Certification: Certified SOA Security Specialist
Certification Full Name: Certified SOA Security Specialist
Certification Provider: SOA
Exam Code: S90.02
Exam Name: SOA Technology Concepts (S90-02A)
S90.02 Exam Product Screenshots
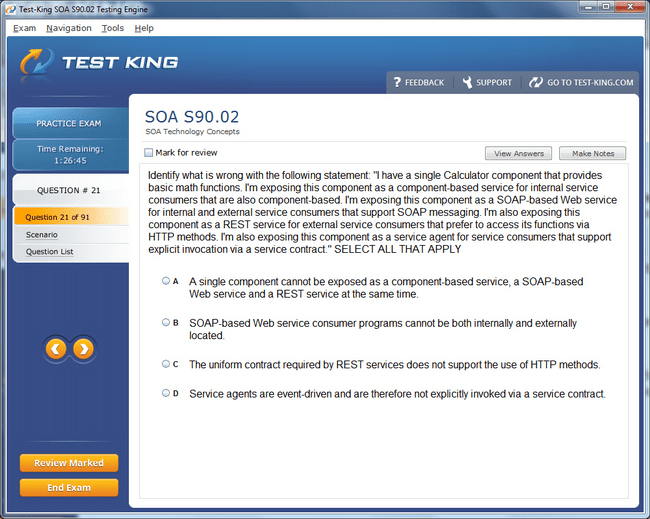
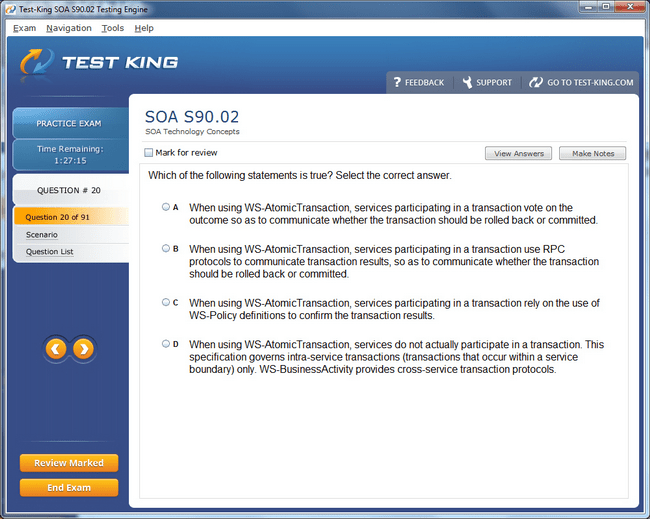
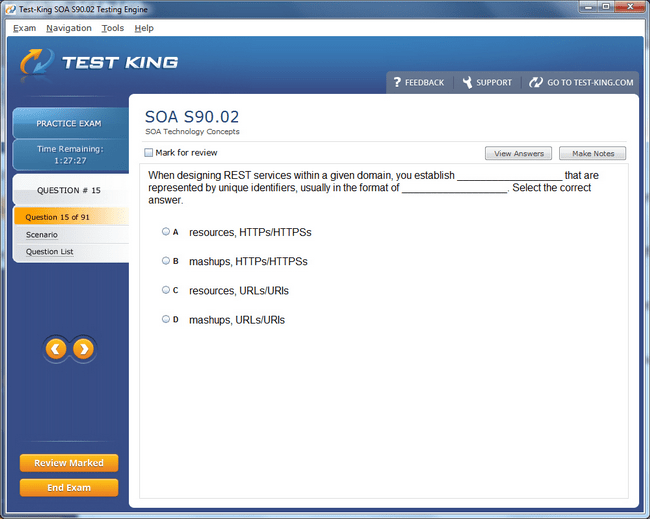
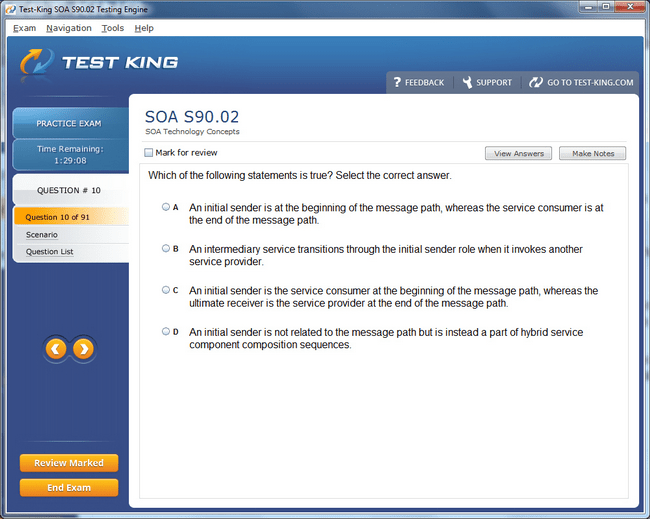
Mastering Service-Oriented Security: Foundations of the Certified SOA Security Specialist Credential
In the sprawling ecosystem of modern enterprise computing, where integration and interoperability form the lifeblood of digital infrastructure, securing service-oriented architectures has become an indispensable mandate. The Certified SOA Security Specialist certification emerges as a vital credential for professionals who seek to comprehend and safeguard the intricate dynamics of distributed systems. This credential is not merely an emblem of theoretical understanding but a validation of one’s capacity to implement, manage, and maintain robust protection mechanisms across interconnected services. The realm of service-oriented security is deeply complex, encompassing authentication, identity management, message integrity, policy enforcement, and encryption, all working in unison to ensure that trust and reliability persist across enterprise boundaries.
Understanding the Core Principles Behind Service-Oriented Security
The Certified SOA Security Specialist certification focuses on the foundations of trust and governance within service-oriented architecture (SOA). It equips professionals with the proficiency to analyze and fortify service ecosystems against both external and internal threats. In an environment where services constantly interact across organizational borders, maintaining confidentiality and authenticity becomes an imperative task. The certification’s curriculum emphasizes understanding SOA’s design principles while seamlessly integrating advanced security patterns that protect data in motion, data at rest, and data in transformation. This dynamic integration of architectural understanding with security expertise makes the credential profoundly relevant to contemporary IT landscapes.
Service-oriented architecture, by its nature, promotes modularity, agility, and reusability. However, these same virtues can also become conduits for vulnerabilities when security is not embedded intrinsically. Each service, interface, and communication channel introduces potential risks that can be exploited by malicious entities. Hence, the role of a Certified SOA Security Specialist transcends conventional boundaries of cybersecurity—it demands mastery over architectural comprehension, governance frameworks, and technological orchestration. Such professionals must perceive the architecture as a living ecosystem, continuously adapting and responding to emerging threats while preserving its foundational stability.
The principles underlying service-oriented security rest upon the pillars of identification, authentication, authorization, integrity, and non-repudiation. These elements ensure that every interaction between services is legitimate, traceable, and shielded from tampering. In complex business ecosystems where services interact across cloud environments, hybrid systems, and legacy platforms, ensuring that each message or transaction adheres to defined security protocols is paramount. The Certified SOA Security Specialist program delves into these components with a methodical approach, illustrating how policy frameworks, identity propagation models, and federated trust mechanisms collaborate to create an unassailable security posture.
A central aspect of mastering SOA security lies in understanding the concept of trust domains. In multi-enterprise collaborations, services often operate across different administrative and technical boundaries. The establishment of secure trust relationships allows these domains to communicate without compromising integrity or confidentiality. This concept is extensively covered within the certification, guiding candidates through the principles of security token services, digital signatures, and encrypted messaging. These tools form the bedrock of secure service communication and reinforce the architectural trust that underpins enterprise collaborations.
Equally vital is the understanding of identity federation within SOA environments. Traditional identity management mechanisms, often siloed within specific systems, are insufficient for modern distributed architectures. Identity federation enables a seamless authentication experience across diverse domains while maintaining strict adherence to security policies. A Certified SOA Security Specialist must be adept at configuring and maintaining these federated systems to ensure that trust is propagated accurately and securely. By leveraging protocols like SAML, OAuth, and WS-Security, they orchestrate a secure exchange of credentials that uphold both user convenience and system integrity.
Policy enforcement and governance represent another cornerstone of SOA security. Without a structured framework to define and enforce security policies, even the most advanced technical mechanisms become vulnerable to inconsistencies and misconfigurations. Governance in SOA security ensures that every service, regardless of its provider or location, adheres to established standards and regulations. The certification emphasizes designing policies that are both adaptable and enforceable, ensuring that security is not a static implementation but a living, evolving discipline. Governance tools and registries are leveraged to monitor compliance, manage exceptions, and facilitate auditing, all of which are critical for maintaining trust across interconnected services.
