Certification: F5-CTS LTM
Certification Full Name: F5 Certified Technology Specialist Local Traffic Manager (LTM)
Certification Provider: F5
Exam Code: 301b
Exam Name: BIG-IP Local Traffic Manager (LTM) Specialist: Maintain & Troubleshoot
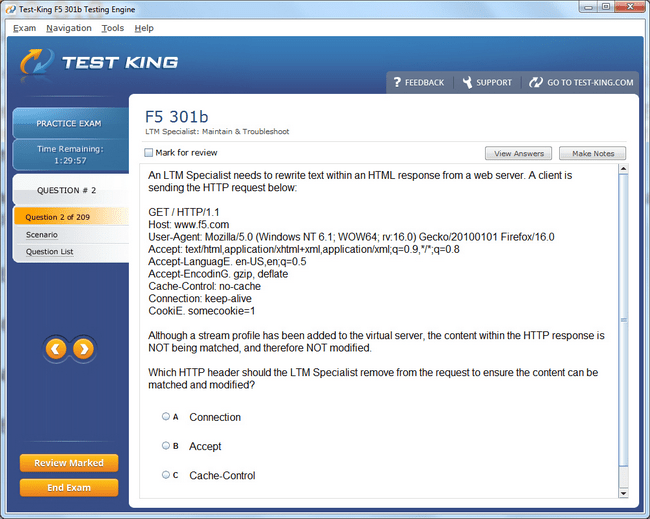
301b Exam Product Screenshots
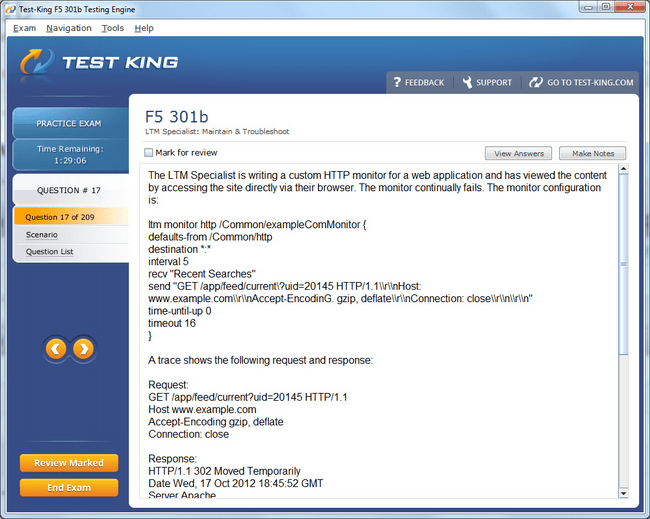
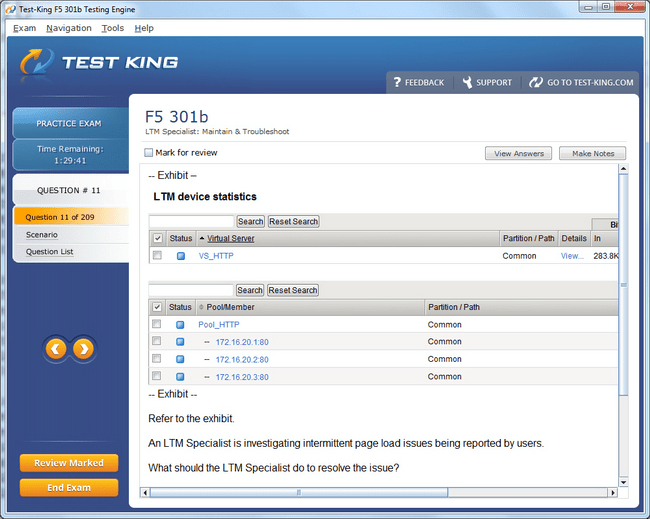
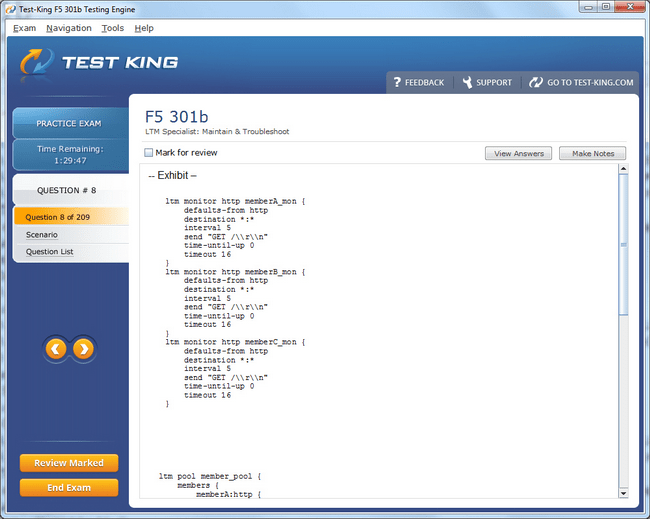
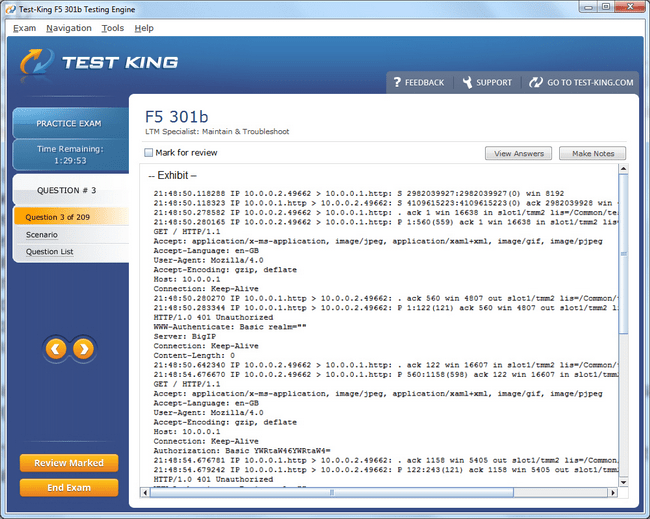
F5-CTS LTM Certification Path: From Beginner to Networking Expert
The F5 Certified Technology Specialist Local Traffic Manager (LTM) credential represents a significant milestone for professionals aspiring to excel in advanced network traffic management. This certification is designed for individuals seeking to deepen their understanding of application delivery networks, load balancing, and security. Earning this certification validates a professional’s ability to configure, manage, and troubleshoot F5 devices and their associated technologies effectively. The credential is recognized globally and serves as a benchmark for those aiming to become experts in the field of traffic management.
Understanding the F5-CTS LTM Certification
The F5-CTS LTM certification covers a broad spectrum of concepts, ranging from fundamental networking principles to intricate configurations of Local Traffic Manager. A candidate embarking on this journey must possess a foundational understanding of TCP/IP, VLANs, routing, and switching. While beginners can attempt this certification, prior exposure to networking concepts accelerates the learning curve and helps in grasping advanced topics more efficiently. The exam evaluates not only theoretical knowledge but also the practical ability to handle real-world traffic management scenarios.
