Certification: STS Messaging Gateway
Certification Full Name: Symantec/Broadcom Technical Specialist Messaging Gateway
Certification Provider: Symantec
Exam Code: ST0-250
Exam Name: Symantec Messaging Gateway 10.5 Technical Assessment (Broadcom)
ST0-250 Exam Product Screenshots
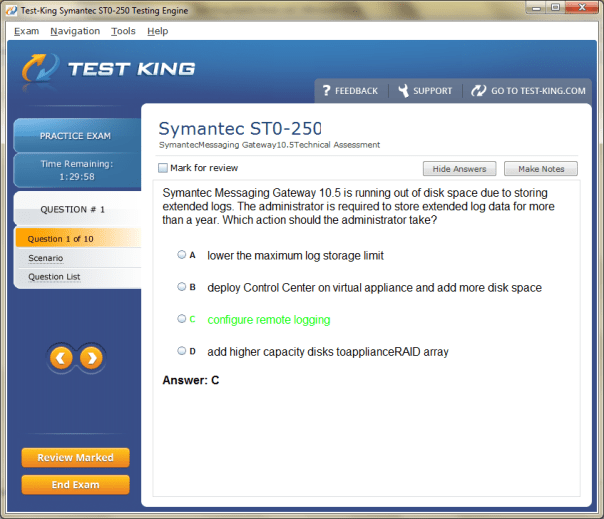
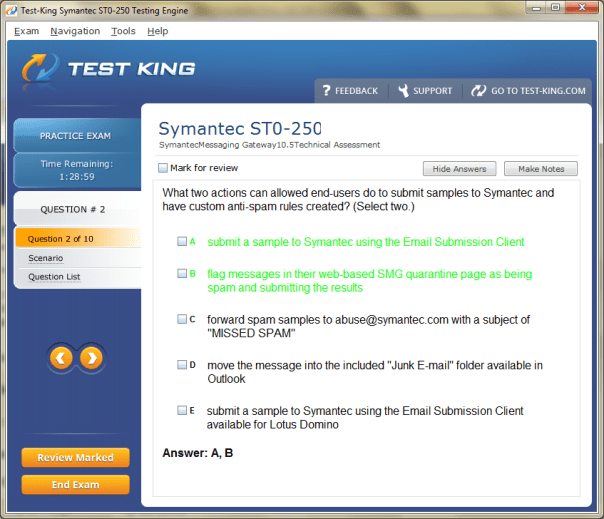
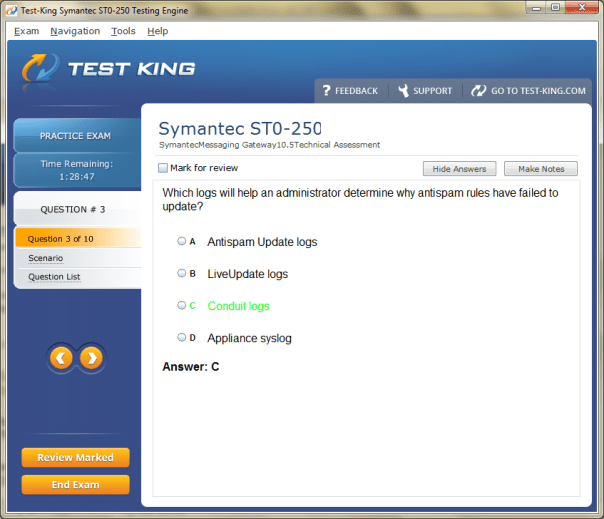
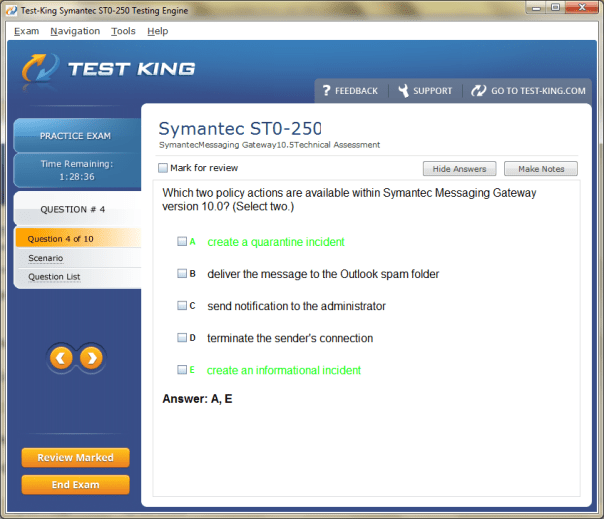
A Complete Guide to Symantec/Broadcom Technical Specialist Messaging Gateway Certification: Boost Your Symantec Skills
In the contemporary realm of cybersecurity, safeguarding digital communications has transcended mere operational necessity to become a strategic imperative. Symantec, now under Broadcom, has long established itself as a formidable pioneer in enterprise security solutions, offering a spectrum of tools designed to mitigate threats, ensure compliance, and preserve organizational integrity. Among these, the messaging gateway technology emerges as a crucial component, acting as a sentinel for enterprise email and messaging systems. The STS Messaging Gateway Certification, formally recognized as the Symantec Technical Specialist Messaging Gateway credential, empowers professionals with the acumen to deploy, configure, and maintain this sophisticated technology efficiently.
Understanding Symantec and the Significance of Messaging Security
Messaging gateways are more than mere filters; they are complex ecosystems capable of detecting nuanced threats, enforcing content policies, and facilitating secure information exchange. In an era where phishing, ransomware, and sophisticated social engineering attacks proliferate, the capability to discern subtle anomalies in messaging traffic is invaluable. The certification equips aspirants with a structured understanding of these systems, enabling them to navigate multifaceted threat landscapes with dexterity. Symantec’s emphasis on innovation and adaptive security frameworks ensures that certified professionals are not merely executors of pre-defined protocols but strategic custodians of organizational communication integrity.
Exploring the Scope and Advantages of Certification
The STS Messaging Gateway credential is meticulously designed for professionals seeking to fortify their technical repertoire in messaging security. Unlike generic IT certifications, this credential delves into the intricate mechanisms underpinning enterprise-level email security, including encryption, content filtering, threat intelligence integration, and policy enforcement. By attaining this certification, individuals not only demonstrate proficiency in operational aspects but also signal their capacity for strategic problem-solving in high-stakes environments.
Earning the certification can profoundly influence career trajectories. Organizations increasingly prioritize candidates who combine practical technical skills with a thorough understanding of threat mitigation strategies. Certified professionals often find themselves entrusted with mission-critical responsibilities, such as designing secure messaging infrastructures, orchestrating incident response protocols, and optimizing performance metrics of security appliances. Moreover, the credential fosters recognition within the cybersecurity community, enhancing professional credibility and positioning individuals as authorities in messaging security architecture.
