Certification: CIW Web Security Professional
Certification Full Name: CIW Web Security Professional
Certification Provider: CIW
Exam Code: 1D0-571
Exam Name: CIW v5 Security Essentials
1D0-571 Exam Product Screenshots
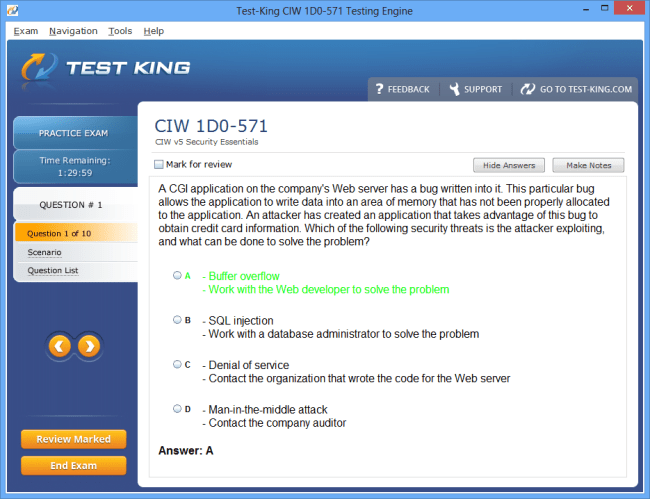
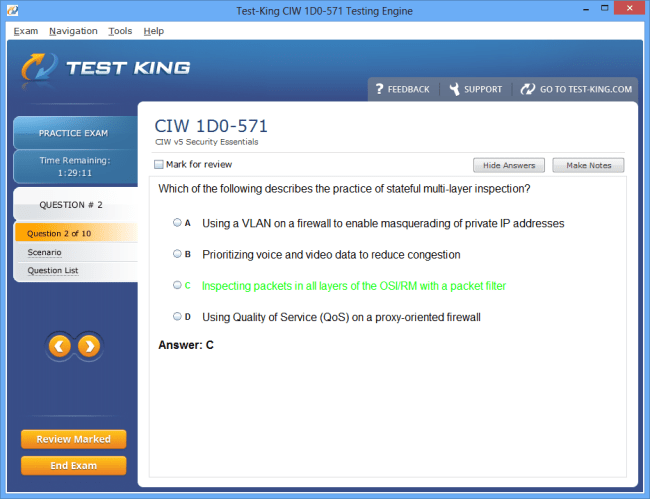
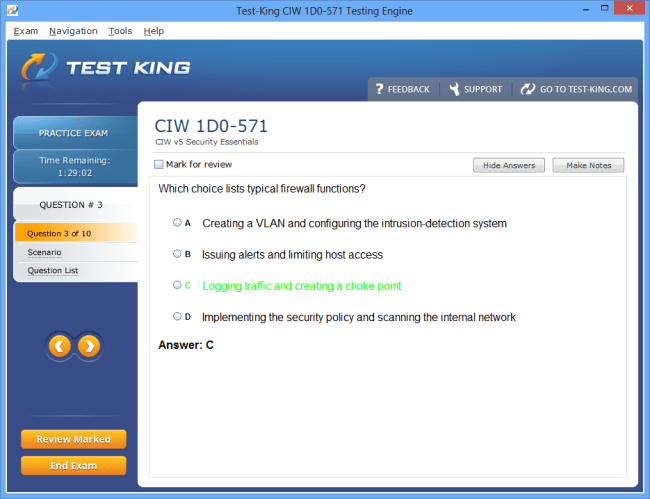
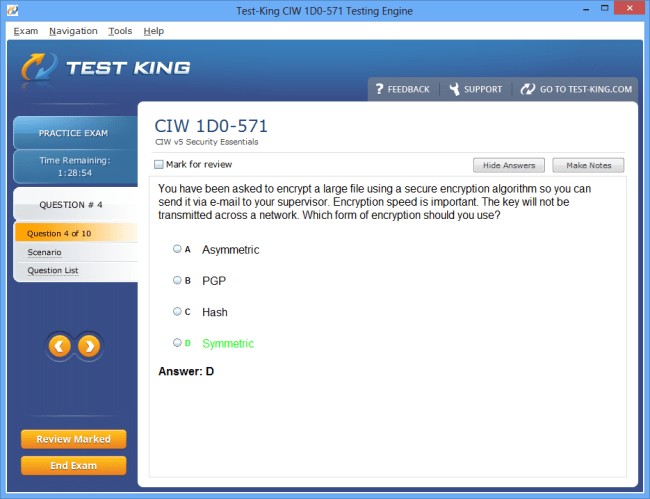
Mastering Digital Defense: An In-Depth Guide to the CIW Web Security Professional Certification
In the rapidly evolving sphere of digital technology, security has transcended its traditional boundaries to become a multifaceted discipline interwoven with every layer of modern computing. The CIW Web Security Professional certification emerges as a distinguished credential for those aspiring to master the delicate art of safeguarding web-based infrastructures. It is not merely a validation of technical competence but an affirmation of a professional’s capacity to anticipate, mitigate, and neutralize cyber threats that endanger digital ecosystems.
Understanding the Essence of the CIW Web Security Professional Certification
The world has witnessed a relentless surge in the sophistication of cyberattacks, transforming simple vulnerabilities into gateways for catastrophic breaches. In this milieu, organizations demand professionals who possess an intricate understanding of web protocols, encryption methods, and data protection frameworks. The CIW Web Security Professional certification stands as an emblem of such expertise, emphasizing a pragmatic comprehension of both theoretical and applied security principles. It equips candidates with the skills to secure network infrastructures, manage authentication mechanisms, and implement layered defense systems that counteract malicious intrusions.
The journey toward this certification begins with understanding its fundamental purpose: to prepare professionals capable of fortifying online environments. It delves deeply into the realms of secure communication, network defense, and system resilience. Candidates learn how to analyze vulnerabilities, assess threats, and deploy protective strategies that align with modern cybersecurity standards. The curriculum extends beyond mere technicalities—it fosters a mindset of vigilance and analytical precision, encouraging practitioners to anticipate rather than simply react to threats.
A certified web security professional is expected to have mastery over the architecture of web communications, including protocols such as HTTPS, SSL, and TLS. These protocols serve as the foundation of online trust, ensuring that sensitive transactions, from banking to e-commerce, remain confidential and tamper-resistant. The certification thus imparts not only knowledge of these technologies but also the ability to configure and manage them within dynamic enterprise settings.
Equally important is the focus on authentication and access control. Modern web infrastructures rely on sophisticated authentication mechanisms, ranging from password-based systems to biometric verification and tokenization. The CIW Web Security Professional certification teaches how to evaluate the strengths and weaknesses of each approach, ensuring that authentication frameworks remain both secure and user-friendly. Professionals also gain insights into identity management, a crucial domain in preventing unauthorized access and ensuring compliance with privacy regulations.
Another critical domain within this certification revolves around cryptography. Encryption represents the very heart of digital defense, transforming readable data into unintelligible ciphertext to deter unauthorized interception. Through this program, candidates develop proficiency in both symmetric and asymmetric cryptography, learning how encryption keys are generated, distributed, and managed. They also explore the use of hashing algorithms and digital signatures, which serve as integral mechanisms for verifying data integrity and authenticity.
However, the significance of the CIW Web Security Professional certification extends far beyond these technical proficiencies. It instills a broader perspective on risk management and governance, urging candidates to understand security as an organizational imperative rather than a purely technical pursuit. The curriculum encourages strategic thinking, guiding professionals to design policies and frameworks that sustain long-term resilience. This strategic dimension distinguishes CIW-certified professionals, as they can bridge the gap between technical operations and executive-level decision-making.
Cybersecurity today is not confined to protecting servers and websites—it encompasses every touchpoint where information flows. From cloud-based environments to mobile applications, vulnerabilities are omnipresent. The certification provides a comprehensive understanding of how web servers interact with other components of digital ecosystems, ensuring that protection mechanisms are coherent and unified. Candidates gain expertise in securing databases, preventing SQL injection attacks, and managing the risks associated with cross-site scripting and cross-site request forgery.
In parallel, there is an emphasis on understanding web application firewalls and intrusion detection systems. These tools act as sentinels, constantly monitoring data traffic and identifying suspicious behavior that could indicate an attack in progress. The certification emphasizes how to configure, maintain, and interpret the alerts generated by such systems. This competence ensures that certified professionals can respond swiftly and decisively to emerging threats, minimizing damage and maintaining operational continuity.