Core Skills and Competencies for LTM Certification
Achieving the F5-CTS LTM certification requires proficiency in several critical areas. At the foundation, a candidate must understand traffic management concepts, including load balancing, SSL offloading, persistence, and content switching. These concepts enable administrators to optimize application performance, enhance reliability, and ensure security across diverse network environments. Knowledge of load balancing algorithms and the ability to implement them based on application requirements is a cornerstone skill.
Additionally, candidates must master configuration and troubleshooting techniques for virtual servers, pools, and nodes. This involves not only creating and managing these objects but also understanding their interactions and dependencies within the broader network ecosystem. An understanding of health monitoring and its role in maintaining high availability is vital. Candidates must be able to configure monitors to detect server health accurately and respond to failures efficiently. Beyond these technical skills, the certification assesses the ability to design scalable and resilient architectures, ensuring that applications remain accessible even under peak loads or during infrastructure failures.
Exam Structure and Preparation Strategies
The examination process for the F5-CTS LTM certification is meticulously designed to evaluate both knowledge and practical skills. Candidates encounter questions that test their understanding of concepts and their ability to apply them to solve real-world problems. The test typically includes scenario-based questions, which challenge individuals to analyze situations and implement solutions using F5 technologies. These scenarios simulate environments where traffic flow, server availability, and application security must be managed dynamically, reflecting the challenges faced by network engineers daily.
Preparation for the exam requires a multi-pronged approach. Self-paced study materials, official F5 documentation, and hands-on lab exercises are indispensable. Candidates benefit from constructing test environments, experimenting with virtual servers, and configuring diverse load balancing methods. Engaging with simulation exercises and mock exams can highlight knowledge gaps and reinforce comprehension. Networking communities and discussion forums provide insights from professionals who have successfully navigated the certification, offering practical tips and nuanced understanding that books alone may not convey.
Real-World Applications of LTM Knowledge
Mastering LTM skills extends beyond exam readiness into practical applications within enterprises and service providers. F5 devices are employed in environments where application availability, security, and performance are paramount. Knowledge of load balancing algorithms allows administrators to direct traffic intelligently, ensuring that server workloads are evenly distributed and response times are optimized. SSL offloading enhances encryption performance, reducing the processing burden on backend servers and improving the overall user experience.
Traffic management knowledge also plays a critical role in mitigating downtime and maintaining service continuity. Administrators who understand persistence and failover mechanisms can implement solutions that seamlessly redirect traffic in the event of server failures, minimizing disruption for end-users. Content switching capabilities allow traffic to be routed based on URL patterns, application types, or other criteria, enabling organizations to implement granular control over network behavior. Security integration, such as employing access policies and inspecting traffic, adds another layer of protection, safeguarding applications against potential threats.
Challenges Faced by Candidates
Despite the structured nature of F5-CTS LTM certification, candidates often encounter several challenges along the path. One common difficulty is grasping the breadth of configurations and understanding the interdependencies among F5 objects. Virtual servers, pools, nodes, and profiles interact in complex ways, and misconfigurations can lead to unexpected traffic behavior. Hands-on practice in a lab environment is crucial to internalizing these relationships and developing confidence in troubleshooting.
Another challenge lies in mastering scenario-based questions that require analytical thinking and application of concepts rather than rote memorization. Candidates must interpret network behavior, anticipate the outcomes of configuration changes, and apply best practices in traffic management. This level of problem-solving requires both theoretical knowledge and practical experience. Candidates may also struggle with time management during the exam, as questions are designed to be challenging and require careful consideration. Developing a methodical approach to analyzing scenarios and implementing solutions helps overcome these obstacles.
Optimizing Career Growth with Certification
Obtaining the F5-CTS LTM certification significantly enhances career prospects within network engineering and IT infrastructure management. Professionals who achieve this credential demonstrate advanced technical expertise, positioning themselves for roles such as network engineer, application delivery specialist, or systems administrator. The certification signals to employers a candidate’s ability to manage complex network environments, optimize application performance, and implement resilient traffic management solutions.
The certification also opens doors to higher-level opportunities within organizations that rely heavily on digital services and cloud infrastructure. As enterprises increasingly depend on robust application delivery networks, the demand for certified professionals grows. Those with F5-CTS LTM credentials often receive recognition for their specialized skills, which can translate into promotions, salary growth, and involvement in strategic projects. Continuous engagement with F5 technologies and staying abreast of updates further enhances professional value, ensuring that knowledge remains relevant in rapidly evolving network environments.
Integrating LTM Knowledge into Practical Scenarios
Implementing LTM knowledge in practical scenarios requires a comprehensive understanding of network architecture, server behavior, and application demands. Administrators often begin by analyzing traffic patterns and determining the appropriate load balancing algorithms for specific applications. The selection process involves assessing factors such as session persistence, server capacity, and response times. Once configured, monitoring the performance and health of servers becomes a continuous task, with adjustments made as necessary to maintain optimal efficiency.
Security considerations are equally integral to traffic management. Administrators must integrate access control policies, monitor for anomalies, and configure secure protocols to protect sensitive information. Advanced scenarios may involve integrating LTM with other F5 modules or third-party solutions, enabling complex application delivery strategies. Knowledge of scripting and automation tools can also streamline routine tasks, reduce configuration errors, and ensure consistent application of best practices across multiple devices.
Continuous Learning and Skill Enhancement
While obtaining the certification marks a notable achievement, continuous learning is essential for maintaining expertise. F5 technologies evolve rapidly, introducing new features and capabilities that professionals must master. Engaging in ongoing training, attending workshops, and participating in professional forums helps keep skills current. Networking with peers provides opportunities to discuss challenges, share solutions, and explore innovative approaches to traffic management.
Practical experience in diverse environments enhances learning beyond theoretical knowledge. Working on projects that involve high-traffic applications, cloud integration, or global server load balancing develops a deeper understanding of network dynamics. This experience cultivates problem-solving skills, enabling administrators to anticipate potential issues and implement proactive measures. By combining certification knowledge with hands-on expertise, professionals solidify their position as trusted experts in application delivery and traffic management.
Delving Deeper into Load Balancing and Traffic Optimization
Achieving mastery in Local Traffic Manager requires more than basic knowledge; it demands an intricate understanding of how traffic flows across networks and how to manipulate that flow to maximize efficiency and reliability. Load balancing is not merely a mechanism to distribute traffic, but a nuanced strategy to ensure optimal resource utilization, minimize latency, and prevent server saturation. The F5-CTS LTM certification emphasizes these principles, equipping professionals to deploy highly available and resilient application delivery infrastructures.
A critical component of traffic optimization is understanding the diverse algorithms available for load balancing. Round-robin, ratio-based, and least connections are commonly used, but the choice of algorithm must be tailored to the characteristics of the application and its users. Round-robin may suffice for evenly matched servers, yet applications with varying workloads require dynamic algorithms that account for server capacity and response times. The ability to interpret traffic analytics and implement adaptive strategies distinguishes proficient administrators from those who rely solely on theoretical knowledge.