Beyond personal advancement, the certification serves as a catalyst for organizational resilience. Certified specialists contribute to minimizing the likelihood of data breaches, mitigating potential financial losses, and ensuring compliance with regulatory frameworks governing digital communication. The structured knowledge imparted through the certification process enables professionals to anticipate emerging threats and implement preemptive strategies rather than reactive solutions, thus transforming organizational security posture into a proactive fortress.
Core Competencies and Skill Enhancement
The certification emphasizes the development of core competencies essential for effective messaging gateway administration. Among these, understanding threat detection mechanisms constitutes a foundational pillar. Messaging gateways incorporate multiple layers of analysis, ranging from heuristic evaluation to signature-based detection, and certified professionals learn to interpret these insights to discern sophisticated threats. The ability to configure filters and policies with precision ensures that benign communications flow unhindered while malicious content is intercepted.
Content security extends beyond mere spam filtration, encompassing compliance with organizational policies, legal mandates, and industry standards. The certification curriculum delves into techniques for content inspection, policy enforcement, and the integration of encryption protocols to safeguard sensitive information. Professionals also gain expertise in managing quarantines, handling false positives, and orchestrating remediation workflows that maintain operational continuity without compromising security.
Operational excellence in a messaging gateway environment necessitates a nuanced understanding of deployment topologies, performance optimization, and interoperability with other security systems. The certification instills practical knowledge in configuring high-availability architectures, tuning performance parameters, and troubleshooting anomalies. By mastering these skills, professionals can ensure that messaging systems remain robust, resilient, and capable of handling large-scale enterprise environments without degradation of service or security.
Analytical acumen is another critical dimension nurtured through certification. Messaging threats often manifest in subtle patterns, requiring the practitioner to interpret logs, examine anomalies, and correlate events across diverse datasets. Certified specialists acquire the capability to discern these patterns with precision, leveraging analytical tools and methodologies to proactively fortify the enterprise messaging infrastructure. This capacity for foresight distinguishes the credentialed professional from those who possess only operational familiarity with messaging systems.
Preparing for Certification: Knowledge Acquisition and Methodologies
Aspiring candidates must engage in comprehensive preparation to excel in the STS Messaging Gateway assessment. Foundational knowledge encompasses understanding the architecture of messaging gateways, the principles of secure communication, and the lifecycle of threat mitigation. Practical familiarity with Symantec’s management interfaces, deployment configurations, and reporting mechanisms is indispensable. Candidates are encouraged to cultivate hands-on experience in simulated environments that replicate real-world messaging traffic and threat conditions.
Structured study plans are highly effective, incorporating theoretical comprehension, lab exercises, and iterative review. Candidates benefit from dissecting case studies that illustrate both routine administration and incident response scenarios. The certification emphasizes applied knowledge, ensuring that candidates not only memorize configurations but also comprehend the rationale behind strategic decisions, such as policy prioritization, encryption deployment, and content inspection hierarchies.
Learning resources extend beyond official documentation to include industry publications, forums, and peer discussions. The dynamic nature of messaging threats necessitates continuous exposure to emerging techniques and trends. Aspirants are advised to maintain familiarity with evolving malware behaviors, regulatory updates, and technological enhancements in Symantec’s suite of security solutions. This continuous learning approach equips candidates with a cognitive toolkit to respond to unforeseen challenges effectively.
Simulation exercises play a pivotal role in knowledge consolidation. Candidates replicate deployment scenarios, configure policies, analyze traffic patterns, and troubleshoot simulated attacks. These practical exercises develop intuition for system behavior under stress and foster confidence in decision-making during real-world incidents. By engaging deeply with both conceptual frameworks and operational intricacies, aspirants build a comprehensive skill set that aligns with the expectations of certified professionals.
Real-World Implications of Messaging Gateway Expertise
The capabilities imparted through the certification extend into tangible organizational advantages. Messaging gateway specialists serve as linchpins in enterprise security, ensuring that communications remain insulated from compromise. Their expertise facilitates compliance with data protection regulations, such as GDPR, HIPAA, and industry-specific mandates, thereby shielding organizations from potential legal ramifications. Additionally, their proficiency enables efficient handling of encrypted communication, secure archiving, and granular policy enforcement, which collectively enhance operational integrity.
The analytical competencies acquired through certification are particularly valuable in threat hunting and forensic analysis. Certified professionals are adept at correlating disparate indicators of compromise, recognizing sophisticated attack vectors, and preemptively deploying countermeasures. This capacity transforms messaging systems from passive conduits of information into active defenses against cyber threats. Organizations benefit from reduced incident response times, minimized data loss, and optimized security operations, which cumulatively strengthen the enterprise posture against adversaries.
Moreover, certified specialists contribute to the cultivation of a security-conscious organizational culture. By mentoring colleagues, documenting best practices, and disseminating knowledge regarding emerging threats, they enhance the collective cyber resilience of the enterprise. Their insights inform policy refinement, technology selection, and strategic planning, ensuring that security considerations are integral to organizational decision-making rather than peripheral concerns.
Future Prospects and Professional Growth
The STS Messaging Gateway credential opens avenues for sustained professional growth and specialization. Messaging security expertise is increasingly recognized as a strategic asset, and certified professionals are often considered for roles that encompass broader cybersecurity responsibilities, including network security, incident response, and compliance management. The certification also positions individuals to explore emerging fields such as threat intelligence analysis, secure communications architecture, and enterprise risk management.
As cyber threats continue to evolve, the ability to adapt and integrate new technologies becomes paramount. Certified specialists are well-equipped to assimilate advanced tools, leverage artificial intelligence for threat detection, and contribute to the strategic evolution of messaging security frameworks. Their foundational training ensures that they are not only adept at current technologies but also capable of embracing innovation and leading initiatives that anticipate future challenges.
The professional recognition garnered through certification serves as a testament to both technical proficiency and strategic insight. Certified individuals are often sought after by organizations that prioritize robust security postures and seek to mitigate the complexities of modern threat landscapes. This credential, therefore, functions as both a practical skill endorsement and a symbol of dedication to excellence in cybersecurity, offering enduring benefits throughout one’s career trajectory.
Understanding the Certification Path and Requirements
The journey toward earning the Symantec Technical Specialist Messaging Gateway credential begins with a comprehensive understanding of the examination framework and eligibility criteria. The credential is designed to assess proficiency in enterprise messaging security, encompassing both theoretical comprehension and practical execution. Candidates seeking to attain this certification must familiarize themselves with the architecture of messaging gateway technologies, the operational nuances of threat detection, content management, and policy enforcement, as well as the methods used to optimize system performance and resilience.
Eligibility for the certification often presupposes a foundational knowledge of information technology concepts, including network infrastructure, cybersecurity fundamentals, and email communication protocols. Candidates with prior experience in enterprise messaging administration or security operations gain a significant advantage, as they can relate abstract concepts to real-world scenarios. While formal prerequisites may not mandate a specific degree, hands-on experience in configuring, monitoring, and troubleshooting messaging systems proves indispensable for exam success. The assessment is structured to distinguish individuals who possess both conceptual clarity and applied expertise, ensuring that certified professionals can navigate complex organizational environments with confidence.