The training also delves into secure software development principles. As web applications become increasingly complex, vulnerabilities often originate within poorly designed code. The certification promotes awareness of secure coding practices, such as input validation, error handling, and secure session management. Professionals learn how to identify potential flaws during the development process and enforce preventive measures long before deployment. This proactive approach drastically reduces the likelihood of exploitation after the system goes live.
Furthermore, the CIW Web Security Professional certification addresses the importance of security policies and incident response strategies. An organization’s resilience depends not only on technological defenses but also on its ability to respond efficiently when an incident occurs. The certification teaches how to design incident response plans that define roles, responsibilities, and communication pathways during a crisis. Candidates understand how to perform forensic analysis, collect digital evidence, and report breaches in compliance with regulatory frameworks.
A distinctive aspect of this certification lies in its global recognition and cross-disciplinary relevance. It is designed for web administrators, system architects, network engineers, and even non-technical managers who oversee digital operations. This inclusivity reflects the universal nature of cybersecurity, where collaboration across departments is indispensable. Whether one is securing an enterprise website, managing a data center, or leading a compliance initiative, the principles taught in this program apply with equal potency.
As the digital world grows increasingly interconnected, the threats it faces evolve in tandem. Ransomware, phishing schemes, and zero-day exploits now dominate the threat landscape, demanding an ever-expanding skill set from professionals. The CIW Web Security Professional certification remains aligned with these developments by continually refining its curriculum to reflect current realities. It ensures that certified individuals remain competent in defending modern infrastructures while adapting to the rapid progression of technology.
The learning experience itself is immersive and dynamic, combining theoretical study with practical application. Candidates are encouraged to engage in simulations that mimic real-world security incidents, testing their ability to apply knowledge under pressure. Through such exercises, they cultivate not just technical expertise but also critical thinking and problem-solving abilities. These attributes are invaluable in high-stakes environments where decisions must be swift and accurate.
Equipped with this certification, professionals gain credibility that extends across industries. Employers recognize CIW credentials as evidence of disciplined study, practical competence, and ethical awareness. In an era where digital integrity is synonymous with corporate reputation, having a certified web security professional on staff represents both a safeguard and a strategic asset.
The certification also complements other cybersecurity credentials, serving as a stepping stone toward advanced specializations. It provides a foundational understanding that can be built upon through additional study in penetration testing, ethical hacking, or information assurance. Many professionals pursue it as part of a lifelong learning journey, seeking to remain agile in a field that evolves with relentless velocity.
In the context of compliance, the certification plays an instrumental role. Modern enterprises are bound by various regulatory frameworks such as GDPR, HIPAA, and PCI-DSS, all of which impose strict requirements on data protection. CIW-certified professionals are trained to interpret these mandates and translate them into actionable security measures. They understand how to maintain audit trails, implement encryption standards, and enforce data retention policies that align with legal expectations.
One of the most valuable competencies imparted by this certification is the ability to communicate effectively about security. Technical expertise alone is insufficient if a professional cannot articulate risks and solutions to non-technical stakeholders. The program emphasizes clear communication, helping professionals present security findings and recommendations in a manner that executives and clients can comprehend. This ability to translate complexity into clarity enhances collaboration and ensures that security receives the attention it deserves within strategic planning.
Another essential facet of the CIW Web Security Professional journey lies in ethical conduct. Cybersecurity is as much about moral responsibility as it is about technical mastery. The certification underscores the importance of adhering to professional ethics, respecting privacy, and using acquired knowledge for legitimate purposes. This moral compass distinguishes certified professionals as trustworthy guardians of digital integrity.
In addition to the technical and ethical dimensions, the certification nurtures an appreciation for continuous adaptation. Cyber adversaries are endlessly inventive, and defense mechanisms must evolve accordingly. The CIW Web Security Professional framework fosters a culture of perpetual learning, urging candidates to remain updated on emerging threats, tools, and methodologies. This adaptability ensures that their knowledge does not stagnate but remains fluid and responsive to technological metamorphosis.
The economic relevance of this certification is equally profound. The cybersecurity labor market is experiencing a severe talent shortage, and employers are eager to recruit individuals with proven credentials. CIW-certified professionals often find themselves in favorable positions when pursuing roles such as web security analyst, network defense engineer, or cybersecurity consultant. The certification not only enhances employability but also strengthens earning potential, reflecting the premium value placed on security expertise.
Beyond employability, the credential enriches personal confidence. To master web security is to comprehend the intricate machinery of the internet—the flow of packets, the negotiation of protocols, and the unseen interplay between clients and servers. This mastery breeds a sense of intellectual empowerment, transforming abstract concepts into practical capabilities. Certified professionals emerge not only as defenders but as innovators capable of designing robust and adaptive solutions.
The learning path toward this certification is characterized by depth and breadth. Candidates encounter an expansive array of topics ranging from cryptographic protocols to network infrastructure defense. Each concept builds upon the previous, creating an integrated understanding of how disparate components converge to form a secure digital environment. This holistic comprehension is indispensable in modern cybersecurity, where isolated expertise often proves insufficient against multifaceted threats.
An integral component of the certification is the exploration of real-world case studies. Candidates analyze historical breaches, dissecting how attackers exploited weaknesses and how preventive measures could have mitigated the damage. These analytical exercises bridge the gap between theoretical learning and real-world application, imparting lessons that resonate beyond the examination environment. Through these reflections, professionals gain the foresight to identify vulnerabilities that might otherwise remain obscured.
Ultimately, the CIW Web Security Professional certification represents more than an academic achievement—it embodies a philosophy of proactive defense, continuous learning, and ethical guardianship. Those who pursue it embrace a vocation that demands both intellect and integrity. They become architects of digital fortresses, ensuring that the virtual world remains as secure and trustworthy as the physical one.
This profound immersion in web security not only elevates individual careers but fortifies the entire digital landscape. Every professional who attains this credential contributes to a broader collective defense, creating an interconnected network of expertise that resists the encroachment of cyber malfeasance. Through knowledge, vigilance, and an unwavering commitment to integrity, CIW-certified professionals stand as the vanguard of modern digital civilization—a bulwark against the unseen forces that seek to undermine the web’s foundations.
Exploring the Technical Core and Applied Expertise of the CIW Web Security Professional Certification
The CIW Web Security Professional certification stands as an emblem of technological mastery, intended to cultivate a deep, nuanced understanding of how to secure the digital domain. It integrates theoretical knowledge with practical applications, producing individuals capable of navigating the intricate and volatile world of cybersecurity. As digital infrastructures expand and online interconnectivity deepens, professionals who pursue this credential are expected to acquire a sophisticated grasp of the mechanisms that govern digital communication, data protection, and system resilience. This exploration of the certification’s technical essence illuminates the expertise it demands, the skills it develops, and the transformative mindset it instills within those who pursue it.
At its foundation, the certification delves into the architecture of the web itself. It begins with an examination of how information travels through the internet, tracing the journey of data packets from source to destination. Candidates learn to understand the layered structure of communication protocols, focusing on the functions of TCP/IP, DNS, HTTP, and HTTPS. This foundational knowledge is not taught in isolation but as part of an integrated perspective that connects network mechanics with security imperatives. The aspirant learns how each layer, from the physical transmission of data to the application interface, presents potential vulnerabilities. By analyzing these vulnerabilities, the professional develops the acumen to implement defensive measures that neutralize threats before they manifest.
Within this landscape, encryption and secure communication play pivotal roles. The certification’s technical core emphasizes cryptographic science as the backbone of digital confidentiality and integrity. Candidates are introduced to algorithms such as AES, RSA, and SHA, not for rote memorization but for comprehension of how they underpin secure exchanges. Through this understanding, the learner grasps the subtleties of key generation, distribution, and management—skills vital to ensuring that sensitive communications remain inaccessible to unauthorized entities. The use of SSL and TLS protocols is explored in depth, with focus on how they authenticate identities and create encrypted channels across the web. The CIW Web Security Professional learns to implement, troubleshoot, and maintain these systems, recognizing their significance in securing e-commerce transactions, cloud services, and remote operations.
Another fundamental domain of this certification involves system and network defense. Candidates gain expertise in designing and maintaining fortified networks that can withstand external and internal threats. They study firewall architectures and learn to configure them to filter data traffic effectively, balancing protection with performance. They also explore the role of intrusion detection and prevention systems, understanding how these tools continuously monitor digital environments for signs of malicious activity. This competence extends to packet analysis, where professionals interpret data streams to identify patterns indicative of anomalies or breaches. Through such rigorous study, individuals become adept at discerning between benign irregularities and potential indicators of compromise.
