Certification: CISSP-ISSAP
Certification Full Name: Information Systems Security Architecture Professional
Certification Provider: ISC
Exam Code: CISSP-ISSAP
Exam Name: Information Systems Security Architecture Professional
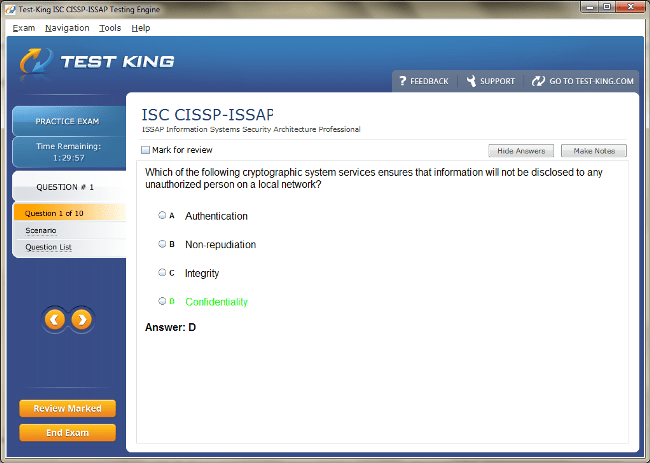
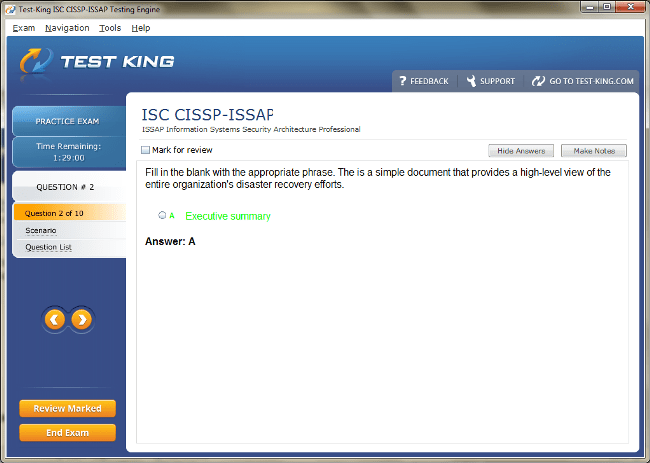
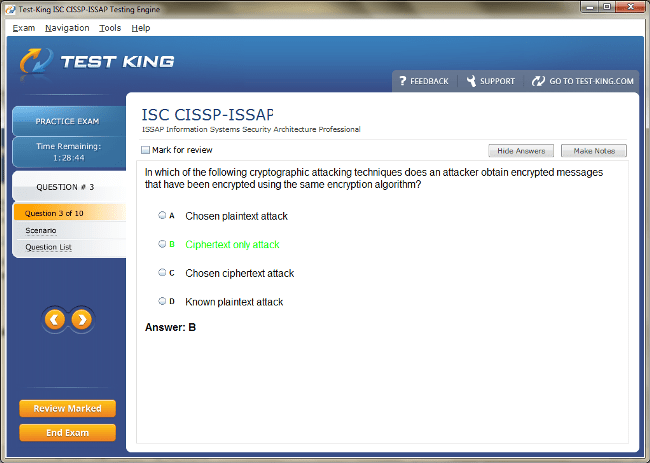
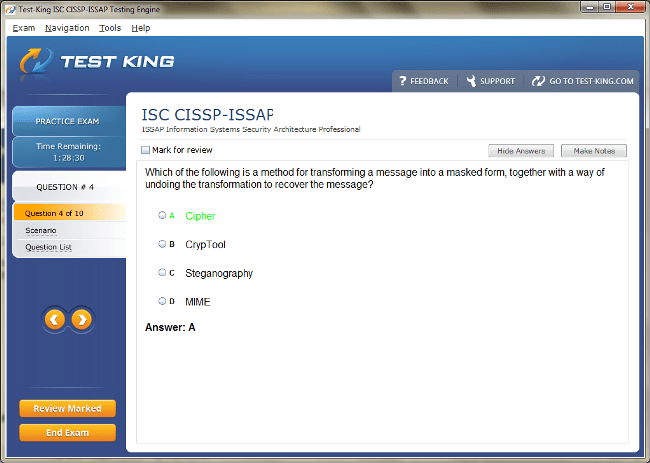
CISSP-ISSAP Exam Product Screenshots
CISSP-ISSAP Certification: Elevate Your Expertise in Information Security Architecture
In the rapidly evolving domain of information technology, the significance of a well-structured security architecture cannot be overstated. Organizations face a myriad of cyber threats daily, ranging from subtle intrusions to orchestrated attacks targeting critical infrastructure. Navigating these challenges demands not only technical proficiency but also a strategic understanding of risk, governance, and the alignment of security solutions with organizational objectives. The Information Systems Security Architecture Professional, recognized under the CISSP-ISSAP designation, embodies this intersection of expertise and strategy. These professionals do not merely respond to threats; they anticipate them, architecting security frameworks that integrate seamlessly with an enterprise's mission, vision, and operational policies.
Understanding the Role and Importance of ISSAP Professionals
The ISSAP professional distinguishes themselves by providing management with risk-based guidance, shaping security strategies that underpin organizational goals. Their role is far more than implementing security tools; it encompasses a nuanced comprehension of policy development, regulatory compliance, and the adaptability required to accommodate changing technological landscapes. Unlike standard security practitioners who focus on operational or tactical functions, ISSAP-certified architects operate at a level where strategic decisions regarding architecture, governance, and risk management converge. This elevated perspective ensures that the security solutions they propose are not only technically sound but also aligned with the broader strategic priorities of the organization.
The expertise of ISSAP professionals extends into multiple facets of an organization’s security posture. They evaluate existing security mechanisms, anticipate potential vulnerabilities, and design architectures that are resilient against both internal and external threats. Their proficiency covers access management systems, communications and network security, cryptography, and physical security considerations. Moreover, they are adept at business continuity planning and disaster recovery strategies, ensuring that an organization’s critical operations can withstand and recover from adverse events. In essence, ISSAP professionals act as the architects of trust, constructing robust security environments that balance risk mitigation with operational efficacy.
Organizations increasingly recognize the value of professionals who can bridge the gap between technical security measures and strategic business objectives. In this context, the CISSP-ISSAP certification emerges as a hallmark of advanced knowledge and capability in information security architecture. By earning this credential, security architects signal their ability to craft comprehensive security programs that not only meet regulatory requirements but also enhance organizational resilience, safeguard intellectual property, and ensure continuity in the face of cyber adversities.
The demand for such expertise is not limited to the private sector; governmental and critical infrastructure organizations also seek ISSAP professionals to protect sensitive information and maintain operational integrity. This certification, therefore, represents a confluence of technical mastery, strategic acumen, and leadership potential, positioning individuals to influence both technological and managerial dimensions of information security.
Achieving the CISSP-ISSAP credential requires more than familiarity with common security practices. Candidates must demonstrate a profound understanding of security architecture principles and the ability to apply these concepts to complex, real-world scenarios. This includes designing access controls, evaluating cryptographic solutions, and implementing security frameworks that align with organizational policies and compliance requirements. The certification reflects a commitment to continuous learning and the capacity to stay ahead of emerging threats in an increasingly complex cyber landscape.
The journey to becoming an ISSAP professional often begins with foundational experience in security architecture. Candidates typically need at least two years of relevant experience beyond holding the CISSP designation. This experience ensures that they have practical exposure to enterprise security challenges and are capable of translating theoretical concepts into actionable solutions. Furthermore, maintaining an excellent record within the CISSP framework is crucial, as it attests to the candidate’s adherence to ethical standards and professional integrity. These prerequisites underscore the rigorous nature of the CISSP-ISSAP certification and its role as a benchmark for elite security architecture expertise.
Beyond eligibility, the value of the certification lies in the strategic responsibilities that ISSAP professionals undertake. They are often tasked with evaluating emerging technologies and determining how these innovations can be integrated securely within existing infrastructures. This requires a meticulous understanding of both the technical specifications of systems and the organizational context in which they operate. For instance, the selection of network security solutions must consider not only encryption strength and intrusion detection capabilities but also compatibility with operational workflows, compliance mandates, and business objectives. Such multifaceted analysis highlights the complexity of the ISSAP role and the necessity for both analytical precision and creative problem-solving.