Exam Structure and Evaluation Criteria
The certification examination is designed to evaluate a holistic understanding of Symantec messaging gateway systems, emphasizing applied knowledge over rote memorization. Candidates encounter scenario-based questions that simulate real-world challenges, requiring the integration of analytical reasoning, technical proficiency, and strategic foresight. The assessment encompasses multiple domains, including threat detection mechanisms, content security, encryption deployment, policy management, system optimization, and troubleshooting procedures.
Candidates are expected to demonstrate proficiency in interpreting system logs, diagnosing anomalies, and implementing remedial actions that preserve operational continuity. The examination format encourages critical thinking by presenting multifaceted problems that require the candidate to weigh the implications of various configuration choices, policy adjustments, or security interventions. Through this approach, the evaluation measures not only knowledge acquisition but also the ability to translate understanding into effective operational strategies within enterprise environments.
The scoring methodology emphasizes precision and comprehension, rewarding candidates who exhibit both depth and breadth of knowledge. Performance metrics typically include accuracy in addressing security scenarios, efficiency in problem-solving, and adherence to best practices in messaging gateway administration. Aspiring professionals benefit from familiarizing themselves with the types of scenarios presented in prior examinations, as this exposure cultivates an intuitive understanding of question patterns and expected responses.
Skills and Knowledge Areas Assessed
A thorough grasp of the core competencies assessed in the certification is essential for aspirants. The examination emphasizes threat detection as a critical pillar of messaging security, requiring candidates to distinguish between benign and malicious communications with acuity. Professionals must understand heuristic analysis, signature-based detection, and behavioral monitoring to identify advanced persistent threats, phishing campaigns, and spam infiltration attempts.
Content management and policy enforcement constitute another significant dimension of the assessment. Candidates are required to demonstrate the ability to configure message filters, enforce encryption protocols, manage quarantined communications, and ensure compliance with organizational and regulatory mandates. This facet of the examination highlights the balance between security and operational efficiency, challenging candidates to implement strategies that safeguard sensitive information without obstructing legitimate communication.
Deployment topology and system optimization form additional knowledge domains. Candidates must be proficient in configuring high-availability messaging gateways, tuning performance parameters, and ensuring seamless integration with other security infrastructure components. Troubleshooting and diagnostic skills are rigorously tested, with scenarios simulating real-world disruptions, system errors, or misconfigurations. The ability to rapidly identify root causes, deploy corrective measures, and document interventions is a hallmark of certified professionals, reinforcing their value in enterprise settings.
Analytical reasoning is embedded throughout the examination framework. Candidates must correlate disparate indicators, interpret complex system logs, and prioritize security interventions based on potential risk impact. This emphasis on analytical acuity ensures that certified individuals are equipped to anticipate emerging threats and implement preventive strategies, rather than merely reacting to incidents as they arise. The examination thereby cultivates a mindset of proactive defense, aligned with the evolving demands of enterprise cybersecurity.
Preparing for the Examination and Assessing Readiness
Effective preparation for the Symantec Technical Specialist Messaging Gateway credential necessitates a deliberate and structured approach. Candidates benefit from cultivating a comprehensive understanding of messaging gateway architecture, the principles of secure communication, and the practical application of policy enforcement. Hands-on experience in configuring and monitoring gateway systems is indispensable, allowing aspirants to internalize operational workflows, anticipate challenges, and develop intuitive problem-solving strategies.
Self-assessment forms a critical component of exam preparation. Candidates should evaluate their proficiency across the primary domains of the examination, identifying areas of strength and aspects requiring further reinforcement. Simulated exercises, scenario analysis, and lab-based practice are highly recommended, as they replicate the dynamic conditions encountered in enterprise messaging environments. Engaging with these exercises fosters both technical confidence and cognitive flexibility, equipping candidates to respond effectively under examination conditions.
Structured study materials, including official Symantec documentation, specialized guides, and peer discussions, provide the theoretical scaffolding necessary for exam success. Immersion in case studies that illustrate common deployment challenges, policy conflicts, and threat mitigation scenarios enriches conceptual understanding and prepares candidates for the applied nature of the examination. Integrating practical experimentation with theoretical study ensures that aspirants develop both procedural competence and strategic insight, essential qualities for certified professionals.
Time management and iterative review are vital in consolidating knowledge. Candidates should allocate sufficient time for deep engagement with core concepts, followed by repeated practice and reinforcement of critical procedures. This cyclical approach, combining exposure, application, and reflection, enhances retention and fosters the cognitive agility required for interpreting complex scenarios during the examination.
Evaluating Professional Background and Eligibility Factors
Candidates considering the Symantec credential benefit from introspection regarding their professional background and readiness. While formal prerequisites may vary, experience in email administration, network security, or systems management significantly enhances exam performance. Exposure to real-world messaging infrastructure, including high-volume email servers, security appliances, and policy-driven content filters, allows candidates to relate theoretical knowledge to operational realities.
Additionally, familiarity with regulatory frameworks and compliance requirements strengthens candidacy. Messaging gateways often function within contexts governed by stringent data protection regulations, necessitating that professionals implement policies that safeguard sensitive communications while maintaining operational efficiency. Candidates with exposure to such environments can draw upon prior experience to navigate examination scenarios with authority and confidence.
Soft skills, including analytical reasoning, problem-solving, and strategic foresight, complement technical expertise. The examination rewards candidates who approach challenges holistically, considering both immediate technical implications and broader organizational impact. Professionals who have cultivated these competencies through prior roles in enterprise security, IT administration, or project management are well-positioned to excel.
Aligning Certification with Career Objectives
Understanding the relevance of the credential to long-term career objectives is integral to preparation. The certification serves as both a validation of technical proficiency and a strategic enhancement of professional credibility. Organizations increasingly recognize the value of individuals who can administer secure messaging systems, anticipate evolving threats, and implement proactive measures to maintain information integrity.
Certified professionals often transition into roles that extend beyond basic administration, including security architecture design, incident response coordination, and enterprise risk management. The credential provides a platform for specialization in messaging security while establishing a foundation for broader cybersecurity expertise. Aspirants should approach examination preparation with an appreciation of these opportunities, framing their study efforts within the context of professional growth and strategic contribution to organizational security.
Core Technical Concepts and Threat Mitigation
Mastery of the Symantec Technical Specialist Messaging Gateway requires a deep understanding of the intricate mechanisms that govern enterprise messaging security. At the heart of this expertise lies the ability to detect, analyze, and respond to a wide spectrum of threats that compromise the integrity and confidentiality of digital communications. Messaging gateways are sophisticated systems designed to scrutinize inbound and outbound emails, identifying malicious patterns, phishing attempts, ransomware infiltration, and other forms of digital subterfuge that exploit organizational vulnerabilities.
