverse organizational contexts. Employers recognize the value of this credential in strengthening operational security, promoting resilience, and enhancing strategic alignment.
Beyond immediate professional utility, EX0-105 provides a platform for continued specialization in cybersecurity, risk management, governance, and auditing. The integration of theoretical understanding, practical acumen, and ethical awareness equips practitioners to navigate complex challenges, adapt to evolving threats, and contribute meaningfully to organizational objectives, reinforcing the centrality of information security in contemporary enterprise environments.
Conceptual Architecture of Information Security
Information security represents a strategic convergence of policy, technology, and human behavior aimed at safeguarding organizational assets against multifarious threats. The EX0-105 examination, administered by EXIN, evaluates foundational expertise in aligning security initiatives with ISO/IEC 27002 principles, ensuring that candidates grasp the intricate interdependencies between governance, risk, and operational controls. The framework encourages practitioners to consider security as a dynamic continuum, integrating preventive, detective, and corrective measures to uphold confidentiality, integrity, and availability across organizational contexts.
Candidates must appreciate the stratification of security controls, which encompasses technical defenses such as encryption and access management, administrative mechanisms including policies and procedural guidance, and physical measures addressing environmental and infrastructural vulnerabilities. The interplay among these domains fosters a holistic approach, emphasizing proactive anticipation of threats, structured mitigation strategies, and agile adaptation to evolving risk landscapes.
Risk Assessment and Threat Modeling
A cardinal element of EX0-105 is the systematic identification and evaluation of risks. ISO/IEC 27002 delineates processes for cataloging assets, analyzing threats, assessing vulnerabilities, and estimating potential impact. Candidates are expected to synthesize both qualitative and quantitative insights, translating complex datasets into actionable mitigation strategies. The examination frequently challenges aspirants to weigh resource allocation against risk severity, necessitating discernment in balancing protective measures with operational feasibility.
Threat modeling, a critical facet of risk assessment, involves envisioning potential attack vectors, insider threats, and environmental hazards. Candidates are required to assess both technical and human dimensions, recognizing that organizational vulnerabilities often arise from procedural lapses or behavioral oversights. EX0-105 emphasizes scenario-based reasoning, compelling candidates to simulate real-world dilemmas, prioritize interventions, and justify decisions in accordance with ISO/IEC 27002 guidance.
Policies, Governance, and Ethical Frameworks
Developing coherent policies and governance structures is pivotal in embedding a culture of accountability and vigilance. EX0-105 examines candidates’ capacity to formulate policies that articulate responsibilities, codify operational norms, and provide guidance for security practices. ISO/IEC 27002 highlights the necessity of aligning these policies with strategic objectives while ensuring flexibility to accommodate evolving operational contexts.
Governance extends beyond policy creation to include oversight mechanisms, reporting channels, and evaluation frameworks. Candidates must understand the orchestration of governance committees, the delineation of roles and responsibilities, and the integration of security oversight into corporate decision-making processes. Ethical considerations are intertwined with governance, as candidates are expected to ensure that security decisions respect legal mandates, organizational integrity, and stakeholder trust.
Asset Management and Classification
The identification, classification, and management of organizational assets are central to robust information security. EX0-105 assesses the ability to categorize assets by sensitivity, operational importance, and potential risk exposure. ISO/IEC 27002 advocates a structured approach to asset management, ensuring that protective measures correspond proportionately to asset value and criticality.
Candidates are also required to implement dynamic asset registers, reflecting changes in asset usage, location, and significance. Integrating asset management with risk assessment, access control, and incident response processes enhances organizational resilience, ensuring that resources are allocated efficiently and that critical information remains safeguarded against unauthorized access, loss, or compromise.
Human Resource Security and Behavioral Considerations
Personnel constitute a pivotal element in the security ecosystem, serving as both the most significant vulnerability and the primary line of defense. EX0-105 evaluates the candidate’s understanding of mechanisms to cultivate a security-conscious workforce. Recruitment protocols, background verification, role-specific training, continuous awareness campaigns, and ethical orientation are all essential in shaping human-centric security strategies.