The web application layer remains one of the most vulnerable frontiers in modern cybersecurity, and the CIW Web Security Professional certification dedicates significant attention to its protection. Candidates learn about common attack vectors such as SQL injection, cross-site scripting, cross-site request forgery, and session hijacking. Instead of merely recognizing these threats, they develop strategies to prevent them through secure coding practices, input validation, and session management. By integrating security into the software development life cycle, professionals ensure that applications are resistant to exploitation from the moment they are conceived. This proactive mindset—embedding security from inception rather than as an afterthought—distinguishes certified individuals as true architects of digital defense.
In addition to defending against software-based vulnerabilities, the certification instills proficiency in securing network infrastructure. The candidate explores virtual private networks (VPNs), proxy servers, and secure gateways as mechanisms to control and protect data flow. They learn how to construct segmented networks that restrict access based on roles and necessity, thereby minimizing the blast radius of any potential compromise. The discipline of network segmentation and least privilege becomes a guiding principle in designing resilient systems. Moreover, candidates study wireless network security, understanding how encryption methods like WPA3 safeguard communications in mobile and distributed environments.
A key aspect of this certification’s structure is its focus on authentication and identity management. In the modern era, where digital identities serve as the cornerstone of access and authorization, mismanagement can lead to severe breaches. Candidates are trained in implementing multifactor authentication systems that combine passwords, tokens, biometrics, and behavioral analytics. This layered approach strengthens the assurance that users are indeed who they claim to be. The study of identity management also involves understanding directory services, access control lists, and federated authentication models that allow seamless yet secure user experiences across interconnected systems.
Beyond technological mastery, the CIW Web Security Professional certification emphasizes the philosophical dimension of defense. It teaches that security is not static but dynamic—a continuous process of observation, evaluation, and refinement. Professionals learn how to conduct risk assessments that measure vulnerabilities against potential impacts, prioritizing resources where they are most needed. They develop an analytical approach to threat modeling, envisioning potential adversaries and predicting their tactics. This anticipatory skill transforms security from a reactive posture into a predictive science.
Incident response and forensics form another pillar of the certification’s applied expertise. Candidates are prepared to handle breaches with composure and precision. They study methodologies for identifying compromised systems, isolating affected components, and restoring integrity without disrupting essential operations. The process involves meticulous documentation, evidence collection, and communication with stakeholders to ensure transparency and accountability. Through simulated exercises, professionals develop the ability to operate under pressure, making calculated decisions during high-stakes situations where time and accuracy are paramount.
An integral part of this learning journey is the exploration of policy creation and governance. A robust security posture is not achieved through technology alone but through well-defined policies that guide human behavior and operational processes. The certification teaches how to craft policies that address access control, data retention, acceptable use, and incident management. Candidates understand the importance of aligning these policies with organizational objectives and regulatory requirements. This ensures that security measures do not exist in isolation but function cohesively within a larger framework of corporate governance.
The CIW Web Security Professional certification also draws attention to the ethical dimensions of cybersecurity. Professionals wielding advanced knowledge hold immense responsibility; misuse of this power can have catastrophic consequences. The certification thus instills an ethical foundation rooted in integrity, respect for privacy, and adherence to professional standards. Candidates learn about the legal implications of digital defense, exploring concepts such as intellectual property rights, privacy laws, and computer misuse regulations. By internalizing these principles, they become not just defenders but stewards of trust in the digital era.
Equally important is the focus on continuous learning and adaptability. The digital landscape is in perpetual flux, with new technologies emerging and older ones becoming obsolete. Threat actors evolve with equal vigor, crafting novel methods to exploit weaknesses. The CIW Web Security Professional certification nurtures a mindset of perpetual education, encouraging candidates to stay informed about evolving trends such as cloud computing, Internet of Things security, and artificial intelligence in threat detection. Professionals who adopt this philosophy remain agile and relevant, capable of responding to the unforeseen challenges that accompany technological progress.
Practical proficiency is reinforced through real-world simulation and applied training. Candidates engage in exercises that replicate actual attack scenarios, allowing them to apply theoretical concepts in controlled environments. These simulations test not only technical skill but also decision-making and collaboration. The ability to interpret logs, trace intrusions, and execute countermeasures is cultivated through repetitive practice until it becomes intuitive. This experiential learning approach ensures that certified professionals can transition seamlessly from academic knowledge to practical implementation.
In examining the value of this certification, one must consider its broad applicability across industries. Every organization that operates in the digital domain—be it healthcare, finance, education, or government—relies on secure web operations. The CIW Web Security Professional certification thus opens doors to diverse career paths. Certified individuals can serve as web security analysts, cybersecurity consultants, penetration testers, or information assurance specialists. Their expertise transcends industry boundaries, as the principles of security remain universally applicable.
The credential’s recognition extends beyond geographical and institutional confines. Employers around the world acknowledge CIW certifications as benchmarks of excellence, reflecting both dedication and competence. This recognition stems from the rigorous curriculum and the comprehensive nature of the knowledge it imparts. For professionals seeking international opportunities, this certification acts as a credential of credibility that communicates proficiency without the need for further validation.
From a technical standpoint, the CIW Web Security Professional certification serves as a confluence of multiple disciplines. It amalgamates aspects of networking, programming, cryptography, and risk management into a single cohesive learning experience. This interdisciplinarity mirrors the real-world demands of cybersecurity, where challenges rarely exist in isolation. By mastering this synthesis, certified individuals gain the rare ability to approach security holistically—considering not only how to protect systems but also why certain defenses are more effective than others in particular contexts.
Another notable aspect of this certification is its emphasis on human factors in cybersecurity. Technology alone cannot ensure safety; human behavior remains a critical variable. The certification examines social engineering, a domain where attackers exploit psychological tendencies rather than technical flaws. By studying these tactics, candidates learn how to build awareness campaigns and training programs that cultivate security-conscious behavior among employees. They understand that the human element can either fortify or undermine the most sophisticated defense systems, and therefore must be managed with equal diligence.
A deeper dive into the technical modules reveals a consistent focus on proactive defense. Rather than waiting for attacks to occur, professionals are trained to anticipate vulnerabilities through continuous monitoring and assessment. They learn about vulnerability scanning, patch management, and system hardening—activities that ensure systems remain resistant to exploitation. The discipline of patch management, for instance, involves a meticulous process of identifying software updates, testing their compatibility, and deploying them strategically to minimize downtime. Such processes demand precision and foresight, qualities that the certification seeks to instill.
The CIW Web Security Professional certification also recognizes the importance of cloud environments, which now host a significant portion of global data and applications. Candidates gain insights into securing cloud infrastructures, understanding shared responsibility models, and implementing encryption across distributed architectures. They learn to evaluate cloud service providers, assess compliance risks, and enforce security policies that align with organizational goals. This knowledge is indispensable in an era where cloud adoption continues to accelerate, bringing both convenience and complexity.
In addition to cloud security, the certification explores the implications of emerging technologies such as artificial intelligence, blockchain, and quantum computing. These innovations hold the potential to reshape cybersecurity in profound ways. For example, machine learning algorithms can enhance threat detection by identifying anomalous behavior patterns that elude traditional systems. Blockchain offers decentralized integrity verification, while quantum computing introduces both unprecedented computational power and new cryptographic challenges. The certification encourages candidates to understand these technologies not merely as trends but as transformative forces that will redefine the security landscape.
Through this expansive curriculum, the CIW Web Security Professional certification transforms the learner’s perspective on cybersecurity from that of a technician to that of a strategist. Certified professionals are expected to analyze the broader implications of security decisions, balancing protection with usability, cost, and efficiency. They understand that absolute security is unattainable but strive for optimal resilience—the ability to recover swiftly and gracefully from inevitable disruptions. This balance between prevention, detection, and response forms the cornerstone of sustainable digital defense.
Ultimately, the technical and philosophical breadth of the CIW Web Security Professional certification creates a new generation of defenders who view cybersecurity not as an isolated specialty but as an intrinsic component of digital civilization. It empowers them with the tools, intellect, and ethical compass required to safeguard the virtual fabric of modern society. Through continuous refinement of knowledge and skill, these professionals contribute to an enduring culture of security—one that transcends technology and becomes woven into the very ethos of digital progress.