A certified professional must comprehend heuristic and signature-based detection techniques, which operate synergistically to provide multi-layered threat defense. Heuristic analysis allows the identification of anomalous patterns and suspicious behavior in email content or attachments, often revealing threats that evade conventional signature-based mechanisms. Signature detection complements this approach by relying on known threat patterns and databases to intercept malware and spam. Professionals proficient in these systems can configure nuanced detection parameters, calibrate thresholds for alerts, and optimize performance to minimize false positives while maximizing security efficacy.
The capability to implement content inspection policies further enhances messaging security. Messages are filtered based on contextual analysis, regulatory compliance requirements, and organizational guidelines. Certified specialists are adept at crafting rules that prevent sensitive information leakage, enforce encryption for confidential correspondence, and restrict the transmission of inappropriate or potentially harmful content. These skills ensure that the messaging infrastructure operates not only securely but also efficiently, maintaining seamless communication across the enterprise.
Deployment, Configuration, and Administration
In addition to theoretical knowledge, hands-on expertise in deployment, configuration, and administration of the messaging gateway is pivotal. Professionals must navigate complex network topologies, integrating the gateway into diverse environments while maintaining operational resilience. Deployment strategies vary depending on organizational scale, user volume, and the specific security requirements of different departments. Certified specialists are trained to evaluate infrastructure needs, design optimal topologies, and implement high-availability configurations that ensure uninterrupted service even under duress.
Configuration extends beyond initial setup to include ongoing policy management, performance tuning, and adaptive threat mitigation. Administrators must balance security measures with operational continuity, calibrating filters, quarantine rules, and encryption protocols to align with organizational objectives. Regular maintenance, firmware updates, and monitoring of system health are integral to sustaining a robust messaging infrastructure. The ability to perform these tasks methodically, while anticipating potential threats and anomalies, distinguishes certified professionals from those with basic operational knowledge.
Administration also encompasses comprehensive logging and reporting capabilities. Messaging gateways generate detailed records of system activity, threat detection events, and policy enforcement actions. Proficient specialists analyze these logs to identify patterns, assess system effectiveness, and implement improvements. This analytical approach enables predictive maintenance and enhances decision-making for future policy adjustments, ensuring the enterprise remains resilient against evolving digital threats.
Security Protocols and Industry Best Practices
An essential component of certification involves a thorough grasp of security protocols and adherence to industry best practices. Messaging gateways interact with diverse communication protocols, including SMTP, IMAP, and POP3, each of which must be managed with attention to security nuances. Certified professionals are trained to configure secure connections, implement transport layer encryption, and enforce authentication mechanisms that mitigate the risk of unauthorized access.
Adherence to industry standards is equally critical. Professionals must ensure that gateway configurations comply with data protection regulations such as GDPR, HIPAA, and other sector-specific mandates. Compliance-oriented practices include message encryption, retention policies, audit trails, and reporting structures that satisfy both internal and external governance requirements. By integrating best practices into daily operations, specialists not only enhance security but also foster trust among stakeholders, demonstrating organizational commitment to information integrity.
Emerging standards and evolving threats necessitate continuous learning. Certified professionals are encouraged to stay informed about advancements in cybersecurity, cryptography, and threat intelligence. This proactive engagement allows them to anticipate novel attack vectors, adopt innovative mitigation strategies, and maintain alignment with the highest levels of enterprise security governance.
Troubleshooting Common Issues and Performance Optimization
Troubleshooting represents a critical skill set within the messaging gateway domain. Professionals encounter a wide array of operational challenges, from configuration conflicts and policy misalignments to performance bottlenecks and unanticipated threat behaviors. Certified specialists employ systematic diagnostic methods, analyzing logs, interpreting alerts, and isolating root causes to resolve issues efficiently. This expertise reduces downtime, minimizes operational disruption, and sustains the overall reliability of messaging systems.
Performance optimization is intertwined with troubleshooting, emphasizing the importance of system responsiveness and throughput. Messaging gateways must manage high volumes of communication without sacrificing security or operational efficiency. Professionals calibrate system parameters, optimize policy execution sequences, and employ resource management strategies to enhance processing speed and accuracy. Mastery of these techniques ensures that enterprise messaging remains both secure and performant, even under high-demand conditions or during periods of intensified threat activity.
Analytical reasoning underpins both troubleshooting and optimization. Certified specialists develop the capacity to discern subtle patterns, correlate disparate indicators, and implement preventive measures that mitigate recurrent problems. This forward-thinking approach transforms routine maintenance into a strategic function, ensuring that messaging infrastructure evolves in response to emerging threats and operational requirements rather than reacting passively to incidents as they occur.
Cultivating Analytical Thinking and Problem-Solving Skills
Beyond technical execution, the certification emphasizes the development of analytical thinking and problem-solving capabilities. Messaging gateways generate extensive data streams, encompassing traffic logs, threat alerts, content scanning results, and policy enforcement metrics. Professionals must interpret these datasets to identify anomalies, forecast potential risks, and devise effective mitigation strategies. This analytical acumen allows for rapid identification of complex threats and informed decision-making that balances security with operational continuity.
Problem-solving extends to strategic decision-making in policy design and deployment architecture. Certified specialists evaluate the implications of various configurations, considering both immediate operational impacts and long-term security outcomes. They anticipate potential attack vectors, assess the efficacy of countermeasures, and implement adaptive strategies that enhance resilience. This combination of analytical insight and applied execution ensures that messaging gateways function as proactive defense mechanisms, safeguarding enterprise communication channels against an ever-evolving threat landscape.
The cultivation of these skills is reinforced through practical exercises, scenario simulations, and iterative reflection on system behavior. Candidates are encouraged to engage in experiential learning that mirrors real-world conditions, providing opportunities to apply theoretical knowledge to tangible challenges. Through this immersive approach, aspirants internalize best practices, refine problem-solving methodologies, and develop the cognitive flexibility necessary to navigate dynamic security environments.
Integrating Certification Knowledge into Enterprise Environments
The competencies developed through certification are most valuable when seamlessly integrated into enterprise environments. Certified professionals contribute to organizational resilience by designing policies that harmonize security imperatives with operational demands. They implement encryption, content filtering, and threat detection protocols in ways that enhance communication efficiency while maintaining robust security postures. Their expertise ensures that enterprise messaging systems can withstand sophisticated cyber threats without impeding business processes.
Collaboration is an integral aspect of applying certification knowledge in practical settings. Specialists often work alongside network administrators, compliance officers, and security analysts to design and maintain cohesive defense frameworks. Their insights inform incident response protocols, guide system upgrades, and shape strategic security initiatives. By embedding their skills into organizational workflows, certified professionals elevate the overall security maturity of the enterprise and foster a culture of proactive risk management.
Professional growth is also supported by ongoing engagement with emerging technologies. Messaging gateway experts continually evaluate new security tools, threat intelligence platforms, and adaptive policies. This dynamic approach ensures that enterprises remain at the forefront of secure communication practices, leveraging the latest advancements to fortify messaging systems against evolving digital threats.