ISO/IEC 27002 underscores the necessity of fostering a culture of vigilance where personnel comprehend their responsibilities, internalize security norms, and actively participate in safeguarding information. Candidates must recognize the interplay between behavioral tendencies, organizational culture, and procedural enforcement, appreciating that human actions significantly influence the efficacy of technological and administrative controls.
Access Control, Authentication, and Authorization
Access control is a foundational component of organizational security, ensuring that information and systems are available only to authorized personnel. EX0-105 assesses knowledge of authentication methods, authorization frameworks, and accountability mechanisms that enforce the principle of least privilege. Role-based access, segregation of duties, and systematic monitoring of access activities constitute critical elements evaluated by EXIN.
Candidates are also expected to manage the lifecycle of access rights, from provisioning to revocation, and to implement monitoring mechanisms that detect anomalies or unauthorized attempts. ISO/IEC 27002 emphasizes the importance of aligning access controls with organizational risk appetite, operational requirements, and regulatory obligations, fostering a secure environment without impeding workflow efficiency.
Cryptography and Secure Communication
Encryption and secure communication protocols constitute an advanced layer of information protection. EX0-105 examines candidates’ understanding of symmetric and asymmetric encryption, digital signatures, key management, and secure data transmission. ISO/IEC 27002 provides a framework for implementing cryptographic controls that ensure confidentiality, integrity, and availability, emphasizing alignment with organizational objectives and compliance requirements.
Candidates must also comprehend vulnerabilities associated with cryptographic mechanisms, evaluating algorithm robustness, key lifecycle management, and potential operational challenges. Secure communications extend to network security, secure tunneling, and monitoring of transmission channels, reflecting a comprehensive approach that integrates technical safeguards with strategic operational oversight.
Operational Security and System Lifecycle Integration
The integration of security within system acquisition, development, and operational maintenance is emphasized in EX0-105. Candidates are expected to understand security requirements during procurement, secure software development practices, and ongoing maintenance protocols including patch management, configuration auditing, and vulnerability scanning. ISO/IEC 27002 advocates embedding security into system lifecycle processes, ensuring proactive mitigation rather than reactive remediation.
Operational security also encompasses monitoring, logging, and incident detection within active systems. Candidates must appreciate the interdependencies between technological infrastructure, human behavior, and organizational procedures, implementing controls that maintain continuity, resilience, and regulatory compliance throughout system operation.
Incident Management and Business Continuity
Resilient organizations anticipate, detect, and respond to incidents effectively. EX0-105 examines incident management strategies, encompassing detection, reporting, investigation, containment, and remediation. ISO/IEC 27002 emphasizes that incident response must be integrated with business continuity planning to ensure rapid recovery and minimal operational disruption.
Candidates are expected to develop frameworks for escalation, stakeholder communication, and post-incident evaluation, translating lessons learned into continuous improvement. By aligning incident management with strategic objectives and operational priorities, practitioners foster an adaptive security posture capable of responding to both expected and unforeseen disruptions.
Compliance, Legal Mandates, and Regulatory Alignment
Understanding and adhering to legal, regulatory, and contractual obligations is a critical competency for EX0-105 candidates. ISO/IEC 27002 highlights the importance of aligning organizational practices with statutory requirements, industry regulations, and internal policies. Candidates must comprehend the consequences of non-compliance, including legal penalties, financial loss, and reputational damage.
EXIN evaluates the ability to implement compliance mechanisms that integrate audit readiness, documentation, and accountability. Candidates must be capable of translating regulatory frameworks into operational controls that not only satisfy statutory mandates but also enhance organizational resilience and stakeholder confidence.
Exam Preparation Techniques
Effective preparation for EX0-105 requires immersive study and practical application. Candidates are encouraged to engage directly with ISO/IEC 27002, translating theoretical principles into real-world scenarios. Practice exercises, case studies, and simulated risk assessments provide the cognitive scaffolding necessary to approach the examination analytically and contextually.