Navigating the Path of Preparation and Knowledge Mastery for the CIW Web Security Professional Certification
The pursuit of the CIW Web Security Professional certification represents more than an academic endeavor; it embodies a disciplined commitment to mastering the principles that safeguard the digital world. For professionals venturing into this certification, the process of preparation demands both intellectual rigor and methodical precision. It calls for a profound understanding of the subject matter and a cultivated capacity to synthesize diverse areas of cybersecurity into a unified comprehension. The path toward mastery begins with recognizing that web security is not merely a collection of technical practices but a living ecosystem governed by patterns, logic, and evolving threats that continuously redefine the boundaries of defense.
To prepare effectively for the CIW Web Security Professional certification, candidates must first embrace the mindset of an investigator. Web security is a domain where curiosity and analytical thinking often outweigh rote memorization. Understanding why vulnerabilities exist, how they are exploited, and what preventive measures can be taken to counteract them requires an inquisitive temperament. Every concept within the certification—from encryption algorithms to access control policies—carries an interrelated function that influences the overall security posture of digital systems. Therefore, the preparation process should not be treated as an isolated study of topics but as the construction of a mental framework that connects the intricate mechanisms of cybersecurity into an organic whole.
The study journey begins with the foundation of networking. Candidates are encouraged to delve deeply into the underlying architecture of data transmission and communication protocols. Grasping the workings of TCP/IP, DNS, and HTTP forms the bedrock upon which advanced concepts are built. The certification expects the learner to go beyond superficial comprehension, exploring packet structures, addressing schemes, and routing processes to identify where vulnerabilities might arise. For instance, misconfigurations in DNS can lead to redirection attacks, while flaws in HTTP handling can expose data during transmission. By internalizing these concepts, the professional learns to visualize digital communication as both an enabler and a potential vector of risk.
As the learner progresses, encryption emerges as a critical pillar of study. It is here that the CIW Web Security Professional candidate must navigate the complex terrain of cryptographic algorithms and their applications. This involves exploring symmetric encryption methods such as AES, as well as asymmetric algorithms like RSA and ECC. The preparation process entails not only understanding how these algorithms function but also when and why they should be applied. For example, symmetric encryption is typically favored for its speed in data encryption, whereas asymmetric methods excel in key distribution and digital signatures. A profound comprehension of hashing algorithms—like SHA and MD5—is also essential, as they underpin integrity verification and password protection systems. Through this exploration, candidates develop a meticulous awareness of how cryptography supports authentication, confidentiality, and non-repudiation in secure web transactions.
Studying secure communication protocols forms the next essential component of preparation. Learners must familiarize themselves with the implementation and troubleshooting of SSL and TLS, the protocols that facilitate encrypted web sessions. Understanding how these protocols establish trust between clients and servers through digital certificates and certificate authorities is vital. Candidates should immerse themselves in the process of certificate issuance, renewal, and revocation, as mishandling these steps can compromise security. Furthermore, understanding how to interpret the handshake process in encrypted communication empowers professionals to diagnose and resolve issues related to encryption failures or misconfigurations.
Another critical area of study is the identification and mitigation of common web vulnerabilities. Candidates preparing for the certification should devote extensive time to understanding how attackers exploit weaknesses in web applications. Familiarity with threats such as cross-site scripting, cross-site request forgery, injection flaws, and insecure session handling is indispensable. Preparation in this domain involves not only recognizing the mechanics of these attacks but also learning how to prevent them through defensive coding practices. This entails studying concepts like input validation, output encoding, and secure session management to ensure that applications remain resilient against intrusion. Understanding these vulnerabilities from both the attacker’s and defender’s perspectives enriches the candidate’s analytical insight and heightens their situational awareness.
Equally significant in preparation is the comprehension of authentication and access control mechanisms. The certification expects candidates to understand how users are verified and how access is managed across digital infrastructures. This requires studying methods such as multifactor authentication, token-based access, and single sign-on frameworks. During preparation, professionals should also explore how directory services, permissions, and role-based access controls contribute to enforcing the principle of least privilege. This principle dictates that users and systems should have only the minimal level of access necessary to perform their functions, thereby minimizing potential damage from compromised accounts. The learner must develop an intuitive grasp of how access controls integrate within larger security architectures, ensuring that authorization processes are both secure and efficient.
A vital dimension of preparation involves familiarizing oneself with network defense strategies. Candidates should cultivate a thorough understanding of firewalls, intrusion detection systems, and intrusion prevention systems. They must learn how these tools function individually and collectively to create a layered defense model. Studying packet filtering, proxy services, and stateful inspection helps candidates grasp how firewalls monitor and regulate data flow. Additionally, exploring the configurations of intrusion detection systems allows learners to identify patterns of suspicious activity and distinguish between false positives and genuine threats. The CIW Web Security Professional candidate must be able to analyze logs, interpret alerts, and respond to anomalies swiftly and accurately.
Preparation should also encompass a comprehensive understanding of incident response and digital forensics. Cyber incidents are inevitable, and how an organization responds determines the extent of the damage and recovery. Candidates should learn about the stages of incident response, including identification, containment, eradication, recovery, and post-incident analysis. They should also understand the importance of preserving evidence for forensic investigation. Familiarity with logging systems, audit trails, and documentation practices is essential, as it enables professionals to trace the origin and nature of breaches. Through this study, candidates develop the capacity to act decisively during crises, maintaining composure and methodical precision in high-pressure scenarios.
Governance and policy formulation are equally important components of exam preparation. The CIW Web Security Professional certification emphasizes not only technical prowess but also strategic foresight. Candidates must learn to craft security policies that govern access, data handling, and incident management. They should study how organizational policies align with regulatory frameworks such as GDPR and HIPAA, which impose specific standards for data privacy and protection. Understanding the interplay between technical controls and administrative measures is crucial for implementing comprehensive security programs. Through this knowledge, candidates can design environments where technological safeguards are reinforced by clearly articulated governance principles.
Ethical awareness and legal literacy form another indispensable dimension of preparation. Professionals pursuing this certification are expected to uphold the highest ethical standards in their practice. Candidates must study laws related to computer misuse, data protection, and intellectual property. They should understand the boundaries of ethical hacking and the consequences of unauthorized access. Preparing in this area cultivates an appreciation for the moral responsibilities inherent in cybersecurity. The learner is reminded that technical skill without ethical grounding can lead to misuse and that true mastery entails both competence and conscience.
A distinctive element of the preparation process involves developing analytical and diagnostic skills. Security professionals must think like adversaries to anticipate their tactics. Candidates should study threat modeling techniques that enable them to identify potential attack paths and weak points within systems. This requires an understanding of reconnaissance methods, social engineering tactics, and exploitation sequences used by attackers. By learning to mirror the thought processes of malicious actors, candidates can preemptively fortify systems and craft countermeasures that neutralize threats before they manifest.
In addition to theoretical learning, candidates must engage in practical experimentation. Building a virtual lab environment is an effective way to apply concepts in a controlled setting. Within this lab, learners can simulate various network configurations, test firewall rules, and analyze system behavior under different security conditions. They can also explore tools used for vulnerability scanning and traffic analysis, gaining firsthand experience of how attacks unfold and how defenses can be optimized. This hands-on practice transforms abstract knowledge into tangible skill, allowing candidates to internalize procedures and develop intuition for real-world application.
Another crucial element in preparation is time management and study planning. The vast breadth of material encompassed by the CIW Web Security Professional certification requires structured learning. Candidates should design a study schedule that allocates sufficient time for each topic while allowing periodic review. Breaking the material into interconnected domains—networking, cryptography, application security, and governance—facilitates a balanced approach. Regular self-assessment through quizzes and mock exams helps identify weak areas and measure progress. Consistent review reinforces retention and fosters confidence as the exam approaches.
Candidates should also develop familiarity with terminology and conceptual clarity. Cybersecurity terminology is often dense, and misunderstanding key terms can lead to conceptual errors. Reviewing glossaries, documentation, and official study materials helps ensure accuracy. The ability to articulate technical concepts clearly is also essential for professional communication. Whether explaining an encryption failure to a developer or presenting a risk analysis to management, clarity of thought and expression is a distinguishing attribute of a well-prepared professional.
During the study process, collaboration and discussion can amplify learning outcomes. Engaging with online forums, study groups, or peer discussions allows candidates to exchange ideas, clarify uncertainties, and gain diverse perspectives. Teaching or explaining concepts to others can further reinforce understanding, as it requires organizing knowledge coherently. The exchange of experiences among peers also introduces real-world insights that deepen the relevance of theoretical study.