Security architecture, as envisioned by ISSAP professionals, is not static; it is a dynamic, evolving framework designed to adapt to new threats, regulatory changes, and business transformations. This adaptability is critical because organizations operate in fluid environments where technological advancements, market pressures, and cyber adversities constantly reshape operational priorities. An effective security architect must therefore anticipate potential disruptions and design mechanisms that are both resilient and scalable. This forward-thinking approach distinguishes ISSAP professionals from conventional security practitioners, emphasizing their strategic contribution to organizational stability and growth.
In practice, the responsibilities of an ISSAP-certified architect extend to a broad array of activities. They perform comprehensive risk assessments, mapping potential threats to business processes and determining appropriate mitigation strategies. They evaluate physical security controls, ensuring that access to sensitive areas and systems is restricted and monitored effectively. They design cryptographic protocols to safeguard data integrity and confidentiality while balancing the practicalities of performance and usability. Moreover, they establish procedures for incident detection, response, and recovery, ensuring that organizational assets remain protected in the event of security breaches.
An ISSAP professional’s expertise is also instrumental in governance and compliance initiatives. Organizations must navigate a complex landscape of regulatory frameworks, industry standards, and contractual obligations. The architect’s role includes interpreting these requirements, assessing organizational adherence, and recommending enhancements to policies and controls. In doing so, they help organizations not only avoid penalties and reputational damage but also instill a culture of security awareness and proactive risk management.
Another critical facet of the ISSAP role is communication. Effective security architecture demands that technical recommendations are translated into language that management, stakeholders, and other teams can understand and act upon. This requires exceptional analytical and interpersonal skills, as well as the ability to construct persuasive arguments that justify investments in security infrastructure. The ISSAP-certified professional must bridge the gap between technical intricacies and strategic imperatives, ensuring that security initiatives receive the support and resources necessary for successful implementation.
The value of the CISSP-ISSAP certification extends beyond immediate organizational impact. It represents a career milestone, reflecting a practitioner’s depth of knowledge, ethical standards, and leadership potential. ISSAP-certified architects often ascend to senior roles within information security, influencing policy, guiding enterprise-wide initiatives, and mentoring future security leaders. The credential signals a commitment to excellence and a readiness to engage with the most complex challenges in cybersecurity.
Furthermore, the certification carries an implicit promise of mastery in areas such as identity and access management, application security, security operations architecture, and infrastructure security architecture. Mastery in these domains is critical in an era where cyber threats are increasingly sophisticated, and the cost of breaches can be catastrophic. By demonstrating proficiency across these dimensions, ISSAP professionals ensure that organizations are equipped to prevent, detect, and respond to security incidents effectively.
From a professional development perspective, the pursuit of CISSP-ISSAP certification fosters a mindset of continual learning. Candidates immerse themselves in case studies, best practices, and emerging research to understand the nuances of advanced security architecture. They engage with simulations and practice scenarios that mirror real-world challenges, refining their problem-solving and decision-making abilities. This rigorous preparation cultivates both confidence and competence, equipping architects to navigate complex security landscapes with agility and foresight.
In essence, the CISSP-ISSAP certification is not merely an accolade; it is a transformative journey. It shapes practitioners into architects of security resilience, combining technical proficiency, strategic vision, and leadership capabilities. Organizations benefit from professionals who can craft cohesive security architectures, anticipate emerging threats, and guide risk-based decision-making processes. For individuals, it offers recognition, career advancement, and the satisfaction of contributing meaningfully to organizational security and stability.
Understanding Who Should Pursue CISSP-ISSAP Certification
In the intricate domain of information security, the pursuit of advanced credentials serves as both a marker of expertise and a conduit for career elevation. The CISSP-ISSAP certification represents one such pinnacle, tailored for professionals who not only possess a foundational understanding of cybersecurity but also demonstrate an aptitude for architectural design, risk assessment, and strategic oversight. The individuals most suited for this certification are those who have accumulated substantial experience in network security and information systems, particularly in roles that demand analytical thinking, problem-solving, and the integration of security solutions with organizational objectives.
Candidates pursuing this credential typically bring with them a minimum of two years of experience specifically in security architecture. This requirement ensures that aspirants have engaged with the multifaceted realities of designing and implementing secure frameworks, rather than merely administering existing systems. The practical exposure gained from these experiences is crucial, as it equips candidates with the ability to evaluate organizational risks, align security solutions with business objectives, and anticipate potential vulnerabilities that may emerge in complex technological environments. Beyond mere technical proficiency, the ideal candidate also demonstrates a keen understanding of governance, compliance, and risk management, embodying the strategic insight required to influence decision-making at higher organizational tiers.
Equally essential is the prerequisite of holding an active CISSP certification with an exemplary record. This ensures that candidates have already demonstrated comprehensive knowledge of information security principles and adhere to professional ethical standards. The combination of practical experience and formal credentialing underscores the rigorous expectations associated with the ISSAP designation, positioning successful candidates as trusted authorities within the field of information security architecture.
The eligibility criteria also underscore a broader philosophy of professional development. Candidates are expected to exhibit not only technical expertise but also strategic foresight and the capacity to operate within a complex organizational ecosystem. They must be capable of translating technical concepts into actionable strategies that align with an organization’s mission and vision, integrating security architecture seamlessly with overarching business objectives. In this sense, the CISSP-ISSAP credential represents a confluence of knowledge, experience, and leadership potential, signifying a practitioner’s readiness to engage with the most sophisticated challenges in cybersecurity.
Prerequisites and Experience Requirements
The path toward earning the CISSP-ISSAP certification is deliberately designed to ensure that candidates possess the depth of knowledge and practical experience necessary to function effectively in high-level security roles. Central to this is the requirement for a minimum of two years of architecture-specific experience. This encompasses exposure to designing, implementing, and evaluating security frameworks that address organizational risks while supporting operational goals. Candidates should have participated in projects involving network security design, cryptography implementation, access control systems, and business continuity planning. Such experience provides a foundation for understanding how security architecture interplays with organizational policies, compliance mandates, and emerging technological trends.
In addition to hands-on experience, aspirants must maintain an unblemished record as a CISSP professional. This prerequisite is indicative of the ethical rigor and professional integrity that ISSAP-certified architects are expected to embody. Ethical conduct is paramount in the field of information security, as architects frequently handle sensitive data, manage critical infrastructure, and make decisions with profound organizational implications. The emphasis on a clean CISSP record reinforces the notion that technical skill alone is insufficient; moral and professional standards are integral to the responsibilities of an advanced security architect.
Beyond formal requirements, candidates are encouraged to cultivate a holistic understanding of security architecture principles. This includes familiarity with risk management methodologies, governance frameworks, cryptographic protocols, identity and access management strategies, and infrastructure security considerations. Practical exposure to these areas enables candidates to navigate complex scenarios where technical decisions intersect with business priorities. For example, implementing a robust access control system requires not only understanding authentication protocols but also assessing organizational workflows, regulatory constraints, and potential operational disruptions. Mastery of these nuances is essential for those seeking the CISSP-ISSAP credential.
Career Advantages of CISSP-ISSAP Certification
The acquisition of the CISSP-ISSAP credential confers a multitude of career advantages, reflecting both the technical depth and strategic significance of the qualification. Foremost among these benefits is enhanced professional recognition. Organizations increasingly value security professionals who possess a comprehensive understanding of information architecture and the ability to align security measures with business imperatives. Holding this certification signals to employers that the individual is capable of designing, analyzing, and implementing sophisticated security frameworks, thereby elevating their stature within the organization and the broader cybersecurity community.
ISSAP-certified professionals often assume pivotal roles in enterprise security initiatives. They are entrusted with responsibilities that encompass both tactical and strategic dimensions, including evaluating emerging technologies, designing security architectures, managing risk assessments, and ensuring regulatory compliance. Their insights influence critical decisions regarding technology investments, security policies, and organizational resilience. By virtue of this expertise, these professionals frequently occupy leadership positions, guiding teams and mentoring junior security staff in the art and science of architecture-driven security.