Moreover, the Certified SOA Security Specialist credential explores the subtleties of message-level security, an area often overlooked in traditional security paradigms. While network-layer protection is essential, service-oriented systems demand additional safeguards to ensure message integrity and confidentiality during transmission. Message-level security mechanisms employ encryption, digital signatures, and timestamp validation to guarantee that the communication remains untampered and authentic, even if transmitted through untrusted intermediaries. This level of granularity in protection exemplifies the sophisticated depth that certified specialists must master.
The modern enterprise operates within a hybrid milieu, blending on-premise infrastructures with cloud-native services. This duality introduces unique security challenges—data may traverse multiple networks, cross jurisdictional boundaries, and encounter differing compliance requirements. The Certified SOA Security Specialist must, therefore, understand how to unify these disparate components under a single, cohesive security strategy. This involves aligning cloud service provider policies with enterprise governance frameworks, implementing consistent encryption standards, and ensuring interoperability between security solutions across heterogeneous environments. Such harmonization requires both technical acumen and strategic foresight.
Risk management within service-oriented architecture represents another dimension of the certification’s focus. Identifying, evaluating, and mitigating risks in a distributed service ecosystem requires analytical precision. The candidate learns to recognize potential vulnerabilities in service communication, identity propagation, and service orchestration layers. Mitigation strategies may include architectural redesign, policy reinforcement, or adopting redundancy and failover mechanisms that sustain availability even under duress. By integrating proactive monitoring and incident response mechanisms, the Certified SOA Security Specialist ensures that risks are managed dynamically rather than reactively.
A significant attribute of this certification is its emphasis on secure service design. Security must be woven into the very fabric of service development rather than appended as an afterthought. The Certified SOA Security Specialist advocates for a security-by-design approach, ensuring that every layer—from service definition to deployment—adheres to best practices in confidentiality, integrity, and availability. Secure service design includes defining precise access control models, embedding input validation routines, and implementing defensive programming techniques. This proactive methodology fosters resilience, reducing the likelihood of breaches and ensuring that services can withstand evolving threats.
The certification also imparts a profound understanding of compliance and regulatory adherence within SOA environments. Organizations today are bound by a plethora of legal and regulatory frameworks governing data protection, privacy, and cybersecurity. Certified professionals must ensure that SOA implementations align with such mandates, whether they stem from international standards or industry-specific guidelines. This requires not only technical expertise but also an awareness of the legal ramifications of data movement across borders. Such holistic understanding positions the Certified SOA Security Specialist as both a technical guardian and a compliance strategist.
Another critical component addressed by the certification is interoperability security. In service-oriented ecosystems, multiple platforms and technologies converge. Ensuring that these heterogeneous systems can communicate securely without compromising on performance or policy adherence is a complex undertaking. A Certified SOA Security Specialist must possess the skill to implement security standards that transcend vendor-specific limitations, fostering interoperability without diminishing protection. This necessitates a deep understanding of WS-Policy, WS-Security, and related specifications that enable seamless yet secure interaction across diverse platforms.
Incident detection and response within SOA infrastructures are further explored as a crucial competency area. Security incidents, whether they arise from external attacks or internal misconfigurations, must be detected swiftly and mitigated effectively. The certification underscores the need for continuous monitoring, employing security information and event management systems that can correlate events across multiple services and environments. A Certified SOA Security Specialist interprets these patterns, identifies anomalies, and initiates corrective actions that restore system integrity while minimizing operational disruption.
Beyond the technical competencies, the certification cultivates an architectural mindset. The Certified SOA Security Specialist is trained to think systemically—viewing security not as a fragmented discipline but as an intrinsic component of architecture. This perspective enables them to design ecosystems where scalability, performance, and protection coexist harmoniously. They can anticipate potential weaknesses introduced by integration, versioning, or service dependencies and design mitigations that maintain the architectural equilibrium. Such foresight distinguishes certified specialists as architects of resilience rather than mere implementers of tools.
Another remarkable feature of the Certified SOA Security Specialist credential is its attention to cryptographic principles. Cryptography forms the backbone of secure service communication, and understanding its application in SOA environments is indispensable. Candidates are expected to comprehend key management, certificate handling, and encryption mechanisms at both transport and message levels. They must also grasp the nuances of asymmetric and symmetric encryption, ensuring that performance and security remain balanced. Effective cryptographic implementation fortifies the trust chain, ensuring that messages and credentials retain their integrity throughout their lifecycle.
As digital transformation continues to redefine enterprise structures, the significance of service-oriented security amplifies. Businesses increasingly rely on microservices, APIs, and containerized applications, all of which echo the principles of SOA. The Certified SOA Security Specialist credential aligns perfectly with these technological shifts, preparing professionals to extend their expertise beyond traditional architectures into emerging paradigms. Whether integrating security into Kubernetes-based services or managing API gateways, the foundational knowledge from SOA security serves as an enduring compass guiding secure design and governance in evolving landscapes.
In a world where digital ecosystems thrive on connectivity, the Certified SOA Security Specialist stands as a sentinel of trust and resilience. The certification’s essence lies not only in understanding security mechanisms but in mastering the orchestration of these mechanisms within complex architectures. It transforms practitioners into strategic architects capable of envisioning, implementing, and sustaining secure service frameworks that uphold organizational integrity. Their proficiency ensures that businesses can innovate with confidence, knowing that their service interactions are safeguarded by rigorously defined principles and fortified by expertise born of deep certification knowledge.
Ultimately, the mastery of service-oriented security transcends mere technicality—it embodies a philosophy of perpetual vigilance, adaptability, and precision. The Certified SOA Security Specialist becomes an orchestrator of trust, ensuring that every digital handshake within an enterprise ecosystem is grounded in authenticity and protected by design. Through disciplined learning and application, this certification empowers professionals to champion the sanctity of data, the sovereignty of architecture, and the continuity of trust in an era where security is both a challenge and an art form.
The Strategic Depth and Applied Proficiency in Service-Oriented Security
In the continuum of modern digital transformation, enterprises are rapidly embracing service-oriented paradigms to achieve elasticity, scalability, and interoperability across their technological frameworks. Yet, this proliferation of interconnected services introduces intricate vulnerabilities that necessitate sophisticated defense mechanisms. The Certified SOA Security Specialist certification emerges as a testament to a professional’s ability to engineer, govern, and safeguard such environments with unwavering precision. It epitomizes a fusion of architectural intellect and security acuity, preparing individuals to navigate the labyrinthine corridors of distributed enterprise systems while fortifying them against emerging perils.
At its core, service-oriented architecture (SOA) represents the synthesis of modularity and integration. Each discrete service, functioning as an autonomous unit, communicates through standardized interfaces, enabling reusability and composability across enterprise boundaries. However, these advantages coexist with inherent complexities, particularly in the domain of security management. The Certified SOA Security Specialist delves into this complexity, offering a profound comprehension of how to integrate rigorous security frameworks without compromising the agility that SOA promises. Professionals trained under this credential are adept at creating environments where security is intrinsic rather than superimposed—where the fabric of the architecture itself becomes a fortress of trust and resilience.
A central tenet of this certification is the comprehension of service governance and its relationship with security enforcement. Governance transcends mere administrative oversight; it embodies the codification of policies, procedures, and standards that dictate how services are developed, deployed, and secured. The Certified SOA Security Specialist learns to implement governance models that ensure uniformity in authentication, encryption, and access control mechanisms across all service endpoints. This ensures that security remains consistent and traceable, even when services are distributed across hybrid infrastructures or managed by multiple stakeholders. Governance also facilitates auditability, a critical attribute for compliance with regulatory frameworks and internal accountability.
Understanding the concept of identity propagation within SOA ecosystems forms another critical layer of expertise. In service interactions that traverse numerous systems, maintaining consistent identity representation is a complex challenge. A Certified SOA Security Specialist must ensure that a user’s identity, once authenticated at the origin, remains intact and verifiable across every subsequent transaction. This involves mastering identity propagation mechanisms that employ tokens, certificates, and digital assertions to preserve the chain of trust. The propagation process must also align with enterprise policies to prevent identity spoofing or unauthorized impersonation. Achieving this delicate balance between usability and security demands both technical finesse and architectural foresight.