Structured study approaches, iterative revision, and continuous self-assessment reinforce comprehension and retention. Engaging with professional forums, discussion groups, and collaborative exercises exposes candidates to diverse interpretations, practical challenges, and innovative solutions. This iterative approach fosters adaptive reasoning, ensuring that knowledge is both deep and operationally relevant.
Exam Strategy and Analytical Approach
During the EX0-105 examination, candidates must combine conceptual understanding with analytical precision. Scenario-based questions require evaluation of contextual cues, application of ISO/IEC 27002 principles, and strategic reasoning. Time management, prioritization, and disciplined reflection are essential for navigating complex scenarios while maintaining accuracy and clarity.
Ethical integrity remains paramount. Candidates are expected to demonstrate intellectual honesty, adherence to examination procedures, and professional accountability. These qualities mirror the expectations of real-world information security practitioners, reinforcing the alignment between certification and operational responsibility in safeguarding organizational assets.
Career Advantages and Professional Application
Attaining EX0-105 certification affirms foundational expertise in information security, offering tangible professional benefits. Certified individuals are equipped to contribute meaningfully to risk assessment, policy formulation, incident management, and regulatory compliance initiatives. Employers value the credential for its demonstration of analytical rigor, operational readiness, and strategic understanding of security principles.
The certification also provides a foundation for further specialization in areas such as cybersecurity, auditing, governance, and risk management. The blend of theoretical insight, practical acumen, and ethical awareness cultivated through EX0-105 preparation positions practitioners to navigate complex challenges, adapt to evolving threats, and enhance organizational resilience, reflecting the enduring value of ISO/IEC 27002-aligned knowledge in contemporary enterprise environments.
Fundamental Concepts of Information Security
Information security constitutes a multifaceted discipline aimed at safeguarding informational assets through the judicious implementation of policies, procedures, and technical safeguards. The EX0-105 examination, offered by EXIN, evaluates foundational proficiency in the principles articulated in ISO/IEC 27002, emphasizing the integration of governance, risk management, and operational controls into organizational structures. Candidates are expected to appreciate the nuanced interplay between preventive, detective, and corrective measures, ensuring confidentiality, integrity, and availability across diverse operational contexts.
Security management extends beyond the mere deployment of technical solutions. It encompasses strategic planning, ethical stewardship, and operational vigilance. Candidates must understand the hierarchy of controls, encompassing administrative, physical, and technological measures, each reinforcing the other to create a resilient ecosystem capable of mitigating both predictable and unforeseen threats.
Strategic Risk Assessment and Threat Prioritization
A core element of EX0-105 involves systematic risk assessment and prioritization. ISO/IEC 27002 provides methodologies for identifying critical assets, evaluating vulnerabilities, and estimating the potential impact of security incidents. Candidates are expected to employ both qualitative and quantitative approaches, integrating probabilistic assessments with scenario-based analysis to inform resource allocation and mitigation strategies.
Threat prioritization requires analytical acuity and practical judgment. Candidates must discern which vulnerabilities pose the greatest risk to operational continuity and organizational objectives. EXIN evaluates the ability to integrate risk assessment with operational planning, requiring candidates to make decisions that balance effectiveness, efficiency, and feasibility within the constraints of organizational resources.
Policies, Governance Structures, and Ethical Imperatives
Formulating coherent policies and governance frameworks is pivotal for embedding a culture of accountability and proactive vigilance. EX0-105 examines candidates’ understanding of how policies delineate responsibilities, codify operational norms, and guide decision-making across organizational hierarchies. ISO/IEC 27002 emphasizes the alignment of policies with strategic objectives while allowing adaptability to accommodate evolving operational landscapes.