Another salient advantage is the expansion of career mobility and opportunity. The CISSP-ISSAP certification is recognized globally as a benchmark of advanced knowledge in information security architecture. This recognition opens doors to senior roles across diverse sectors, including finance, healthcare, government, and critical infrastructure. The credential serves as a differentiator in competitive markets, enabling professionals to secure positions that require both technical acumen and strategic insight. For organizations, this translates into access to highly capable security architects who can design resilient, future-proof security frameworks.
The certification also fosters professional growth by encouraging continual learning. The field of information security is in perpetual flux, shaped by emerging technologies, evolving threat landscapes, and shifting regulatory requirements. Maintaining ISSAP certification necessitates engagement with ongoing education, participation in professional development opportunities, and an awareness of the latest advancements in security architecture. This commitment to lifelong learning ensures that certified architects remain at the forefront of their field, capable of adapting to new challenges with agility and precision.
ISSAP-certified professionals contribute uniquely to the strategic direction of organizations. They play a central role in shaping governance frameworks, implementing risk-based security strategies, and evaluating technological innovations for organizational impact. Their capacity to synthesize complex technical information into actionable recommendations enhances organizational resilience and informs executive decision-making. This strategic positioning underscores the dual value of the certification: it recognizes technical expertise while simultaneously affirming leadership capabilities within the context of enterprise security.
In addition to strategic influence, CISSP-ISSAP certification enhances the practical effectiveness of professionals in their daily responsibilities. ISSAP architects are proficient in designing secure systems that withstand sophisticated attacks, implementing cryptographic protocols to protect sensitive data, and establishing business continuity plans to ensure operational stability. Their work reduces the likelihood of breaches, mitigates the impact of incidents, and supports the long-term sustainability of organizational operations. This practical impact reinforces the tangible benefits of certification, demonstrating value that extends beyond prestige to measurable improvements in security posture.
Furthermore, the certification equips professionals with the analytical skills necessary to navigate complex threat landscapes. ISSAP architects excel at assessing potential vulnerabilities, anticipating attack vectors, and developing proactive mitigation strategies. Their ability to interpret security incidents within a broader organizational context allows them to prioritize responses effectively, allocate resources efficiently, and communicate critical insights to stakeholders. This analytical acumen is invaluable in environments where rapid decision-making and precision are paramount, further solidifying the professional standing of ISSAP-certified individuals.
ISSAP certification also has implications for compensation and career trajectory. Professionals who hold this credential often command higher salaries and more senior positions compared to their non-certified peers. The combination of technical mastery, strategic insight, and leadership capability makes these individuals indispensable to organizations seeking to fortify their information security architecture. As cyber threats become increasingly sophisticated and pervasive, the demand for architects who can design resilient, compliant, and adaptive security frameworks continues to grow, enhancing the long-term career prospects of certified professionals.
The career advantages of CISSP-ISSAP certification extend to personal fulfillment and professional credibility. Achieving this credential represents the culmination of rigorous study, practical experience, and adherence to high ethical standards. It signifies a commitment to excellence in information security architecture and positions individuals as thought leaders in their field. The recognition garnered through this credential fosters confidence, encourages professional networking, and opens avenues for collaboration with other experts in cybersecurity, thereby expanding both influence and opportunity.
Beyond individual benefits, organizations also gain substantially from employing ISSAP-certified professionals. These architects provide critical guidance on aligning security initiatives with organizational objectives, integrating risk management practices into operational workflows, and implementing strategies that protect against evolving threats. Their expertise ensures that technology investments are judicious, security policies are robust, and incident response mechanisms are effective. By leveraging the skills of ISSAP-certified architects, organizations can achieve a resilient security posture that supports both innovation and operational continuity.
Ultimately, the eligibility, prerequisites, and career advantages of CISSP-ISSAP certification converge to create a pathway for highly skilled professionals to exert meaningful influence within the field of information security. The rigorous requirements ensure that only those with substantial experience, proven ethical standards, and strategic insight attain this credential. In turn, the certification provides recognition, career advancement, and professional growth opportunities, enabling architects to shape the security posture of organizations at the highest levels. By combining technical mastery with strategic vision, ISSAP-certified professionals occupy a critical nexus in cybersecurity, contributing both to the protection of organizational assets and to the evolution of security architecture as a discipline.
CISSP-ISSAP Domains and Their Role in Building Resilient Information Security Architecture
The realm of information security architecture is not merely a technical construct but a sophisticated orchestration of strategy, governance, and pragmatic design. Within the CISSP-ISSAP certification, each domain forms an integral pillar in the edifice of enterprise security, binding policy, technology, and operational intelligence into a coherent framework. To master this domain of expertise is to acquire the vision of an architect who can translate abstract security principles into tangible, operational resilience.
The architecture envisioned under CISSP-ISSAP is not confined to digital frameworks alone. It embodies a symbiotic relationship between governance, compliance, risk assessment, infrastructure, identity management, and operational continuity. Each area of mastery signifies an essential facet of the architect’s mind, harmonizing regulatory adherence with dynamic technological evolution.
Governance, Compliance, and Risk Management
Every formidable security structure begins with governance. It is the invisible compass directing all strategic decisions, ensuring that an organization’s mission and regulatory obligations align with its operational goals. Governance defines the ethical and procedural skeleton of information security, establishing policies, directives, and standards that form the basis for secure enterprise architecture.
Compliance amplifies this governance by tethering it to statutory, contractual, and ethical obligations. Whether adhering to frameworks like ISO 27001, NIST, or GDPR, compliance ensures that an organization’s digital fabric withstands the scrutiny of regulators and partners alike. For an ISSAP-certified professional, understanding compliance is not about checklists but about embedding these regulations into the architectural DNA of the enterprise.
Risk management, in this context, is both an art and a discipline. It requires the foresight to predict potential vulnerabilities before they manifest and the analytical acuity to measure and mitigate their impact. The ISSAP professional cultivates a perspective that perceives risk as a living entity—mutable, unpredictable, yet controllable through deliberate assessment and control. From identifying external threats to quantifying internal weaknesses, risk management allows the architect to balance protection and productivity with precision.
Security Architecture Modeling
Security architecture modeling represents the intellectual core of the ISSAP framework. It is here that abstract theories evolve into structured, logical models guiding system design. The architect operates within frameworks such as SABSA, TOGAF, or Zachman—not as mere followers but as designers tailoring these methodologies to fit organizational context.
This modeling process demands a holistic comprehension of business strategy and technical constraints. It integrates confidentiality, integrity, and availability principles into a structural design that is both scalable and adaptable. An adept security architect visualizes how each element interacts—networks, endpoints, users, and data—and then maps these interactions to enforce security at every juncture.
Modeling also embodies predictive architecture—designing not only for the present but for future contingencies. It involves the intricate art of foreseeing how emerging technologies, like zero-trust frameworks or quantum-resistant algorithms, will reshape enterprise defenses. For an ISSAP expert, architecture modeling is not static documentation; it is a living schematic that evolves in tandem with technological metamorphosis.
Infrastructure Security Architecture
Infrastructure forms the operational foundation upon which all enterprise activities depend. To secure this layer is to fortify the nervous system of the digital organization. Infrastructure security architecture focuses on integrating hardware, software, network, and physical components into a secure, cohesive system that functions with both agility and dependability.
The ISSAP professional perceives the infrastructure not as isolated devices but as interconnected nodes forming a complex digital ecosystem. This perspective demands a granular understanding of routing, firewalls, virtualization, segmentation, and encryption. Beyond these technicalities lies the critical role of redundancy and fault tolerance—ensuring that systems remain operational even in the wake of disruption or compromise.
In practical terms, infrastructure security architecture mandates designing secure data centers, implementing robust disaster recovery mechanisms, and employing layered defenses across hybrid environments. Whether dealing with on-premises assets or cloud-native deployments, the architect ensures seamless coexistence between innovation and security. A misconfigured firewall or weak encryption standard could cascade into catastrophic compromise, and hence, each decision is weighed with analytical precision and foresight.
The concept of defense-in-depth resonates profoundly within this domain. It is not merely about multiple layers of control but about the intelligent orchestration of these layers to counteract advanced threats. ISSAP professionals excel in designing architectures that anticipate failure modes, minimize attack surfaces, and sustain operational resilience even amid complex cyber aggressions.