Security policy orchestration stands as one of the most vital aspects of service-oriented security. Policies define how services interact, what levels of access are permitted, and how exceptions are handled. Within a multi-domain SOA environment, policy conflicts can easily emerge when disparate services adhere to varying standards. The Certified SOA Security Specialist is equipped to harmonize these policies through a unified governance framework. They design policy enforcement points (PEPs) and policy decision points (PDPs) that ensure each service request is scrutinized, validated, and aligned with the overarching enterprise rules. This orchestration not only enhances protection but also ensures adaptability, allowing security models to evolve with organizational needs.
Another profound aspect addressed within the certification is secure message exchange. While traditional network security mechanisms such as firewalls and intrusion detection systems focus on securing transport layers, SOA security operates at the message level, providing granular control over communication integrity. Message-level security employs mechanisms like digital signatures, encryption, and timestamp validation to ensure that each transaction retains its authenticity and confidentiality from origin to destination. Certified professionals understand how to implement standards such as WS-Security, XML Encryption, and XML Signature to achieve this integrity, even when messages traverse multiple intermediaries or heterogeneous platforms. This intricate understanding transforms them into architects of data sanctity.
In addition to message security, the certification underscores the importance of service registry protection. The service registry acts as a repository that houses critical metadata about available services, endpoints, and interfaces. A compromised registry could lead to catastrophic consequences, enabling attackers to intercept or manipulate service requests. The Certified SOA Security Specialist learns to secure the registry through authentication controls, access restrictions, and encryption mechanisms that prevent unauthorized modifications or data leakage. Furthermore, registry governance ensures that only vetted and compliant services are published, minimizing exposure to insecure or deprecated components.
Trust frameworks form the conceptual backbone of service-oriented security. In distributed ecosystems, establishing trust among disparate services and domains requires structured trust models supported by digital certificates and public key infrastructures (PKI). The Certified SOA Security Specialist develops mastery over creating, managing, and validating trust relationships through security token services and federated identity systems. These frameworks enable secure interactions even when services belong to distinct administrative domains. Trust establishment is not static; it evolves as relationships change, contracts expire, or services are decommissioned. Hence, the specialist must implement dynamic trust negotiation mechanisms that ensure continuity without compromising integrity.
Another dimension of expertise cultivated through this certification pertains to security threat modeling. Threat modeling in service-oriented systems is complex due to the multiplicity of interaction points and the heterogeneity of components. Certified professionals are trained to systematically identify potential vulnerabilities across service compositions, orchestration layers, and data transformation pipelines. They analyze possible attack vectors such as replay attacks, XML injection, message tampering, and denial-of-service attempts. Once identified, these risks are mitigated through architectural controls, security patterns, and defensive coding practices. The emphasis lies in designing preemptive strategies that eliminate weaknesses before exploitation rather than relying solely on reactive countermeasures.
Resilience engineering also occupies a pivotal role in SOA security. In an environment where services interdepend, the failure of one component can cascade throughout the architecture. The Certified SOA Security Specialist is trained to design systems that remain operational even under duress. Techniques such as redundancy, failover mechanisms, and secure load balancing are employed to maintain availability and reliability. Furthermore, specialists ensure that recovery processes are embedded with security considerations, preventing unauthorized access during restoration activities. This convergence of reliability and protection underscores the holistic approach of the certification.
The certification further imparts knowledge on auditing and accountability within SOA environments. Every service invocation, message exchange, and authentication event must be traceable for post-incident analysis and compliance verification. Certified professionals design comprehensive logging and monitoring systems that capture relevant events while preserving privacy and data minimization principles. Audit trails serve dual purposes: they enhance transparency for governance and provide forensic evidence in case of security breaches. By ensuring that logs are tamper-evident and securely stored, the Certified SOA Security Specialist reinforces organizational trust and compliance readiness.
In the modern enterprise, security cannot exist in isolation—it must integrate with business objectives and operational priorities. The Certified SOA Security Specialist bridges this divide, ensuring that security architectures align seamlessly with organizational goals. They participate in strategic decision-making, advising leadership on risk management, policy formation, and technology adoption. Their expertise enables organizations to pursue innovation confidently, knowing that new services or integrations adhere to established security paradigms. By translating technical imperatives into business value, these professionals become indispensable assets in both technology and governance spheres.
The dynamic nature of today’s service ecosystems necessitates continuous adaptation. Emerging technologies such as microservices, serverless computing, and containerization have redefined how services are deployed and managed. The Certified SOA Security Specialist remains relevant amidst these shifts by applying core SOA principles to contemporary architectures. For instance, securing microservices involves extending message-level encryption and policy enforcement to API gateways and service meshes. Similarly, serverless architectures demand meticulous attention to ephemeral identities and function-level authorization. By extrapolating foundational SOA security principles into these new domains, certified professionals ensure that security evolves alongside innovation.
Cryptographic agility forms another domain of expertise that distinguishes certified professionals. In a world where cryptographic algorithms continuously face obsolescence, agility ensures that systems can transition seamlessly to stronger encryption mechanisms without service disruption. The Certified SOA Security Specialist must anticipate cryptographic lifecycle changes and design key management systems that accommodate algorithmic evolution. They understand the implications of cryptographic strength on performance and scalability, making informed decisions that preserve both efficiency and security. This foresight prevents obsolescence-induced vulnerabilities and ensures sustained trustworthiness of the enterprise’s digital fabric.
Interoperability security, a cornerstone of SOA, demands intricate comprehension of cross-platform compatibility. Organizations frequently integrate services built on disparate technologies—Java-based systems interacting with .NET services, or RESTful APIs communicating with SOAP-based endpoints. The Certified SOA Security Specialist must ensure that these interactions remain secure, regardless of underlying implementation differences. Achieving interoperability without weakening security requires a profound understanding of shared standards, message encoding formats, and protocol compatibility. It also involves negotiating trust between heterogeneous systems, ensuring that policy enforcement and encryption mechanisms remain intact across platforms.
Furthermore, the certification explores the concept of secure orchestration, wherein multiple services collaborate to fulfill composite business functions. Orchestration introduces additional layers of complexity, as it aggregates security dependencies from individual services into a unified workflow. The Certified SOA Security Specialist must design orchestration workflows that inherit and enforce the strongest security attributes of participating services. This includes ensuring transactional integrity, non-repudiation, and confidentiality throughout the orchestration lifecycle. They must also safeguard orchestration engines from injection attacks, unauthorized workflow modifications, and data exposure during inter-service communication.
Incident response and recovery planning within SOA environments represent another vital learning domain. Unlike monolithic systems, where containment is straightforward, service-oriented ecosystems require coordinated recovery efforts across multiple components. Certified professionals develop incident response frameworks that specify roles, responsibilities, and communication protocols during a security event. They employ automated remediation techniques that isolate compromised services while maintaining continuity for unaffected components. Post-incident reviews focus on identifying systemic weaknesses and implementing corrective measures that prevent recurrence. Through such disciplined methodologies, the Certified SOA Security Specialist ensures both immediate recovery and long-term resilience.
Equally significant is the understanding of compliance-driven security architectures. Global regulations such as the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and the Payment Card Industry Data Security Standard (PCI DSS) impose stringent requirements on how data is handled within service-oriented frameworks. The Certified SOA Security Specialist ensures that compliance is not an afterthought but an embedded design principle. They map service-level data flows to regulatory obligations, apply encryption to sensitive information, and design audit-ready processes. This proactive compliance integration reduces legal exposure and enhances the organization’s reputation for responsible data stewardship.
The certification also cultivates an awareness of emerging threat landscapes in distributed environments. With the advent of quantum computing, artificial intelligence-driven attacks, and supply chain compromises, traditional defenses may soon prove inadequate. The Certified SOA Security Specialist must remain vigilant and innovative, exploring post-quantum cryptography, anomaly-based intrusion detection, and zero-trust architectures. By staying abreast of evolving technologies and integrating them judiciously into service ecosystems, they ensure that security remains anticipatory rather than reactionary.
Ultimately, the Certified SOA Security Specialist certification molds professionals into guardians of distributed trust. Their expertise extends beyond the confines of encryption and authentication into the realms of governance, compliance, architecture, and strategy. They perceive service-oriented architecture not merely as a technological construct but as a dynamic ecosystem whose vitality depends on continuous protection and ethical stewardship. Through their mastery, enterprises can sustain agility without succumbing to the perils of digital interdependence. In a world increasingly defined by connectivity and collaboration, their role remains not just relevant but indispensable—ensuring that every service interaction, every data exchange, and every architectural evolution unfolds within a sanctuary of trust, resilience, and precision.