Beyond the immediate goal of passing the certification exam, preparation for the CIW Web Security Professional credential should be viewed as an investment in lifelong competence. The skills acquired during this journey serve as the foundation for continued professional growth. As candidates progress, they cultivate habits of disciplined learning, analytical reasoning, and ethical mindfulness that remain invaluable long after the examination. The process transforms them into perpetual learners, capable of adapting to the ever-shifting landscape of cybersecurity.
The certification’s preparation also reinforces the idea that security is a shared responsibility. Candidates are encouraged to view their future roles not in isolation but as part of a collective effort to protect the digital fabric of society. Understanding how individual actions contribute to broader organizational and societal resilience fosters a sense of purpose. This mindset is what ultimately distinguishes the CIW Web Security Professional—it produces not only skilled practitioners but guardians of digital trust.
In essence, preparation for this certification demands more than academic dedication; it requires an integration of intellect, discipline, and foresight. Candidates must internalize the concepts they study until they become second nature. They must cultivate the ability to think critically, act decisively, and communicate effectively. Each topic—whether encryption, authentication, or governance—forms a thread in the intricate tapestry of cybersecurity knowledge. When woven together through diligent preparation, these threads create a fabric strong enough to resist the forces of digital adversaries.
Thus, the path toward becoming a CIW Web Security Professional is both demanding and transformative. It molds individuals into analysts, strategists, and defenders capable of safeguarding the digital world with intellect, integrity, and innovation. The mastery acquired through preparation transcends the confines of examination halls and becomes an enduring instrument of protection in a world increasingly reliant on the sanctity of information.
The Role of Advanced Knowledge and Expertise in Achieving Web Security Mastery
The digital world has evolved into an intricate and interconnected system that depends heavily on secure frameworks, dependable infrastructures, and expert professionals who can foresee and mitigate cyber threats before they disrupt essential functions. The CIW Web Security Professional Certification stands as a distinguished credential in this field, designed to validate an individual’s ability to secure online ecosystems with technical precision and strategic awareness. As digital networks expand and malicious actors develop more sophisticated tools, the need for web security professionals who possess both theoretical comprehension and practical competence has never been greater. This certification provides a refined pathway for individuals to understand, interpret, and implement multifaceted layers of protection that align with the highest standards of digital safety.
Web security today is no longer limited to firewalls and antivirus software; it encompasses a wide spectrum of strategies, tools, and methodologies. From encryption and authentication to risk management and penetration testing, professionals certified in this discipline learn to interpret complex security challenges and apply pragmatic solutions that preserve data integrity and organizational stability. The CIW Web Security Professional program cultivates the intellectual dexterity required to analyze vulnerabilities, reinforce web infrastructures, and align defense mechanisms with global cybersecurity frameworks. The knowledge attained through this certification extends far beyond traditional classroom learning; it immerses individuals into the deep strata of network behavior, cyber-attack patterns, and countermeasure strategies that shape the modern cyber defense ecosystem.
A fundamental aspect of the certification involves understanding the digital anatomy of web applications and the vulnerabilities that plague them. The growing prevalence of cloud computing, online transactions, and digital identities means that each web application represents both a point of service and a potential target. A certified professional is trained to dissect these environments, evaluating how data is transmitted, stored, and protected within the virtual architecture. Encryption protocols, intrusion detection systems, and access control mechanisms form the backbone of this expertise. Yet, what truly distinguishes a CIW-certified professional is their ability to interpret how human behavior, technological design, and policy frameworks intertwine to create or mitigate risk.
In an era where information warfare and digital espionage are becoming more prevalent, the necessity of a structured and standardized understanding of web security has intensified. Organizations no longer view cybersecurity as an auxiliary function but as a foundational pillar of their operational existence. The CIW Web Security Professional Certification fills this crucial gap by cultivating individuals who can function as both analysts and architects of digital safety. Through the study of web security principles, cryptographic standards, authentication systems, and the intricacies of web protocols, professionals are equipped to transform their theoretical knowledge into actionable strategies that strengthen digital infrastructure.
The learning trajectory associated with this certification reflects a deliberate balance between technical mastery and conceptual understanding. It delves into the anatomy of cyber threats, exploring the intricate mechanics behind phishing attacks, SQL injections, cross-site scripting, denial-of-service exploits, and other methods employed by cyber adversaries. By understanding the logic behind these malicious actions, certified professionals gain the intellectual advantage needed to anticipate and neutralize threats effectively. This analytical perspective is what elevates a CIW Web Security Professional beyond ordinary network technicians; it shapes them into strategic defenders capable of constructing resilient systems that can withstand persistent digital aggression.
Another important dimension of the CIW Web Security Professional Certification is its emphasis on encryption and secure communications. Encryption serves as the cornerstone of modern cybersecurity, transforming readable data into complex sequences that cannot be deciphered without appropriate authorization. Certified professionals become adept at applying encryption techniques such as SSL/TLS, symmetric and asymmetric cryptography, and hashing algorithms. This not only secures communications between clients and servers but also protects stored data from unauthorized access. In many industries, from finance to healthcare, encryption compliance has become a legal requirement, and professionals with the CIW credential play an essential role in ensuring that organizations adhere to such standards.
Equally vital to mastering digital defense is the comprehension of authentication and access control systems. Insecure authentication mechanisms are among the leading causes of data breaches worldwide. Through the CIW Web Security Professional program, individuals acquire in-depth understanding of password protection, multi-factor authentication, digital certificates, and single sign-on protocols. They learn to implement these systems in a way that balances security with user convenience. A CIW-certified expert can design and maintain authentication infrastructures that not only safeguard sensitive assets but also enhance user experience without compromising confidentiality or accessibility.
Web servers and networks, being the fundamental components of digital communication, require continual monitoring and maintenance to preserve their integrity. The certification provides a meticulous exploration of server configuration, firewall deployment, intrusion prevention systems, and virtual private networks. Participants learn how to recognize network anomalies, interpret security logs, and apply corrective measures when potential breaches are detected. This continuous surveillance forms the defensive perimeter of any digital ecosystem, ensuring that vulnerabilities are identified and resolved before they can be exploited by malicious entities. The expertise in configuring and maintaining secure web servers not only minimizes exposure to external attacks but also reinforces trust among users who depend on those services.
The CIW Web Security Professional Certification also underscores the importance of risk management and compliance. Security does not exist in a vacuum; it operates within the legal, ethical, and organizational contexts that define acceptable behavior and governance. Professionals learn to evaluate risks based on their likelihood and impact, applying structured methodologies such as qualitative and quantitative analysis to prioritize mitigation efforts. They also become proficient in aligning organizational security policies with international standards such as ISO 27001 and regulatory frameworks like GDPR or HIPAA. This alignment ensures that digital defense is not only technically robust but also ethically and legally sound.
Beyond technical competencies, the certification encourages the cultivation of a cybersecurity mindset—an awareness that extends beyond immediate technical solutions and encompasses proactive anticipation of threats. This mindset involves perceiving every digital transaction as a potential point of vulnerability and every user interaction as a component of the broader security landscape. Through continuous learning, situational awareness, and adherence to ethical conduct, CIW-certified professionals evolve into strategic guardians of digital ecosystems. They recognize that the essence of cybersecurity lies not in reaction but in preemption, in the ability to foresee patterns of intrusion and dismantle them before they mature into crises.
A profound understanding of web application architecture further enhances the effectiveness of certified professionals. As web technologies evolve, frameworks such as HTML5, JavaScript, and RESTful APIs have introduced new layers of interactivity and efficiency but also new potential attack vectors. The certification curriculum provides insights into how these frameworks function and how vulnerabilities can be introduced during development. This knowledge allows professionals to collaborate effectively with developers, ensuring that security considerations are integrated at every stage of the application lifecycle—from design and coding to deployment and maintenance.
In contemporary cybersecurity discourse, ethical hacking and penetration testing have become indispensable tools for evaluating system resilience. The CIW Web Security Professional Certification provides a comprehensive exploration of these practices. Professionals learn to simulate real-world attacks within controlled environments, using these exercises to expose weaknesses and refine defense mechanisms. Ethical hacking is not an act of destruction but one of discovery and reinforcement—it allows organizations to understand their security posture and strengthen it before adversaries can exploit it. This practice cultivates a scientific and investigative approach to cybersecurity, emphasizing precision, accountability, and methodical execution.
Incident response and recovery form another critical pillar of digital defense. Despite preventive measures, breaches can still occur, and how an organization responds determines the extent of damage and recovery time. Certified professionals are trained to develop incident response plans, coordinate with internal teams, and engage with external stakeholders during crises. They understand the importance of preserving digital evidence, maintaining communication transparency, and implementing remediation steps efficiently. This structured approach not only limits the impact of security incidents but also ensures that lessons are learned and systems are fortified against future occurrences.