Identity and Access Management Architecture
Identity is the cornerstone of digital trust. Without reliable mechanisms to authenticate and authorize users, even the most fortified networks crumble under the weight of unauthorized access. The ISSAP-certified expert masters identity and access management (IAM) as a discipline that intertwines human behavior, cryptographic assurance, and system interoperability.
IAM architecture encompasses the design and governance of policies ensuring that the right individuals gain the right access at the right time. This involves crafting frameworks for user provisioning, single sign-on, federation, and privileged access management. The architect must balance convenience with control—granting legitimate access without opening gateways to potential exploitation.
Modern IAM extends beyond conventional credentials, embracing adaptive authentication, behavioral analytics, and biometric verification. The ISSAP professional leverages these technologies to develop architectures that evolve dynamically with user context and threat intelligence. The architect’s acumen lies not only in deploying tools but in sculpting an identity ecosystem where authentication processes are seamless, yet uncompromising in their rigor.
Furthermore, identity federation and decentralized identity models add another dimension to IAM design. These allow interoperability across enterprises while maintaining sovereignty over credentials. The ISSAP architect thus becomes a guardian of digital identity integrity, ensuring continuity of trust across distributed systems and multi-cloud environments.
Application Security Architecture
Applications form the most visible layer of enterprise interaction and, consequently, one of the most exploited. Application security architecture under the ISSAP framework involves embedding security from the earliest stages of software conception through deployment and maintenance. It transcends reactive patching and advocates for proactive design strategies that immunize software ecosystems against threats.
At its essence, application security architecture merges development methodologies like DevSecOps with design principles that mitigate vulnerabilities at the source. It involves establishing secure coding practices, integrating automated vulnerability scanning, and enforcing rigorous testing across development lifecycles.
The ISSAP architect engages deeply with concepts like input validation, session management, encryption of sensitive data, and secure API design. The goal is to ensure that every function, interface, and data exchange adheres to the principles of least privilege and controlled exposure.
In contemporary architectures, applications no longer exist in isolation. They interact within distributed environments powered by microservices and containerized platforms. This complexity necessitates an architecture that not only safeguards individual components but also governs their intercommunication. The ISSAP expert constructs blueprints where each application component is resilient, observable, and compliant with the overarching security strategy.
Security Operations Architecture
Security operations architecture represents the synthesis of vigilance and response. It is the embodiment of operational discipline ensuring that the designed systems function securely in perpetuity. The ISSAP-certified professional views operations not merely as maintenance but as a dynamic continuum of monitoring, detection, analysis, and improvement.
This architecture integrates tools and processes that enable real-time visibility into system behaviors—security information and event management systems, intrusion detection frameworks, and threat intelligence platforms. However, technology alone is insufficient. The architecture must also include well-defined processes and human workflows that ensure timely and effective incident handling.
An ISSAP expert designs operations that reflect the philosophy of continuous assurance. From establishing baselines of normal behavior to developing automated response mechanisms, every operational decision enhances resilience. In such architecture, feedback loops are integral—insights from incidents feed into redesigning and fortifying the system, creating a cycle of perpetual improvement.
Security operations architecture also intersects with business continuity and disaster recovery. The ISSAP architect ensures that operational security sustains the enterprise’s ability to function even during crises. This involves meticulous planning for redundancy, failover strategies, and post-incident restoration protocols.
Moreover, as organizations embrace automation and artificial intelligence, operations must adapt to new paradigms. The ISSAP professional evaluates the implications of autonomous decision-making within security frameworks, ensuring accountability and ethical oversight remain intact even as systems gain cognitive autonomy.
Through a symphony of governance, modeling, infrastructure protection, identity management, application integrity, and operational sustainability, the CISSP-ISSAP domains collectively define the architecture of digital fortitude. Each element interlocks with the other, forming an unbroken chain of defense, adaptability, and foresight that empowers organizations to navigate the volatile landscape of modern cybersecurity with confidence and composure.
CISSP-ISSAP Examination Structure and Skills Measured in Information Security Architecture
The CISSP-ISSAP certification stands as one of the most esteemed validations of expertise in information security architecture, blending technical proficiency with strategic foresight. The certification is not merely a test of memory or procedural recall; rather, it is an intricate assessment of analytical dexterity, design philosophy, and the capacity to align security architecture with complex organizational goals. Within its structure lies an evaluation of both conceptual mastery and practical wisdom, ensuring that those who hold this credential can translate theoretical principles into coherent, functional, and adaptive security architectures.
The CISSP-ISSAP examination encapsulates the essence of architectural thinking within cybersecurity. It evaluates an individual’s ability to perceive information systems as dynamic ecosystems—each component interacting with others under the influence of regulatory, operational, and technical constraints. This perspective distinguishes the ISSAP credential from traditional security certifications. While many emphasize implementation, ISSAP focuses on architecture: the art and science of designing frameworks that harmonize security mechanisms with enterprise aspirations.
The exam is designed to assess not only one’s technical breadth but also strategic integration. It ensures that the candidate can identify systemic vulnerabilities, design resilient architectures, and incorporate governance principles within real-world environments. The examination process itself mirrors the architectural discipline it represents—structured, layered, and demanding a synthesis of intellect and experience.
Understanding the Structure and Purpose of the Examination
The CISSP-ISSAP examination operates as a rigorous evaluation of the candidate’s ability to architect and govern enterprise-level security environments. The test consists of multiple-choice and scenario-based questions that compel candidates to analyze, infer, and decide rather than recall static facts. It spans approximately three hours, demanding both precision and endurance. The total number of questions typically ranges near 125, and these are designed to probe various facets of architectural intelligence—ranging from governance frameworks to applied cryptography and risk-based decision-making.
The scoring model reflects a global standard of competence. Candidates must achieve a minimum scaled score of 700 out of 1000, indicating a deep comprehension of both theory and applied methodology. The exam is conducted in a computer-based format through authorized testing centers, ensuring uniformity, security, and accessibility for professionals worldwide. The fee for attempting the CISSP-ISSAP examination is substantial, symbolizing the premium nature of this credential and the level of proficiency it expects from candidates.
The structure of the exam is not random; it follows a deliberate pattern that mirrors the architecture of security domains it assesses. Each domain contributes a specific proportion to the total evaluation, representing its relative significance within the broader architectural discipline. Candidates are expected to interlink concepts seamlessly, as questions often traverse multiple domains simultaneously. This integrated approach ensures that only those with holistic understanding—rather than fragmented technical knowledge—can succeed.
The examination also emphasizes contextual reasoning. Many of its scenarios present ambiguous, multifaceted situations requiring architects to prioritize objectives, balance competing requirements, and make judgments rooted in both business logic and security rationale. For instance, a candidate may be asked to design a secure architecture for a hybrid enterprise system balancing confidentiality with performance optimization. The correct response demands not only technical precision but strategic discernment.
Core Competencies and Skills Assessed
The CISSP-ISSAP exam is a profound evaluation of architectural acumen, demanding mastery over both foundational and advanced security concepts. The primary skills measured can be delineated into thematic competencies, each reflecting an indispensable aspect of enterprise security design and governance.
Designing Security Architectures
At the heart of ISSAP lies the ability to design comprehensive, scalable, and adaptable security architectures. This competency examines the candidate’s understanding of how business objectives and risk appetite influence design choices. It evaluates whether the architect can integrate principles of confidentiality, integrity, and availability into an ecosystem that balances innovation with protection.
The architect must demonstrate proficiency in defining security domains, delineating trust boundaries, and identifying dependencies across systems. Moreover, this skill involves determining which controls—technical, administrative, or physical—are best suited to mitigate specific risks. The ability to design with foresight, anticipating emerging threats and technological evolutions, is paramount.
In practice, this may manifest as crafting architectures for distributed systems, securing virtual environments, or designing adaptive frameworks for organizations undergoing digital transformation. The ISSAP-certified professional must exhibit the dexterity to harmonize architecture with organizational identity, ensuring that each component supports strategic objectives while maintaining compliance with internal and external mandates.
Implementing and Evaluating Physical Security Controls
Though often underestimated in the digital age, physical security remains a vital component of comprehensive security architecture. The CISSP-ISSAP examination underscores the necessity of integrating physical safeguards with logical and procedural defenses. Candidates are evaluated on their understanding of access control mechanisms, environmental protections, and facility design considerations that contribute to overall system resilience.