Integrating Enterprise Governance and Dynamic Protection in Distributed Service Environments
In the ever-expanding sphere of digital interconnectivity, organizations are experiencing a tectonic shift from monolithic systems to fluid, service-oriented frameworks. This evolution, while empowering efficiency and interoperability, has also intensified the complexity of safeguarding data flows, service transactions, and identity propagation. Within this intricate digital tapestry, the Certified SOA Security Specialist stands as a pivotal guardian, mastering the art of embedding fortification mechanisms within the architectural DNA of enterprise systems. This advanced understanding transforms security from an isolated technical discipline into a continuous governance principle, ensuring that every transaction, message, and communication across distributed services adheres to the highest standards of authenticity, confidentiality, and integrity.
The Certified SOA Security Specialist certification embodies a multidimensional understanding of how governance, technology, and strategic foresight converge to establish sustainable security ecosystems. At its essence, the certification does not merely teach defensive practices but fosters an architectural mentality—one where security is not a product but an intrinsic state of existence. Professionals who achieve this credential learn to view an enterprise as an interconnected organism, where services, APIs, and data flows must coexist under a unified framework of trust and accountability. They learn to anticipate vulnerabilities before they materialize, crafting proactive mechanisms that defend against infiltration while enabling seamless functionality.
In service-oriented architectures, governance serves as the skeletal structure upon which all security controls are built. Without governance, even the most advanced technical solutions can descend into disarray. The Certified SOA Security Specialist is trained to implement a layered governance model, balancing centralized control with distributed autonomy. Governance frameworks outline how services are registered, authenticated, and authorized, ensuring uniform compliance with corporate and regulatory standards. This discipline encompasses policy enforcement, trust verification, auditing mechanisms, and change management processes. Each policy becomes a directive that guides how services interact and how their security attributes are maintained throughout their lifecycle. Governance, therefore, becomes both the compass and the safeguard of enterprise consistency.
A crucial aspect of governance lies in access management. Within SOA environments, the granularity of access control must align with the principle of least privilege, ensuring that entities—whether human or machine—possess only the permissions necessary to perform their designated functions. The Certified SOA Security Specialist learns to design multi-layered access models that incorporate authentication, authorization, and accountability in an integrated manner. This involves employing identity federation and single sign-on mechanisms that extend trust across multiple domains without compromising control. The expert ensures that every transaction can be traced back to a verifiable identity, preserving non-repudiation and facilitating post-event analysis in the event of a security anomaly.
Inter-service communication, a defining attribute of SOA, introduces multifaceted challenges in maintaining message integrity and confidentiality. The certification’s curriculum emphasizes the mastery of message-level security—a paradigm that transcends network protection by embedding cryptographic safeguards directly within service messages. Through techniques such as digital signing, encryption, and secure token exchange, the Certified SOA Security Specialist ensures that every data packet maintains its authenticity, even when traversing untrusted networks or intermediaries. This approach is particularly significant in hybrid and multi-cloud environments, where services may reside across diverse administrative boundaries. Message-level protection acts as a perpetual sentinel, verifying integrity at every stage of transmission.
The architecture of trust is another cardinal element of SOA security. In distributed systems, trust cannot be assumed; it must be earned, established, and periodically reaffirmed. The Certified SOA Security Specialist possesses the expertise to construct trust domains and federated identity frameworks that facilitate secure cooperation among heterogeneous services. By implementing trust negotiation protocols and certificate-based validations, they create dynamic trust relationships that evolve with the system’s topology. These trust mechanisms extend beyond technical authenticity—they embody organizational reliability, ensuring that service providers and consumers operate under mutual confidence. This delicate equilibrium between assurance and autonomy lies at the heart of sustainable service-oriented architectures.
Cryptographic governance constitutes another pillar of expertise within the Certified SOA Security Specialist’s realm. Cryptography serves as both shield and enabler in digital communication. However, cryptographic strength alone is insufficient without proper key lifecycle management. Certified professionals develop proficiency in key generation, distribution, rotation, and revocation, ensuring that cryptographic assets remain resilient against obsolescence and compromise. They learn to apply encryption symmetrically and asymmetrically depending on performance requirements and data sensitivity. Furthermore, they design cryptographic policies that anticipate technological evolution, including the looming influence of quantum computing. Such foresight transforms reactive defense into proactive preservation.
Incident prevention, detection, and response within SOA ecosystems are sophisticated endeavors that demand synchronization across services and layers. The Certified SOA Security Specialist understands that prevention begins with architectural soundness. Secure service design, input validation, and consistent policy enforcement eliminate a vast proportion of vulnerabilities before they are exploited. Yet, no system is impervious, and thus, robust detection mechanisms must accompany these preventative measures. Specialists configure event correlation systems that interpret patterns across distributed logs, recognizing anomalies that may indicate intrusions or policy violations. Upon detection, automated incident responses isolate compromised services, reroute traffic, and alert administrators while ensuring operational continuity. This orchestration of anticipation, recognition, and containment exemplifies the tactical precision that defines advanced service security management.
Beyond technical intricacies, the certification instills an understanding of risk management as an enduring discipline. In a service-oriented environment, risk is not static—it mutates with every integration, update, and dependency introduced into the ecosystem. The Certified SOA Security Specialist cultivates the ability to quantify and prioritize risks based on their potential impact and probability. They employ analytical models that evaluate architectural weaknesses, transactional exposure, and compliance deficiencies. Once identified, these risks are mitigated through architectural reinforcement, policy enhancement, or technological controls. This continuous cycle of risk identification, mitigation, and reassessment ensures that the enterprise remains perpetually resilient, adapting to both predictable and unforeseen challenges.
Data privacy represents another cornerstone of the Certified SOA Security Specialist’s expertise. In an age where data sovereignty and ethical governance command global attention, securing data flows within SOA environments demands rigorous attention. Certified professionals design systems that protect personal and sensitive data through anonymization, tokenization, and contextual access control. They ensure compliance with international data protection frameworks by implementing transparent consent mechanisms and auditable processing trails. Beyond legal adherence, this commitment to privacy cultivates trust between organizations and users, reinforcing the moral fabric of digital operations.
The evolution of enterprise infrastructure toward hybrid and multi-cloud models has further complicated the landscape of SOA security. The Certified SOA Security Specialist navigates this complexity by developing security frameworks that transcend individual platforms. In multi-cloud architectures, services may reside across geographically and administratively distinct domains. Ensuring cohesive security across these boundaries requires harmonization of identity management, encryption standards, and policy enforcement. Certified professionals implement federated governance architectures that unify diverse systems under a single security posture, enabling interoperability without fragmentation. This consolidation is not merely technical—it represents a philosophical alignment of security principles across the enterprise continuum.
Auditing and accountability remain vital to maintaining transparency and credibility within service-oriented ecosystems. The Certified SOA Security Specialist implements auditing mechanisms that capture granular details of service interactions while preserving efficiency. Logs record authentication events, access decisions, and data transactions in a format that supports both real-time monitoring and forensic investigation. These records must be immutable, ensuring their admissibility as evidence in compliance audits or legal inquiries. Moreover, specialists integrate analytics-driven auditing systems that detect behavioral deviations, illuminating hidden threats before they escalate into breaches. The result is a self-aware architecture—one capable of introspection and self-correction through its own audit trails.
Interoperability challenges form another critical domain of focus. As enterprises integrate services from diverse vendors and platforms, maintaining secure communication becomes a formidable challenge. The Certified SOA Security Specialist leverages standards such as WS-Security, WS-Policy, and SAML to achieve secure interoperability. These standards define uniform protocols for message integrity, authentication, and encryption, ensuring that services with disparate technological foundations can still interact securely. However, beyond technical conformance, interoperability demands strategic insight—balancing flexibility with consistency, enabling innovation without diluting protection. The certified professional, therefore, acts as both engineer and diplomat, harmonizing technological diversity within the immutable boundaries of security governance.
Another domain of expertise is resilience architecture—the art of sustaining security even under conditions of failure or attack. In distributed ecosystems, disruptions are inevitable. Network outages, service degradation, and malicious attacks can cascade across interconnected components. The Certified SOA Security Specialist designs resilience mechanisms that localize failures, ensuring that disruptions remain contained. Redundancy, fault tolerance, and secure failover procedures form the backbone of this resilience strategy. Specialists also embed verification routines that validate service integrity during recovery, ensuring that reactivated components remain uncompromised. This dynamic adaptability transforms vulnerability into recoverability, ensuring continuity in the face of adversity.