As the digital world continues its inexorable expansion, new technologies such as artificial intelligence, blockchain, and quantum computing are reshaping the security landscape. The CIW Web Security Professional Certification equips individuals with a forward-looking perspective, allowing them to comprehend and adapt to these emerging paradigms. For instance, AI-driven security analytics enhance threat detection capabilities by identifying anomalies in massive datasets, while blockchain introduces decentralized verification mechanisms that reduce dependency on single points of failure. A CIW-certified professional understands the interplay between innovation and risk, enabling them to harness technology’s potential without compromising its security.
The significance of web security extends beyond individual organizations; it influences national economies, critical infrastructure, and even the balance of geopolitical power. Cyberattacks targeting financial systems, healthcare networks, and government databases can have devastating repercussions. Professionals trained under the CIW Web Security Professional program contribute to a broader societal mission—preserving trust in digital systems that underpin global commerce, communication, and governance. Their work embodies the ethical responsibility of safeguarding not just data but also human welfare, privacy, and autonomy in a world increasingly governed by digital interactions.
The certification also nurtures collaboration and communication skills, recognizing that cybersecurity is rarely a solitary endeavor. Effective defense requires coordination among departments, including IT, management, legal, and human resources. Certified professionals learn to articulate complex technical issues in language that stakeholders can comprehend, fostering informed decision-making. This ability to translate cybersecurity insights into actionable strategies enhances the collective resilience of organizations, enabling them to create cultures of vigilance rather than complacency.
Moreover, the professional growth opportunities arising from this certification are substantial. As organizations expand their digital presence, the demand for qualified web security experts continues to escalate. Roles such as web security analyst, information assurance specialist, penetration tester, and cybersecurity consultant have become indispensable across industries. A CIW-certified individual distinguishes themselves not only through technical proficiency but also through an established reputation for reliability and ethical conduct. Employers recognize this credential as evidence of commitment, competence, and the capacity to manage the complexities of contemporary cyber defense.
In essence, the CIW Web Security Professional Certification represents more than a qualification—it embodies a philosophy of continuous learning, strategic foresight, and ethical stewardship of the digital realm. Those who pursue it enter a realm of perpetual discovery, where each new vulnerability presents an opportunity for innovation and each defense mechanism reflects human ingenuity. The certification’s comprehensive approach ensures that professionals do not merely react to change but drive it, shaping the contours of web security for the generations that follow.
Through its rigorous curriculum, applied methodology, and emphasis on integrity, the CIW Web Security Professional Certification equips individuals with the intellectual armament to navigate an increasingly hostile cyber landscape. Its graduates stand as sentinels of the digital world, upholding the delicate equilibrium between connectivity and security, accessibility and privacy. They embody the essence of mastery—an enduring pursuit of excellence that defines the discipline of web security and fortifies the digital foundations of our interconnected age.
The Interconnection of Practical Competence and Strategic Intelligence in Web Security
In the rapidly advancing realm of digital connectivity, where every transaction, message, and interaction passes through intricate virtual networks, the necessity for proficient and well-trained security experts has reached a critical zenith. The CIW Web Security Professional Certification serves as a prestigious validation of one’s proficiency in safeguarding web-based infrastructures from malicious incursions. This certification does not simply measure the ability to identify threats; it signifies a deeper comprehension of the mechanisms that underpin secure communication, data protection, and network resilience. It molds individuals into digital guardians who can traverse the labyrinthine corridors of cybersecurity with a balance of precision, intellect, and ethical discernment.
Web security, as a discipline, functions as the central pillar sustaining the integrity of global digital operations. The exponential growth of online platforms, mobile applications, and interconnected systems has expanded the potential attack surface for cybercriminals. Every enterprise, from small startups to multinational corporations, depends upon the seamless and secure transmission of data. The CIW Web Security Professional Certification trains individuals to construct and maintain this digital trust by mastering the defensive mechanisms that shield systems from unauthorized infiltration and compromise. Such expertise demands not just technical aptitude but also strategic foresight—an understanding of how security decisions today influence organizational continuity tomorrow.
The modern cyber environment is characterized by an unending contest between innovation and exploitation. As technology evolves, so too do the tactics of those seeking to exploit its vulnerabilities. Within this volatile landscape, a CIW-certified professional must adopt a proactive rather than reactive stance. Their role extends far beyond installing firewalls or configuring encryption protocols; they must anticipate threats, predict adversarial patterns, and reinforce weak points before exploitation occurs. The certification’s curriculum embodies this philosophy of vigilance, instilling in learners the analytical rigor necessary to evaluate risk factors, identify patterns of malicious intent, and apply adaptive countermeasures that evolve with the threat environment.
The foundation of this certification lies in a profound understanding of how web systems operate at their core. Every website, application, or service functions through a series of interconnected components—servers, databases, network protocols, and user interfaces—that collectively determine its functionality and security posture. A CIW Web Security Professional must be capable of dissecting this architecture with surgical precision. They study how requests move between clients and servers, how cookies store sensitive information, how authentication systems manage identity, and how encryption ensures confidentiality. This comprehensive knowledge enables them to pinpoint potential vulnerabilities hidden within the layers of code and configuration.
One of the pivotal domains covered under this certification is cryptography—the science of encoding and decoding information to prevent unauthorized access. Encryption acts as a linguistic barrier, transforming readable data into an unreadable cipher that only authorized recipients can decipher. CIW-certified professionals master a variety of cryptographic methods, from symmetric and asymmetric key encryption to digital signatures and hashing algorithms. They learn to apply these techniques to secure communications, verify identities, and maintain data integrity. In an era where data breaches can devastate reputations and erode consumer trust, the role of encryption becomes indispensable. Through their expertise, certified professionals ensure that sensitive information remains confidential even in the face of interception or compromise.
Beyond the mathematical elegance of encryption lies the complexity of authentication. Authenticating users is an art of balancing security and usability. Too little protection invites intrusion; too much restriction hinders access. CIW Web Security Professionals acquire the ability to design authentication mechanisms that maintain this delicate equilibrium. They explore methods such as password policies, digital certificates, multi-factor authentication, and single sign-on frameworks. They understand that every authentication method carries its own vulnerabilities—passwords may be guessed or stolen, tokens may be intercepted, biometric data may be spoofed. Thus, a CIW professional must not only implement these systems but continually refine and monitor them to ensure they resist evolving attack vectors.
Another critical domain explored through the CIW Web Security Professional Certification is network defense and monitoring. The digital network acts as both the circulatory system and the nervous system of an organization’s IT infrastructure. It transports data, enables communication, and coordinates processes. Any breach within this network can compromise the entire organism. Certified professionals are trained to establish defensive perimeters using technologies such as intrusion detection systems, virtual private networks, and firewalls. They learn how to configure these systems to recognize suspicious activities, filter malicious traffic, and prevent data leakage. Moreover, they are taught the art of continuous monitoring—examining network logs, analyzing anomalies, and responding to indicators of compromise with calculated efficiency.
While defensive architecture is critical, understanding the offensive perspective is equally vital. Ethical hacking, a discipline included in the CIW Web Security Professional program, empowers individuals to think like adversaries. Through controlled simulations, professionals learn how cyber attackers exploit vulnerabilities in web applications, misconfigurations, or outdated systems. This knowledge allows them to uncover weaknesses before malicious entities can exploit them. The distinction between ethical and unethical hacking lies in intent and authorization—the former aims to strengthen defenses, while the latter seeks to destroy or manipulate. Ethical hacking, therefore, is an indispensable tool in a professional’s arsenal, enabling them to anticipate threats and fortify systems through firsthand understanding.
In the context of contemporary cybersecurity, incident response and digital forensics play an essential role in minimizing damage when breaches occur. Despite best efforts, no system can claim to be entirely impervious to compromise. The ability to respond swiftly, contain threats, and recover operations defines the resilience of an organization. CIW Web Security Professionals are trained to design and implement incident response frameworks that include identification, containment, eradication, and recovery processes. They also study the preservation and analysis of digital evidence—an intricate field that demands meticulous attention to detail. Through forensic methodologies, they trace the origins of breaches, reconstruct the sequence of events, and provide actionable insights for preventing future incidents.