This competency examines the architect’s ability to align physical security mechanisms—such as surveillance systems, biometric access, secure perimeters, and redundancy facilities—with digital safeguards. The emphasis lies on ensuring that physical vulnerabilities do not compromise information assets. For instance, a secure data center must account for not only network firewalls but also power continuity, environmental regulation, and restricted physical access.
An ISSAP architect approaches physical security as a fundamental stratum of defense, harmonizing it with identity management, encryption policies, and operational resilience. In the exam, this understanding is reflected in scenario-based questions requiring the candidate to design or assess physical security elements within a broader architectural context.
Applying Cryptography and Secure Communication Principles
Cryptography stands as one of the most sophisticated disciplines within cybersecurity, and its integration into architecture design is both a science and an art. The ISSAP examination assesses the candidate’s ability to apply cryptographic techniques judiciously across systems and data flows. Rather than testing memorization of algorithms, the exam probes the understanding of when and why specific cryptographic mechanisms should be employed.
Candidates must demonstrate an understanding of encryption lifecycle management, key distribution protocols, and secure channel design. This skill set extends beyond technical configuration to encompass governance—ensuring that cryptographic practices comply with regulatory standards and align with business risk profiles.
Furthermore, the examination explores concepts such as public key infrastructure, certificate management, and the application of quantum-resistant cryptography in emerging architectures. The ISSAP architect must discern how to balance performance, scalability, and confidentiality without overcomplicating system design.
In essence, this competency measures the candidate’s ability to integrate cryptography as an enabler of trust, ensuring that security mechanisms facilitate, rather than impede, organizational efficiency.
Recognizing Threats and Designing Countermeasures
The dynamic landscape of cyber threats requires architects to evolve beyond reactive defense mechanisms. The CISSP-ISSAP examination measures the ability to identify, classify, and mitigate threats through design-oriented solutions. This demands a profound understanding of threat intelligence, attack vectors, and the interplay between human and technological vulnerabilities.
Candidates are assessed on their ability to recognize patterns of intrusion and correlate them with architectural weaknesses. The goal is to ensure that an ISSAP-certified professional can design systems inherently resilient against exploitation, rather than dependent solely on reactive monitoring tools.
For instance, the architect might be evaluated on designing architectures resilient against supply-chain attacks, insider threats, or advanced persistent threats. This involves employing layered defenses, segregation of duties, anomaly detection mechanisms, and resilient network segmentation. The exam measures not just knowledge of tools but strategic design thinking—anticipating how adversaries exploit complexity and countering such exploits through simplicity and control.
Applying Access Control Methodologies
Access control represents the ethical and procedural nexus of architecture—where principles of least privilege, need-to-know, and accountability converge. The CISSP-ISSAP exam evaluates a candidate’s proficiency in designing, implementing, and managing access control systems that ensure both usability and protection.
This encompasses discretionary, mandatory, and role-based access control methodologies, along with modern paradigms such as attribute-based and risk-adaptive access controls. The architect must understand how to translate organizational hierarchies, trust models, and compliance requirements into coherent access frameworks.
In the examination context, candidates are often presented with case-based questions requiring them to reconcile conflicting priorities: granting flexibility to users while preventing privilege escalation. They must demonstrate the intellectual agility to construct systems that remain functional without compromising security or governance integrity.
Access control also intersects with identity management and cryptography. The ISSAP-certified architect must appreciate these interdependencies and design cohesive solutions that support scalability, interoperability, and transparency.
Integrating and Monitoring Security Products
An essential skill assessed within the CISSP-ISSAP framework is the ability to integrate and oversee diverse security tools into a unified architecture. Modern enterprises utilize an array of products—firewalls, intrusion detection systems, endpoint protection, data loss prevention, and encryption gateways. The architect’s challenge lies in orchestrating these components to operate synergistically rather than as isolated silos.
The examination gauges whether the candidate can evaluate tool efficacy, align functionalities with organizational needs, and ensure continuous monitoring without overburdening system performance. It also assesses understanding of interoperability standards, automation frameworks, and centralized visibility mechanisms like security information and event management platforms.
This competency emphasizes adaptability—the capacity to evolve architectures as technologies and threats advance. The ISSAP professional must exhibit a visionary grasp of integration strategies, ensuring that each tool contributes to a unified, coherent defense ecosystem.
Designing for Operational Continuity and Resilience
Another critical dimension of the CISSP-ISSAP examination is the architect’s ability to design systems that endure adversity. Business continuity, disaster recovery, and operational resilience are not peripheral considerations but core architectural imperatives. The exam measures an individual’s ability to design infrastructures that sustain critical functions under duress, recover swiftly from disruption, and adapt to changing threat landscapes.
Candidates must demonstrate understanding of redundancy planning, failover strategies, and data replication mechanisms. The architect’s role extends beyond technical recovery—it encompasses strategic foresight, ensuring that continuity plans align with organizational mission and risk tolerance.
Furthermore, resilience is assessed in terms of adaptability: the capacity to reconfigure architectures dynamically as new technologies and threats emerge. The ISSAP-certified professional must design with elasticity, embedding self-healing and adaptive capabilities into system architecture.
Strategic Governance and Architectural Ethics
Embedded within every ISSAP assessment lies the subtle evaluation of governance and ethics. Security architects operate at the intersection of technology and morality, making decisions that affect privacy, transparency, and trust. The exam subtly probes the candidate’s understanding of ethical principles governing architecture—ensuring accountability, preventing abuse of privilege, and maintaining the integrity of information systems.
Governance, in this context, involves developing policies that regulate design, implementation, and operational processes. The ISSAP candidate must demonstrate comprehension of regulatory compliance, auditability, and policy alignment. This skill set requires the capacity to bridge communication between technical teams and executive leadership, translating complex security postures into strategic imperatives comprehensible to non-technical stakeholders.
Ultimately, the governance dimension reinforces that architecture is not solely technical craftsmanship but an embodiment of institutional ethics and responsibility.
Through its exhaustive evaluation process, the CISSP-ISSAP examination identifies those rare professionals who can merge analytical intelligence with ethical stewardship. It measures how candidates envision, design, and safeguard the future of digital enterprises—fortifying structures not just against today’s adversities but also tomorrow’s uncertainties. Every question within the examination echoes the philosophy that architecture is not a static construct but an evolving symphony of governance, resilience, and human ingenuity.
Study Resources and Effective Preparation Strategies for CISSP-ISSAP Certification
Preparation for the CISSP-ISSAP certification demands far more than rote learning or mechanical memorization; it requires an intellectual immersion into the philosophy and mechanics of security architecture. The process is a synthesis of comprehension, analysis, and application, where the aspirant cultivates both technical sagacity and strategic vision. Success in this certification lies in the ability to harmonize deep theoretical understanding with practical reasoning, transforming scattered knowledge into cohesive architectural mastery.
The CISSP-ISSAP aspirant must approach preparation as an architect approaches design—methodically, with precision and contemplation. Every concept studied should be perceived as a building block contributing to the grand structure of information security architecture. The journey to mastering this discipline involves utilizing diverse study materials, integrating structured learning methodologies, and nurturing a mindset anchored in perseverance and adaptability.
Effective preparation for CISSP-ISSAP certification can be imagined as constructing a vast edifice of knowledge—each domain forming an essential pillar supporting the integrity of the entire framework. Governance, risk management, identity, application security, infrastructure design, and operations are not isolated topics; they are interconnected systems whose comprehension demands holistic thinking. The learner must therefore navigate across conceptual boundaries, perceiving how decisions in one area influence the equilibrium of another.
Developing a Study Framework Anchored in Strategic Planning
The cornerstone of successful preparation lies in developing a structured study plan aligned with personal learning pace and professional obligations. Before delving into resources or reference materials, candidates should conduct a self-assessment to identify strengths and weaknesses across the CISSP-ISSAP domains. This introspection assists in prioritizing study efforts and preventing the inefficient distribution of time.
A comprehensive study schedule typically spans several months, divided into progressive cycles of learning, revision, and evaluation. During the initial cycle, candidates focus on conceptual clarity—understanding key principles, definitions, and theoretical constructs. The second cycle emphasizes application, exploring how these concepts manifest in real-world scenarios. The final cycle involves extensive practice, where simulated exams and analytical exercises test both knowledge retention and critical reasoning.
