Configuring a VPN Server
Exam: Microsoft 70-649 - TS: Upgrading Your MCSE on Windows Server 2003 to Windows Server 2008, Technology Specialist
External clients that are connected to internet, access to internal networks can be provided by VPN servers. Windows Server 2008 can be configured to act like a VPN server by installation of Network Policy and Access Services server role and selecting Routing and Remote Access Services and Remote Access Service role services.
Windows Server 2008 can act both like a VPN server and a dial-up server at the same time. In most of the deployments have it acting one or the other role. For configuring Windows Server 2008 to perform functions like a VPN server, the following steps need to be followed:
- The first step is to run the Routing And Remote Access Server Setup Wizard. The wizard is in the Routing And Remote Access console. Click on the Remote Access (Dial-Up Or VPN) option.
- Click on the network interface that is connected to the Internet. For configuration of the interface a public IP address has to be used. If NAT is being used, the appropriate ports have to be forwarded to it from the NAT server's public IP address.
- The next step is to specify if the assignment of IP addresses to VPN clients has to be from a static pool or from a DHCP server which is on the internal network.
- The next step involves specifying if the VPN server is to perform authentication locally or as a RADIUS client.
VPN Protocols
3 VPN protocols are supported by Windows Server 2008: SSTP, L2TP, and PPTP. Discussing the protocols in detail:- Secure Socket Tunneling Protocol (SSTP): It uses an HTTPS channel for the process of encapsulation. User authentication is carried out by encryption and PPP. TCP port 443 uses SSTP, that is used for SSL traffic. This means that it is very rarely blocked by firewalls at public access points like hotels etc.
NAT gateways can be easily traversed by SSTP. A major drawback with SSTP is that it is only supported by Windows Server 2008 and Windows Vista SP1. SSTP requires installation of Secure Sockets Layer (SSL) certificate on the VPN server. This matches the hostname that is assigned to the public address of the VPN server. The connection is made by the clients using this very hostname and they need to trust the certification authority (CA) that releases the SSL certificate.
- Layer 2 Tunneling Protocol with IPsec (L2TP/IPsec): For protecting the data, IPsec and PPP are used by L2TP. The default configuration uses a PKI (public key infrastructure) for issuing computer certificates to every VPN client. Using preshed keys is also a possibility but it is not a secure option. L2TP/IPsec is supported by Windows Server 2008, Vista, XP, and Windows 2003. It is only Windows XP with Service Pack 2 and later that can use L2TP/IPsec through NAT gateways as they are compatible with NAT Traversal. Data encryption, integrity protection and origin authentication are a part of L2TP/IPsec. UDP -User Datagram Protocols ports 500, 1701 and 4500 are to be used for allowing L2TP/IPsec access to the VPN server.
- Point to Point Tunneling Protocol (PPTP): Microsoft Point-to-Point (MPPE) are used by PPTP for encrypting and PPP for the purposes of user authentication. Not as secure as L2TP/IPsec or SSSTP. Some NAT gateways can be traversed by PPTP. PPTP provides data encryption but not data integrity and authentication of origin of data.
When Windows Server 2008 is configured as a VPN server, connections can be made by using all three protocols. Separate network policies for different connection settings can be configured. The settings are dependent on the protocol that is being used. For disabling a specific protocol, the first step is to clear the check boxes for Remote Access Connections (Inbound Only) and Demand-Dial Routing Connections (Inbound And Outbound). The same is depicted in the diagram given below.
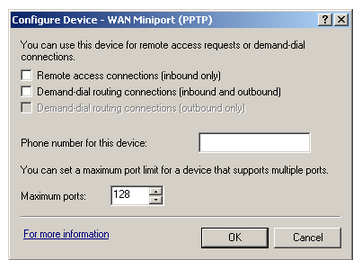
Disabling PPTP on a VPN server
VPN Authentication
The authentication protocols for VPN connections that are supported by Windows Server 2008 are MS-CHAPv2, EAP-MS-CHAPv2, EAP-TLS, PEAP-MS-CHAPv2 and PEAP-TLS.