Moreover, the certification delves into the crucial domain of web application security, which has become a cornerstone of digital defense. Web applications are often the primary interface between users and services, making them prime targets for cyberattacks. Vulnerabilities such as cross-site scripting, SQL injection, remote file inclusion, and session hijacking can compromise both the application and its users. CIW-certified professionals develop the ability to identify and remediate these vulnerabilities through systematic testing, code review, and secure development practices. They collaborate with developers to ensure that security is not an afterthought but an integral aspect of the software development lifecycle.
Risk management, too, forms an inseparable part of a CIW Web Security Professional’s responsibilities. Cybersecurity is not merely about technology—it is about making informed decisions under uncertainty. Certified professionals are equipped with frameworks to assess risks in terms of probability, impact, and exposure. They learn to prioritize mitigation strategies based on organizational goals, resource availability, and compliance requirements. Through this process, they bridge the gap between technical expertise and executive decision-making, ensuring that cybersecurity investments yield tangible benefits. This alignment of risk management with business strategy transforms web security from a technical function into a strategic asset.
The certification also highlights the importance of compliance with global data protection and privacy standards. In an interconnected world, information transcends borders, and so must the regulations that govern it. Certified professionals become conversant with international frameworks such as the General Data Protection Regulation, the Payment Card Industry Data Security Standard, and various national cybersecurity laws. They understand how to align organizational policies with these legal obligations to avoid penalties and maintain consumer trust. In many cases, a CIW-certified expert acts as the liaison between technical teams and regulatory authorities, ensuring that all digital operations adhere to the required standards of confidentiality, integrity, and availability.
Equally significant is the growing interplay between cybersecurity and artificial intelligence. As machine learning and automation become embedded within digital ecosystems, new opportunities and vulnerabilities emerge. CIW Web Security Professionals learn to analyze these developments critically. They understand how AI can enhance security through predictive threat modeling, anomaly detection, and automated response, but they also recognize the potential for adversarial AI attacks. This dual awareness allows them to integrate intelligent technologies responsibly, ensuring that automation amplifies human judgment rather than replaces it.
A defining feature of the CIW Web Security Professional Certification is its emphasis on continuous learning. Cyber threats evolve with remarkable velocity; tools and techniques that are effective today may be obsolete tomorrow. Thus, professionals must cultivate intellectual agility and a spirit of perpetual curiosity. The certification encourages the pursuit of ongoing education through workshops, seminars, and professional communities. By remaining attuned to emerging trends such as quantum-resistant encryption, blockchain security, and zero-trust architectures, certified individuals maintain their relevance and authority in an ever-changing field.
In addition to technical acumen, the program fosters a profound sense of ethical responsibility. Cybersecurity professionals occupy positions of immense trust, with access to sensitive systems and confidential data. The misuse of such power can cause irreparable harm. Hence, the CIW Web Security Professional Certification integrates ethical principles that guide decision-making and professional conduct. Certified individuals are expected to uphold transparency, accountability, and integrity in all aspects of their work. They must act not only as defenders of technology but as stewards of digital morality, ensuring that their expertise is used to protect rather than exploit.
Communication and collaboration are equally vital in the landscape of web security. Isolated expertise, no matter how advanced, cannot sustain complex digital ecosystems. Certified professionals are trained to collaborate with multidisciplinary teams, translating intricate technical concepts into accessible insights for decision-makers. Whether advising executives on strategic investments or guiding developers through secure coding practices, their ability to articulate ideas clearly and persuasively amplifies their effectiveness. This skill transforms them from mere technicians into trusted advisors capable of influencing organizational culture and policy.
In professional practice, the real measure of a CIW Web Security Professional lies in their capacity to maintain equilibrium between innovation and protection. Digital transformation demands speed, adaptability, and experimentation, while security demands caution, stability, and verification. The tension between these imperatives defines the modern technological enterprise. Certified professionals act as mediators, ensuring that progress does not come at the expense of safety. They design frameworks where agility and security coexist harmoniously, enabling organizations to innovate confidently without exposing themselves to unnecessary peril.
The global recognition of the CIW Web Security Professional Certification has further elevated its significance in the job market. Employers across industries seek professionals who can fortify digital assets, respond to incidents, and navigate the intricacies of compliance. The certification demonstrates not only competence but commitment—a signal that the individual has undergone rigorous training and adheres to internationally recognized standards of excellence. With cybersecurity threats growing in both frequency and sophistication, organizations increasingly rely on certified experts to anchor their defensive strategies.
Ultimately, the CIW Web Security Professional Certification empowers individuals to perceive the digital world through a lens of structured insight and refined judgment. It transforms raw technical knowledge into applied intelligence, blending the precision of science with the foresight of strategy. Each certified professional carries within them the capacity to influence not just the security of a single network, but the trustworthiness of the digital civilization that depends upon it. Through diligence, ethical fortitude, and relentless pursuit of mastery, they uphold the invisible foundations of the modern era—ensuring that the web remains not only functional but safe, resilient, and worthy of humanity’s collective reliance.
The Transformation of Web Security Expertise and the Evolution of the Digital Sentinel
In the contemporary digital continuum, where every transaction, interaction, and innovation is intertwined with the vast and volatile domain of cyberspace, the necessity for resilient and knowledgeable web security professionals has become an imperative cornerstone of technological civilization. The CIW Web Security Professional Certification serves as a definitive testament to an individual’s capability to defend digital architectures, preserve the sanctity of data, and maintain the equilibrium between accessibility and protection. It represents the synthesis of technological proficiency, strategic awareness, and ethical consciousness—traits essential to thrive in a world where information itself has become the most coveted and contested asset.
The very foundation of web security rests on understanding the intricacies of how the internet functions at its deepest levels. A certified professional is trained to analyze, interpret, and fortify systems that facilitate global communication. This expertise transcends simple technical configuration; it involves the capacity to perceive vulnerabilities as patterns within larger systemic behaviors. The CIW Web Security Professional Certification cultivates this perception by immersing learners in the study of web protocols, encryption systems, authentication frameworks, and defensive infrastructures. Through this extensive immersion, individuals acquire the rare ability to transform conceptual understanding into pragmatic action, ensuring that each digital interaction remains confidential, authentic, and reliable.
The cyberspace of today is defined by interdependence. The growing convergence of cloud computing, mobile devices, artificial intelligence, and the Internet of Things has redefined the security paradigm. Each connected device, each automated process, becomes both an asset and a potential liability. The CIW Web Security Professional Certification prepares individuals to navigate this paradox with intellectual agility. It provides the tools to architect systems that can function autonomously yet securely, fostering innovation without inviting chaos. As threats mutate and expand across different vectors, certified professionals learn to adapt their defense mechanisms, evolving in tandem with the very technologies they safeguard.
A central aspect of this certification lies in mastering encryption—the cryptographic science that forms the linguistic and mathematical shield of the digital age. Encryption converts legible information into unreadable sequences, intelligible only to those possessing the correct decryption key. This ensures that data, whether at rest or in transit, remains immune to interception. The CIW Web Security Professional Certification delves deeply into both symmetric and asymmetric cryptography, exploring techniques such as public-key infrastructure, digital certificates, and hashing algorithms. A certified expert learns how to implement these methods to maintain secure communications between servers, clients, and users. They understand the fragile equilibrium between encryption strength and system performance, and how to tailor security solutions to the unique demands of various environments.
Another cornerstone of expertise developed through this certification is authentication—the validation of identity in a digital ecosystem that thrives on anonymity. The modern internet’s fluid structure necessitates robust identity verification mechanisms to prevent impersonation and unauthorized access. Professionals trained under this certification acquire mastery in designing authentication systems that employ multifactor verification, biometric identifiers, and cryptographic credentials. They learn to identify the vulnerabilities inherent in these systems, ensuring they remain resistant to brute-force attacks, credential stuffing, and social engineering exploits. Authentication is not merely about verifying who someone is; it is about preserving the sanctity of trust within digital interactions.
Beyond encryption and authentication, the CIW Web Security Professional Certification emphasizes the mastery of intrusion detection and prevention systems. Cyber adversaries are no longer isolated individuals operating in obscurity; they are organized, well-funded, and relentless. Certified professionals must therefore maintain an unbroken chain of vigilance. Through extensive study of firewalls, proxy servers, and network monitoring systems, they develop the expertise to recognize the faintest indicators of intrusion. By analyzing log patterns, monitoring traffic behavior, and correlating anomalies, they can identify breaches before they evolve into catastrophic failures. The art of intrusion prevention is both reactive and predictive—it requires intuition, pattern recognition, and the ability to interpret data not as static information but as a dynamic reflection of potential threat behavior.