Beyond algorithm selection, administrators must consider session persistence, also known as sticky sessions, which ensures that a user continues interacting with the same server throughout a session. This is crucial for applications requiring continuous state information, such as online banking or e-commerce platforms. Understanding persistence profiles and their appropriate deployment under various traffic scenarios is central to delivering consistent user experiences. Additionally, the intricacies of cookie-based persistence versus source IP persistence must be appreciated, as each carries unique operational implications.
Virtual Servers, Pools, and Nodes: Practical Implementation
At the heart of LTM expertise lies the ability to manage virtual servers, pools, and nodes. Virtual servers act as the interface between users and backend resources, receiving requests and directing them according to predefined rules. Pools are collections of nodes, which represent individual servers, and administrators must configure them to ensure equitable traffic distribution and high availability. Monitoring the health of each node through active and passive methods enables the system to respond to failures proactively, redirecting traffic and maintaining uninterrupted service.
Configuring these elements requires attention to detail, as misconfigurations can introduce latency, cause application failures, or expose vulnerabilities. Administrators must understand the interplay between virtual servers, pools, and nodes, recognizing how changes in one component affect overall performance. Advanced scenarios may involve multiple pools supporting the same application or virtual servers serving as intermediaries for complex content routing. Expertise in these configurations not only facilitates efficient traffic management but also provides the foundation for troubleshooting complex issues.
Health monitoring is an indispensable aspect of ensuring service reliability. Administrators employ diverse methods to assess server availability, response time, and application integrity. Simple ICMP or TCP monitors detect basic availability, while HTTP and HTTPS monitors evaluate application responsiveness and content validity. The ability to interpret monitor results and adjust configurations accordingly is a hallmark of an experienced practitioner. This proactive approach minimizes downtime, enhances user satisfaction, and optimizes the utilization of backend resources.
SSL Offloading and Security Integration
Security remains a core concern in traffic management, and SSL offloading is a critical technique for optimizing encrypted traffic handling. By terminating SSL connections at the LTM device, administrators relieve backend servers from the computational overhead of encryption and decryption. This not only accelerates application performance but also centralizes security management, allowing for consistent implementation of encryption standards and certificate management.
Understanding the nuances of SSL profiles, cipher selection, and protocol enforcement is essential. Misconfigured SSL settings can lead to vulnerabilities, degraded performance, or failed connections. Administrators must also integrate access control mechanisms and inspect traffic for anomalies, ensuring that applications remain secure from malicious activities. The ability to harmonize performance optimization with stringent security measures exemplifies the depth of expertise required for F5-CTS LTM certification.
Furthermore, integrating security into traffic management involves leveraging the LTM’s capabilities to implement rate limiting, traffic shaping, and filtering based on application or user behavior. These mechanisms allow administrators to mitigate denial-of-service attacks, prevent abuse, and enforce policies that maintain service quality. A thorough understanding of security implications in conjunction with traffic flow dynamics is indispensable for professionals aiming to deliver robust and resilient network services.
Content Switching and Application Delivery Strategies
Content switching extends the functionality of LTM beyond basic load balancing. By directing traffic based on URLs, host headers, or content types, administrators gain granular control over user requests. This capability enables tailored application delivery strategies, such as routing mobile users to optimized servers, directing requests for static content to caching nodes, or applying specialized security policies based on request characteristics.
Implementing content switching effectively requires careful planning and testing. Administrators must define rules that align with business objectives while minimizing latency and resource contention. Misconfigured content switching rules can lead to service interruptions or unintended traffic routing, emphasizing the importance of meticulous design and validation. The strategic application of these capabilities enhances user experience, supports complex application architectures, and enables scalable service delivery.
Integrating content switching with other LTM features, such as persistence and SSL offloading, further enhances the versatility of traffic management solutions. For instance, routing users based on content while maintaining session integrity ensures consistent user experiences. Similarly, combining SSL offloading with content switching allows administrators to inspect encrypted traffic for application-level routing decisions without compromising performance or security.
Troubleshooting and Performance Optimization
Proficiency in traffic management is incomplete without the ability to troubleshoot effectively. Administrators must diagnose issues ranging from misrouted requests to degraded application performance. Troubleshooting begins with understanding network topology, analyzing traffic flows, and interpreting monitor results. It involves identifying anomalies, correlating events, and systematically applying corrective measures to restore optimal service.
Performance optimization encompasses multiple dimensions. Administrators analyze server response times, network latency, and application behavior to fine-tune configurations. Adjusting load balancing algorithms, optimizing persistence settings, and refining content switching rules contribute to enhanced efficiency. Continuous monitoring and iterative improvements ensure that applications remain responsive under variable loads, providing users with reliable and seamless access.
Real-world troubleshooting often requires innovative thinking, as complex deployments may involve multiple interdependent systems, cloud integrations, and third-party services. Administrators must consider factors such as DNS resolution, backend server capacity, and client behavior in diagnosing problems. The combination of analytical skills, technical knowledge, and practical experience distinguishes accomplished professionals capable of resolving intricate network challenges.
Advanced Deployment Considerations
Advanced deployment scenarios for LTM involve integration with multi-site environments, high availability clusters, and global server load balancing. Administrators design architectures that accommodate redundancy, failover, and disaster recovery, ensuring continuous service delivery even under adverse conditions. The interplay between local traffic management and broader network strategies requires comprehensive planning and meticulous execution.
Scalability considerations are paramount in large-scale environments. Administrators anticipate traffic growth, plan for incremental capacity, and deploy strategies to distribute load across multiple nodes and data centers. Leveraging automation and orchestration tools facilitates consistent configuration, reduces errors, and streamlines operational workflows. Understanding how LTM integrates with broader IT infrastructure and cloud platforms enables administrators to implement sophisticated application delivery solutions that meet evolving business demands.
Training and hands-on experience remain essential for mastering advanced deployments. Engaging with complex lab environments, simulating failover scenarios, and experimenting with diverse traffic patterns cultivate expertise. Professionals who invest in continuous learning and practical application are well-equipped to address the challenges of modern enterprise networks, maintain service reliability, and optimize application performance.
Leveraging Analytics and Reporting
Effective traffic management extends beyond configuration and monitoring to encompass analytics and reporting. Administrators utilize metrics on server utilization, request patterns, and application performance to inform decisions. Detailed analysis of traffic trends enables predictive adjustments, capacity planning, and identification of potential bottlenecks before they impact users.
Reporting capabilities provide insights into user behavior, security incidents, and resource allocation. Administrators can generate reports that highlight anomalies, measure adherence to service-level agreements, and support operational audits. The integration of analytics into traffic management empowers organizations to make data-driven decisions, optimize infrastructure investment, and deliver superior application experiences.