Monitoring and analytics play a decisive role in maintaining operational vigilance. The Certified SOA Security Specialist utilizes real-time monitoring frameworks that provide visibility across the entire service topology. Metrics such as response times, authentication frequency, and policy compliance rates are continuously analyzed to detect deviations from baseline behavior. Through machine learning-driven analytics, the specialist can identify latent threats that may elude conventional detection systems. This proactive vigilance ensures that the system evolves in tandem with its threat landscape, fortifying itself through continuous observation and adaptation.
Ethical responsibility also forms an integral component of the Certified SOA Security Specialist’s ethos. Beyond the technical dimensions, the professional must recognize the ethical implications of digital defense. Securing service-oriented systems involves safeguarding not just data but human trust. Misuse of authority, negligence in privacy protection, or complacency in compliance can erode this trust irreparably. Thus, certified professionals adhere to a code of conduct grounded in transparency, accountability, and fairness. They ensure that every security measure respects human rights and organizational integrity, elevating their role from mere protectors of systems to custodians of ethical technology.
In addition, the certification emphasizes collaboration across disciplines. Security cannot function in isolation; it requires alignment with developers, architects, business strategists, and compliance officers. The Certified SOA Security Specialist acts as a liaison, translating complex security concepts into actionable business policies. They participate in architectural reviews, guiding developers in implementing secure coding practices and advising executives on regulatory readiness. This interdisciplinary fluency enhances organizational cohesion, ensuring that security considerations permeate every tier of enterprise operation.
Emerging technologies continue to redefine the boundaries of service-oriented security. Artificial intelligence, blockchain, and edge computing introduce novel paradigms of interaction and decentralization. The Certified SOA Security Specialist must adapt by applying traditional security principles to these new contexts. For instance, blockchain’s distributed ledger aligns naturally with SOA’s decentralized nature, but it introduces unique challenges in identity verification and consensus integrity. Similarly, edge computing requires securing services deployed across vast, geographically dispersed networks. By extrapolating foundational SOA security concepts into these evolving domains, certified professionals remain architects of future-ready defense strategies.
Finally, the Certified SOA Security Specialist embodies the synthesis of theory and application. Their expertise extends beyond procedural adherence—they internalize the symbiosis between architectural integrity and security consciousness. They perceive every service invocation as a potential conduit for risk, every policy as a manifestation of trust, and every encryption key as a custodian of digital virtue. Through the continuous refinement of skills, vigilance, and ethical discernment, they transform enterprise architectures into living fortresses—resilient, adaptable, and self-sustaining. Their mastery ensures that service-oriented ecosystems not only function efficiently but endure securely, maintaining equilibrium amid the perpetual flux of technological evolution.
Advanced Mechanisms of SOA Security in Distributed Enterprise Systems
In the contemporary digital paradigm, service-oriented architectures have become the linchpin of enterprise integration, enabling dynamic interoperability among diverse systems, applications, and services. As organizations transition toward cloud-native infrastructures, microservices, and distributed digital ecosystems, the need for fortified SOA security mechanisms has amplified exponentially. The Certified SOA Security Specialist credential embodies the expertise required to safeguard such architectures through comprehensive frameworks that intertwine authentication, authorization, confidentiality, and integrity. Within the dynamic interplay of these principles, professionals learn to orchestrate multifaceted protection strategies that adapt to complex organizational demands and evolving cyberthreats.
At its essence, the certification cultivates a profound understanding of how service-oriented architectures are structured, how they communicate, and where vulnerabilities often emerge. Every service in a distributed environment functions as an autonomous entity, interacting with others through well-defined interfaces. These interactions, though streamlined for interoperability, open vectors for interception, tampering, or impersonation if not rigorously protected. Thus, mastering SOA security is not limited to encryption or access controls but extends into constructing a holistic security posture embedded within each service transaction. This intricately layered approach is what distinguishes an ordinary practitioner from a Certified SOA Security Specialist.
A crucial tenet in securing SOA environments is the establishment of robust identity management frameworks. Since services operate autonomously, identifying and verifying each requestor becomes paramount. The specialist must be proficient in employing federated identity systems that enable secure credential propagation across diverse domains without exposing sensitive data. Techniques such as Security Assertion Markup Language (SAML) and OAuth are not merely tools but philosophies that govern trust relationships among distributed systems. Through these, the Certified SOA Security Specialist ensures that every transaction, whether internal or external, adheres to an inviolable chain of trust.
Equally vital is the discipline of policy enforcement across services. In traditional systems, policies are often centralized, but SOA requires decentralized yet harmonized governance. The certification program imparts the intricacies of defining and applying service-level policies that dictate who can access which resources and under what conditions. Policies may include conditions for data transformation, message encryption, or validation of digital signatures. The Certified SOA Security Specialist develops the intellectual acumen to design policy enforcement points (PEPs) that act as sentinels at critical junctures, ensuring every communication adheres to organizational mandates and compliance standards.
The certification also delves deep into the conceptual and practical aspects of message-level security, which is indispensable in SOA environments where communication traverses multiple intermediaries. Unlike transport-level security, which protects only the communication channel, message-level security ensures the integrity and confidentiality of individual messages irrespective of the transport medium. The Certified SOA Security Specialist is trained to embed security tokens, apply XML encryption and digital signatures, and maintain end-to-end protection even when messages are routed through various intermediaries. Such meticulous attention to detail ensures that no component of the architecture becomes a weak link.
One of the most intricate challenges in service-oriented architectures is the management of distributed trust domains. When multiple organizations collaborate through services, establishing and maintaining trust becomes an endeavor of both technical and procedural significance. The Certified SOA Security Specialist gains expertise in trust federation models, certificate management, and cross-domain authentication techniques that preserve confidentiality while enabling interoperability. A delicate equilibrium must be achieved—too much restriction impedes functionality, whereas too little exposes the system to compromise. It is this nuanced balance that epitomizes mastery in SOA security.
Beyond these technical proficiencies, the certification emphasizes architectural foresight. Securing an SOA environment is not solely about defensive mechanisms but also about designing resilience. The Certified SOA Security Specialist learns to architect services in a way that isolates failures, limits blast radii, and provides graceful degradation under attack conditions. This involves understanding dependencies between services, implementing redundancy in authentication mechanisms, and ensuring fault tolerance across the service chain. Each architectural decision reflects a security philosophy that prioritizes stability and continuity as much as protection.
Moreover, the Certified SOA Security Specialist develops a discerning comprehension of compliance landscapes and governance frameworks. SOA security is not an isolated discipline; it operates within the boundaries of international standards and legal mandates such as ISO 27001, GDPR, and industry-specific regulations. The certification empowers professionals to translate these abstract directives into tangible service-level controls, ensuring compliance without stifling innovation. Governance mechanisms such as audit trails, security metrics, and monitoring systems become the operational instruments of transparency and accountability.
The orchestration of security in SOA environments also involves continuous observation and adaptation. The Certified SOA Security Specialist is adept at implementing monitoring architectures that provide real-time insights into anomalies, breaches, or policy violations. By leveraging security information and event management (SIEM) tools and integrating them into SOA governance layers, professionals ensure proactive defense. Monitoring is not simply about detection; it is about anticipation—recognizing behavioral deviations that suggest potential vulnerabilities before they evolve into incidents.
Another vital area explored through this certification is encryption management within SOA. Encryption must be contextual—data in transit demands one type of protection, while data at rest requires another. The Certified SOA Security Specialist comprehends the delicate art of key management, understanding that encryption is only as strong as the protection of its cryptographic keys. This involves the use of hardware security modules (HSMs), automated key rotation, and lifecycle management processes that prevent both misuse and operational failure.
Interoperability, a hallmark of SOA, introduces unique complications for security enforcement. Systems built on disparate technologies must still exchange information securely. The Certified SOA Security Specialist learns to bridge technological divides using platform-agnostic protocols, ensuring that security policies remain intact across heterogeneous environments. Through practical exposure and analytical rigor, specialists gain the competence to align legacy systems with contemporary security paradigms, extending protection without requiring complete overhauls.
Resilience against evolving cyber threats is another cornerstone of this professional path. Threats targeting SOA architectures are often subtle, exploiting misconfigurations, unprotected endpoints, or weak policy enforcement. The certification encourages proactive threat modeling, where professionals anticipate possible attack vectors, simulate exploit conditions, and devise countermeasures. This includes identifying potential risks such as XML injection, replay attacks, or denial-of-service attempts against service registries. Through such preemptive practices, the Certified SOA Security Specialist transcends reactive security and adopts a forward-thinking defensive posture.