Governance structures extend to oversight committees, reporting channels, and monitoring mechanisms. Candidates are expected to understand the orchestration of governance responsibilities, ensuring that security initiatives are systematically reviewed, assessed, and refined. Ethical considerations are interwoven into governance practices, compelling candidates to ensure that decisions respect legal mandates, organizational integrity, and stakeholder trust.
Asset Management and Classification Strategies
Effective asset management constitutes a foundational pillar of information security. EX0-105 evaluates candidates’ ability to identify, classify, and manage informational and physical assets based on sensitivity, criticality, and exposure to risk. ISO/IEC 27002 prescribes structured approaches for cataloging assets, assigning classification levels, and implementing protective measures commensurate with organizational priorities.
Dynamic asset registers, which account for changes in usage, location, or operational significance, are essential for maintaining an accurate security posture. Integration of asset management with risk assessment, access control, and incident response ensures a cohesive protective framework. Candidates are expected to demonstrate both conceptual understanding and practical application of these strategies in simulated scenarios reflective of real-world challenges.
Human Resource Security and Organizational Culture
Human resources represent both a strategic asset and a potential vulnerability. EX0-105 assesses candidates’ understanding of mechanisms to cultivate a security-conscious workforce, including recruitment protocols, background checks, induction programs, role-specific training, and continuous awareness initiatives. ISO/IEC 27002 highlights the importance of embedding security into organizational culture, where personnel comprehend responsibilities, internalize norms, and actively participate in safeguarding information.
Behavioral insights are critical, as human actions often dictate the effectiveness of technological and administrative controls. Candidates must appreciate the interplay between individual behavior, group dynamics, and procedural enforcement, designing strategies that reinforce vigilance, accountability, and ethical decision-making within the workforce.
Access Control, Authentication, and Authorization
Access control remains a cornerstone of information security. EX0-105 examines knowledge of authentication, authorization, and accountability mechanisms that enforce the principle of least privilege. ISO/IEC 27002 emphasizes role-based access, segregation of duties, and systematic monitoring of access activity, ensuring that users interact with systems and data commensurate with their responsibilities.
Candidates are also expected to manage the entire lifecycle of access rights, from provisioning and modification to revocation. Monitoring and logging mechanisms facilitate the detection of anomalies or unauthorized attempts, reinforcing organizational resilience. Practical scenarios in EX0-105 require analytical evaluation of complex access situations, integrating technical and administrative considerations to maintain operational security.
Cryptography, Data Protection, and Secure Communication
Cryptographic techniques constitute a sophisticated layer of information security. EX0-105 evaluates understanding of symmetric and asymmetric encryption, digital signatures, key management, and secure transmission protocols. ISO/IEC 27002 prescribes cryptographic controls that ensure confidentiality, integrity, and availability of data while remaining aligned with organizational requirements and compliance obligations.
Secure communication extends beyond encryption, encompassing network segmentation, secure tunneling, and continuous monitoring for potential breaches. Candidates must also assess cryptographic vulnerabilities, algorithm robustness, and operational feasibility. EXIN emphasizes the application of cryptography within broader organizational frameworks, integrating technical safeguards with strategic objectives.
Operational Security and System Lifecycle Management
Embedding security throughout the system lifecycle is essential for sustainable protection. EX0-105 examines the integration of security considerations in system acquisition, development, deployment, and maintenance. Candidates must comprehend secure coding practices, procurement evaluation, patch management, configuration auditing, and vulnerability assessment as continuous processes rather than discrete actions.
ISO/IEC 27002 underscores that operational security is an evolving discipline, requiring monitoring, iterative improvement, and alignment with organizational changes. Candidates are evaluated on their ability to implement controls that maintain operational continuity, resilience, and regulatory compliance, ensuring that security is proactive rather than reactive.
Incident Management and Business Continuity Planning
Resilient organizations anticipate and respond effectively to incidents. EX0-105 evaluates understanding of incident management, including detection, reporting, investigation, containment, and remediation. ISO/IEC 27002 highlights the importance of integrating incident management with business continuity planning to minimize operational disruption.