Continuous Skill Refinement
Achieving expertise in Local Traffic Manager is an ongoing process. As application architectures evolve, cloud adoption accelerates, and network demands intensify, administrators must continually refine their skills. Engaging in advanced courses, participating in professional forums, and experimenting with emerging features ensures that knowledge remains current. Hands-on experience with diverse deployments consolidates theoretical understanding, allowing professionals to anticipate challenges, innovate solutions, and implement best practices effectively.
By cultivating a mindset of continuous improvement, administrators not only maintain their proficiency but also enhance their value within organizations. Mastery of advanced traffic management techniques, combined with strategic problem-solving capabilities, positions professionals as indispensable contributors to enterprise IT success.
Mastering Complex Configurations and Troubleshooting Techniques
Reaching an advanced level in Local Traffic Manager requires deep familiarity with the architecture of F5 devices and the ability to configure complex traffic management scenarios. The F5-CTS LTM certification emphasizes practical knowledge alongside theoretical comprehension, preparing professionals to navigate intricate deployments. Administrators must manage virtual servers, pools, nodes, and profiles with precision, understanding not only their individual functions but also their interdependencies and the impact of changes on overall network behavior.
Advanced configuration involves creating multi-tiered virtual servers that interact with numerous pools and nodes. Each node may represent a server with unique characteristics, capacity, and application requirements. Administrators must design these configurations to balance load efficiently, maintain high availability, and provide seamless user experiences. Fine-tuning parameters such as connection limits, timeouts, and health monitors ensures that servers handle traffic appropriately, avoiding bottlenecks and preventing service degradation under peak loads.
Health monitoring extends beyond simple availability checks. Administrators utilize active and passive monitors to assess server responsiveness, content accuracy, and application behavior. Active monitoring probes servers at regular intervals, evaluating performance and detecting potential issues before they impact users. Passive monitoring observes real-time traffic to identify anomalies, failures, or latency spikes. Understanding when to use each type and how to interpret their results is fundamental to maintaining resilient and high-performing networks.
Traffic Manipulation and Optimization Strategies
The ability to manipulate traffic intelligently distinguishes seasoned administrators from beginners. Load balancing algorithms must be selected based on application type, user behavior, and server performance. Round-robin, least connections, and ratio-based algorithms provide basic distribution, while advanced scenarios may require dynamic load balancing that accounts for server load, response time, and custom metrics. Administrators analyze traffic patterns to anticipate peaks, distribute requests evenly, and prevent individual nodes from becoming overwhelmed.
Persistence management ensures that users maintain consistent sessions with the same backend server when required. Cookie-based persistence, source IP persistence, and SSL session persistence offer diverse approaches depending on the application’s requirements. Misconfigured persistence can lead to user frustration, inconsistent data handling, or degraded application performance. Administrators must evaluate the nature of the application, traffic volume, and backend architecture to determine the most suitable persistence method.
Content switching enhances flexibility in traffic management by directing requests based on URLs, host headers, or other content attributes. This allows administrators to deploy differentiated policies for mobile users, regional traffic, or specialized applications. Strategic content switching improves user experience, optimizes server utilization, and supports complex application architectures. It also facilitates integration with security policies, ensuring that traffic is inspected and filtered according to predefined rules.
SSL Offloading and Secure Traffic Handling
Handling encrypted traffic efficiently is a critical component of advanced LTM management. SSL offloading enables administrators to terminate SSL connections at the LTM device, relieving backend servers from the computational burden of encryption and decryption. This approach enhances performance while centralizing certificate management and enforcing consistent security protocols across applications.
Administrators must configure SSL profiles meticulously, selecting appropriate ciphers, protocols, and encryption standards. Misconfigurations can expose vulnerabilities, disrupt client connections, or impair performance. Additionally, integrating SSL offloading with traffic management features such as content switching, persistence, and load balancing ensures that encrypted traffic is processed seamlessly while maintaining security. Understanding the interaction between encryption, performance, and application requirements is vital for delivering robust, secure services.
Access control and traffic inspection complement SSL offloading by enforcing security policies at the edge. Administrators implement rate limiting, filtering, and anomaly detection to prevent attacks and unauthorized access. These measures safeguard applications without compromising performance, illustrating the nuanced balance between security and efficiency that advanced LTM expertise demands.
Troubleshooting Complex Network Scenarios
Effective troubleshooting requires analytical thinking and practical experience. Administrators often face scenarios where multiple interdependent systems, cloud integrations, and dynamic traffic patterns introduce unforeseen issues. Diagnosing problems involves interpreting monitor results, analyzing traffic flows, and correlating server behavior with application performance. Systematic approaches, combined with deep knowledge of LTM components, enable rapid identification and resolution of issues.
Common troubleshooting challenges include misrouted traffic, persistence failures, SSL handshake errors, and performance bottlenecks. Administrators address these by verifying configurations, assessing health monitor outcomes, and examining load balancing rules. Advanced troubleshooting may also require evaluating the interactions between content switching, security policies, and backend server behavior. The ability to anticipate potential failures and implement proactive measures minimizes downtime and maintains service reliability.
Performance optimization is closely tied to troubleshooting. Administrators monitor response times, server utilization, and traffic patterns, adjusting configurations to improve efficiency. This includes refining load balancing algorithms, optimizing persistence settings, and tuning content switching rules. Continuous observation and iterative improvement ensure that applications remain responsive under varying traffic conditions, supporting superior user experiences.
Multi-Site Deployments and High Availability
Advanced LTM configurations often extend to multi-site environments, where high availability and disaster recovery are paramount. Administrators design architectures that accommodate redundancy, failover, and geographic distribution. Virtual servers, pools, and nodes are deployed across multiple locations to ensure uninterrupted service even during hardware failures, network outages, or maintenance activities.
Global server load balancing complements local traffic management by distributing traffic across data centers based on performance, availability, and proximity. This approach reduces latency, enhances resilience, and improves application performance for geographically dispersed users. Administrators integrate local and global traffic strategies to create comprehensive, scalable architectures that meet enterprise demands.
High availability configurations include active-active and active-standby deployments, each with specific design considerations. Administrators must plan for failover sequences, synchronization of configuration data, and health check dependencies to ensure seamless service continuity. Understanding these concepts and implementing them effectively is a defining characteristic of advanced LTM professionals.
Analytics, Reporting, and Capacity Planning
Advanced traffic management extends to analytics and reporting, which provide insights into server utilization, request patterns, and application performance. Administrators leverage these insights to anticipate traffic growth, identify potential bottlenecks, and plan for resource expansion. Detailed reporting on traffic trends, security events, and system performance supports informed decision-making and operational audits.
Capacity planning is an essential aspect of advanced deployments. Administrators evaluate server capabilities, network bandwidth, and application requirements to forecast growth and allocate resources efficiently. This proactive approach prevents service degradation, optimizes investment in infrastructure, and ensures that applications remain accessible and responsive under varying loads.
Real-time monitoring complements analytics by providing immediate visibility into network performance. Administrators can detect anomalies, respond to failures, and adjust configurations dynamically. The integration of monitoring, reporting, and predictive analysis empowers organizations to maintain high-performing, resilient networks while adapting to evolving demands.