Enhancing Operational Efficiency and Strategic Impact
The impact of certification extends beyond technical execution to encompass strategic contributions within the enterprise. Certified specialists optimize resource allocation, streamline system processes, and enhance the efficiency of security operations. By implementing structured policies and preventive measures, they reduce operational disruptions and enable IT teams to focus on higher-value initiatives. Messaging gateway expertise thus serves as both a protective measure and a catalyst for operational excellence.
Strategic foresight is cultivated through the integration of analytical insights with organizational objectives. Professionals anticipate potential vulnerabilities, evaluate risk exposure, and recommend policy adjustments that balance security imperatives with business continuity. Their recommendations influence enterprise decision-making, inform investment in security infrastructure, and contribute to a culture of vigilant, informed risk management. This dual focus on operational efficiency and strategic impact underscores the value of certification, positioning specialists as indispensable contributors to both security and organizational success.
Structured Learning Approaches and Study Planning
Achieving the Symantec Technical Specialist Messaging Gateway credential requires a disciplined and methodical approach to learning, combining theoretical knowledge with hands-on practice. A structured study plan serves as the foundation for success, ensuring that candidates cover essential topics systematically while reinforcing practical skills. Aspirants benefit from segmenting their preparation into manageable cycles, dedicating time to core concepts, practical exercises, and iterative review to consolidate understanding.
Effective study strategies begin with a comprehensive assessment of one’s current proficiency across various knowledge domains. This introspective approach allows candidates to identify strengths and areas needing reinforcement. Developing a personalized study schedule that balances conceptual exploration with applied experimentation enhances retention and ensures a more confident approach to examination challenges. By establishing clear objectives for each learning session, candidates maintain focus, cultivate discipline, and progressively build mastery over the intricate mechanisms of messaging gateway systems.
The use of diverse learning modalities reinforces comprehension and engagement. Combining textual resources, video tutorials, interactive simulations, and scenario-based exercises enables candidates to approach complex concepts from multiple perspectives. This multidimensional strategy not only deepens understanding but also cultivates the adaptability required to address real-world challenges in enterprise messaging environments. Furthermore, maintaining a consistent study rhythm reduces cognitive fatigue, allowing for sustained focus and cumulative knowledge acquisition over time.
Recommended Learning Materials and Resources
Candidates preparing for the certification benefit from a curated selection of learning materials that encompass both foundational theory and practical application. Official Symantec documentation provides authoritative guidance on messaging gateway architecture, deployment strategies, policy configuration, and threat mitigation techniques. These resources offer detailed insights into operational workflows, system functionalities, and configuration nuances, forming the backbone of a comprehensive study plan.
Supplementary materials, including industry publications, cybersecurity journals, and peer-reviewed articles, provide additional perspectives and case studies. Exposure to diverse scenarios and real-world challenges enriches understanding, allowing candidates to correlate theoretical knowledge with practical implications. Peer discussion forums, study groups, and mentorship opportunities further enhance learning by facilitating the exchange of ideas, troubleshooting strategies, and best practices among individuals pursuing similar objectives.
Practical exercises play a pivotal role in internalizing concepts. Candidates are encouraged to engage in hands-on activities that simulate enterprise messaging environments, including configuring policies, monitoring traffic, analyzing logs, and responding to simulated threats. These exercises foster experiential learning, enabling aspirants to apply theoretical knowledge in controlled yet realistic scenarios. The iterative practice of troubleshooting, performance optimization, and policy enforcement develops both technical proficiency and analytical acumen, essential attributes for certified specialists.
Utilizing Virtual Environments for Simulation
Virtual environments serve as indispensable tools for experiential learning, allowing candidates to replicate the operational complexities of messaging gateway systems without compromising live enterprise networks. Through virtual labs, aspirants can explore deployment topologies, configure multiple policy layers, and simulate high-volume messaging scenarios. This controlled experimentation provides insight into system behavior under varying conditions, facilitating the development of intuitive problem-solving strategies and adaptive decision-making.
Simulation exercises also allow candidates to experiment with diverse threat scenarios, including phishing attacks, ransomware infiltration, and content violations. By observing system responses, adjusting detection parameters, and analyzing outcomes, aspirants gain a nuanced understanding of the interplay between configuration choices and security efficacy. This immersive approach enhances readiness for the examination, ensuring that candidates can confidently apply learned principles to practical situations while demonstrating the analytical precision expected of certified professionals.
Furthermore, virtual environments encourage iterative learning. Candidates can repeatedly test configurations, explore alternative strategies, and refine their approach without the risk of disrupting live systems. This repetition fosters mastery, builds confidence, and reinforces the cognitive flexibility necessary to navigate the dynamic challenges inherent in messaging gateway administration.
Peer Learning and Mentorship
Engaging with peers and mentors significantly enhances the learning process, providing opportunities for collaborative problem-solving and knowledge exchange. Study groups and discussion forums enable aspirants to share insights, clarify doubts, and collectively analyze complex scenarios. This interaction promotes the assimilation of diverse perspectives, encourages critical thinking, and fosters a deeper understanding of both operational procedures and strategic considerations.
Mentorship offers additional advantages by providing guidance from experienced professionals who have navigated similar certification pathways. Mentors can offer insights into common pitfalls, effective study techniques, and practical applications of theoretical concepts. Their experiential wisdom helps candidates anticipate examination challenges, understand the rationale behind system behaviors, and develop strategies that align with industry best practices. Through mentorship, aspirants gain not only technical guidance but also encouragement and perspective, enhancing both competence and confidence.
Collaborative learning environments also simulate real-world professional interactions, preparing candidates for the teamwork and communication skills required in enterprise settings. Certified specialists often work alongside network administrators, security analysts, and compliance officers, and exposure to collaborative problem-solving during preparation mirrors these operational dynamics, fostering readiness for both examination scenarios and professional responsibilities.
Effective Revision Techniques and Knowledge Reinforcement
Revision constitutes a critical phase of preparation, enabling candidates to consolidate knowledge, identify gaps, and reinforce retention. Effective revision strategies encompass repeated review of core concepts, reapplication of practical exercises, and testing oneself under conditions that mimic examination constraints. By systematically revisiting key topics, aspirants strengthen neural pathways associated with technical knowledge, enhancing recall and analytical application during assessment.
Spaced repetition techniques are particularly beneficial, distributing review sessions over time to optimize long-term retention. Revisiting configuration procedures, policy enforcement strategies, and threat detection methods at regular intervals ensures that knowledge remains accessible and resilient to cognitive decay. Additionally, synthesizing learning into concise summaries, conceptual maps, or procedural checklists aids in distilling complex concepts into manageable reference points, streamlining last-minute review without sacrificing depth.
Integrating scenario-based revision further sharpens analytical capabilities. Candidates rehearse responses to hypothetical operational challenges, drawing upon both theoretical knowledge and practical experience. This approach reinforces cognitive flexibility, enabling aspirants to adapt learned principles to novel situations, anticipate potential complications, and implement effective solutions. The iterative cycle of study, practice, and reflection cultivates a robust understanding of messaging gateway systems and fosters the confidence necessary for examination success.