Candidates are expected to design frameworks for escalation, stakeholder communication, and post-incident evaluation. Lessons learned from incidents must inform continuous improvement and operational refinement. This dynamic, anticipatory approach equips candidates to navigate complex security scenarios, balancing analytical rigor with practical execution.
Legal, Regulatory, and Compliance Awareness
Compliance forms a critical dimension of information security. EX0-105 assesses awareness of statutory requirements, industry regulations, and contractual obligations. ISO/IEC 27002 emphasizes embedding compliance into policies, procedures, and operational practices, ensuring adherence to legal mandates while enhancing organizational resilience.
Candidates must understand the implications of non-compliance, including legal, financial, and reputational consequences. Implementation of audit mechanisms, documentation practices, and accountability structures ensures that regulatory obligations are met systematically. EXIN evaluates the candidate’s capacity to synthesize compliance considerations with practical security measures, creating a robust and legally sound operational environment.
Preparation and Knowledge Reinforcement Techniques
Success in EX0-105 requires structured study and applied practice. Candidates are encouraged to engage thoroughly with ISO/IEC 27002, converting theoretical principles into actionable scenarios. Practice exercises, case studies, and simulated risk assessments reinforce analytical reasoning and applied understanding.
Iterative review, targeted revision, and continuous self-assessment enhance retention and readiness. Participation in professional forums and collaborative exercises exposes candidates to diverse perspectives, problem-solving approaches, and operational insights. This comprehensive preparation ensures that candidates are equipped to navigate the examination’s analytical and scenario-based challenges effectively.
Examination Strategy and Cognitive Approach
EX0-105 demands both knowledge mastery and strategic reasoning. Scenario-based questions require evaluation of contextual cues, application of ISO/IEC 27002 principles, and analytical judgment. Effective time management, prioritization, and structured reasoning are critical for maintaining accuracy and clarity throughout the examination.
Candidates must also demonstrate ethical integrity, reflecting professional expectations of information security practitioners. Intellectual honesty, adherence to examination procedures, and accountability reinforce the alignment between certification and operational responsibility in safeguarding organizational assets.
Professional Value and Career Advancement
EX0-105 certification validates foundational expertise in information security, conferring tangible professional benefits. Certified individuals are positioned to contribute to risk assessment, policy development, incident management, and regulatory compliance. Employers value the credential for its demonstration of analytical rigor, operational readiness, and strategic understanding of security principles.
Beyond immediate practical utility, EX0-105 provides a foundation for specialization in cybersecurity, governance, auditing, and risk management. Candidates cultivate theoretical knowledge, applied skills, and ethical awareness, equipping them to navigate evolving threats, enhance organizational resilience, and contribute strategically to enterprise security objectives.
Holistic Principles of Information Security
Information security is an intricate discipline that synthesizes governance, technical controls, human factors, and operational strategy to safeguard organizational assets. EX0-105, offered by EXIN, tests foundational knowledge aligned with ISO/IEC 27002, emphasizing the integration of these principles into cohesive, operationally effective security frameworks. Candidates are expected to appreciate the multidimensional nature of security, balancing preventive, detective, and corrective mechanisms to maintain confidentiality, integrity, and availability across diverse organizational systems.
ISO/IEC 27002 underscores that effective security is not merely a technical endeavor; it requires the orchestration of policy, culture, and procedural rigor. Administrative controls, physical safeguards, and technological mechanisms must work in concert to mitigate vulnerabilities and anticipate emerging threats. The EX0-105 examination evaluates a candidate’s ability to navigate these interdependencies with analytical clarity and practical insight.
Risk Assessment and Strategic Threat Management
A critical competency for EX0-105 is the structured identification and management of risk. Candidates are expected to catalogue informational and physical assets, assess vulnerabilities, evaluate potential threats, and estimate the impact of security incidents. ISO/IEC 27002 provides frameworks for both qualitative and quantitative risk analysis, enabling practitioners to prioritize security initiatives based on threat severity, asset criticality, and organizational objectives.