Another intricate discipline within SOA security is the protection of service registries. Registries function as directories that catalog available services and their access points. If compromised, they can serve as conduits for impersonation or misdirection. The Certified SOA Security Specialist ensures that registries are guarded by strict authentication and authorization controls, limiting visibility to trusted entities and preventing disclosure of sensitive service metadata. Securing the registry ensures that only verified services are discoverable, thereby reducing exposure to malicious intrusions.
Performance optimization within secure SOA environments represents an intellectual challenge that balances protection with efficiency. Excessive encryption layers or policy validations can introduce latency. The Certified SOA Security Specialist must develop architectural sensitivity to ensure that security does not compromise system agility. This involves selective application of security layers, caching strategies for authentication tokens, and optimization of cryptographic algorithms. The result is an equilibrium where performance and protection coexist in harmony.
A pivotal aspect of the certification curriculum lies in governance and lifecycle management. Services evolve, policies change, and threats mutate; therefore, security cannot remain static. The Certified SOA Security Specialist internalizes the discipline of lifecycle-oriented governance—designing controls that adapt to evolving services without destabilizing operations. Version management, deprecation policies, and secure service retirement processes are treated as essential components of sustainable SOA security.
Beyond enterprise boundaries, the Certified SOA Security Specialist also operates within multi-cloud and hybrid environments, where services span diverse infrastructures. In such contexts, traditional perimeter-based security becomes obsolete. Instead, the certification equips professionals with the capability to implement zero-trust principles within service interactions. Every service request, regardless of origin, is verified, authenticated, and authorized. This paradigm shift demands both conceptual clarity and practical dexterity—traits cultivated through the certification’s rigorous methodology.
The Certified SOA Security Specialist further gains expertise in incident response and remediation in distributed architectures. When breaches occur, their propagation across services can be swift and complex. Professionals learn to isolate compromised services, revoke affected credentials, and restore integrity without systemic collapse. Forensic readiness becomes part of the strategy, enabling detailed post-incident analysis and continuous refinement of defensive controls.
Another distinguishing dimension of this certification lies in its emphasis on collaboration between security and architecture teams. The Certified SOA Security Specialist does not operate in isolation but serves as the connective tissue between developers, architects, and governance authorities. This interdisciplinary fluency ensures that security is woven into design from inception rather than retrofitted after deployment.
Furthermore, as organizations transition toward microservices, the Certified SOA Security Specialist’s expertise remains profoundly relevant. Microservices inherit the principles of SOA but introduce granular autonomy and faster evolution. Securing them requires the same foundational discipline—identity propagation, message integrity, encryption, and policy orchestration—but at greater scale and velocity. The certification thus prepares professionals not only for current architectures but also for emerging paradigms that continue to evolve in complexity and scale.
Through its comprehensive framework, the Certified SOA Security Specialist certification cultivates mastery in the art and science of securing distributed systems. The professionals who pursue it acquire not only technical proficiency but also strategic vision, enabling them to perceive security as a living, evolving ecosystem rather than a static configuration. They learn to articulate protection through architecture, to balance constraints with capabilities, and to sustain integrity amidst continuous transformation. This intellectual maturity defines the true essence of service-oriented security—an intricate symphony of trust, technology, and foresight that safeguards the digital enterprise in an era of relentless connectivity.
Governance Frameworks, Trust Management, and Strategic Resilience in SOA Security
In the ever-evolving landscape of digital enterprise systems, governance and trust have become the cornerstones of sustainable service-oriented architecture security. The Certified SOA Security Specialist embodies the rare synthesis of technical expertise and strategic foresight necessary to sustain secure interoperability in distributed environments. Within the intricate orchestration of interconnected services, governance defines order, trust establishes assurance, and resilience ensures endurance. Together, these constructs form the triumvirate foundation that distinguishes a truly mature SOA security ecosystem. This intricate discipline is not confined to static rules but extends into the art of harmonizing policy enforcement, authentication hierarchies, and regulatory adherence across dynamic systems that transcend traditional architectural boundaries.
The Certified SOA Security Specialist is fundamentally a custodian of governance principles within complex architectures. Governance, in this context, transcends administrative control; it represents an architectural philosophy that aligns technical mechanisms with organizational imperatives. It dictates how policies are conceived, propagated, and enforced across the entire service landscape. A well-governed SOA environment manifests as a symphony of defined roles, transparent policies, auditable actions, and adaptive controls. Professionals who earn the certification understand that governance is not merely about compliance—it is about cultivating discipline, predictability, and accountability across all service interactions.
Within this governance matrix, trust management occupies a vital position. Trust is the invisible currency that enables secure interactions among autonomous services operating across diverse domains. The Certified SOA Security Specialist develops an advanced comprehension of how trust is constructed, exchanged, and maintained in distributed systems. This includes the design of federated trust models where multiple identity providers collaborate under a unified framework, allowing secure authentication and authorization without redundancy or exposure. In such ecosystems, trust is propagated through security tokens, digital certificates, and cryptographic assertions, each validated through meticulously designed protocols.
Trust, however, is not static. It evolves with the operational environment, necessitating constant recalibration and validation. The Certified SOA Security Specialist ensures that trust relationships are dynamic, governed by revocation mechanisms, renewal cycles, and verification audits. A certificate, for instance, is not an eternal marker of authenticity—it has a lifecycle that must be vigilantly managed. If an identity provider is compromised, the entire trust network can be jeopardized. Hence, professionals in this field learn to architect federated trust infrastructures that are both resilient and revocable, ensuring that the compromise of one node does not cascade into systemic failure.
A crucial element of governance within SOA security involves policy harmonization across heterogeneous services. Each service may adhere to its own operational policies, yet enterprise-level uniformity is essential for coherent protection. The Certified SOA Security Specialist excels in designing unified policy frameworks that integrate with service-level governance tools. Policies govern access control, message handling, data retention, and authentication protocols. Through intelligent orchestration, these policies function autonomously yet remain synchronized, maintaining balance between independence and uniformity.
Equally important is the understanding of security metadata management. In a service-oriented architecture, metadata encapsulates descriptive information about services, including access endpoints, encryption requirements, and authentication methods. The Certified SOA Security Specialist treats metadata as a strategic asset. Misconfigured or exposed metadata can serve as a reconnaissance tool for adversaries, providing insights into the system’s architecture. Thus, professionals are trained to protect metadata through encryption, controlled visibility, and rigorous validation processes, ensuring that it serves legitimate discovery without becoming a vector for exploitation.
Another dimension of governance revolves around auditing and accountability. The Certified SOA Security Specialist integrates auditing as a continuous, non-intrusive mechanism that chronicles every service interaction for traceability and compliance. In an environment composed of thousands of service calls per second, effective audit trails must be both scalable and immutable. Audit records serve as the forensic backbone for post-incident analysis, compliance verification, and performance assessment. The professional ensures that audit systems are resilient to tampering, leveraging digital signatures and time-stamping to preserve evidentiary integrity.
Compliance plays a crucial role in governance as well. SOA security operates within the broader jurisdiction of international and regional mandates, including data protection laws, privacy regulations, and cybersecurity frameworks. The Certified SOA Security Specialist translates these abstract mandates into executable service-level controls. For instance, data residency laws may require that specific information remain within defined geographical boundaries. The specialist ensures that services comply through policy enforcement mechanisms that restrict cross-border data flows while maintaining operational efficiency.
Trust management also involves behavioral verification beyond cryptographic assertions. Behavioral trust models assess service reliability based on performance metrics, reputation, and historical interactions. The Certified SOA Security Specialist employs analytical tools to evaluate these dimensions, creating adaptive trust decisions that respond to contextual shifts. For example, a service exhibiting irregular response patterns might trigger additional verification steps, ensuring that trust is not blind but conditional. This form of dynamic trust modeling is essential in defending against sophisticated threats such as credential misuse or service impersonation.
Risk management forms the underlying substrate of SOA governance. Every service interaction introduces risk—be it technical, procedural, or human. The Certified SOA Security Specialist identifies, quantifies, and mitigates these risks through a systematic process that integrates seamlessly into the SOA lifecycle. Risk assessments are not isolated exercises but ongoing evaluations synchronized with architectural evolution. Threat modeling, vulnerability analysis, and impact assessment become continuous practices that inform governance policies and technical implementations alike.
Strategic resilience in SOA security extends far beyond redundancy or fault tolerance. It involves cultivating adaptability within both systems and processes. The Certified SOA Security Specialist designs architectures that can reconfigure under duress, isolate anomalies, and maintain service continuity even when components fail. This adaptability requires deep understanding of dependency graphs, service orchestration layers, and fallback mechanisms. Through architectural redundancy and intelligent routing, specialists ensure that critical services remain operational even amidst partial compromise or degradation.