Balancing Study with Cognitive Well-being
Sustained preparation for the certification requires attention to cognitive well-being and mental resilience. High-intensity study schedules, complex technical content, and extended periods of concentration can induce fatigue, impairing retention and analytical performance. Candidates are encouraged to integrate regular breaks, physical activity, and mindfulness techniques into their study routine, promoting mental clarity and sustained focus.
Sleep hygiene, nutrition, and stress management play pivotal roles in optimizing cognitive function. Adequate rest enhances memory consolidation, attentional control, and problem-solving capacity, while balanced nutrition supports neural efficiency and sustained energy. Mindfulness practices, including meditation and reflective journaling, provide mechanisms for managing examination-related anxiety, fostering composure, and sustaining motivation throughout the preparation period.
The cultivation of cognitive well-being complements technical study by enhancing the capacity to engage deeply with complex material, approach challenges methodically, and retain information effectively. Certified specialists not only possess technical proficiency but also the mental resilience required to navigate dynamic operational environments, demonstrating the interplay between knowledge acquisition and cognitive preparedness.
Integrating Learning into Practical Experience
Effective preparation extends beyond theoretical study to encompass the integration of acquired knowledge into practical experience. Candidates are encouraged to apply learned principles within controlled environments, exploring system configurations, policy enforcement, and threat response in tangible contexts. This experiential learning bridges the gap between conceptual understanding and operational execution, fostering competence and confidence in real-world scenarios.
Engagement with live or simulated messaging environments allows aspirants to observe the dynamic interplay between system components, policy rules, and threat behaviors. By configuring, monitoring, and analyzing system responses, candidates internalize procedural workflows, develop troubleshooting expertise, and cultivate the analytical reasoning necessary for proactive defense. The iterative application of knowledge reinforces learning, ensuring that concepts are not merely memorized but deeply understood and readily deployable in professional contexts.
Professional networking further supports the integration of learning into practice. Interaction with peers, mentors, and industry practitioners provides exposure to diverse operational strategies, emerging threats, and innovative approaches to messaging security. These exchanges enrich understanding, broaden perspective, and cultivate adaptive problem-solving skills, ensuring that certified specialists remain agile, informed, and effective in dynamic enterprise environments.
Psychological Preparation and Mindset
Success in the Symantec Technical Specialist Messaging Gateway examination begins long before the first question is read; it is rooted in psychological preparedness and a resilient mindset. Candidates must cultivate confidence, focus, and composure to navigate the nuanced scenarios that typify the assessment. Stress management plays a pivotal role, as anxiety can impede cognitive clarity, reduce recall, and hinder problem-solving capabilities. Developing a positive mindset involves visualization of successful performance, rehearsal of challenging scenarios, and affirmation of one’s mastery over technical concepts and operational procedures.
Practices such as deep breathing, meditation, and mental rehearsal help candidates stabilize attention and reduce pre-examination tension. Viewing the examination as an opportunity to demonstrate expertise rather than a threat to competence fosters a sense of control and reduces counterproductive pressure. Additionally, familiarization with examination conditions, including timing constraints and question formats, contributes to cognitive readiness by reducing uncertainty and minimizing surprises on the actual day.
Time Management and Strategic Pacing
Effective time management is integral to examination success. The STS Messaging Gateway assessment presents a mixture of conceptual and scenario-based questions, each requiring careful analysis and deliberate reasoning. Candidates benefit from allocating time proportionally to question complexity, ensuring that straightforward items are addressed efficiently while reserving sufficient cognitive bandwidth for intricate scenarios. Establishing a pacing strategy prior to the examination enhances confidence, reduces rushed decisions, and minimizes the likelihood of incomplete responses.
During the assessment, monitoring time without becoming preoccupied is essential. Candidates can employ mental checkpoints, dividing the examination into segments and tracking progress to maintain a steady rhythm. Strategic pacing allows for deliberate reflection on complex problems, the cross-verification of answers, and reallocation of time as necessary to address high-value questions. Mastery of pacing is particularly critical in scenario-driven items, where thoughtful consideration of policy implications, configuration choices, and threat mitigation strategies determines accuracy.
Avoiding Common Pitfalls
Awareness of common pitfalls encountered by candidates enhances preparation and minimizes the risk of preventable errors. One frequent challenge is overreliance on memorization rather than understanding underlying principles. The examination emphasizes applied knowledge, requiring candidates to interpret system behavior, analyze threats, and implement appropriate configurations. Memorization without comprehension often leads to misinterpretation of complex scenarios, reducing performance and confidence.
Another common issue is misreading questions or overlooking critical details. Scenario-based items often include nuanced parameters, multiple conditional clauses, or embedded constraints that influence the optimal response. Careful reading, attention to context, and consideration of all variables ensure that candidates select solutions aligned with best practices and operational feasibility. Candidates are encouraged to pause briefly before answering, mentally summarizing key points and potential consequences of their decisions.
Overconfidence can also pose a hazard. Candidates who assume familiarity with basic concepts may underestimate the intricacy of applied scenarios. Maintaining vigilance, cross-verifying assumptions, and methodically working through each problem ensures thorough analysis. Balancing confidence with analytical diligence optimizes performance and reduces the likelihood of avoidable mistakes.
Interpreting Complex Scenario-Based Questions
Scenario-based questions constitute a substantial portion of the certification examination, assessing candidates’ ability to apply knowledge to realistic operational challenges. These questions often present multi-layered situations, including misconfigured policies, evolving threat patterns, and competing operational priorities. Candidates must analyze the scenario holistically, identify underlying issues, and determine solutions that balance security, compliance, and operational efficiency.
Effective interpretation involves decomposing scenarios into constituent elements, mapping relationships between system components, and predicting outcomes of potential interventions. Candidates should consider factors such as threat severity, policy interactions, encryption requirements, and operational continuity when evaluating response options. By approaching scenarios methodically, aspirants can distinguish superficial issues from underlying systemic vulnerabilities and implement solutions that demonstrate both technical proficiency and strategic insight.
Developing a structured approach to scenario analysis during preparation enhances exam-day performance. Candidates benefit from practicing similar problems under timed conditions, reviewing their rationale, and refining strategies based on observed outcomes. This iterative method cultivates cognitive agility, reinforces problem-solving frameworks, and fosters the ability to adapt principles to novel challenges with precision and confidence.
Post-Examination Steps and Knowledge Consolidation
While the examination itself represents a milestone, the post-examination phase remains crucial for knowledge consolidation and professional development. Candidates often encounter insights during the assessment that highlight areas requiring further refinement, which can inform future practice or continuing education. Reflecting on the examination experience, analyzing thought processes, and identifying patterns in question types contributes to long-term expertise, irrespective of the immediate outcome.