Threat modeling plays an essential role, requiring candidates to simulate attack vectors, anticipate insider threats, and consider environmental hazards. The examination challenges candidates to integrate risk analysis with decision-making processes, emphasizing the judicious allocation of resources and the implementation of controls proportionate to the likelihood and impact of potential incidents.
Policies, Governance, and Ethical Accountability
Effective governance is foundational for robust information security. EX0-105 evaluates candidates’ ability to formulate policies that define roles, responsibilities, and operational expectations. ISO/IEC 27002 emphasizes alignment with organizational strategy, ensuring that policies are actionable, measurable, and adaptable to evolving operational contexts.
Governance mechanisms extend beyond policy creation to include oversight committees, reporting structures, and performance monitoring. Candidates must also recognize the ethical dimensions of security governance, ensuring that practices comply with legal obligations, uphold organizational integrity, and maintain stakeholder trust. Ethical stewardship is a recurring theme in EX0-105, highlighting the nexus between professional conduct and effective security management.
Asset Management and Classification
The identification, classification, and safeguarding of assets are pivotal competencies evaluated in EX0-105. ISO/IEC 27002 advocates systematic cataloging of information and physical resources, assigning classification levels based on sensitivity, operational relevance, and exposure to risk. Candidates are expected to implement dynamic asset registers that reflect changes in asset value, location, and significance, integrating these insights with access control, risk management, and operational policies.
Proper asset management ensures that organizational resources are allocated efficiently and that critical information is protected against loss, unauthorized access, or compromise. EXIN evaluates candidates on their ability to operationalize these principles, demonstrating both conceptual understanding and practical implementation skills.
Human Resource Security and Cultural Integration
Personnel are both the most significant asset and potential vulnerability in any information security framework. EX0-105 examines candidates’ understanding of human resource security practices, including recruitment protocols, background checks, induction programs, ongoing training, and awareness campaigns. ISO/IEC 27002 emphasizes embedding security principles into organizational culture, promoting accountability, vigilance, and ethical behavior.
Candidates must also comprehend behavioral dynamics, recognizing that lapses in human judgment or adherence can compromise otherwise robust technical and administrative controls. By integrating human-centric strategies with broader operational objectives, practitioners foster a security-conscious culture that reinforces resilience and adaptability.
Access Control, Authentication, and Privilege Management
Access control mechanisms are central to information protection. EX0-105 evaluates candidate knowledge of authentication methods, authorization frameworks, and accountability measures. ISO/IEC 27002 highlights role-based access, segregation of duties, and the principle of least privilege, ensuring that personnel access only the information and systems necessary for their responsibilities.
Candidates must manage the full lifecycle of access rights, including provisioning, modification, and revocation. Continuous monitoring, logging, and anomaly detection support effective governance, ensuring timely identification of unauthorized activities and operational compliance. Practical scenarios often test the candidate’s ability to navigate complex access control situations while maintaining organizational efficiency.
Cryptography and Secure Communication Protocols
Encryption and secure communication are sophisticated elements of modern information security. EX0-105 assesses understanding of symmetric and asymmetric encryption, key management practices, digital signatures, and secure transmission protocols. ISO/IEC 27002 provides guidelines for implementing cryptographic controls that protect data confidentiality, integrity, and availability while aligning with regulatory obligations.
Candidates must also evaluate cryptographic vulnerabilities, algorithmic robustness, and operational feasibility, ensuring that secure communications are reliable and scalable. Integration of cryptographic mechanisms with network security, monitoring, and organizational policy exemplifies the comprehensive approach emphasized in EX0-105.
Operational Security and System Lifecycle Management
Security must be integrated throughout the system lifecycle to ensure resilience and continuity. EX0-105 emphasizes embedding security considerations in system acquisition, development, deployment, and maintenance. Candidates must understand secure coding practices, procurement evaluation, patch management, configuration auditing, and vulnerability scanning as ongoing processes.
