Multicast, Scheduled, and Automatic Deployment
Exam: Microsoft 70-646 - Windows Server 2008, Server Administrator
Multicast permits efficient use of bandwidth by organizations. This allows an OS image to be transmitted over the network to multiple installation clients. Multicast deployment is supported in environments where multicast transmission is supported by the routers.
Deployments can be scheduled, allowing transmission of installation image data to take place at a specific time. An example of this could be configuration of deployment during hours other than peak hours having minimum effect on the working. In the alternative a scheduled multicast can be configured to take place when particular number of clients are capable of receiving an image. It is also possible to combine settings.
The figure represented below depicts a multicast transmission that is to occur at 3:00 in the morning and when ten clients are ready to receive the image. When WDS is combined with an unattended installation file, a set of computers can be turned on before closing the office for the day and finding that automatic configuration and installation has been carried out. An auto-cast represents a situation where the multicast transmission starts the moment a client requests for installation of image. Auto-casts are mostly used for deployments that are one-time rather than large scale.
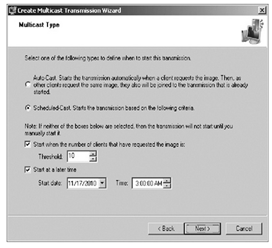
Configuring a multicast transmission
WDS Images
WDS brings in to use images which are primarily of two types - install images and boot images.
- Install Images: These are images of the operating system that are deployed on computers that run Windows Server 2008 R2, Windows Server 2008, Windows 7, or Windows Vista. Install.wim is the default installation image. It is located in the \Sources directory of the installation DVD. If WDS is being used for deploying Windows 7 to computers with processor architectures that are not identical, addition of separate installation images for each architecture to the WDS server becomes necessary. Architecture specific installation hosts architecture specific images. Creation of custom images is also possible, where having only a single image per processor architecture is a necessity.
- Boot Images: These are used for starting computers of the clients before installation of the OS image. When a boot image is started over the network, a menu displaying images that can be deployed is displayed. The Windows Server 2008 R2 Boot.wim file allows advanced deployment options. The file should be used in place of Boot.wim file available from other sources.There are two different types of additional boot images that can be configured for use with WDS.
- Capture Images: is a boot image that is responsible for starting the WDS capture utility used with a reference computer and prepared using the Sysprep utility.
- Discover Images: These are used for deploying images to computers that are not PXE enabled or on networks that do not permit PXE. These images are stored on USB, CD or DVD. The computer is started from the media rather than the PXE network card.
WDS and Product Activation
Even though product activation is not required for the actual installation process, administrators that consider the use of WDS for automated deployment, should consider the use of volume activation for the purpose of automatic activation. Volume activation makes available a centralized yet a simple method that can be used for activating a large number of deployed servers. Three methods of activation and two kinds of keys can be used.
The key types that can be used are:
- Multiple Activation Key (MAK): This allows activation of a specific number of computers and each successful activation reduces the activation pool.
- Key Management Services (KMS): This allows activation of computers in a managed environment without any need of individual connections to Microsoft.
Both the keys can be used in combination with each other. The number of times they connect to the network and internet connectivity determines the solution that has to be deployed.
Related IT Guides
- Analyzing the IPv6 Address Structure
- Determine which edition of Windows Server is appropriate for a specific set of circumstances
- IPv4-to-IPv6 Compatibility and Transition to IPv6
- Plan for the installation of or upgrade to Windows Server 2008 or Windows Server 2008 R2
- Planning an IPv6 Network
- Planning Windows Server 2008 and Windows Server 2008 R2 DNS
- Using IPv6 Tools
- Windows Deployment Services
- Windows Server 2008 R2 Answer Files