Successful candidates proceed to leverage the credential in practical environments, applying learned concepts to real-world messaging gateway administration, threat mitigation, and policy enforcement. Engaging in continuous practice, revisiting complex scenarios, and integrating emerging cybersecurity trends ensures that the knowledge acquired remains current and operationally relevant. The post-examination period thus reinforces the symbiotic relationship between certification preparation, applied proficiency, and sustained professional growth.
Candidates who do not achieve the desired results immediately benefit from a structured reflection process. Identifying conceptual gaps, revisiting challenging topics, and refining problem-solving approaches enhance readiness for subsequent attempts. This iterative learning approach exemplifies the adaptive mindset emphasized throughout the certification journey, fostering resilience, technical acumen, and analytical sophistication.
Techniques for Enhanced Cognitive Performance
Optimizing cognitive performance during the examination extends beyond content mastery to encompass mental strategies for efficient processing and recall. Techniques such as active engagement with questions, mental visualization of system behavior, and sequential problem mapping enhance comprehension and reduce cognitive overload. Candidates are encouraged to mentally simulate configuration adjustments, threat responses, and policy implementations as they navigate scenario-based items, translating abstract knowledge into actionable insights.
Mnemonic devices, conceptual analogies, and associative reasoning further support memory retention and retrieval. By linking new information to prior knowledge or practical experience, candidates reinforce neural pathways that facilitate rapid recall during the assessment. Additionally, focusing on one task at a time, avoiding multitasking, and maintaining attentional clarity ensures that cognitive resources are deployed efficiently, minimizing errors and maximizing analytical depth.
Environmental factors, such as physical comfort, lighting, and noise control, also influence cognitive performance. Candidates are advised to optimize examination conditions to reduce distractions, maintain concentration, and sustain mental stamina throughout the assessment duration. By attending to both internal and external factors, aspirants enhance their ability to process complex information, evaluate multiple variables, and deliver precise, well-reasoned responses.
Integrating Practical Experience into Exam Strategy
Practical experience with Symantec messaging gateway systems underpins successful exam performance. Candidates who have engaged in policy configuration, threat analysis, log interpretation, and system optimization can draw upon these experiences when confronting examination scenarios. Translating hands-on familiarity into analytical reasoning enables aspirants to approach complex questions with confidence, anticipate system behavior, and implement solutions that reflect both theoretical understanding and operational insight.
Simulated exercises conducted during preparation reinforce this integration of knowledge and practice. By recreating typical challenges encountered in enterprise environments, candidates cultivate pattern recognition, procedural fluency, and adaptive problem-solving. This experiential learning strengthens the cognitive frameworks required for interpreting intricate scenarios, ensuring that responses are grounded in both technical rigor and strategic foresight.
Peer collaboration and mentorship also enhance exam strategies. Discussing scenario approaches, reviewing policy decisions, and analyzing threat responses with experienced professionals provides alternative perspectives and exposes candidates to nuances they may not encounter independently. This collaborative engagement enriches understanding, fosters analytical flexibility, and equips aspirants to navigate the multifaceted demands of the examination effectively.
Leveraging Certification for Career Advancement
Earning the Symantec Technical Specialist Messaging Gateway credential serves as a catalyst for significant professional growth within the cybersecurity and enterprise IT domains. Organizations increasingly recognize the value of individuals who possess both technical proficiency and strategic understanding of messaging security infrastructure. Certified professionals demonstrate their capacity to administer enterprise-level systems, mitigate sophisticated threats, and implement policies that protect sensitive communications while maintaining operational continuity. These capabilities position individuals for roles of increased responsibility, encompassing system architecture design, security policy development, and incident response coordination.
The certification enhances credibility in professional environments, signaling to employers and colleagues that the individual possesses the expertise required to manage complex messaging gateway systems effectively. This recognition often translates into opportunities for promotion, higher remuneration, and expanded influence within security and IT teams. Beyond immediate career benefits, certification fosters long-term employability by validating skills that remain in high demand as organizations continue to prioritize the security of their communication channels.
Roles and Responsibilities of Certified Professionals
Professionals holding the credential often assume pivotal roles in enterprise security architecture. Responsibilities typically encompass deployment, configuration, and administration of messaging gateways, as well as monitoring and optimizing system performance. These specialists are entrusted with enforcing content security policies, managing encryption protocols, and overseeing threat detection mechanisms that safeguard organizational communication. Their expertise extends to analyzing logs, identifying anomalies, and implementing preventive measures that enhance the resilience of messaging systems.
Additionally, certified professionals often collaborate with network administrators, compliance officers, and security analysts to ensure cohesive and comprehensive protection strategies. They advise on policy development, provide guidance for incident response, and assist in integrating messaging gateways with broader security infrastructure. This collaborative function underscores the strategic dimension of the certification, highlighting the importance of applying technical skills within a coordinated organizational framework to achieve maximal security outcomes.
Integration of Messaging Gateway Expertise in Enterprise Security
The practical application of certification knowledge within enterprise environments has profound implications for organizational resilience. Messaging gateways operate as critical checkpoints in the flow of corporate information, intercepting threats, enforcing compliance, and safeguarding sensitive communications. Certified specialists ensure that these systems operate optimally, balancing security imperatives with operational efficiency. Their ability to configure policies, fine-tune detection mechanisms, and troubleshoot performance issues ensures that enterprise messaging remains both secure and reliable under varying load conditions.
Integration also involves proactive threat anticipation. Certified professionals leverage their understanding of attack patterns, phishing strategies, and malware propagation to anticipate vulnerabilities and implement countermeasures before incidents occur. This forward-thinking approach transforms messaging gateways from passive defensive tools into active instruments of cybersecurity, reinforcing the organization’s overall protective posture. The expertise gained through certification thus translates into tangible organizational benefits, reducing potential downtime, mitigating data breaches, and ensuring regulatory compliance.
Emerging Trends in Messaging Security
The field of messaging security is continually evolving, driven by innovations in cyberattack methodologies and advancements in protective technologies. Certified specialists must remain conversant with emerging trends such as artificial intelligence-driven threat detection, cloud-based email security solutions, and advanced encryption protocols. Staying abreast of these developments enables professionals to refine deployment strategies, adopt innovative tools, and maintain organizational systems that are both resilient and adaptive to contemporary threats.
The proliferation of sophisticated phishing campaigns, ransomware, and targeted social engineering attacks necessitates a dynamic approach to messaging security. Certified professionals are equipped to implement adaptive policies, analyze evolving threat intelligence, and adjust gateway configurations to counter emerging risks. Their role extends beyond reactive incident management, encompassing strategic foresight and continuous improvement to anticipate vulnerabilities and enhance overall enterprise security.
Long-Term Benefits and Professional Recognition
The Symantec Technical Specialist Messaging Gateway credential provides enduring advantages that extend beyond immediate employment opportunities. Certified individuals gain access to a network of peers and professionals who share insights, best practices, and emerging knowledge in messaging security. This professional community fosters continuous learning, exposure to innovative strategies, and collaboration on complex challenges. Such engagement enhances both technical proficiency and professional visibility, reinforcing the individual’s standing within the cybersecurity landscape.