Consistency is more valuable than intensity. Studying smaller portions daily ensures deeper retention compared to sporadic, exhaustive sessions. Each study session should end with reflective analysis—summarizing learned concepts in one’s own words to ensure internalization rather than memorization. Writing personal summaries transforms passive reading into active comprehension.
Strategic planning also involves setting measurable milestones. For instance, completing the study of governance and compliance architecture within a specified timeframe, followed by a self-assessment quiz, ensures steady progress. This disciplined methodology mirrors the systematic nature of security architecture itself, reinforcing the habits of analytical organization and structured reasoning that the ISSAP credential demands.
Utilizing Authoritative Study Resources
The foundation of effective CISSP-ISSAP preparation rests on the careful selection of study materials that align with the exam’s objectives and contemporary security practices. Among the most authoritative resources is the official (ISC)² ISSAP study guide, which delineates every domain with clarity and precision. This guide, written by seasoned professionals, provides an in-depth exploration of theoretical frameworks, security models, and case studies reflecting real organizational contexts.
Complementing the official guide are supplemental materials such as domain-specific textbooks, white papers, and research publications focusing on enterprise security architecture. Books on governance, cryptography, and infrastructure modeling enrich understanding by offering multiple perspectives on the same concept. Reading beyond the prescribed syllabus strengthens intellectual flexibility—an indispensable trait for security architects who must adapt designs to ever-evolving threats and technologies.
Peer-reviewed journals and academic research serve as valuable supplements for advanced learners seeking to explore emerging paradigms like zero-trust frameworks, post-quantum cryptography, and adaptive identity management systems. Engaging with these materials enhances analytical acuity and ensures the candidate’s knowledge remains contemporary and forward-looking.
In addition to written materials, digital learning platforms provide structured video lectures, webinars, and interactive modules guided by expert instructors. These formats allow visual and auditory reinforcement, catering to diverse learning styles. For candidates balancing professional responsibilities, on-demand learning modules offer flexibility without sacrificing depth.
However, a discerning learner must remain cautious of superficial resources or unverified summaries. The credibility and accuracy of study material directly affect conceptual clarity. Authentic sources, verified by security professionals or the certifying body, must always take precedence over unofficial interpretations.
Leveraging Practice Tests and Analytical Evaluation
A crucial element of CISSP-ISSAP preparation involves rigorous practice through mock exams and situational analyses. Practice tests serve a dual purpose: familiarizing candidates with the examination’s structure and timing, and exposing areas requiring deeper study. These simulated assessments replicate the complexity and nuance of the actual exam, compelling candidates to think critically under controlled time constraints.
While practicing, it is vital to treat each question as an analytical exercise rather than a mere test of recall. The ISSAP exam prioritizes conceptual synthesis—how an architect integrates diverse principles to design effective solutions. Therefore, after completing practice questions, candidates should analyze not only why an answer is correct but also why alternatives are incorrect. This analytical reflection transforms testing into an active learning process, refining both reasoning and decision-making capabilities.
Many aspirants benefit from maintaining a detailed log of mistakes encountered during practice tests. By categorizing errors—whether conceptual, interpretive, or procedural—one can identify recurring patterns and address them systematically. This iterative correction process strengthens long-term understanding and improves exam performance.
Timed tests are especially effective in developing endurance and mental agility. The ability to manage time judiciously across 125 complex questions within three hours demands both intellectual composure and strategic pacing. Candidates must practice transitioning fluidly between analytical reasoning and decisive action—skills that mirror the rapid decision-making environment of real-world security architecture.
The Role of Conceptual Reinforcement and Visual Mapping
Complex architectural principles are often better retained through visualization. Creating conceptual diagrams, process flows, and mind maps transforms abstract theories into tangible structures. These visual tools allow candidates to perceive interconnections between domains and observe how security elements coalesce into unified systems.
For example, a mind map linking governance, risk management, and compliance illustrates their cyclical interdependence: governance establishes direction, risk management quantifies exposure, and compliance validates alignment. Similarly, visualizing data flows between application components aids comprehension of how identity management and encryption intersect within architecture.
Visual reinforcement also facilitates memory retention. The human mind recalls structured imagery more readily than disjointed text. By constructing visual frameworks, candidates convert isolated facts into meaningful patterns. Reviewing these maps before the exam serves as an efficient form of revision, condensing extensive material into manageable summaries.
Integrating Study Groups and Professional Communities
Collaborative learning amplifies understanding by exposing candidates to diverse viewpoints and problem-solving methodologies. Participating in study groups allows discussions that clarify ambiguities, reinforce complex concepts, and encourage accountability. Through dialogue, candidates exchange practical experiences, comparing architectural solutions applied in different organizational contexts.
Engaging with professional cybersecurity communities further enriches preparation. Online forums, social media groups, and professional associations provide platforms where ISSAP aspirants and certified professionals interact. These communities often share insights about exam trends, evolving domain emphases, and real-world application of architectural principles.
Moreover, discussions within such communities foster the analytical thinking essential for success. By debating complex scenarios—such as designing secure cloud infrastructures or balancing usability with stringent access controls—participants sharpen their capacity for multidimensional reasoning. This collaborative discourse mimics the decision-making processes encountered in professional security architecture roles, thus enhancing both exam readiness and career competence.
Applying Real-World Scenarios and Case Study Analysis
The ISSAP examination values applied intelligence over abstract knowledge. To prepare effectively, candidates must ground their understanding in practical scenarios mirroring real-world architectural challenges. Studying case analyses—ranging from enterprise security breaches to successful architecture implementations—reveals the tangible implications of design decisions.
Candidates should dissect these cases meticulously, identifying the root causes of security failures and the architectural strategies that could have mitigated them. For instance, analyzing a data breach caused by inadequate segmentation reveals lessons about network design and risk prioritization. Conversely, studying successful implementations demonstrates how layered defenses, redundancy planning, and adaptive governance enhance enterprise resilience.
Many advanced learners simulate architectural problem-solving by designing hypothetical systems based on industry contexts such as finance, healthcare, or critical infrastructure. This exercise bridges theory and practice, compelling candidates to integrate multiple domains—governance, cryptography, access management, and operations—into cohesive architectures. Such experiential learning fosters the analytical fluidity that the ISSAP exam rewards.
Mastering Time Management and Mental Discipline
Time management during preparation and examination is both a science and an art. A well-structured study timeline ensures steady progress without cognitive exhaustion. Allocating specific durations for each domain, interspersed with short breaks, sustains focus and prevents burnout. Adhering to this schedule cultivates discipline—an indispensable trait for security architects who must maintain composure under operational pressure.
During the exam itself, candidates must balance thorough analysis with prompt decision-making. Spending excessive time on a single complex question can compromise the ability to address subsequent ones. A pragmatic approach involves marking challenging questions for later review and progressing through the test strategically.
Mental discipline also extends to psychological resilience. The breadth of ISSAP content can be intimidating, and anxiety can cloud rational thought. Techniques such as deep breathing, structured note-taking, and reflective pauses can stabilize focus during preparation and testing. Building confidence through consistent practice reinforces composure, enabling candidates to engage the exam with calm decisiveness.
Constructing Effective Study Notes and Revision Compendiums
Concise and well-organized study notes act as intellectual anchors throughout the preparation journey. After completing each domain, summarizing the material in one’s own phrasing ensures deeper internalization. These notes should capture core principles, architectural frameworks, and practical examples without overloading with redundant details.
A layered note-taking approach proves highly effective: initial notes capture comprehensive detail, while successive revisions distill information into key concepts. Eventually, the candidate should possess a compact compendium that encapsulates the essence of the ISSAP body of knowledge. Reviewing these condensed notes during the final stages of preparation reinforces long-term memory and supports quick recollection during the exam.
Color-coded annotations, mnemonic devices, and short reference charts can further enhance the usability of notes. For instance, associating governance principles with visual symbols or acronyms facilitates rapid recall. Over time, these visual and linguistic cues become embedded within memory, improving response efficiency during timed testing conditions.