Automation and Orchestration in Traffic Management
Automation and orchestration are increasingly important in sophisticated LTM environments. Administrators leverage scripts, templates, and orchestration tools to streamline configuration, reduce errors, and enforce consistency across multiple devices. Automated workflows facilitate routine tasks, such as deploying virtual servers, updating SSL certificates, and applying security policies, freeing administrators to focus on strategic initiatives.
Orchestration enables coordinated management of complex deployments, particularly in environments with multi-site architectures or cloud integration. Administrators define policies that guide traffic distribution, failover behavior, and application delivery, ensuring that the network adapts seamlessly to changing conditions. Mastery of automation and orchestration enhances operational efficiency, reduces human error, and supports scalable, resilient infrastructures.
Continuous Learning and Professional Development
Even after mastering advanced configurations and troubleshooting techniques, continuous learning remains essential. F5 technologies evolve rapidly, introducing new features, protocols, and best practices. Professionals maintain their expertise by engaging with updated documentation, attending training workshops, participating in forums, and experimenting with emerging features in lab environments.
Hands-on experience reinforces theoretical understanding, enabling administrators to anticipate challenges and innovate solutions. Exposure to diverse deployment scenarios, including cloud integration, high-traffic applications, and global infrastructures, cultivates a nuanced understanding of traffic behavior. Continuous skill enhancement ensures that professionals remain competitive, capable of delivering resilient, high-performing application delivery networks.
Mastering Performance Monitoring and Proactive Traffic Management
Achieving expert-level proficiency in Local Traffic Manager requires not only understanding configurations but also mastering performance monitoring and proactive traffic management. The F5-CTS LTM certification emphasizes these abilities, preparing administrators to anticipate potential issues, optimize application delivery, and maintain uninterrupted service across complex network infrastructures. Monitoring is not merely an operational task but a strategic function that informs configuration decisions, capacity planning, and security measures.
Administrators employ a variety of monitoring techniques to evaluate server health, application responsiveness, and network efficiency. Active monitors probe servers at defined intervals, assessing the availability and performance of applications. These probes may include checks for protocol-specific responses, content validation, or complex scripted interactions. Passive monitoring observes actual traffic flows in real time, providing insights into user behavior, latency, and anomalies that may not be evident through synthetic tests. Combining active and passive monitoring creates a comprehensive view of the environment, enabling proactive management.
Understanding thresholds and response patterns is crucial for effective monitoring. Administrators must define acceptable performance parameters, identify early warning signs of degradation, and configure alerts that trigger before users experience disruption. For example, elevated response times or intermittent packet loss may indicate backend server overload, network congestion, or configuration errors. By interpreting these signals accurately, administrators can adjust load balancing strategies, refine persistence methods, and reallocate resources dynamically to maintain optimal service levels.
Traffic Analysis and Optimization Strategies
Traffic analysis is a cornerstone of advanced LTM expertise. Administrators scrutinize traffic patterns to understand peak loads, regional distribution, and application-specific behavior. This analysis informs load balancing decisions, content switching rules, and high availability strategies. For instance, identifying high-volume requests for static content may suggest routing them to dedicated caching nodes, while latency-sensitive applications may require prioritization to specific servers with lower response times.
Optimization extends to all facets of traffic management. Load balancing algorithms must be evaluated continually to ensure they match evolving application and server conditions. Least connections, ratio-based, and dynamic load balancing approaches may be employed depending on server performance metrics and traffic distribution. Administrators refine persistence profiles to maintain session continuity without overloading individual nodes, adjusting cookie-based or source IP persistence settings to accommodate unique application behaviors.
Content switching enhances optimization by directing traffic based on application-specific criteria. Administrators may configure rules that route mobile traffic to lightweight servers, prioritize secure connections for sensitive applications, or separate internal and external requests for regulatory compliance. The strategic combination of load balancing, persistence, and content switching ensures that applications perform efficiently under variable demand, delivering seamless experiences for users while preserving backend stability.
Advanced SSL Offloading and Secure Traffic Practices
SSL offloading remains a critical component of performance enhancement. Terminating encrypted traffic at the LTM device reduces computational load on backend servers, accelerating response times and enabling centralized security control. Administrators must configure SSL profiles carefully, selecting appropriate ciphers, protocols, and certificate management strategies to balance security and performance.
Beyond offloading, secure traffic practices involve integrating inspection, rate limiting, and anomaly detection. Administrators may analyze traffic for irregular patterns indicative of potential attacks, unauthorized access, or misconfigurations. By combining SSL offloading with intelligent security policies, LTM devices can provide robust protection while ensuring high-performance traffic management. Understanding the delicate equilibrium between encryption overhead, user experience, and application availability is essential for advanced practitioners.
The ability to inspect encrypted traffic without compromising performance involves careful orchestration of SSL profiles, content inspection, and monitoring strategies. Administrators leverage these capabilities to enforce compliance, detect intrusions, and optimize traffic flow simultaneously. Security integration in performance management exemplifies the multifaceted responsibilities of professionals pursuing F5-CTS LTM certification.
Health Monitoring and Resiliency Planning
Health monitoring is fundamental to proactive traffic management. Administrators implement comprehensive monitoring for nodes, pools, and virtual servers, ensuring early detection of failures, latency spikes, or misconfigurations. Monitors may include ICMP checks, protocol-specific probes, or content validation to assess application responsiveness. Accurate interpretation of these results guides traffic redirection, server reallocation, and configuration adjustments, minimizing service disruption.
Resiliency planning complements monitoring by ensuring that traffic can be rerouted seamlessly during failures. Administrators design architectures that support high availability through redundant nodes, active-standby configurations, and failover strategies. Anticipating potential points of failure, whether hardware, software, or network-based, allows administrators to implement proactive measures that preserve uptime. Multi-site deployments and global server load balancing enhance resiliency by distributing traffic geographically, reducing latency, and ensuring uninterrupted service in the event of localized disruptions.
Capacity planning is closely tied to monitoring and resiliency. Administrators analyze historical traffic patterns, peak load trends, and resource utilization to forecast growth and allocate resources efficiently. This proactive approach prevents bottlenecks, ensures consistent application performance, and supports scaling strategies in dynamic environments. By integrating monitoring insights into capacity planning, professionals create a predictive framework that aligns with business requirements and user expectations.
Proactive Troubleshooting and Performance Tuning
Troubleshooting in advanced LTM environments is a proactive, rather than reactive, endeavor. Administrators examine traffic flows, monitor results, and performance metrics to identify potential inefficiencies before they manifest as user-facing issues. Advanced troubleshooting may involve examining interdependencies among virtual servers, pools, nodes, and content switching rules to pinpoint causes of latency, packet loss, or server overload.
Performance tuning extends beyond resolving failures to optimizing application delivery. Administrators refine load balancing algorithms, persistence settings, and SSL offloading configurations based on observed traffic behavior and performance analytics. Fine-tuning server selection, request routing, and session management enhances overall efficiency, reduces response times, and improves user satisfaction. Iterative tuning, guided by comprehensive monitoring and traffic analysis, ensures that applications maintain peak performance under varying demand conditions.