Incident preparedness is another essential component of resilience. The Certified SOA Security Specialist establishes incident response blueprints tailored for service-oriented environments, where incidents may propagate across multiple services and domains. These blueprints define escalation protocols, isolation procedures, and communication frameworks that enable swift containment. The specialist ensures that these responses are automated where feasible, minimizing human latency and reducing the attack window.
One of the most sophisticated aspects of the certification lies in the study of security governance evolution in hybrid and multi-cloud architectures. As organizations distribute their services across diverse platforms, governance must transcend local boundaries. The Certified SOA Security Specialist learns to unify governance across clouds, ensuring consistent policy enforcement, synchronized authentication, and uniform audit visibility. This requires mastery of both traditional SOA principles and contemporary cloud-native paradigms such as identity federation, API gateways, and zero-trust architecture.
A modern Certified SOA Security Specialist also understands that resilience is not purely technical—it is psychological and cultural. Security culture within an organization determines how policies are perceived, adopted, and maintained. Governance without cultural reinforcement devolves into formality. Hence, the specialist plays a pedagogical role, promoting awareness and compliance among teams. By fostering a culture of accountability and vigilance, governance transitions from an imposed directive into an intrinsic behavior.
Trust ecosystems in service-oriented architectures also hinge upon cryptographic key governance. Cryptography underpins nearly every aspect of SOA security—encryption, digital signatures, authentication, and integrity verification. The Certified SOA Security Specialist comprehends the delicate choreography of key generation, distribution, storage, and revocation. Mismanagement of keys can dismantle even the most robust architecture. Therefore, specialists employ hardware security modules and automated key lifecycle systems to preserve both accessibility and inviolability.
A profound yet often underestimated aspect of SOA governance involves interoperability governance. The Certified SOA Security Specialist ensures that governance frameworks remain compatible across varying technologies, platforms, and vendors. This includes the alignment of message formats, security standards, and protocol versions. Such governance not only sustains operational fluidity but also guarantees that security enforcement is consistent regardless of underlying technology.
The specialist’s strategic lens also extends to monitoring and continuous improvement. Governance and trust management are not static milestones—they are cyclical processes of evaluation and enhancement. Continuous monitoring ensures that governance controls remain effective as threats evolve. The Certified SOA Security Specialist employs analytics, telemetry, and behavioral baselines to identify deviations, measure policy adherence, and forecast potential vulnerabilities. The discipline’s ultimate aim is not to create an unchanging fortress but a living ecosystem that adapts intelligently to emerging threats.
Another advanced concept within the certification’s domain is service reputation management. Reputation serves as an intangible yet powerful trust indicator. The Certified SOA Security Specialist develops frameworks for monitoring service reliability, failure rates, and compliance consistency to determine reputation scores. High-reputation services are prioritized in interactions, while low-reputation entities undergo enhanced scrutiny or isolation. This dynamic stratification of trust introduces a self-regulating mechanism that enhances systemic resilience.
In addition to these operational elements, strategic foresight is central to the Certified SOA Security Specialist’s philosophy. Governance must anticipate technological evolution—quantum computing, decentralized architectures, and AI-driven automation will reshape SOA security landscapes. Specialists must envision governance models capable of integrating future paradigms without fracturing existing stability. They must conceive of cryptographic agility that can withstand post-quantum threats and adaptive authentication frameworks that evolve with identity paradigms.
Another indispensable realm of expertise lies in privacy governance. As data traverses multiple services and domains, privacy risks multiply. The Certified SOA Security Specialist enforces privacy by design principles, ensuring that every service interaction minimizes data exposure, enforces anonymization, and complies with consent directives. Privacy governance operates alongside security governance but demands its own distinct focus on ethical stewardship, transparency, and data sovereignty.
Furthermore, resilience extends into supply chain governance. Modern enterprises depend on third-party services, and each external dependency introduces potential exposure. The Certified SOA Security Specialist implements vendor risk assessment programs and enforces integration policies that demand compliance with internal security standards. This layered defense mechanism ensures that external entities do not compromise the enterprise’s internal sanctity.
The discipline of resilience also demands predictive insight. The Certified SOA Security Specialist employs threat intelligence feeds, behavioral analytics, and anomaly detection algorithms to foresee vulnerabilities before they manifest. By integrating these predictive capabilities into governance frameworks, specialists transform reactive defenses into anticipatory systems. This metamorphosis from reaction to anticipation is emblematic of true mastery in SOA security.
Finally, the Certified SOA Security Specialist serves as a strategic architect of enduring trust. Their expertise transcends mere technical implementation, manifesting instead as a harmonization of architecture, governance, and human intent. In their stewardship, the service-oriented architecture becomes not merely a collection of interoperable services but an organism of trust, resilience, and adaptability. Governance becomes its nervous system, trust its circulatory essence, and resilience its unyielding frame. Through disciplined mastery, continuous vigilance, and strategic intellect, the Certified SOA Security Specialist ensures that the digital enterprise remains both agile and inviolable in an era defined by complexity and interconnectivity.
The Evolution of SOA Security Practices and the Strategic Value of the Certified SOA Security Specialist Credential
The digital ecosystem has undergone an extraordinary metamorphosis, transitioning from monolithic infrastructures to highly distributed, service-oriented frameworks that operate across heterogeneous platforms, hybrid clouds, and interconnected environments. Within this multifaceted transformation, the role of security has transcended mere protection—it has become a foundational principle guiding the design, deployment, and governance of modern enterprise systems. The Certified SOA Security Specialist stands at the confluence of architecture, trust, and innovation, orchestrating complex security measures that sustain interoperability without compromising resilience or agility. This advanced certification signifies not only technical mastery but also a refined comprehension of how digital services interrelate within a shared trust domain, demanding both precision and foresight in implementation.
The journey toward mastering SOA security begins with an understanding that services no longer function as isolated units but as dynamic participants in an ever-expanding network of interactions. Each service call, message exchange, or authentication handshake represents a potential point of vulnerability if not properly safeguarded. The Certified SOA Security Specialist recognizes that true protection emerges not from rigid isolation but from intelligently interwoven defenses. Security in SOA is an act of orchestration rather than imposition—it requires every service, policy, and protocol to function in coherent harmony. Such mastery is cultivated through deliberate governance, meticulous design, and an unwavering commitment to consistency.
One of the central doctrines within service-oriented security revolves around trust federation and identity propagation. In contemporary ecosystems, users and applications frequently interact across multiple domains, each governed by distinct authentication authorities. The Certified SOA Security Specialist ensures that these boundaries do not become barriers but conduits of secure trust exchange. Federated identity frameworks such as SAML, OpenID Connect, and OAuth exemplify the mechanisms through which secure credential delegation occurs. These frameworks allow users authenticated in one domain to access services in another without the risk of repeated exposure of credentials. However, these processes demand scrupulous oversight—token expiration, signature validation, and replay prevention must all be orchestrated with mathematical precision to avoid exploitation.
A critical aspect of SOA security that the Certified SOA Security Specialist must internalize is message integrity. Every exchange in a service-oriented environment, regardless of complexity, must guarantee authenticity and immutability. To achieve this, specialists employ message-level encryption and digital signatures, ensuring that no intermediary can alter content without detection. This approach is especially indispensable when messages traverse untrusted networks or intermediaries such as brokers and gateways. By embedding integrity mechanisms directly into the message payload, the Certified SOA Security Specialist guarantees that data remains uncorrupted, even if transmission channels are compromised.
Another vital component of mastery lies in understanding the interplay between policy governance and operational flexibility. Policies define the behavioral and security expectations for services—who can invoke them, under what circumstances, and with what constraints. The Certified SOA Security Specialist is tasked with designing adaptable policy frameworks that uphold security without stifling agility. Policies are treated as living constructs, evolving with organizational needs and threat landscapes. Their enforcement, whether through centralized policy decision points or distributed enforcement nodes, must align with architectural realities. The challenge lies in harmonizing granularity with manageability—too fine-grained an approach introduces complexity, while overly broad rules erode precision.
Moreover, as SOA continues to integrate with microservices, APIs, and containerized ecosystems, the Certified SOA Security Specialist’s expertise extends into the realm of decentralized control. Microservices operate independently, yet they share communication channels and data flows that must be protected. Specialists must adapt traditional SOA principles to contemporary patterns such as service meshes, which rely on sidecar proxies for secure communication, mutual TLS authentication, and real-time traffic governance. Although the underlying technologies differ, the philosophical essence remains unchanged: maintaining inviolable trust relationships while ensuring seamless communication.