Balancing Professional Experience with Theoretical Study
Many CISSP-ISSAP candidates are experienced security professionals, yet experience alone is insufficient to guarantee success. Practical exposure must be complemented by theoretical refinement. The certification’s rigor lies in its ability to test both dimensions simultaneously.
Candidates should leverage professional experience as a contextual lens for interpreting theoretical material. For instance, those working in infrastructure design can connect domain knowledge with governance principles or cryptographic strategies. Conversely, individuals from policy or compliance backgrounds can use study materials to strengthen their technical comprehension of architectures and protocols.
Real-world exposure provides invaluable insight into how theoretical constructs function within operational constraints. However, formal study ensures that these experiences align with global best practices and standardized architectural frameworks. By blending experience with structured study, candidates develop a multidimensional understanding reflective of true ISSAP proficiency.
Sustaining Motivation and Cognitive Stamina
The preparation journey for CISSP-ISSAP can be intellectually demanding and extended over several months. Sustaining motivation requires both intrinsic commitment and extrinsic reinforcement. Setting progressive goals and rewarding their completion maintains momentum. Reflecting regularly on personal progress and future aspirations reminds the candidate of the broader purpose behind certification—career advancement, intellectual mastery, and professional distinction.
Equally vital is maintaining cognitive stamina. Prolonged study without sufficient rest diminishes comprehension and retention. Regular intervals of rest, balanced nutrition, and physical exercise contribute to mental sharpness and resilience. Adopting mindfulness practices or meditative techniques can further enhance concentration and clarity during intense study periods.
Preparation should never devolve into monotonous repetition. Introducing variety—such as alternating between reading, visualization, discussion, and practice tests—stimulates the mind and prevents fatigue. Learning thrives on diversity, and variation in study methods sustains curiosity throughout the journey.
The CISSP-ISSAP certification represents the zenith of intellectual and professional refinement in information security architecture. To prepare for it effectively is to embrace a process of transformation—cultivating not only knowledge but discernment, endurance, and adaptability. The candidate who approaches preparation with strategic rigor, disciplined study, and reflective insight emerges not merely as an exam passer but as a true architect of secure, resilient digital ecosystems.
The Strategic Impact of CISSP-ISSAP Professionals in Modern Information Security Architecture
The evolution of the digital ecosystem has transformed how organizations perceive and execute information security. The world has moved far beyond the era where isolated defensive measures sufficed to protect enterprise systems. Today’s enterprises demand architectures that are both strategic and adaptive, balancing regulatory compliance, operational fluidity, and technological innovation. Within this intricate landscape, professionals holding the CISSP-ISSAP certification emerge as the intellectual vanguards who synthesize governance, technology, and foresight into resilient frameworks of protection. Their strategic influence extends across every dimension of enterprise operations—from design ideation and policy formulation to implementation oversight and continuous optimization.
CISSP-ISSAP professionals do not merely manage security systems; they engineer the very foundation upon which organizational integrity and digital trust are constructed. Their expertise extends beyond the technical horizon, encompassing business strategy, organizational psychology, and risk economics. In a world where cyber resilience defines corporate survival, their contributions carry both operational and existential significance. They embody the union of analytical precision and visionary thinking, transforming abstract policies into living architectures that sustain enterprise continuity.
The Strategic Role of CISSP-ISSAP Architects in Enterprise Environments
The presence of a CISSP-ISSAP-certified professional within an enterprise signals a commitment to architectural intelligence—a recognition that information security must be embedded into every operational layer. These professionals function as architects of security strategy, bridging executive intent with technical execution. Their capacity to interpret organizational objectives and translate them into enforceable security architectures gives them an indispensable role in corporate governance.
Unlike traditional cybersecurity practitioners who focus primarily on defense mechanisms, the ISSAP expert crafts holistic frameworks that predict vulnerabilities before they materialize. This predictive capability stems from a profound understanding of risk management and the interplay between business processes, data flows, and technological dependencies. Their architectural designs are guided by both theoretical foundations and empirical experience, ensuring that security mechanisms enhance rather than hinder organizational performance.
They participate directly in strategic decision-making, advising leadership on policy direction, investment priorities, and compliance trajectories. By evaluating emerging technologies and mapping them against regulatory landscapes, they enable informed decisions that preserve organizational agility without compromising security. Their influence is particularly pronounced in industries where confidentiality, integrity, and availability are non-negotiable, such as finance, healthcare, defense, and telecommunications.
Moreover, CISSP-ISSAP architects possess the rare capability to communicate seamlessly across technical and executive domains. They articulate complex architectural paradigms in language that resonates with business leaders, fostering alignment between cybersecurity objectives and corporate strategy. This linguistic fluency transforms them into diplomatic intermediaries who reconcile the divergent priorities of innovation and regulation.
Leadership and Organizational Integration
Leadership in information security architecture extends beyond command; it involves orchestration. A CISSP-ISSAP professional operates as both a strategist and a conductor, ensuring that every subsystem of security—from network defense to identity management—functions in unison. They establish governance models that distribute accountability across teams while maintaining centralized oversight to ensure architectural cohesion.
Through the establishment of security architecture frameworks, they define the parameters within which organizational security evolves. These frameworks standardize policy implementation, facilitate cross-departmental collaboration, and ensure scalability as the enterprise grows. The ISSAP-certified professional ensures that governance does not become a rigid constraint but a living, adaptive structure capable of responding to evolving risks.
Their leadership also manifests in mentoring and capability development. By guiding security engineers, analysts, and compliance officers, they cultivate a culture of architectural awareness across the organization. This intellectual mentorship ensures continuity of expertise, allowing security principles to permeate through every operational layer.
They engage in continuous dialogue with senior management, advocating for resource allocation toward sustainable security initiatives. Their influence shapes budgetary planning, ensuring that investment in security is treated as an enabler of innovation rather than a reactive expense. Through this strategic advocacy, they transform organizational perspectives—shifting security from a technical necessity to a strategic advantage.
Architectural Innovation and Adaptive Design
One of the hallmarks of CISSP-ISSAP professionals lies in their capacity for innovation within the boundaries of security governance. They are the architects who design adaptive systems capable of withstanding both known and emergent threats. Their architectural thinking transcends static controls, favoring dynamic, modular designs that can evolve in response to environmental shifts.
In contemporary organizations, the convergence of cloud computing, artificial intelligence, and decentralized systems demands flexible architectural paradigms. The ISSAP expert integrates these technologies into secure configurations that preserve performance and scalability while maintaining compliance with stringent standards. They achieve equilibrium between agility and fortification—a balance that defines the essence of modern security architecture.
Their innovative mindset also encompasses foresight into technological disruption. For instance, as quantum computing threatens to redefine cryptographic paradigms, ISSAP professionals explore post-quantum algorithms and resilience strategies long before they become industry norms. This anticipatory approach ensures that organizations remain one step ahead of adversarial evolution.
In addition, they embrace automation and machine learning to optimize operational vigilance. By designing architectures that incorporate behavioral analytics, anomaly detection, and autonomous response systems, they reduce dependence on manual intervention while enhancing incident response efficiency. Their innovation is pragmatic—grounded in real-world feasibility yet visionary in scope.
Governance, Compliance, and Ethical Stewardship
The strategic significance of CISSP-ISSAP professionals extends deeply into the realm of governance and ethics. They recognize that information security is not merely a technological obligation but a moral imperative—an assurance of trust between organizations and their stakeholders. Governance, in their context, is not a bureaucratic ritual but an ethical framework that defines how power and responsibility are exercised in digital environments.
They design architectures that inherently embed compliance requirements, ensuring seamless alignment with international standards such as ISO 27001, NIST, and GDPR. Rather than treating compliance as an afterthought, they weave regulatory adherence into the architectural fabric of systems, minimizing risk while optimizing operational continuity. Their ability to interpret legal and regulatory language into actionable technical constructs is one of their defining competencies.
Equally vital is their commitment to ethical stewardship. They ensure that data handling practices respect privacy, transparency, and fairness. In the age of pervasive surveillance and algorithmic bias, their influence safeguards organizational integrity by promoting accountability and responsible innovation.
By developing policies that govern identity management, access control, and data retention, they establish a moral compass that guides the organization’s digital behavior. The ISSAP professional thus acts not only as a designer of secure systems but also as a custodian of ethical technology usage—ensuring that progress never compromises principle.