In complex deployments, troubleshooting may require cross-layer analysis, including network infrastructure, application behavior, and backend server performance. Administrators evaluate traffic distribution, monitor correlations, and adjust configurations dynamically. The ability to anticipate issues, implement preemptive adjustments, and validate outcomes distinguishes advanced practitioners from those limited to reactive problem-solving.
Integrating Analytics and Reporting into Decision-Making
Analytics and reporting play a pivotal role in performance enhancement and traffic management. Administrators analyze metrics on request volume, server utilization, latency, and application responsiveness to make informed decisions about configuration adjustments and resource allocation. These insights facilitate predictive capacity planning, optimize load balancing strategies, and support high availability architectures.
Reporting also provides visibility into user behavior, application performance, and security events. Administrators generate detailed insights that inform strategic decisions, operational improvements, and compliance audits. For example, identifying traffic surges during specific hours may lead to reallocation of resources or adjustment of load balancing priorities. Observing anomalous patterns can trigger security reviews or infrastructure assessments. By integrating analytics into daily operations, administrators create a data-driven approach to traffic management that enhances performance, reliability, and security simultaneously.
Automation, Orchestration, and Efficiency Gains
Automation and orchestration are integral to advanced performance management. Administrators employ scripts, templates, and automated workflows to standardize configurations, apply security policies, and update SSL certificates across multiple devices efficiently. These tools reduce human error, ensure consistency, and allow professionals to focus on strategic optimization rather than repetitive tasks.
Orchestration enables coordinated management of complex environments, particularly those with multi-site deployments, high availability clusters, or cloud integration. Administrators define policies that govern traffic distribution, failover behavior, and resource allocation dynamically. Automated orchestration ensures that changes propagate seamlessly, configurations remain synchronized, and performance objectives are consistently met. Mastery of these tools enhances operational efficiency, reduces risk, and supports scalable, resilient infrastructures capable of meeting evolving business demands.
Continuous Skill Development and Advanced Learning
Even with mastery of monitoring, optimization, and proactive management, continuous learning is essential for staying ahead in Local Traffic Manager expertise. F5 technologies evolve rapidly, introducing new capabilities, protocols, and performance features. Professionals maintain relevance by engaging in updated training materials, experimenting in lab environments, and participating in peer forums to share insights and experiences.
Hands-on practice with advanced deployments, high-traffic applications, and multi-site architectures reinforces theoretical knowledge. Professionals develop intuition for traffic behavior, recognize subtle signs of potential issues, and implement innovative solutions that optimize performance and reliability. Continuous skill development ensures that administrators not only maintain their proficiency but also enhance their value as trusted experts in traffic management and application delivery.
Implementing Scalable Architectures and Advanced Automation
Achieving mastery in Local Traffic Manager encompasses not only configuration and performance optimization but also designing scalable architectures that accommodate evolving business requirements. The F5-CTS LTM certification emphasizes skills necessary to deploy and manage application delivery networks that handle increasing traffic volumes, distributed infrastructures, and dynamic application demands. Scalability involves both vertical enhancements, such as upgrading server capabilities, and horizontal expansion, including the addition of new nodes or sites to maintain service reliability under peak loads.
Administrators must understand the nuances of virtual servers, pools, and nodes in the context of scalability. Efficient distribution of traffic across multiple nodes ensures that no single server becomes a performance bottleneck. Fine-tuning load balancing algorithms according to traffic patterns and application behavior is essential for preserving response times and user experience. The selection of algorithms, including ratio-based, least connections, and dynamic load balancing methods, must consider backend server capabilities, application sensitivity, and anticipated growth trajectories.
Persistence management plays a critical role in scalable deployments. Administrators implement session persistence mechanisms that guarantee user sessions remain consistent, even as traffic is distributed across numerous nodes or sites. Cookie-based persistence, source IP persistence, and SSL session persistence each offer distinct advantages depending on the application’s architecture and user behavior. Understanding the operational implications of these methods ensures seamless user experiences while preventing overutilization of specific resources.
Automation is a cornerstone of managing scalable environments efficiently. Administrators employ orchestration tools, scripting, and templates to standardize configuration deployment across multiple devices and locations. Automated workflows facilitate repetitive tasks, such as provisioning virtual servers, updating SSL certificates, or applying security policies consistently. By reducing human intervention, administrators minimize errors, enforce uniform standards, and accelerate deployment timelines, which is particularly valuable in multi-site and high-volume environments.
Integrating LTM with Enterprise Applications and Cloud Infrastructures
Integration with enterprise applications and cloud platforms extends the utility of LTM beyond traditional load balancing. Administrators leverage LTM capabilities to enhance application performance, ensure high availability, and provide secure access to distributed services. Traffic management strategies are adapted to accommodate cloud-native architectures, hybrid environments, and multi-data center deployments.
In cloud-integrated environments, administrators must account for elasticity, dynamic resource allocation, and variable traffic patterns. Load balancing decisions are influenced by cloud resource availability, network latency, and application requirements. Integrating LTM with cloud orchestration platforms enables dynamic adjustment of virtual servers, pools, and nodes, ensuring that traffic is directed efficiently even as cloud resources scale automatically. This integration provides continuity, enhances user experience, and allows enterprises to leverage cloud agility without compromising application performance or security.
Enterprise applications often require sophisticated traffic policies, including content switching, SSL offloading, and access control. Administrators configure rules that route requests based on URLs, host headers, or content types, allowing applications to scale efficiently while maintaining compliance with internal or regulatory policies. Secure traffic handling is critical in these scenarios, ensuring that sensitive data is protected without introducing latency or operational complexity. The combination of performance, scalability, and security is essential for maintaining enterprise-grade application delivery.
Advanced Traffic Analytics and Predictive Resource Management
Advanced traffic analytics empowers administrators to anticipate load spikes, identify performance bottlenecks, and optimize resource allocation proactively. LTM devices provide detailed metrics on request volumes, response times, server utilization, and traffic distribution. Administrators analyze these metrics to make informed decisions regarding load balancing strategies, persistence configuration, and resource expansion.
Predictive resource management relies on historical traffic data and real-time monitoring to forecast future demands. By identifying trends and usage patterns, administrators can provision additional nodes, adjust load balancing priorities, and implement content switching rules to accommodate anticipated traffic. This proactive approach prevents service degradation during peak periods and ensures that users experience consistent performance, even under fluctuating conditions.
Analytics also supports troubleshooting by correlating performance anomalies with specific configuration changes, network events, or application behavior. Administrators can pinpoint the root cause of latency, server failures, or security incidents, enabling rapid resolution and preventing recurrence. Integrating predictive insights into traffic management strategies strengthens resilience and enhances operational efficiency across complex enterprise environments.