ISO/IEC 27002 promotes proactive integration of security into operational workflows, fostering a culture where risks are anticipated and mitigated rather than retroactively addressed. Candidates are evaluated on their ability to implement continuous monitoring and improvement practices, ensuring alignment with organizational objectives, regulatory compliance, and operational efficiency.
Incident Management and Business Continuity
Preparedness for incidents is a hallmark of organizational resilience. EX0-105 examines incident management competencies, including detection, reporting, investigation, containment, and remediation. ISO/IEC 27002 underscores the integration of incident response with business continuity planning to ensure rapid recovery and minimal disruption to critical operations.
Candidates are expected to design escalation procedures, communicate with stakeholders effectively, and evaluate post-incident outcomes for continuous improvement. This holistic approach equips practitioners to respond adaptively to unanticipated disruptions while maintaining operational stability and strategic alignment.
Legal, Regulatory, and Compliance Considerations
Compliance with legal, regulatory, and contractual obligations is essential for organizational security. EX0-105 evaluates awareness of statutory mandates, industry-specific regulations, and internal policies. ISO/IEC 27002 emphasizes embedding compliance into operational procedures, ensuring that security measures satisfy legal obligations while enhancing organizational trust and credibility.
Candidates must recognize the consequences of non-compliance, including legal, financial, and reputational repercussions. Implementation of audit protocols, documentation practices, and accountability mechanisms ensures sustained adherence, integrating compliance seamlessly into broader security management strategies.
Preparation Strategies and Knowledge Reinforcement
Effective preparation for EX0-105 requires structured engagement with ISO/IEC 27002, practice exercises, and scenario-based learning. Candidates are encouraged to simulate real-world security challenges, apply theoretical principles, and reflect on decision-making outcomes. Iterative review, self-assessment, and targeted focus on weaker areas enhance retention and analytical acuity.
Participation in collaborative exercises, professional forums, and discussion groups broadens perspective and exposes candidates to diverse operational challenges. This approach cultivates critical thinking, practical judgment, and adaptive reasoning, aligning preparation with the analytical and scenario-based demands of EXIN’s examination framework.
Examination Tactics and Analytical Approach
Success in EX0-105 depends on a balance of knowledge mastery, strategic thinking, and composure. Scenario-based questions require careful evaluation, contextual interpretation, and the judicious application of ISO/IEC 27002 principles. Candidates must manage time effectively, prioritize tasks, and maintain clarity in their reasoning while navigating complex scenarios.
Ethical integrity remains paramount, reflecting professional expectations for information security practitioners. Candidates must demonstrate intellectual honesty, adherence to examination protocols, and accountability, mirroring the principles that underpin effective operational security.
Professional Advancement and Certification Benefits
EX0-105 certification validates foundational competence in information security management. Certified individuals are equipped to contribute to risk assessment, policy formulation, incident management, and regulatory compliance initiatives within diverse organizational environments. Employers value the credential for its demonstration of analytical skill, operational readiness, and strategic comprehension of security principles.
The certification also serves as a springboard for specialization in cybersecurity, governance, auditing, and risk management. By combining theoretical knowledge, practical insight, and ethical awareness, practitioners are prepared to navigate evolving threats, reinforce organizational resilience, and advance their professional trajectory.
Conclusion
Attaining EX0-105 certification signifies mastery of the fundamental principles of information security as articulated in ISO/IEC 27002. The examination assesses not only conceptual understanding but also practical application, encompassing governance, risk management, operational security, human factors, cryptography, compliance, and incident management. Candidates who succeed demonstrate analytical rigor, strategic acumen, ethical integrity, and operational preparedness. Beyond credentialing, EX0-105 serves as a foundation for professional growth, enabling practitioners to contribute meaningfully to organizational resilience, security culture, and the ongoing evolution of information security practices in an increasingly complex digital landscape.