The certification also immerses professionals in the field of web application security, one of the most critical arenas of modern cybersecurity. Applications form the primary interface between users and services, making them fertile ground for exploitation. A CIW-certified expert learns to scrutinize application architecture, identifying weaknesses such as cross-site scripting, SQL injection, remote file inclusion, and insecure session management. By collaborating closely with development teams, they integrate security at every stage of the software lifecycle—from conceptual design to final deployment. This proactive approach ensures that vulnerabilities are addressed before they manifest in production environments, creating a culture of security-driven development rather than post-failure correction.
Incident response and disaster recovery represent another dimension of the CIW Web Security Professional Certification. Despite the most fortified defenses, breaches can occur. The difference between an organization that collapses and one that recovers lies in the efficiency of its response. Certified professionals are trained to develop and execute structured response protocols, identifying the source of breaches, containing their impact, eradicating malicious elements, and restoring systems to operational stability. They learn the principles of digital forensics, ensuring that every trace of evidence is preserved for analysis and possible legal recourse. This process requires not only technical dexterity but also psychological composure—the ability to operate under pressure while maintaining methodical accuracy.
Risk management forms the philosophical backbone of web security. The CIW Web Security Professional Certification teaches individuals to approach cybersecurity through the lens of calculated risk rather than fear. Every digital asset carries inherent vulnerabilities, but not all risks are equal. Certified professionals learn to assess the probability and potential impact of threats, prioritize defensive efforts, and allocate resources efficiently. This pragmatic approach transforms security from a reactionary expense into a strategic investment. Through understanding organizational hierarchies, compliance requirements, and business objectives, CIW-certified professionals bridge the often-divergent worlds of technology and enterprise governance.
The importance of compliance in the cybersecurity domain cannot be overstated. Global organizations operate across jurisdictions governed by a myriad of data protection regulations. The CIW Web Security Professional Certification ensures that professionals are conversant with standards such as ISO 27001, GDPR, HIPAA, and PCI DSS. They learn to integrate compliance into security frameworks, ensuring that digital operations not only withstand threats but also adhere to the ethical and legal mandates of global commerce. This alignment of technology and law forms the foundation of trustworthy digital ecosystems—where users can interact, transact, and communicate without fear of exploitation or surveillance.
In parallel with compliance, the certification explores the human element of cybersecurity. Technology alone cannot defend against negligence or deception. Social engineering remains one of the most effective tools in the arsenal of cybercriminals. CIW-certified professionals learn to identify the psychological manipulation tactics used in phishing, pretexting, and baiting schemes. More importantly, they develop strategies to counter these tactics through education, awareness campaigns, and organizational culture. They recognize that security is as much about human behavior as it is about technical infrastructure, and that the most resilient systems are those where users understand their role as the first line of defense.
As digital technology continues to integrate artificial intelligence, automation, and machine learning, the CIW Web Security Professional Certification adapts its focus to address the emerging challenges of intelligent systems. AI-driven networks can detect and respond to threats with unprecedented speed, but they also introduce new vulnerabilities—bias in algorithms, data poisoning, and adversarial attacks. Certified professionals learn to navigate these complexities, ensuring that AI systems are both intelligent and secure. They understand the interplay between data ethics, algorithmic transparency, and cybersecurity, creating frameworks that protect not just machines but the integrity of decision-making processes that rely upon them.
The evolution of web security also extends to the realm of cloud computing, where data is no longer confined within physical boundaries. The certification provides deep insight into securing virtual environments, understanding access control in shared infrastructures, and safeguarding cloud-based applications. Certified professionals become adept at managing encryption keys, securing APIs, and auditing cloud configurations to prevent mismanagement and unauthorized exposure. In doing so, they ensure that the advantages of scalability and accessibility offered by the cloud do not come at the cost of confidentiality and control.
Equally significant is the emergence of quantum computing—a transformative force that challenges traditional cryptographic systems. CIW-certified experts are encouraged to stay informed about post-quantum cryptography and other emerging paradigms that will shape the next era of digital security. Their adaptability becomes a defining trait, allowing them to transition seamlessly between technological epochs without losing their strategic foundation. This foresight ensures that the digital infrastructure they protect today remains relevant and resilient in the face of tomorrow’s innovations.
At its core, the CIW Web Security Professional Certification represents an intellectual metamorphosis. It transforms an individual from a passive observer of technology into an active custodian of its integrity. The journey toward mastery involves not only acquiring technical expertise but cultivating a disciplined mindset—one rooted in persistence, curiosity, and ethical awareness. Certified professionals internalize the principle that cybersecurity is not a one-time achievement but a continuous process of adaptation and refinement. In every configuration, every analysis, and every decision, they uphold the balance between progress and preservation.
The demand for web security expertise continues to escalate as organizations expand their digital frontiers. Certified professionals find themselves at the nexus of innovation and protection, where every strategic decision carries implications for both opportunity and vulnerability. Their skills are sought across industries such as finance, healthcare, government, and education, where the integrity of data is inseparable from operational success. Beyond employment, the certification grants individuals the confidence to pursue leadership roles, influence policy, and contribute to the evolution of global cybersecurity standards.
The CIW Web Security Professional Certification is not merely an academic pursuit; it is a philosophical commitment to digital stewardship. Each professional who earns this credential embodies a promise—to defend, to educate, and to innovate with integrity. They stand as sentinels of a world increasingly dependent on invisible architectures of code and connectivity. Their expertise ensures that these architectures remain sanctuaries rather than battlegrounds, places of collaboration rather than conflict.
Conclusion
The essence of the CIW Web Security Professional Certification transcends technical mastery. It represents a lifelong commitment to the guardianship of digital civilization. Certified professionals are not simply technicians; they are strategists, educators, and visionaries. They understand that every byte of information carries value, and that their vigilance preserves the fabric of modern life. As cyber threats evolve and technologies transform, their role becomes ever more vital—not as passive responders, but as architects of security in an era defined by digital interdependence.
Through the pursuit of this certification, individuals acquire not only knowledge but purpose. They gain the ability to interpret complexity, to foresee danger, and to design solutions that protect both data and dignity. The digital realm, with all its vulnerabilities and wonders, depends upon such guardians—those who wield their expertise not for personal gain but for the collective good. The CIW Web Security Professional Certification stands as both a testament to their capability and a symbol of their duty: to ensure that the web, humanity’s most powerful creation, remains secure, ethical, and enduring.
Frequently Asked Questions
How can I get the products after purchase?
All products are available for download immediately from your Member's Area. Once you have made the payment, you will be transferred to Member's Area where you can login and download the products you have purchased to your computer.
How long can I use my product? Will it be valid forever?
Test-King products have a validity of 90 days from the date of purchase. This means that any updates to the products, including but not limited to new questions, or updates and changes by our editing team, will be automatically downloaded on to computer to make sure that you get latest exam prep materials during those 90 days.
Can I renew my product if when it's expired?
Yes, when the 90 days of your product validity are over, you have the option of renewing your expired products with a 30% discount. This can be done in your Member's Area.
Please note that you will not be able to use the product after it has expired if you don't renew it.
How often are the questions updated?
We always try to provide the latest pool of questions, Updates in the questions depend on the changes in actual pool of questions by different vendors. As soon as we know about the change in the exam question pool we try our best to update the products as fast as possible.
How many computers I can download Test-King software on?
You can download the Test-King products on the maximum number of 2 (two) computers or devices. If you need to use the software on more than two machines, you can purchase this option separately. Please email support@test-king.com if you need to use more than 5 (five) computers.
What is a PDF Version?
PDF Version is a pdf document of Questions & Answers product. The document file has standart .pdf format, which can be easily read by any pdf reader application like Adobe Acrobat Reader, Foxit Reader, OpenOffice, Google Docs and many others.
Can I purchase PDF Version without the Testing Engine?
PDF Version cannot be purchased separately. It is only available as an add-on to main Question & Answer Testing Engine product.
What operating systems are supported by your Testing Engine software?
Our testing engine is supported by Windows. Andriod and IOS software is currently under development.
Top CIW Exams
CIW Certifications
- CIW
- CIW Database Design Specialist
- CIW JavaScript Specialist
- CIW Perl Specialist
- CIW Site Development Associate
- CIW Web Design Professional
- CIW Web Design Specialist
- CIW Web Development Professional
- CIW Web Foundations Associate
- CIW Web Security Associate
- CIW Web Security Professional
- Master CIW Designer
- Master CIW Enterprise Developer