Security Integration in Scalable and Automated Deployments
Security remains an integral component of advanced LTM deployments. Administrators implement SSL offloading to optimize encrypted traffic while centralizing certificate management. Careful configuration of SSL profiles, including ciphers, protocols, and encryption standards, ensures that traffic remains secure without compromising performance. Misconfigurations can expose vulnerabilities, degrade service, or prevent client connections, making meticulous attention to detail essential.
In scalable and automated environments, security integration extends to traffic inspection, anomaly detection, and access control. Administrators configure rate limiting, filtering, and authentication policies to protect applications from malicious activity or unauthorized access. Automation ensures that security policies are consistently applied across multiple nodes, virtual servers, and sites, maintaining compliance and reducing administrative overhead. The ability to harmonize security, performance, and scalability reflects the depth of expertise required for F5-CTS LTM certification.
Content switching and persistence policies further contribute to secure traffic handling. Administrators may route sensitive requests to dedicated nodes or apply enhanced security measures based on URL patterns, headers, or client characteristics. These strategies enable granular control over traffic while preserving performance, demonstrating the multifaceted nature of traffic management in enterprise environments.
High Availability and Disaster Recovery Strategies
Ensuring high availability is paramount in enterprise traffic management. Administrators design architectures that incorporate redundancy, failover mechanisms, and multi-site deployments to maintain continuous service during failures. Active-active and active-standby configurations are deployed based on business requirements, traffic patterns, and risk tolerance.
Failover mechanisms must be meticulously configured to prevent service disruption. Administrators synchronize configurations across devices, monitor node and pool health, and implement intelligent routing to maintain application availability. Disaster recovery planning involves replicating critical traffic management configurations across sites, establishing failover priorities, and conducting regular validation exercises. Integrating high availability with predictive analytics and automation ensures that the environment adapts dynamically to failures, sustaining performance and reliability.
Global server load balancing enhances resiliency by distributing traffic across geographically dispersed sites. Administrators consider proximity, server health, and performance metrics to direct users to the optimal location. This approach reduces latency, supports business continuity, and ensures that high-demand applications remain accessible even in the event of localized disruptions. The combination of local traffic management and global strategies represents the pinnacle of scalable, resilient application delivery expertise.
Performance Optimization through Advanced Load Balancing Techniques
Optimizing application performance in large-scale environments requires nuanced understanding of load balancing methodologies. Administrators must evaluate multiple algorithms, adjusting them according to server capacity, traffic characteristics, and application requirements. Dynamic load balancing, which considers real-time server metrics, enables intelligent distribution that prevents bottlenecks and maintains responsiveness.
Persistence strategies complement load balancing by preserving session integrity and ensuring that users continue interacting with the same backend server when necessary. Cookie persistence, source IP persistence, and SSL session persistence provide flexibility to accommodate diverse applications, including stateful and transactional systems. Correct implementation of these techniques enhances user experience and prevents service degradation under variable load conditions.
Content switching further refines traffic delivery, enabling administrators to route requests based on application-specific criteria, user attributes, or regional considerations. This capability allows fine-grained control over traffic flow, improves resource utilization, and supports differentiated service levels for diverse user groups. Integrating content switching with load balancing and persistence provides a cohesive strategy for maximizing performance in complex, high-traffic environments.
Continuous Learning and Professional Growth
Even after mastering scalable architectures, automation, and enterprise integration, continuous learning remains essential for maintaining expertise. F5 technologies evolve rapidly, introducing new features, protocols, and capabilities. Professionals engage with updated training materials, explore emerging best practices, and participate in peer forums to refine their skills and remain current with industry developments.
Hands-on experimentation with multi-site deployments, high-traffic applications, and cloud-integrated environments reinforces theoretical knowledge and cultivates practical intuition. Professionals who invest in ongoing learning develop the ability to anticipate challenges, implement innovative solutions, and deliver resilient, high-performing networks. Continuous growth ensures that administrators maintain their value as trusted experts in application delivery, traffic management, and enterprise network optimization.
Achieving Mastery in Local Traffic Management
Attaining mastery in Local Traffic Manager is a culmination of extensive knowledge, practical experience, and the ability to integrate advanced strategies across complex network environments. The F5-CTS LTM certification provides the foundation for professionals to demonstrate expertise in configuring, managing, and optimizing application delivery networks while ensuring security, performance, and high availability. Mastery involves understanding the interplay of virtual servers, pools, nodes, and profiles in dynamic traffic scenarios, along with the ability to troubleshoot and optimize these configurations effectively.
Advanced administrators analyze traffic patterns, evaluate server capacity, and implement load balancing algorithms that accommodate fluctuating user demand. The choice of algorithms—whether round-robin, least connections, ratio-based, or dynamic—must align with application requirements, backend infrastructure, and anticipated growth. Understanding the operational nuances of each algorithm, along with the effects on persistence and session continuity, is essential for delivering consistent user experiences.
Persistence mechanisms ensure that users maintain uninterrupted sessions with the same backend server when required. Cookie-based persistence, source IP persistence, and SSL session persistence each offer distinct advantages depending on the application’s architecture and traffic characteristics. Effective implementation requires careful planning, testing, and continuous monitoring to ensure that session continuity does not negatively impact performance or server utilization.
Advanced Traffic Optimization Techniques
Optimizing application delivery encompasses a spectrum of techniques that extend beyond traditional load balancing. Administrators leverage content switching to route traffic based on URLs, host headers, or request attributes, providing granular control over how applications handle requests. Content switching enables differentiated policies for mobile users, regional traffic, or specialized applications, enhancing both performance and security.
SSL offloading remains integral to performance optimization. Terminating encrypted traffic at the LTM device reduces the computational load on backend servers, accelerates response times, and centralizes certificate management. Administrators must configure SSL profiles carefully, selecting appropriate ciphers, protocols, and encryption standards to safeguard traffic without compromising application performance. Integrating SSL offloading with persistence and content switching ensures that encrypted traffic is processed efficiently while maintaining seamless user experiences.
Health monitoring is another critical component of advanced traffic optimization. Active and passive monitors provide visibility into server health, application responsiveness, and network stability. Active monitors periodically probe servers to detect failures, while passive monitoring observes real-time traffic for anomalies or performance degradation. Interpreting monitor results and adjusting configurations proactively prevents service disruption, maintains reliability, and enhances overall network efficiency.
Troubleshooting Complex Deployment Scenarios
Troubleshooting advanced LTM deployments requires analytical thinking, technical expertise, and hands-on experience. Administrators encounter scenarios where multiple interdependent systems, multi-site deployments, and dynamic traffic flows introduce potential issues. Effective troubleshooting involves examining traffic patterns, monitor results, configuration dependencies, and backend server behavior to identify root causes.
Common challenges include misrouted traffic, SSL handshake errors, persistence failures, and latency spikes. Administrators resolve these issues by systematically analyzing virtual servers, pools, nodes, and associated profiles, verifying configurations, and implementing corrective actions. Advanced troubleshooting may also require cross-layer analysis, including network infrastructure, application logic, and external integrations. The ability to diagnose and remediate complex problems swiftly minimizes downtime and sustains high-quality service delivery.