Long-term career benefits include specialization opportunities, such as roles in threat intelligence, security architecture design, compliance management, and enterprise risk assessment. The credential equips individuals with a foundation to pursue advanced certifications, leadership positions, and consulting engagements. As organizations increasingly seek individuals capable of implementing robust, adaptive security measures, the certification serves as a differentiator, establishing both credibility and marketability in a competitive professional environment.
Practical Applications and Organizational Impact
Certified specialists contribute to tangible organizational improvements, including enhanced policy enforcement, optimized system performance, and strengthened threat response capabilities. Their expertise ensures that messaging gateways operate as comprehensive defense mechanisms, integrating with broader security infrastructure to provide layered protection. By maintaining vigilant oversight, adjusting configurations in response to threat intelligence, and advising on strategic policy deployment, these professionals directly influence the effectiveness of enterprise cybersecurity programs.
Beyond technical execution, the role encompasses strategic impact. Certified specialists inform organizational decision-making, guiding investments in security infrastructure, recommending best practices, and mentoring team members in operational excellence. Their ability to translate complex technical concepts into actionable strategies enhances both operational efficiency and security posture, demonstrating the multifaceted value of certification in real-world applications.
Sustaining Expertise Through Continuous Learning
Attaining the credential is not the culmination but rather a milestone in a continuous journey of professional growth. Messaging security is inherently dynamic, and sustained expertise requires ongoing engagement with technological advancements, threat evolution, and industry best practices. Certified professionals are encouraged to participate in training workshops, conferences, and knowledge-sharing forums, ensuring that their skills remain current and applicable to emerging challenges.
Continuous learning also involves reflective practice, wherein specialists analyze past deployments, review incident responses, and extract lessons that inform future strategy. This iterative approach reinforces technical competence, enhances problem-solving abilities, and fosters adaptive thinking. By embracing continuous learning, certified professionals maintain the agility required to navigate complex, ever-changing enterprise environments, sustaining both personal growth and organizational value.
Strategic Leadership and Mentorship Opportunities
Beyond operational responsibilities, certified specialists often assume mentorship and leadership roles within their organizations. Their expertise positions them to guide junior administrators, provide training in best practices, and influence the strategic direction of messaging security initiatives. Through mentorship, they disseminate knowledge, cultivate a culture of vigilance, and enhance the overall capability of IT and security teams. Leadership in this context extends to strategic planning, policy review, and integration of messaging gateways with broader enterprise security frameworks.
These leadership responsibilities underscore the strategic dimension of the certification. Professionals are not merely executors of technical tasks but architects of resilient communication environments. Their guidance ensures that organizational messaging infrastructure evolves in alignment with both current operational demands and anticipated future threats, demonstrating the long-term impact of certification on enterprise security strategy.
Career Trajectory and Professional Opportunities
The credential opens diverse career pathways in cybersecurity, IT administration, and enterprise risk management. Professionals may advance into specialized roles, including messaging security architect, security operations analyst, compliance manager, or consultant for secure communications infrastructure. The combination of practical expertise, analytical acumen, and strategic insight enhances employability, enabling certified individuals to navigate competitive job markets and pursue roles that align with both technical skills and career aspirations.
The professional recognition associated with certification extends to both internal and external stakeholders. Employers value the assurance that certified specialists can maintain secure, compliant, and efficient messaging systems, while peers and industry professionals recognize the technical credibility and strategic judgment the credential represents. This recognition fosters trust, expands influence, and enhances the professional reputation of the individual within the cybersecurity community.
Conclusion
The Symantec Technical Specialist Messaging Gateway certification represents a confluence of technical mastery, strategic insight, and professional growth. Certified individuals are equipped to safeguard enterprise communications, optimize messaging infrastructure, and navigate complex threat landscapes with confidence. Their expertise extends beyond operational execution to encompass policy development, system integration, and strategic guidance, providing tangible benefits to both organizations and their own professional trajectories.
By attaining this credential, professionals signal their commitment to excellence in messaging security, demonstrating both practical competence and analytical sophistication. The certification empowers individuals to assume pivotal roles within enterprises, influence organizational security strategy, and contribute meaningfully to the protection of critical information. Continuous engagement with emerging technologies, threat intelligence, and industry best practices ensures that certified specialists remain agile, effective, and valued contributors to the evolving field of enterprise cybersecurity, making the credential both a professional milestone and a foundation for enduring career success.
Frequently Asked Questions
How can I get the products after purchase?
All products are available for download immediately from your Member's Area. Once you have made the payment, you will be transferred to Member's Area where you can login and download the products you have purchased to your computer.
How long can I use my product? Will it be valid forever?
Test-King products have a validity of 90 days from the date of purchase. This means that any updates to the products, including but not limited to new questions, or updates and changes by our editing team, will be automatically downloaded on to computer to make sure that you get latest exam prep materials during those 90 days.
Can I renew my product if when it's expired?
Yes, when the 90 days of your product validity are over, you have the option of renewing your expired products with a 30% discount. This can be done in your Member's Area.
Please note that you will not be able to use the product after it has expired if you don't renew it.
How often are the questions updated?
We always try to provide the latest pool of questions, Updates in the questions depend on the changes in actual pool of questions by different vendors. As soon as we know about the change in the exam question pool we try our best to update the products as fast as possible.
How many computers I can download Test-King software on?
You can download the Test-King products on the maximum number of 2 (two) computers or devices. If you need to use the software on more than two machines, you can purchase this option separately. Please email support@test-king.com if you need to use more than 5 (five) computers.
What is a PDF Version?
PDF Version is a pdf document of Questions & Answers product. The document file has standart .pdf format, which can be easily read by any pdf reader application like Adobe Acrobat Reader, Foxit Reader, OpenOffice, Google Docs and many others.
Can I purchase PDF Version without the Testing Engine?
PDF Version cannot be purchased separately. It is only available as an add-on to main Question & Answer Testing Engine product.
What operating systems are supported by your Testing Engine software?
Our testing engine is supported by Windows. Andriod and IOS software is currently under development.
Top Symantec Exams
Symantec Certifications
- SCS Administration of Symantec Email Security.cloud - Symantec/Broadcom Certified Specialist Administration of Symantec Email Security.cloud
- SCS Administration of Symantec Endpoint Protection 14 - Symantec/Broadcom Certified Specialist Administration of Symantec Endpoint Protection 14
- SCS Administration of Symantec ProxySG 6.7 - Symantec/Broadcom Certified Specialist Administration of Symantec ProxySG 6.7
- SCS Data Loss Prevention - Symantec/Broadcom Certified Specialist Data Loss Prevention
- STS Messaging Gateway - Symantec/Broadcom Technical Specialist Messaging Gateway
- STS NetBackup 7.5 for Windows - Symantec/Broadcom Technical Specialist NetBackup 7.5 for Windows