Enhancing Operational Resilience and Risk Intelligence
Operational resilience represents the true measure of an organization’s security maturity. The CISSP-ISSAP professional plays a decisive role in architecting systems that maintain functionality even under duress. They perceive resilience as more than redundancy; it is an architectural philosophy that ensures continuity through adaptability.
They develop frameworks that interlace disaster recovery, business continuity, and incident response into a cohesive model. This model ensures that organizational operations persist even in the presence of system compromise, natural disasters, or malicious attacks. Through architectural foresight, they anticipate potential points of failure and implement mechanisms that prevent cascading disruptions.
The ISSAP professional also refines risk intelligence—transforming risk data into actionable insights. They employ both quantitative and qualitative methodologies to assess vulnerabilities, prioritize mitigation strategies, and align them with organizational risk appetite. Their approach to risk is systemic, treating it as an inherent element of enterprise function rather than an external threat to be eliminated.
By cultivating a feedback-driven architecture, they ensure that lessons learned from incidents translate into continuous improvement. This cyclical process of assessment, adaptation, and reinforcement establishes an evolving state of readiness, positioning the organization to navigate uncertainty with confidence.
Strategic Influence on Business Transformation
As enterprises undergo digital transformation, CISSP-ISSAP professionals serve as strategic anchors ensuring that innovation unfolds within secure and controlled parameters. Their architectural expertise becomes pivotal when organizations migrate to hybrid cloud infrastructures, adopt Internet of Things ecosystems, or integrate artificial intelligence into decision-making processes.
In such transformations, they evaluate the interplay between technological ambition and security feasibility. They ensure that rapid innovation does not outpace control mechanisms, maintaining harmony between growth and governance. By defining architectural blueprints that support secure scalability, they enable organizations to innovate without jeopardizing data integrity or operational stability.
Their advisory role also extends to vendor management and third-party integrations. They assess external partners’ security postures, ensuring that supply chain interdependencies do not introduce systemic vulnerabilities. This vigilance reflects their comprehensive understanding of interconnected enterprise ecosystems, where a single weak node can compromise entire networks.
CISSP-ISSAP professionals thereby contribute directly to corporate sustainability. Their strategic oversight transforms cybersecurity into a facilitator of business evolution—creating trust in digital ecosystems, enhancing stakeholder confidence, and protecting brand reputation.
Cross-Disciplinary Collaboration and Knowledge Integration
The strategic efficacy of CISSP-ISSAP professionals is magnified through their ability to collaborate across diverse disciplines. They operate at the convergence of information technology, legal compliance, behavioral science, and management strategy. This multidisciplinary agility allows them to mediate between disparate teams, ensuring unity of purpose across organizational silos.
They engage with software developers to embed security into the software development lifecycle, collaborate with auditors to validate architectural compliance, and consult with executives to shape governance directives. This integrative capacity ensures that every operational and strategic initiative is underpinned by coherent architectural integrity.
Their influence also extends into education and awareness. Through structured training and knowledge dissemination, they elevate organizational literacy in cybersecurity principles. This empowerment of personnel transforms security from a specialized function into a collective responsibility, embedding resilience into corporate culture.
The integration of knowledge across disciplines also facilitates innovation. By understanding both the technological and human dimensions of security, CISSP-ISSAP professionals design systems that account for human error, behavioral tendencies, and organizational dynamics. This anthropotechnical approach enriches architectural design, rendering it both technically sound and psychologically attuned.
The Role of CISSP-ISSAP Professionals in Shaping the Future of Cybersecurity
The world of cybersecurity is evolving at an unprecedented pace, driven by technological convergence and adversarial sophistication. In this milieu, the CISSP-ISSAP professional stands as both architect and philosopher—bridging human ingenuity with technological fortitude. Their strategic impact transcends immediate operational defense, influencing the philosophical and ethical trajectory of information security as a discipline.
As organizations increasingly adopt intelligent automation, decentralized networks, and digital identity ecosystems, the role of architecture becomes more critical. The ISSAP professional’s capacity to design adaptive, intelligent, and resilient frameworks ensures that the core principles of security—confidentiality, integrity, and availability—remain inviolable amidst rapid transformation.
Their influence will also expand into global collaboration. As cybersecurity threats grow transnational, ISSAP architects will shape cross-border standards and cooperative defense frameworks. Their expertise will be pivotal in constructing architectures that transcend organizational boundaries, facilitating collective resilience across industries and nations.
In academia and research, they will continue to refine the theoretical foundations of information security architecture—bridging gaps between abstract frameworks and practical implementation. Their analytical contributions will inform policy, regulation, and industry best practices, ensuring that cybersecurity evolves not as a reactive measure but as a proactive discipline grounded in design excellence.
Conclusion
CISSP-ISSAP professionals represent the epitome of strategic and intellectual advancement in the realm of information security architecture. Their work transcends technical administration to embody visionary governance, ethical stewardship, and architectural innovation. They stand at the confluence of knowledge and foresight, shaping systems that not only defend but also empower organizations to thrive in a volatile digital landscape.
Their impact reverberates across dimensions—governance, risk management, compliance, infrastructure, and human behavior—unifying them under the umbrella of architectural coherence. Through their leadership, organizations achieve a delicate equilibrium between protection and performance, between regulation and creativity.
As digital infrastructures expand and threats evolve, the importance of such professionals grows exponentially. They are not merely custodians of information security; they are the architects of digital civilization itself—constructing frameworks of trust that uphold the integrity of the interconnected world. The CISSP-ISSAP certification thus symbolizes more than professional mastery; it embodies a covenant between intellect and responsibility, ensuring that the future of technology remains secure, ethical, and profoundly human.
Frequently Asked Questions
How can I get the products after purchase?
All products are available for download immediately from your Member's Area. Once you have made the payment, you will be transferred to Member's Area where you can login and download the products you have purchased to your computer.
How long can I use my product? Will it be valid forever?
Test-King products have a validity of 90 days from the date of purchase. This means that any updates to the products, including but not limited to new questions, or updates and changes by our editing team, will be automatically downloaded on to computer to make sure that you get latest exam prep materials during those 90 days.
Can I renew my product if when it's expired?
Yes, when the 90 days of your product validity are over, you have the option of renewing your expired products with a 30% discount. This can be done in your Member's Area.
Please note that you will not be able to use the product after it has expired if you don't renew it.
How often are the questions updated?
We always try to provide the latest pool of questions, Updates in the questions depend on the changes in actual pool of questions by different vendors. As soon as we know about the change in the exam question pool we try our best to update the products as fast as possible.
How many computers I can download Test-King software on?
You can download the Test-King products on the maximum number of 2 (two) computers or devices. If you need to use the software on more than two machines, you can purchase this option separately. Please email support@test-king.com if you need to use more than 5 (five) computers.
What is a PDF Version?
PDF Version is a pdf document of Questions & Answers product. The document file has standart .pdf format, which can be easily read by any pdf reader application like Adobe Acrobat Reader, Foxit Reader, OpenOffice, Google Docs and many others.
Can I purchase PDF Version without the Testing Engine?
PDF Version cannot be purchased separately. It is only available as an add-on to main Question & Answer Testing Engine product.
What operating systems are supported by your Testing Engine software?
Our testing engine is supported by Windows. Andriod and IOS software is currently under development.
Top ISC Exams
- CISSP - Certified Information Systems Security Professional
- CCSP - Certified Cloud Security Professional (CCSP)
- SSCP - System Security Certified Practitioner (SSCP)
- CISSP-ISSAP - Information Systems Security Architecture Professional
- CISSP-ISSEP - Information Systems Security Engineering Professional
- CISSP-ISSMP - Information Systems Security Management Professional
- CAP - Certified Authorization Professional
- CSSLP - Certified Secure Software Lifecycle Professional
ISC Certifications
- CAP - Certified Authorization Professional
- CISSP - Certified Information Systems Security Professional
- CISSP Concentrations
- CISSP-ISSAP - Information Systems Security Architecture Professional
- CISSP-ISSEP - Information Systems Security Engineering Professional
- CISSP-ISSMP - Information Systems Security Management Professional
- CSSLP - Certified Secure Software Lifecycle Professional
- ISC-CCSP - Certified Cloud Security Professional
- SSCP - Systems Security Certified Practitioner