One of the most sophisticated challenges in SOA security governance is the implementation of zero-trust principles. The Certified SOA Security Specialist acknowledges that no entity, whether internal or external, should be inherently trusted. Every request must be continuously verified, every session revalidated, and every identity authenticated afresh. This paradigm dismantles the archaic notion of secure perimeters, replacing it with context-aware validation that operates at every layer of interaction. In this model, the professional becomes both architect and sentinel, enforcing trust boundaries that shift dynamically with context and behavior.
The discipline also extends deeply into the domain of data protection and privacy preservation. In service-oriented architectures, data moves continuously between services, often across jurisdictions and infrastructures. The Certified SOA Security Specialist ensures that every transfer adheres to data minimization principles, encryption mandates, and jurisdictional compliance obligations. Sensitive attributes are masked, anonymized, or pseudonymized depending on business logic and legal constraints. Privacy governance becomes a perpetual process embedded into service design rather than an afterthought. Through these mechanisms, enterprises achieve the delicate equilibrium between accessibility and confidentiality.
In addition to defensive measures, the Certified SOA Security Specialist must also embody an analytical mindset that anticipates future vulnerabilities. Predictive risk assessment, supported by threat modeling and simulation, allows specialists to foresee possible exploit vectors and mitigate them preemptively. They examine the architecture through an adversarial lens, identifying potential weaknesses in authentication sequences, dependency chains, or service discovery protocols. Such anticipatory thinking transforms security from a reactive shield into a proactive force. The professional learns to perceive threats not as isolated incidents but as evolving patterns that can be countered through architecture, automation, and adaptive intelligence.
An integral function of SOA security lies in continuous monitoring and behavioral analytics. The Certified SOA Security Specialist constructs surveillance frameworks capable of detecting anomalies across thousands of transactions. Every deviation—whether in message frequency, payload structure, or authentication sequence—can signify a potential compromise. To manage this complexity, specialists integrate monitoring systems with governance frameworks, creating real-time visibility across services. These insights feed into adaptive policy engines that adjust enforcement dynamically, ensuring that responses are both timely and precise.
Trustworthiness in SOA ecosystems also hinges upon secure communication protocols. While transport-level security mechanisms such as TLS provide foundational confidentiality, message-level security adds persistence to trust. The Certified SOA Security Specialist must discern when to apply each method and how to layer them effectively. For internal communications within trusted boundaries, transport encryption may suffice, but external or multi-domain interactions demand message encryption that persists beyond transient connections. This layered approach exemplifies the sophistication and discernment that the certification cultivates.
Beyond the technical sphere, the Certified SOA Security Specialist must possess a refined grasp of regulatory frameworks. As service-oriented systems expand globally, compliance becomes a multidimensional challenge encompassing data sovereignty, auditability, and legal interoperability. The specialist translates regulatory imperatives—such as GDPR, HIPAA, and ISO 27001—into tangible service-level controls. Compliance is not treated as a burden but as an architectural discipline, shaping policies, authentication flows, and data-handling procedures. The result is an ecosystem that is not only secure but also ethically and legally sound.
Resilience remains the guiding philosophy that underpins the work of the Certified SOA Security Specialist. Security cannot be inflexible; it must endure turbulence without collapsing. Resilient architectures are self-healing, fault-tolerant, and designed for continuity. The professional ensures that service degradation does not equate to system failure. Circuit breakers, redundancy mechanisms, and dynamic rerouting are architected not as afterthoughts but as intrinsic properties of secure service design. In such architectures, even when one node falters, others sustain the continuum of trust and functionality.
Furthermore, collaboration is intrinsic to the Certified SOA Security Specialist’s role. They act as the liaison between development, operations, and compliance teams, ensuring that security permeates the software lifecycle from inception to decommissioning. DevSecOps practices are integrated into SOA environments, where automated pipelines validate compliance, test encryption protocols, and enforce policy adherence before deployment. This integration transforms security into a developmental constant rather than a post-deployment correction.
A sophisticated area of focus for the Certified SOA Security Specialist is cryptographic governance. Encryption algorithms evolve, and what is secure today may be obsolete tomorrow. Professionals must ensure cryptographic agility—the ability to transition algorithms and key lengths without disrupting operations. As quantum computing looms on the horizon, the Certified SOA Security Specialist must prepare for post-quantum cryptographic standards, ensuring future-proof protection for existing systems. This foresight distinguishes the visionary from the merely competent, establishing long-term trustworthiness across evolving technological epochs.
In hybrid and multi-cloud environments, where services interconnect across varied infrastructures, the Certified SOA Security Specialist orchestrates consistent policy enforcement. Cloud platforms may differ in authentication mechanisms or encryption capabilities, yet security uniformity must be preserved. Specialists implement federated governance, unifying authentication, audit, and monitoring across all domains. This consistency not only ensures protection but also enhances operational predictability, enabling organizations to scale securely without fragmentation.
Incident management within service-oriented architectures represents a domain of unparalleled complexity. The Certified SOA Security Specialist develops incident response architectures capable of isolating compromised services, halting malicious propagation, and restoring operational integrity. Each incident response plan is contextualized—tailored to the topology, service dependencies, and business criticality of the environment. Automation plays a pivotal role here, reducing human latency and ensuring deterministic remediation actions. Forensic readiness complements these processes, ensuring that post-incident analysis yields actionable insights for architectural reinforcement.
Moreover, the Certified SOA Security Specialist upholds the ethical dimensions of security governance. In a world where digital trust governs human interaction, the professional must navigate not only technical complexities but moral obligations. Transparency, fairness, and accountability must inform every architectural decision. Ethical security ensures that defensive mechanisms do not infringe upon user rights or compromise equity in access. This moral grounding transforms the specialist from a mere technologist into a steward of digital integrity.
As artificial intelligence becomes increasingly integrated into SOA environments, the Certified SOA Security Specialist must adapt to new paradigms of risk. Machine learning models may drive decision-making processes within services, introducing vulnerabilities such as data poisoning, model inversion, or adversarial manipulation. Specialists develop safeguards that validate AI behavior, monitor decision consistency, and preserve algorithmic integrity. This confluence of AI and SOA security exemplifies the evolving complexity of the discipline and the necessity of perpetual learning.
Conclusion
The Certified SOA Security Specialist represents the embodiment of strategic intellect and technological mastery in an era defined by interconnectivity and uncertainty. Their work transcends traditional cybersecurity boundaries, evolving into an architectural art form where governance, trust, and resilience coalesce. Through the lens of this certification, security becomes not a reactionary measure but a structural essence interwoven into the fabric of every service interaction. The Certified SOA Security Specialist ensures that enterprises not only withstand disruption but also thrive within it—protected, adaptable, and perpetually aligned with the principles of integrity and trust. In mastering service-oriented security, these professionals forge the invisible architecture of confidence that sustains the digital world, transforming ephemeral connections into enduring alliances of assurance and technological equilibrium.
Frequently Asked Questions
How can I get the products after purchase?
All products are available for download immediately from your Member's Area. Once you have made the payment, you will be transferred to Member's Area where you can login and download the products you have purchased to your computer.
How long can I use my product? Will it be valid forever?
Test-King products have a validity of 90 days from the date of purchase. This means that any updates to the products, including but not limited to new questions, or updates and changes by our editing team, will be automatically downloaded on to computer to make sure that you get latest exam prep materials during those 90 days.
Can I renew my product if when it's expired?
Yes, when the 90 days of your product validity are over, you have the option of renewing your expired products with a 30% discount. This can be done in your Member's Area.
Please note that you will not be able to use the product after it has expired if you don't renew it.
How often are the questions updated?
We always try to provide the latest pool of questions, Updates in the questions depend on the changes in actual pool of questions by different vendors. As soon as we know about the change in the exam question pool we try our best to update the products as fast as possible.
How many computers I can download Test-King software on?
You can download the Test-King products on the maximum number of 2 (two) computers or devices. If you need to use the software on more than two machines, you can purchase this option separately. Please email support@test-king.com if you need to use more than 5 (five) computers.
What is a PDF Version?
PDF Version is a pdf document of Questions & Answers product. The document file has standart .pdf format, which can be easily read by any pdf reader application like Adobe Acrobat Reader, Foxit Reader, OpenOffice, Google Docs and many others.
Can I purchase PDF Version without the Testing Engine?
PDF Version cannot be purchased separately. It is only available as an add-on to main Question & Answer Testing Engine product.
What operating systems are supported by your Testing Engine software?
Our testing engine is supported by Windows. Andriod and IOS software is currently under development.