Performance tuning complements troubleshooting by focusing on optimization rather than correction. Administrators refine load balancing algorithms, persistence settings, SSL offloading configurations, and content switching rules to enhance response times and server efficiency. Iterative performance tuning, guided by comprehensive analytics and monitoring insights, ensures that applications remain responsive under fluctuating traffic conditions. This proactive approach demonstrates the depth of expertise that F5-CTS LTM certification represents.
Automation, Orchestration, and Enterprise Integration
Advanced mastery includes the ability to implement automation and orchestration to streamline network management. Administrators leverage scripts, templates, and orchestrated workflows to deploy configurations consistently, update SSL certificates, and apply security policies across multiple devices. Automation reduces human error, enforces uniform standards, and accelerates deployment timelines, particularly in enterprise-scale or multi-site environments.
Orchestration coordinates complex deployments, including high availability clusters, global server load balancing, and hybrid cloud integration. Administrators define policies that dynamically manage traffic distribution, failover behavior, and resource allocation. This approach ensures that networks respond intelligently to failures, traffic surges, or application demands while maintaining performance and security. Integration with enterprise applications and cloud infrastructures allows LTM devices to enhance application delivery across diverse environments, providing agility and scalability without compromising reliability.
Traffic analytics and predictive resource management further reinforce enterprise integration. Administrators leverage historical traffic data and real-time monitoring to forecast demand, optimize load balancing strategies, and allocate resources proactively. Predictive insights prevent bottlenecks, maintain consistent application performance, and support capacity planning initiatives. These practices enable administrators to deliver reliable, high-performing networks even in dynamic or unpredictable conditions.
Security Considerations in Advanced Deployments
Security remains a core focus in sophisticated traffic management. SSL offloading, traffic inspection, access control, and anomaly detection work in tandem to safeguard applications and sensitive data. Administrators configure SSL profiles to enforce encryption standards, integrate access policies, and monitor traffic for malicious activity. Combining performance optimization with security ensures that applications remain fast, reliable, and protected against threats.
In complex deployments, administrators implement granular security strategies by leveraging content switching and persistence policies. Sensitive requests may be routed to dedicated nodes or subjected to enhanced security measures based on traffic characteristics. Rate limiting and traffic shaping protect against denial-of-service attacks or abuse, maintaining service integrity while preserving performance. The ability to balance security, performance, and scalability reflects the advanced competency that F5-CTS LTM certification validates.
High Availability, Disaster Recovery, and Global Traffic Management
High availability is a hallmark of expert LTM deployment. Administrators design resilient architectures using redundancy, failover mechanisms, and multi-site configurations to maintain uninterrupted service. Active-active and active-standby topologies are deployed to ensure continuous application availability, with failover strategies synchronized across virtual servers, pools, and nodes.
Disaster recovery planning complements high availability by replicating configurations across sites, establishing failover priorities, and validating recovery processes. Administrators integrate predictive analytics, monitoring insights, and automated workflows to ensure that failovers occur seamlessly and service disruption is minimized. Global server load balancing further enhances resilience by distributing traffic across geographically dispersed sites, optimizing latency, and supporting business continuity.
Performance optimization in these environments requires sophisticated load balancing strategies, refined persistence, and intelligent content switching. Administrators must evaluate server performance, traffic patterns, and user behavior to make real-time adjustments, ensuring that high-demand applications remain accessible and responsive. The ability to design, implement, and maintain such complex infrastructures demonstrates the advanced expertise associated with F5-CTS LTM certification.
Career Advancement and Professional Impact
Achieving mastery in LTM has a significant impact on career growth and professional recognition. Certified administrators demonstrate the ability to design, deploy, and optimize complex application delivery networks, making them valuable assets to enterprises that rely on high-performance, secure, and resilient IT infrastructure. Roles such as senior network engineer, application delivery specialist, and infrastructure architect become attainable, with opportunities for higher responsibility and strategic involvement.
Organizations increasingly prioritize professionals who can integrate advanced traffic management, automation, security, and cloud integration. The ability to anticipate challenges, implement proactive solutions, and maintain performance under varying conditions positions certified administrators as trusted experts. This recognition often translates into career progression, increased earning potential, and participation in critical projects that shape enterprise IT strategies.
Continuous professional development ensures that knowledge remains current. Administrators engage with emerging F5 technologies, cloud-native application architectures, and advanced traffic management practices to maintain relevance in an evolving industry. Hands-on experience with diverse environments, combined with theoretical mastery, fosters intuition, problem-solving capabilities, and innovative thinking—key attributes for sustaining long-term success.
Conclusion
The journey to mastering Local Traffic Manager through the F5-CTS LTM certification equips professionals with unparalleled expertise in traffic management, application delivery, and network optimization. From foundational configurations to advanced load balancing, SSL offloading, content switching, automation, and high availability, this certification validates the ability to design, deploy, and maintain resilient, high-performing networks.
Administrators develop the skills to anticipate challenges, optimize performance, integrate security, and implement scalable, automated solutions that support enterprise and cloud infrastructures. Mastery of these capabilities not only enhances technical competence but also significantly advances career opportunities, establishing certified professionals as invaluable contributors to organizational success. Continuous learning, hands-on experience, and the application of advanced strategies ensure that F5-CTS LTM-certified administrators remain at the forefront of network engineering, delivering superior performance, reliability, and security in an increasingly complex digital landscape.
Frequently Asked Questions
How can I get the products after purchase?
All products are available for download immediately from your Member's Area. Once you have made the payment, you will be transferred to Member's Area where you can login and download the products you have purchased to your computer.
How long can I use my product? Will it be valid forever?
Test-King products have a validity of 90 days from the date of purchase. This means that any updates to the products, including but not limited to new questions, or updates and changes by our editing team, will be automatically downloaded on to computer to make sure that you get latest exam prep materials during those 90 days.
Can I renew my product if when it's expired?
Yes, when the 90 days of your product validity are over, you have the option of renewing your expired products with a 30% discount. This can be done in your Member's Area.
Please note that you will not be able to use the product after it has expired if you don't renew it.
How often are the questions updated?
We always try to provide the latest pool of questions, Updates in the questions depend on the changes in actual pool of questions by different vendors. As soon as we know about the change in the exam question pool we try our best to update the products as fast as possible.
How many computers I can download Test-King software on?
You can download the Test-King products on the maximum number of 2 (two) computers or devices. If you need to use the software on more than two machines, you can purchase this option separately. Please email support@test-king.com if you need to use more than 5 (five) computers.
What is a PDF Version?
PDF Version is a pdf document of Questions & Answers product. The document file has standart .pdf format, which can be easily read by any pdf reader application like Adobe Acrobat Reader, Foxit Reader, OpenOffice, Google Docs and many others.
Can I purchase PDF Version without the Testing Engine?
PDF Version cannot be purchased separately. It is only available as an add-on to main Question & Answer Testing Engine product.
What operating systems are supported by your Testing Engine software?
Our testing engine is supported by Windows. Andriod and IOS software is currently under development.


